Getting started with IPFS | 50 questions about IPFS (4)

26. What is the IPFS storage mining machine?
The IPFS storage mining machine is determined according to the hardware requirements of the IPFS storage and the network requirements are not high, which can effectively save network resources. The storage mining machine has relatively high hardware requirements. The storage miner has collateral, and it runs continuously for 7*24*365 days. Once the power is cut off, the network is broken, the server hardware is damaged, etc., the collateral will be partially deducted or deducted.
(1) Type of architecture of IPFS storage mining machine:
a. Intel system for traditional data centers
- How To | Install IPFS and IPFS Clusters on Raspberry PI
- PoD-Tiny – the simplest protocol for zero-trust transactions
- Technical Guide | Using Pubma to perform chaotic testing of the network
b. Using ARM structure
(2) Several problems to be solved in the storage space of the IPFS mining machine:
a. Resolve the deletion of duplicate data
b. Solve data compression
c. Solve the self-healing of data
27. What is the IPFS search mining machine?
The IPFS search mining machine is a mining machine customized according to the search service. The speed and stability of the mining machine to the network, the fixed IP requirements are very high, and the hardware requirements are relatively low, which can also effectively save hardware. Resources.
28. Super-fusion technology in IPFS storage mining machine
The hyper-convergence concept refers to not only resources and technologies such as computing, network, storage, and server virtualization in the same unit (x86 server), but also cache acceleration, deduplication, online data compression, backup software, Elements such as snapshot technology, and multiple nodes can be aggregated through the network to achieve modular and seamless scale-out, forming a unified resource pool.

29, the difference between IPFS mining machine and Bitcoin mining machine
IPFS mining is the space capacity of the hard disk. Bitcoin mining is calculated by calculation. Therefore, the IPFS mining machine is relatively faster than the Bitcoin mining machine.
30, IPFS architecture – network layer introduction
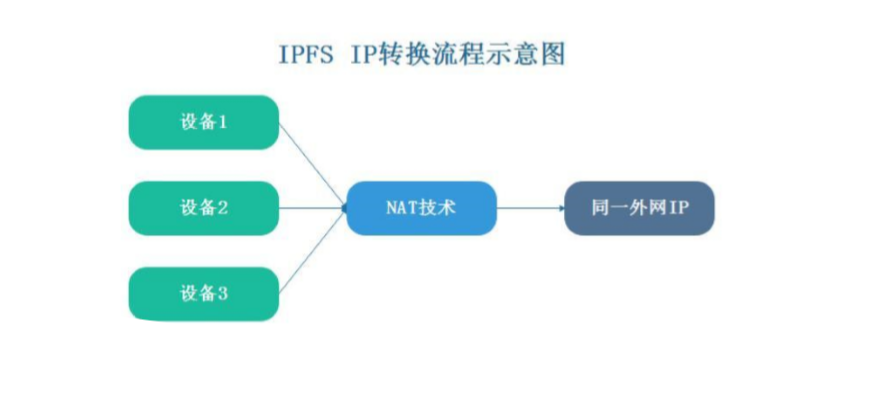
The network layer is one of the cores in the IPFS architecture, and LibP2P can support any transport layer protocol. NAT technology allows devices on the internal network to share the same external network IP. This principle is used by home routers.
31, Filecoin consensus mechanism
It is the use of copy proof (Porep) as the core work function, and is summarized in the space-time certificate (Post), and has a secret leader (Sle) election structure.
(1) Copy proof (Porep)
a. The certifier is providing each copy of the physical resource data that is independent of each other, even if the certifier is capable of generating the data;
b. The prover P can prove to the verifier that P itself stores a specific copy of the data D, and the copy is not repeatedly stored in the same physical memory;
(2) Time and space certificate (Post)
a. Non-interactive proof, self-certification, interactive generation of a censorable proof chain;
b. Allow the prover P to concentrate the space certificate (or storage certificate) into the auditable record over time, which proves that P does consume space S (or store data D) and maintains a clear time T;
(3) Secret Leaders Election SLE – Fair Election; Verifiable; Avoid Bribery / Collusion / Corruption;

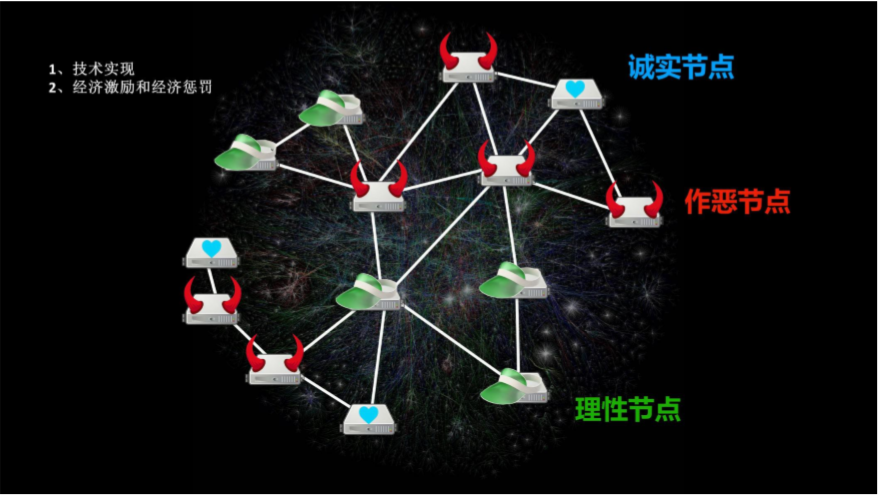
32. How to prevent deceptive behavior of evil miners in Filecoin
The secret leader election process is actually process identification (power fault tolerant PFT; copy proof; space time proof), value equivalence in the design of the pass, and mortgage margin mode. In other words – "no value, no parity", behavioral rewards that are conducive to network construction are deep, and two-way interactive verification or guarantee mode to prevent evil.
(1) Witch Attack: A bad miner pretends to physically store many copies (rewarding rewards) by creating multiple witch identities, but only once
(2) Outsourcing attacks: relying on the ability to quickly acquire data from other storage providers, and the miners may promise to store more data than their actual physical capacity.
(3) Generational attack: A bad miner may claim to store a large amount of data, instead they use a small program to efficiently generate a request. If the small program claims to store the data, the possibility that the miners will get the block reward in the file coin increases because it is directly proportional to the current usage of the miners.
33. How to motivate storage contributors in Filecoin
(1) The client initiates the storage data PUT behavior;
(2) storing the contributor to respond to the order;
(3) The order is successfully matched and recorded on the block;
(4) Contributors receive income.
34. Filecoin's economic model
(1) Real sharing economy, hard disk + Airbnb;
(2) Matching resources by the code of the consensus mechanism and the market agreement;
(3) Unlike the pseudo-sharing economy, it eventually became a third-party leasing company;
(4) All transactions are transparent and the pledged coins do not enter anyone's pocket;
(5) Storage prices vary with value around the market economy.
35. Will the same file in the IPFS network be backed up several times?
The backup is determined several times by the order. IPFS has the most basic backup mechanism. The default base redundancy is three copies of the same file. Although there is no limit, the market effect will make the extra redundancy not frequently accessed be stored. The party actively deletes.
"IPFS50Q" is the IPFSNEWS [IPFS Getting Started] section of the IPFS domain knowledge popularization section, which aims to bring you closer to technology through in-depth explanations.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Ethereum 2.0: Randomness
- Technical Guide | Understanding the Generalized Plasma Technology Structure – part I
- Third-party code auditing and testing of Algorand test network: mature system and good anti-attack
- Technical Guide | Specifications for Plasma Cash Block Structure
- Introduction to Blockchain Technology | Atomic Exchange
- How to build a distributed exchange based on atomic interchange technology using Oraclize
- Bai Shuo: From the technical point of view, DeFi feasibility, 3 major challenges, 8 big mistakes, how to crack | 2019 Global Blockchain (Hangzhou) Summit Forum
