Restoring the entire process of asset transfer: $6.02 million stolen from the DragonEX exchange
In the early morning of March 24th, Beijing time, the DragonEX exchange issued a notice stating that its platform digital assets were stolen, and called on all parties to jointly block hackers. It can be learned from the announcement that more than 20 kinds of mainstream virtual currency assets such as BTC, ETH and EOS on the DragonEX exchange have been stolen. Although the exchange officially did not announce the specific amount, it was initially estimated that the exchange was stolen. The large number of currencies and the large amount of damaged assets are rare in the development of the entire blockchain.
After receiving the warning from the DragonEX exchange, the PeckShield security team immediately analyzed the entire process of the "hacker" attack and restored the full path of the asset transfer on the chain. According to preliminary statistics from the PeckShield digital asset escort system, the DragonEx exchange lost a total of $6,028,283 worth of digital assets, and digital assets worth $929,162 have flowed into the exchange. There are still $5,099,121 worth of digital assets in the hands of hackers. in.
PeckShield security personnel preliminary analysis believes that the hacker has a high probability of implementing digital asset batch transfer by stealing the exchange wallet private key or illegally obtaining API server access.
The thieves’ implementation of stolen money and money laundering can be divided into two stages:
- Popular Science | Hash Function Brief
- The first long-term supported version, Hyperledger launches Fabric v1.4 LTS
- In-depth understanding of IPFS (1): Beginner to Advanced Guide
1. The stage of stealing money: occurred from 1 am to 8 am on March 24, the hacker transferred more than 20 currency assets such as BTC, ETH, EOS, etc. of the exchange to his personal account, and completed asset transfer and stealing;
2, the stage of washing coins: began on March 26th so far, so far, hackers have transferred digital assets worth 929,162 US dollars to various exchanges, it is likely to have been sold, the remaining 5,099,121 most of the funds are still attackers Among the associated accounts, there is the possibility of further inflow into the exchange, and all parties need to jointly implement the fund closure.
The timeline of the stolen money:
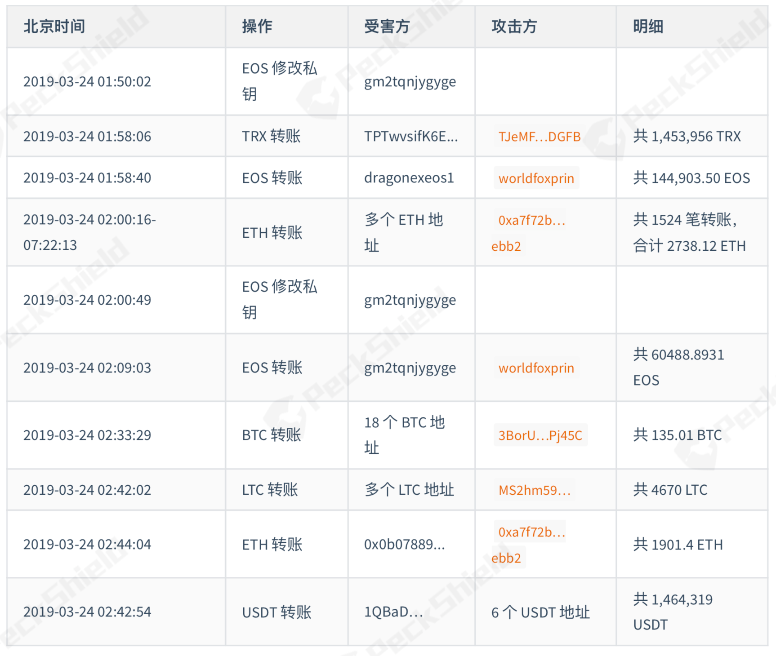
PeckShield security personnel initially restored the chain transfer record behavior of mainstream currencies such as BTC, ETH, EOS, TRX, USDT through the hacker address published by DragonEX, and restored the entire process of the exchange of stolen coins:
Loss of assets details:
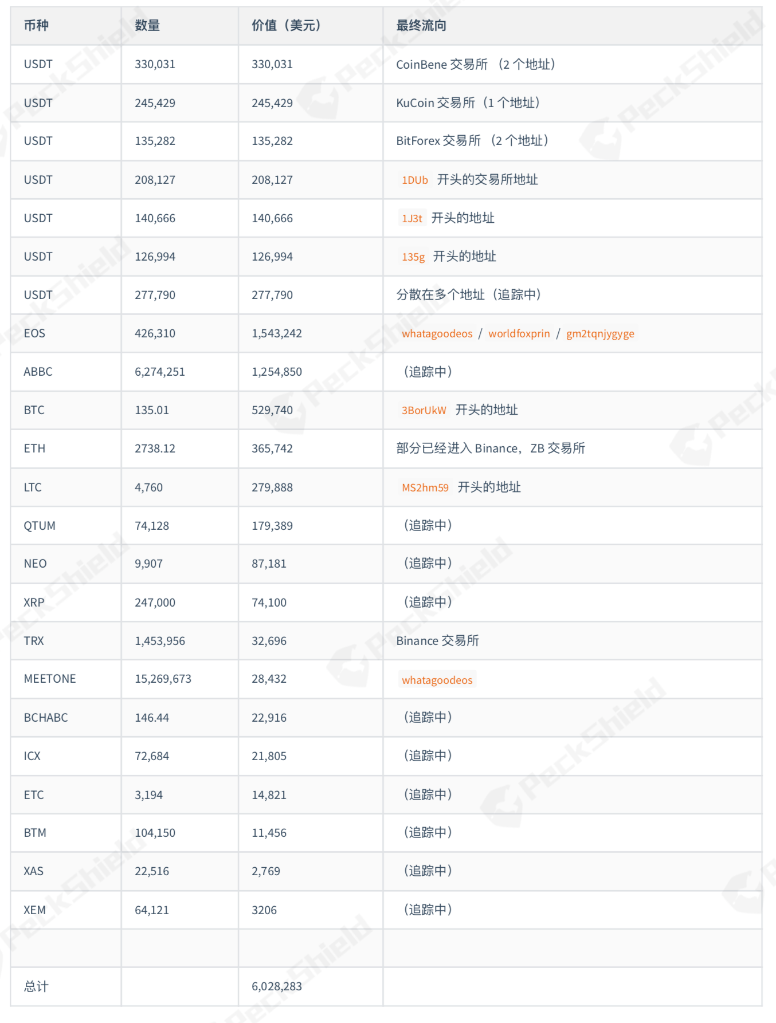
(Analysis of the theft of major chain assets:)
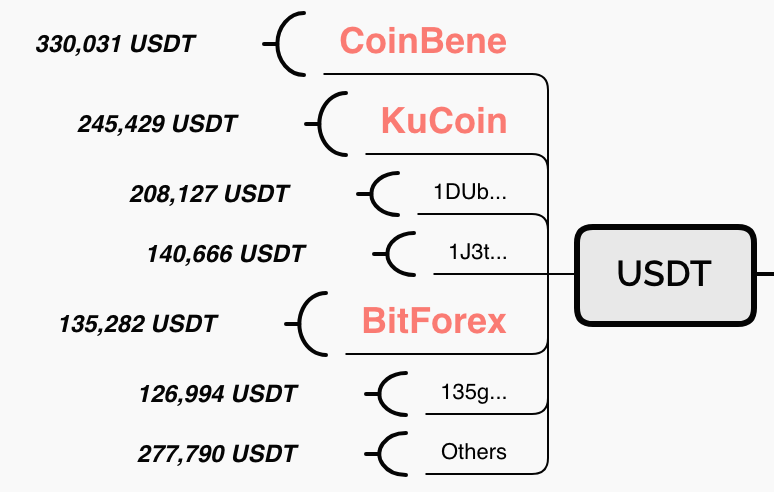
The following takes the USDT and TRON main network as an example to analyze the whole process of “hacking” stolen coins:

USDT main chain:
1. At 02:42 on March 24th, DragonEx named 1QBaDdhCTC2k9WWFhCXCJvYHpVSqLSRxaJ to transfer a large number of USDTs to the following six addresses:
1P4cdD9kTFGV6wmFxbeoZXosRNUrMrMbmN 273,597 pieces USDT; 1JBoGBv7GnqN6ncEi9aSU71gobcMG9R1Ca 222,738 pieces USDT114F7vWREusZTRGcEZGoTAuhWvq8T5tzxR 238,652 pieces USDT1HapWDybdWW1H61saGokQ88xVaHvfukgu2 240,971 pieces USDT; 17gqLwmBxdmKEP8vaBEn2ghHvj4vqCiR6q 240,971 pieces USDT1B6t6RnVMpTQKhbXsr8hNB3DiyXSSkomkU 247,390.31777 pieces USDT;
2. After receiving the USDT, the above six addresses will be transferred to the exchange gradually through multi-layer conversion. Currently, PeckShield researchers initially locate the current USDT asset distribution as follows:
1 wherein a plurality of through 330,031 pieces USDT address translation, ultimately into CoinBene exchanges address and name 1HCviLYNqHAyeZxGTj9Mtgvj1NJgQuSo91 by 1GirA64XdJjH6HHzgH7Tj5WoBmyH5Z3wjn 1CdbfukQ1JsJK5csqYGonP1mDp3hVyePc3; 2. 245,429 pieces USDT also through a plurality of address translation, ultimately flows through 1AEJpcgLUrMyqz3iPAF3ETozwV3PaZkjGo named 17ScKNXo4cL8DyfWfcCWu1uJySQuJm7iKC exchange of KuCoin address; 3. USDT 208,127 pieces of an unknown exchange inflow address 1DUb2YYbQA1jjaNYzVXLZ7ZioEhLXtbUru; 4. 140,666 pieces stay in USDT 1J3tVZrmQFiH2R8fCsGab7AfWVKh6wHTQ6; 5. 135,282 pieces USDT also through a plurality of address translation, ultimately into the BitForex 12vCxak5xc1t6T275xbm6AJ4xsZCxkTSc5 named by 1CNwEPguYVUhziMEiCe1PKKSHv2Ur5B1KC exchanges and 1CNuTqmJcwfyWKdtuqhitUL4pewWcPJuzf Address; 6. 126,994 USDTs also undergo multiple address translations, eventually flowing to the 135gVHBkLUidwpd6va9eZyECGVLCek2z4y address; 7. The remaining 277,790 USDTs are spread across multiple different accounts.
TRON main chain:
The following figure depicts the process of the stolen assets of the TRON address announced by the exchange:

The details of the process are as follows:
1. On March 24th, the address of DragonEX named TPTwvsifK6EiQ1mm6b4eEQAcammL5215g6 is transferred to TJeMF6CpEDeG94UAF7d4dzjXkgrwwtDGFB address 1,453,956TRX;
2. There is no change in the TjeM…DGFB address between March 24th and March 26th;
3. On the 26th of March 26th, between 9:00 and 10:00, the address TJeM…DGFB separates the 1,453,956TRX received from 03-24 to the 6 new addresses. At the same time, all the assets obtained before and after the 6 addresses are transferred to TR8T47ouBgr7V2ssDjDaz9PJ7JaPH3kwrR address, PeckShield researchers found that TR8T…kwrR address suspected currency exchange exchange address;
4. At this point, 1,453,956TRX are all transferred to the Onan Exchange.
summary:
In this security incident of the DragonEX exchange, the hacker transferred all the major digital currencies in an exchange within a short period of time, and then confuses the funds input through other digital currency exchanges, and the funds are smoothly washed out.
However, most of the stolen assets are still controlled by hackers. The parties in the exchange, including the real-time transaction alert of hacker account funds, can assist security companies to lock and block stolen assets and help victims to reduce as much as possible. Loss of digital assets.
In general, the hacking of exchanges is related to the digital asset security of many users. PeckShield security personnel appeal to all major transactions to improve the security and risk control capabilities of the platform, and if necessary, look for a professional third-party security team to assist.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Technical Guide | Ethereum Wallet Development: Wallet Address Generation Process
- The Uncle Block of the Ethereum Reward Mechanism (Part 2)
- Dry goods | read the solidity programming
- Bitcoin Lightning Network: Micro Payment Channel
- Uncle of the Ethereum Reward Mechanism (middle)
- Project combat: Bitcoin charge and withdrawal integration
- Ethereum trading fee is too high? Teach you how to set up a transfer miner fee
