American Computer Society: What exactly can blockchain technology do?
Associate Professor Scott Ruoti, electrical computers and assistant professor in the Department of Science and the University of Tennessee Ben Kaiser, PhD Policy Center of Information Technology Princeton University Arkady Yerukhimovich, assistant professor of computer science at George Washington University Jeremy Clark, Montreal Concordia Institute of Systems Engineering information: author Rob Cunningham, Associate Director of Network Assurance, CERT Department, School of Software Engineering & Adjunct Professor of Network Security, Carnegie Mellon University
Source: Contributions from IPFS Force Zone
Original link: https://queue.acm.org/detail.cfm?id=3376896
Last year, the Blockchain Research Department of the People's Bank of China released "What can and cannot do with blockchain" . Coincidentally, the first issue of the American Computer Society Newsletter in 2020 released an in-depth survey article jointly written by multiple technical experts, "What can a blockchain do? ".
- Babbitt Column | Stocks, Tokens, Who Are the Future Trends?
- Former SEC officials look at China's central bank digital currency: 2020
- Six marketing trends for the blockchain industry in 2020
The article believes that blockchain, the underlying technology that Bitcoin operates in, has always been sought after by technology news. The biggest gimmick in technology news is that blockchain technology has reduced, or even completely eliminated people's need for trust. This publicity makes the blockchain enhance people's imagination, and people also use the imagination to enhance the ability of the blockchain.
In fact, trust is complicated. Blockchain technology does eliminate people's specific, narrow dependence on trust, but it also requires new assumptions, which may be better or worse for specific use cases. Therefore, there are many words about the efficiency, security, and cost of blockchain technology.
Obviously, blockchain technology needs more detailed discussion. Business executives, government leaders, investors, and researchers often ask three questions:
- What is blockchain technology?
- What features does it provide?
- What good applications?
"What Can a Blockchain Do? The goal of this article is to answer these questions thoroughly, provide a holistic overview of blockchain technology, distinguish it from publicity, and provide a useful vocabulary for future discussions of blockchain technology
Blockchain technology attributes
The first major category of blockchain technology concepts is technical attributes, which are further subdivided into three key groups: shared governance and operations, verifiable status, and data recovery capabilities. Figure 1 below shows the relationship between them.
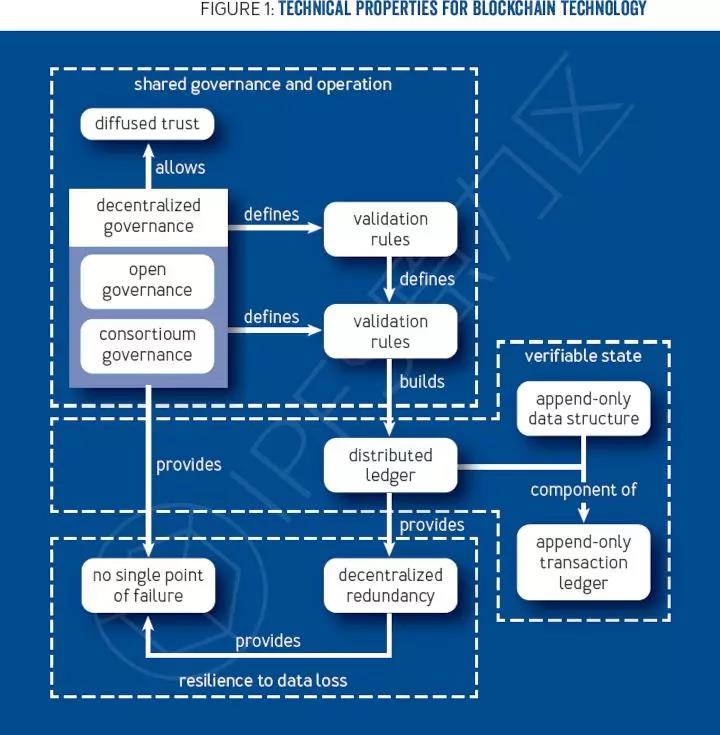
Shared governance and operations
Blockchain technology solves the situation where certain entities (for example, individuals or companies) want to participate in a public system but do not trust each other or any third party separate operating systems. By identifying system details (governance) and then deploying network equipment (called miners) to run the system, each entity can ensure correct operation. In the event of a small number of attacking miners (within a highly nuanced range), honest miners can refuse malicious actions taken by attacking miners and retain the correct operation of the system. In this regard, blockchain technology provides a wide range of trust in which miners collectives are trustworthy. This is often given inappropriate trust-trust still exists, but has been decentralized.
Sharing operations are achieved through consensus protocols, which are used by miners to agree on what operations (called transactions) the system performs. The transaction mentioned here sometimes sounds like a financial transaction-the transfer of value from one account to another-but generally it is a requirement: to perform a specific function on the input given in a set of transactions (it Itself may be stored in the blockchain system). Shared governance exists about what efficient processing looks like (for example, the transaction is digitally signed by the sender) and how the system works (for example, the size and number of operations in a transaction are less than a certain limit). The sharing operation means that each miner verifies the transaction, and the consensus between the miners is used to ensure that only the correct valid transaction output is written to the blockchain system (invalid or incorrect transactions can be proposed but will be rejected by the miners).
Blockchain systems can be divided into two categories: decentralized governance (license-free blockchain) and alliance governance (licensed blockchain).
Verifiable status
Entities use blockchain technology because they want their trust to be rooted in the system (that is, the current state of the system accurately reflects the transactions that consensus protocols have allowed to execute in the past). In order to achieve this trust, miners write all transactions into a cryptographically verified only additional ledger, provide a complete system source, and allow miners (or external parties) to audit the current state and past operations of the system.
In many systems, including Bitcoin, this ledger is often referred to as the blockchain (we avoid using this term to describe the ledger to avoid confusion with the overall reference of blockchain technology). In the ledger, all transactions are strictly orderly. After reaching an agreement (as long as they agree), this order has never changed, and the transaction has never been cancelled. Therefore, starting from the first block (called the genesis block), all miners will process all transactions in the same order and reach the same current state of the entire system.
Data recovery capabilities
If the ledger is stored in a separate location, all parties can detect the deletion or modification of the data, but there is no guarantee that the data can be recovered. Using blockchain technology, all miners can copy the contents of the ledger to resolve single points of failure. When data does need to be recovered—for example, if a certain miner's ledger is damaged or there is a new miner connection—the copied data can be verified to ensure that it correctly represents the state of the system.
Some blockchain systems try to limit the amount of data that any given miner needs to replicate by sharding the data and allocating miners to manage and operate only a subset of the system. This is the sharding technique, and each part of the data is called sharding. Sharding can greatly reduce the amount of data that miners need to store, and can also improve the performance of consensus protocols. Consensus protocols usually expand based on the number of miners. Nonetheless, consensus has increased the complexity of auditing the entire system. In addition, by reducing the number of miners responsible for any given transaction, sharding can reduce the number of miners required for an attack to deceive end-users into the existence of a transaction.
Functions of the blockchain
Defined here are the advanced functions implemented using blockchain technology in system design. The three core functions of blockchain technology have been described in the first part:
- Shared governance and operations;
- Verifiable status
- Resilience to data loss.
In coding, we identified 11 additional features. (In Figure 2, these functions are color-coded: purple indicates functions; blue indicates technical performance; green indicates technical elements. Arrows indicate that the target depends on the source.
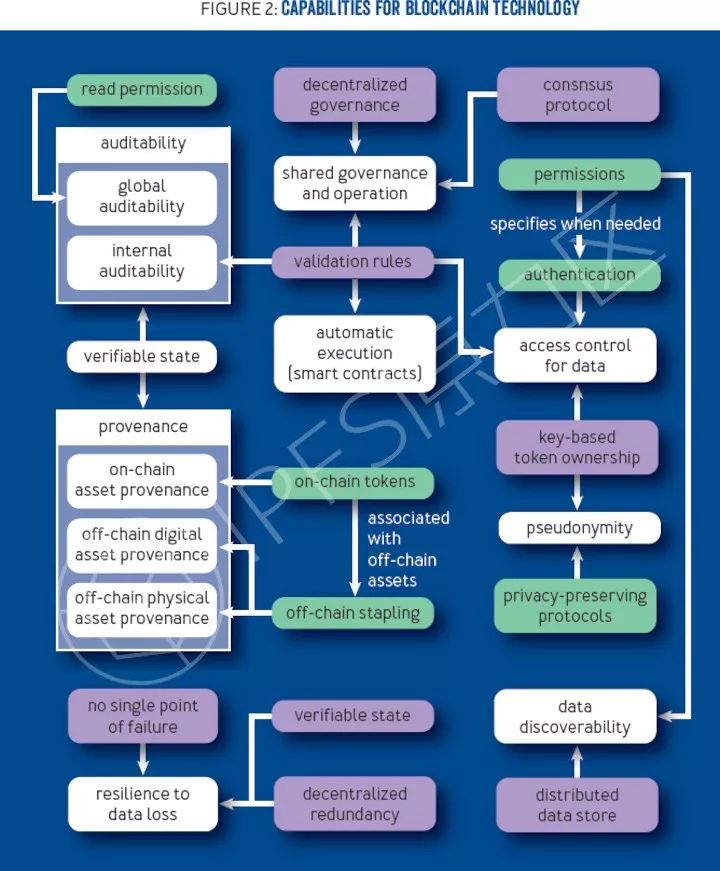
Provenance and auditability
The blockchain system provides a complete history of all transactions, these transactions are by consensus process (that is, the source of the complete system). Miners can use this information to audit the system and ensure that the system always follows appropriate rules. In addition, non-miners can use this information to verify that the system is properly governed and operated.
If transactions are used to store information about digital or real-world resources, those resources must be identified on-chain. The provenance information of the blockchain system can also be used to provide audit information for these resources. This can be used to track off-chain physical assets (for example, for supply chain management), off-chain digital assets (for example, copyrighted digital media), or on-chain assets (for example, cryptocurrencies or data files). Access control and pseudonymous data stored in the blockchain system may have some restrictions, and users can use it as an input to a transaction or modify it as part of a transaction. For example, a financial asset should only be a valid input for a transaction if the asset owner approves its use. One way to provide this functionality is to store an access control list (acl) in the ledger and have the appropriate users prove their identity to the miner (for example, using Kerberos or OAuth 2.0) as part of the transaction verification process.
More commonly, access control in blockchain systems is implemented cryptographically: data is associated with a public key when it is created, and only users who can prove their knowledge are granted the ability to use or modify that data as part of a transaction. The corresponding private key (for example, attached to the data verified by generating a signed public key). You can extend or transfer ownership of data by associating it with a new public key.
There is another advantage to key-based (rather than acl-based) data ownership: it allows anonymously to own and use data. However, this requires careful attention in system design to use appropriate encryption techniques (for example, zero-knowledge proofs, hybrid networks, or secure multiparty computing) to avoid associating real-world individuals with their keys and operations. This remains an open question.
Automatic execution
In a universal blockchain system, transactions that store a set of function codes and the initial state of a contract can be used to deploy smart contracts or decentralized applications (DApps). These functions can then be called in subsequent transactions. The function itself is executed by the miner, and the output is verified by the consensus protocol. Any entity can execute any function, but if the conditions for calling the function are not what the blockchain wants, the function may be programmed to fail. The computing power of scripting languages varies from system to system, and there are many subtle differences that ensure that functions can be executed in a timely and deterministic manner by each miner. Bitcoin is known for its limited scripting language. It has little support for anything other than financial transactions, while Ethereum is committed to providing very detailed contract codes that can perform general calculations.
Discoverability of data
Challenges and limitations
- Scalability and performance: the cost of decentralized governance and POW energy consumption
- Correctness on the chain: All code has bugs, and smart contracts are no exception.
- Off-chain tagging: How can physical assets (real-world events and information) be tracked and tagged off-chain?
- Security: the decentralized nature is more vulnerable to attacks (DDOS, partitioning, blocking consensus, etc.)
- Privacy and Anonymity: User Anonymity
- Ease of use: Blockchain systems require users to store, manage, and protect encryption keys. As everyone knows, this requirement is a major obstacle for most users.
Applications
financial
- Digital currencies and payments: consortium governance
- Asset transaction: decentralized transaction
- Markets and auctions: transactions and auctions using blockchain
- Insurance and Futures: Blockchain as a Time Base
- Penalties, remedies and sanctions: legal contracts
Data storage and sharing
- Asset tracking: a common environment for collaboration between businesses
- Identity and key management: people as assets
- Tamper-resistant record storage: off-chain storage, on-chain tracking
Other cases
- Shared governance: electronic voting and voting
- Fair Arbitration: Gambling and Gaming
to sum up
In the final analysis, blockchain technology is not a panacea, but it is a useful tool when the overhead of the system is reasonable for the needs. How to determine if your business or system needs a blockchain? A good start is to ask the following questions:
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- DeFi weekly selection 丨 High ETH lock-up volume, zero mortgage DeFi for "Great Leap Forward"
- The IRS is here again! Tax assessment required for single cryptocurrency donations exceeding $ 5,000
- How did Libra fail today, and how can it succeed in 2020?
- Blockchain backdating threat: Without identity verification, value transfer can only be performed in specific scenarios
- A review of the privacy coin developments in December 2019. The XMR, Grin, Beam, and ZEC you care about are all here
- Talk about Hayek, Satoshi Nakamoto and Bitcoin
- 2019 Global Blockchain Policy Annual Report: China focuses on support, and the US mostly regulates




