Elliptic Curve Cryptography & Workload Proof
Most cryptographic assets use an elliptical curve identical to Bitcoin, called secp256k1. This makes it possible to reuse Bitcoin's many elliptic curve libraries and tools.
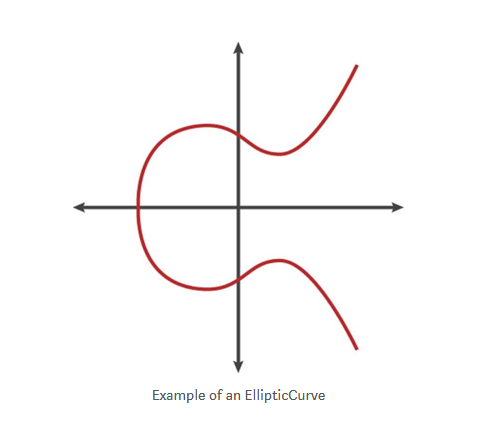
Elliptic Curve Cryptography (ECC) is a public key encryption algorithm based on elliptic curve mathematics.
The following figure shows that most cryptographic assets use an elliptic curve identical to Bitcoin, called secp256k1. This makes it possible to reuse Bitcoin's many elliptic curve libraries and tools.
- Technical Guide | Ethereum Wallet Development: Generate Account Address, Private Key, Keystore, mnemonic
- Restoring the entire process of asset transfer: $6.02 million stolen from the DragonEX exchange
- Popular Science | Hash Function Brief
The elliptic curve technique is used to create a public key derived from a private key.
How elliptic curve technology works
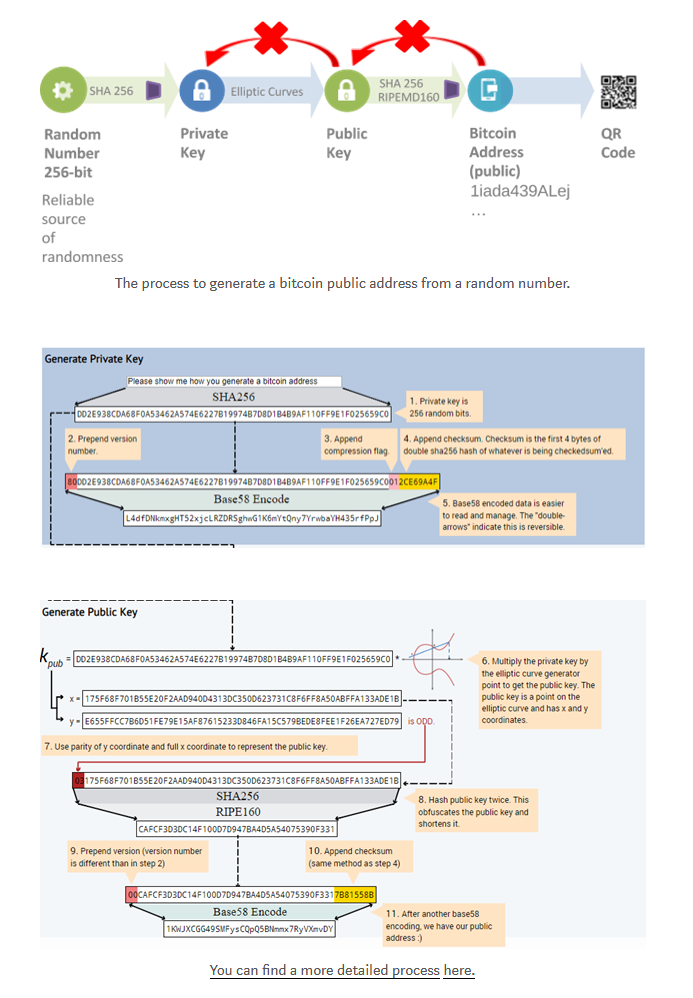
Starting with the private key of a randomly generated number _k_, we multiply it by a predetermined point on the curve called _generator point_G_ to create another point on the curve, which is the corresponding Key _K. The generation point is specified as part of the +secp256k1+ standard, and all implementations for +secp256k1+ are always the same, and all keys derived from this curve use the same point _G_:
K = k * G
k is the private key
G is the predetermined point
K is the generated public key, a point on the curve
Since the predetermined points on all bitcoin user curves are always the same, the public key k multiplied by G will always get the same public key K. The relationship between k and K is fixed, but this situation exists only in one direction. The operation can only be from k to K. This is why the bitcoin address (derived from K) can be shared with anyone and does not reveal the user's private key (k).
To visualize a point multiplied by an integer, we will describe it using a simpler elliptic curve than the real number, aiming to find multiple kGs at a predetermined point G on the curve.
This arithmetic logic is the same as adding G itself continuously by k times. In an elliptic curve, adding a point to itself is equivalent to drawing a tangent on the point and finding the location where it intersects the curve, and then reflecting that point on the x-axis.
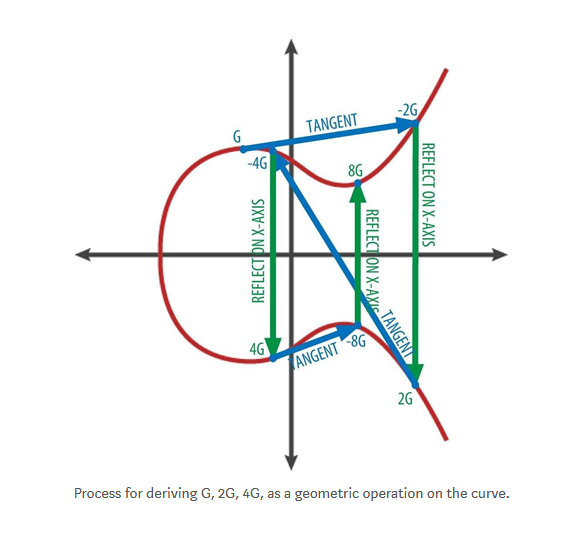
The figure below shows the process of exporting G, 2G, 4G as a geometric operation on the curve.
1. The first step is to have a reliable random source and get a random number (256 bits).
2. Second, you need to apply SHA256 to the number and get the private key (k).
3. By applying an elliptic curve (encryption technique), the public key (K) is obtained, as described above.
4. Substitute SHA 256 and RIPEMD160 (a different hash function) to get the bitcoin address.
5. Display addresses in a number of different formats, the most common being the QR code.
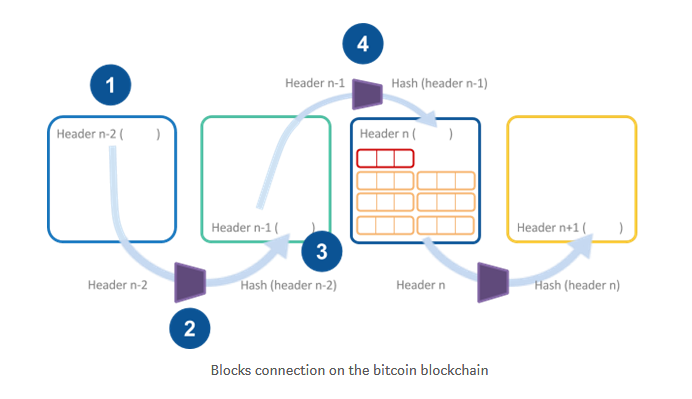
How do blocks link to each other?
Each block contains many transactions. Each block contains specific information about that particular block. The main field of the block is the block header of the block. The block header contains the hash value of the previous block (PreHash), the hash value (Hash) of the block, and the timestamp (TimeStamp), the difficulty of the block, and the root of the "state Trie" in the Root:StateDB. The RLP hash of the node. In the Block, each account is represented by a stateObject object, the account is uniquely identified by Address, and its information is modified in the execution of the related transaction (Transaction). All account objects can be inserted into a Merkle-PatricaTrie (MPT) structure one by one to form a "state Trie". Nonce: A 64-bit hash that is applied to the "drill" phase of the block and will be modified during use.
A blockchain is a chain structure that contains the head node (the first block) and the tail node (the last block) of the chain. Once someone has calculated the hash value of the latest data information in the blockchain, it is equivalent to packing the latest transaction record, and the new block will be created and connected at the end of the blockchain.
Workload Proof (POW)
As noted above, Workload Proof (POW) systems (or protocols or functions) are economic countermeasures that address service or resource abuse or block service attacks.
working principle:
As mentioned above, the block header contains: the hash value of the previous block (PreHash), the hash value of the block (Hash), and the time stamp (TimeStamp), the difficulty of the block, Root, Nonce.
The key element in implementing PoW is Nonce. The operation of the PoW is carried out by computers scattered throughout the competition. Who can find the earliest match, the Nonce, which is the original data to be packaged, is equivalent to obtaining the packaging right (bookkeeping right) of the block. After the guess value is found, it is packaged into blocks and broadcasted together with the data and the hash value. After confirmation and recognition by the majority node, the packager can obtain the reward provided by packing the block.
If you are a miner, the first thing you need to do is to "mining" to find a block header and apply SHA256. To do this, you need to assign a number to the Nonce because all other fields in the block header are fixed. For example, suppose you start with Nonce = 0. This way, you will get an alphanumeric string (2poiuwfsvhxnv382249j).
As follows:
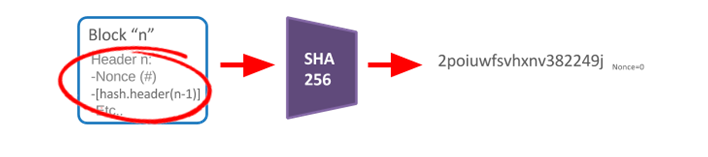
Then all you need to do is compare the results with the target values. The target value is a variable used to define a numeric or alphanumeric string at the beginning. (eg 0000000wirug43xj).
The question is: Is the hash value of the specific Nonce block header the same as the target value of 0 or more? For example, 2poiuwfsvhxnv382249j is less than 0000000wirug43xj, and the former contains less than 0. So which variable do you need to change on the header of the block to apply SHA256 to get different results? This is the benefit of the SHA256 collision resistance property. Collision resistance is an attribute of a cryptographic hash function: if it is difficult to find two inputs hashed to the same output, the hash function H is anti-collision; that is, the two inputs a and b make H = H, And a≠b. Each hash function that inputs more than the output will inevitably collide. Consider a hash function, such as SHA-256, which produces a 256-bit output from a large input. Because by simply changing the Nonce to the block header and applying SHA 256, the result is completely different (and random) from the previous answer. Change the Nonce in the above example to 1 and the result is "0057aasñhlqywirfdr334".
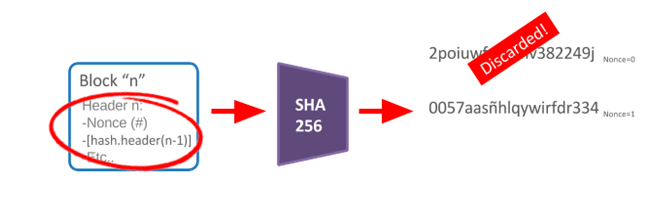
0057aasñhlqywirfdr334 contains 0 and the number of 0000000wirug43xj is also different.
The process continues (the miner goes through millions of calculations per second in this process and will try again when the results are wrong) until the target's Nonce is obtained.
Therefore, all miners are competing in order to be the first to find the target Nonce, which also reflects the disadvantage of PoW, that is, wasting energy.
Once the miner gets the Nonce, he will broadcast on the network, and other nodes will find that the target value is quickly verified by entering the Nonce and applying SHA256Nonce.
As a bonus, miners who acquired the block Nonce received bitcoin in two ways:
1) The fee paid by the exchange included in the block.
2) The system creates a new bitcoin. (As of May 2017, its 12.5 btc / block)
How long does it take for the miner to find Nonce?
When Satoshi Chong designed bitcoin, the mining difficulty adjustment mechanism was added to make the bitcoin block time ideally constant at around 10 minutes. The Bitcoin Agreement stipulates that every 2016 block will automatically adjust the mining difficulty of the next 2016 block based on the total time of the last 2016 blocks. Ideally, the 2016 block will take two weeks (2016*10s). If it is less than two weeks, it will increase the difficulty. If it is more than two weeks, it will reduce the difficulty.
Increasing the difficulty means adding zero to the beginning of the target value; reducing the difficulty means reducing zero at the beginning of the target value.
This article is compiled from the financial network of the financial network from Hackernoon, does not represent the financial perspective of the financial network chain.
Original link: https://hackernoon.com/cryptographic-essence-of-bitcoin-part-2-how-do-public-private-keys-work-2c52d6bc8406
Author: Gayan Samarakoon compilation: LornaQ
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- The first long-term supported version, Hyperledger launches Fabric v1.4 LTS
- In-depth understanding of IPFS (1): Beginner to Advanced Guide
- Technical Guide | Ethereum Wallet Development: Wallet Address Generation Process
- The Uncle Block of the Ethereum Reward Mechanism (Part 2)
- Dry goods | read the solidity programming
- Bitcoin Lightning Network: Micro Payment Channel
- Uncle of the Ethereum Reward Mechanism (middle)
