The study found that 5% of the Monero currency circulating in the market was mined by malware

According to the study, mining was done through encrypted hijacking, using other users’ computer processing power to mine cryptocurrencies without the owner’s permission.
Josh Grunzweig of the No. 42 Threat Research Group collected approximately 470,000 unique samples of anonymous miners found on the Palo Alto network platform.
The report found that there were 3,773 emails connected to the pool, 2,995 pool url addresses, 2,341 XRM wallets, 981 bitcoin wallets, 131 e-wallets, 44 Ethereum wallets, and 28 Litecoin wallets.
According to Grunzweig, Monero has an “unbelievable monopoly” on the currency mined by malware, maliciously exploiting a total of $175 million in Monero (about 5% of all Monero currently in circulation). The total market value of Monero is about $1.9 billion, and the transaction price is about $119. The deadline for publication is 24 hours, a drop of about 10%.
Of the 2,341 Monero wallets found, only 55% (or 1278) had more than 0.01 XMR (currently around $1.19).
The report also pointed out that the data does not include the web-based Monero miners or other miners they are unable to access, which means that 5% of the data is likely to be too low.
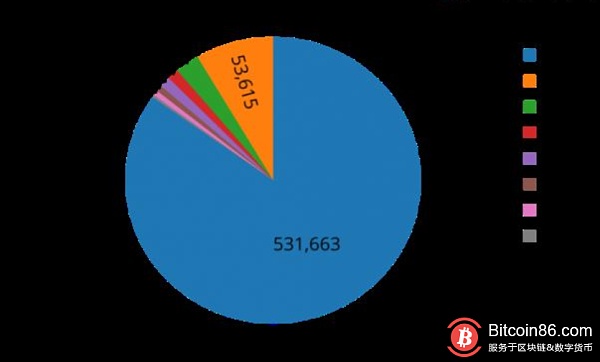
The distribution of cryptocurrencies targeted by malicious miners. Source: Palo Alto Network
According to the report, the total hash rate of Monero encryption – about 19 megahertz per second (MH/s), which brings $30,443 a day – is about 2% of the global hash power of the Monero network. According to the report, the top three sources of hash rates are about $2,737, $2,022 and $1,596 per day.
In an email to Cointelegraph, Justin Ehrenhofer of the Monero Malware Response Working Group wrote that because Monero is “without any clear use case construction,” people “may use the privacy of Monero. Accessible work characteristics prove that you are seeking improper personal interests for yourself.”
For this reason, the Malware Working Group is a volunteer group dedicated to educating encrypted users about how to avoid malware and being encrypted:
“The Monero community is interested in helping unwelcome system mining and other illegal activities. We can never stop every machine from being damaged. It is estimated that the proportion of coins mined by Monero coins largely reflects the number of destroyed machines. In addition to mining Monero coins, they can also send spam and Surveillance of users. We hope that our contribution will limit unwelcome behavior at the source.”
Yesterday, Japanese police reported that they had begun investigating the case of Monero’s use of Coinhive mining software for theft. Last week, a security team found that more than 40,000 computers were infected with mining malware, including Monero, which came from industries such as finance, education, and government.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles






