Blockchain backdating threat: Without identity verification, value transfer can only be performed in specific scenarios
Source: medium.com
Compilation: First Class (First.VIP)
The lack of digital identity verification will reduce the effectiveness of the blockchain, and autonomous identity will improve the identity verification process.
The most common use of blockchain networks is value transfer. Cryptocurrencies will be the standard for future digital assets. A smooth (non-resistance) transfer of programmable digital value is a key step in the future digital economy. Individuals have more control over their money. Customers experience more user-centric and affordable services. The company has real-time balance sheets and automatic financing. The entire financial industry has eliminated many complex steps and developed more functional, inclusive and transparent services.
- A review of the privacy coin developments in December 2019. The XMR, Grin, Beam, and ZEC you care about are all here
- Talk about Hayek, Satoshi Nakamoto and Bitcoin
- 2019 Global Blockchain Policy Annual Report: China focuses on support, and the US mostly regulates
Value transfer
If we take a closer look at what is value transfer, we will find that payment is only a small part of it, and the transfer of money and assets is the result of value transfer. For example, one company orders products from another. The business process involves the buyer signing a purchase order. The seller approves the order and sends the bill / receives the payment. The seller then ships the product to the buyer and signs a title receipt. With product assurance and support, process responsibilities are further expanded. Larger orders can also be funded and guaranteed by different financial institutions. Finally, tax management is also part of the business process.
When we want digital value transfer, we want to connect the entire business process. Orders, payments, finances, and collections are all part of the value transfer process. At present, some financial institutions and third-party service providers have undertaken more or less part of the work in this process. The main role of financial institutions in the transaction process is to assist large customers. Service providers focus on scalable solutions in the process. Although there are some automated ways to do this, the value transfer process is still incoherent and manual.
Smart contractualization of business processes
Some blockchain platforms solve this problem by providing so-called smart contracts. These programmable contracts support the modeling of complex business scenarios with multiple participants. The business rules in the contract are automatically enforced in some way. This tamper-resistant process enables each participant to verify the current state of the contract. Trust comes from business processes, rather than understanding each participant, so the contract network strengthens trust.
Currently, these platforms have a limited scope of work. The first method is to use a public blockchain network with cryptocurrencies and smart contracts. Such networks are generally open to everyone, have extensive interoperability, and have the disadvantage of weak law enforcement. Enforcing laws is difficult in an open, decentralized global network. The second method is to build a closed network with known participants. Network governance rules define the ownership of responsibilities in business processes. In this way, network users can use legally binding smart contracts between different organizations.
Lack of digital authentication
The economy based on the blockchain network has not fully fulfilled its promise. One of the key reasons is the lack of digital authentication. Without authentication, value transfer can only take place in specific scenarios. Without legally binding identity verification, public blockchain networks have limited ability to model real business processes. Closed networks are legally binding and can manage users, but this also limits interoperability beyond network use cases, which is very similar to our situation on traditional platforms. For example, credit card payments are severely restricted worldwide, and financial institutions can only operate more flexible and expensive financing solutions with specific customers.
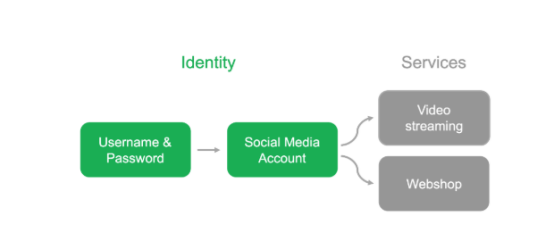
Social media login has become an increasingly popular login mechanism
Digital authentication is the missing part of digital value transfer. Now we have many ways to deal with identity information. The user's data and authentication are scattered among different service providers. Users either use a traditional system-based login or a third-party (such as a social media platform) associated account information. It is difficult to track where the various parts of identity data are located. Although the alliance model has been improved, users cannot use data between different systems. This ultimately leads us to a situation where identity-related data does not belong to the user and is not controlled by the user.
The situation is even worse when service providers handle value transfers. Users need to go through a problematic KYC process that threatens privacy. On the other hand, it relies on complex systems to manage user information. The lack of a true digital identity creates problems for value transfer. The identity and signature of business transactions need to be identified by all participants in a secure environment.
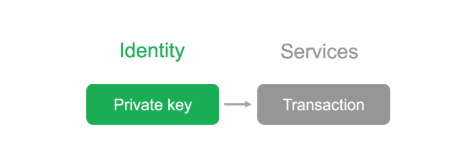 Private keys control transactions in blockchain networks
Private keys control transactions in blockchain networks
The most important innovation introduced by the blockchain network is the use of modern public key infrastructure. In shared ledger transactions, the role of the key is equivalent to identity. Shared keys are a great way to ensure identity interoperability. Participants in the transaction need only generate keys before the transaction begins. Cryptography ensures the integrity of online transactions. Therefore, no centralized party is required to manipulate network identities. The network itself acts as an identity sharing infrastructure. There are still some problems with this approach: the state of the network is controlled by the key, not by your own digital identity. Identity interoperability remains problematic: how do we verify who does what?
Autonomy to rescue
Autonomous identity means that the user controls his own identity information and identity-related data models. This is the next step in identity management. Users own and control their own identity data, instead of letting identity information spread among service providers. Data can only be shared with the user's consent if they need to know.
Autonomous identity technology relies on the blockchain network as a shared public key infrastructure. Identity holders control their own identities through the ownership of private keys. For identity data, this is like in a transaction network. Users control their own identity information, and other users can verify this information over the network.
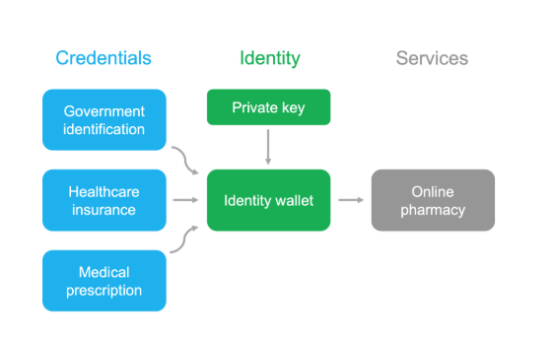
Verifiable credentials can be combined to provide much-needed trust for highly regulated online services
The ability to digitally sign and verify data is an important part of autonomous identity technology. Autonomous blockchain network enables you to have verifiable credentials linked to your identity. These credentials contain data certificates that are cryptographically signed by someone. They can represent documents or pieces of information, such as:
- Government verified name and age
- The traffic management department verified the driver's license
- Diploma accredited by the college
- Festival tickets verified by seller
Organizations can issue credentials to users just as they issue formal paper documents. Users save these digital credentials into their digital wallets as proof of different services. These services can then validate the credentials over the network without directly connecting to the original issuer. The user controls what kind of credentials he / she wants to provide without having to provide unnecessary information.
The identity information that each service uses to access the service may be different, so there is no need to use the same identity information that you use today with email or social media accounts. For some services, users do not even need to provide a real name; instead, they can provide valid citizenship. Autonomy networks also support zero-knowledge proofs. This is a form of encryption that can prove something without revealing the original information, such as proving that the user is of legal age without revealing the date of birth. Sensitive information does not spread around like traditional services, so this is a very convenient way to protect user privacy. The beauty of autonomy is that users can combine credentials from different sources and provide zero-knowledge proof. Proven combinations of information can go through the most stringent KYC processes.
Linking business processes to authentication
Linking autonomous identities to trading networks will open up a whole new world of opportunities. Because the user saves identity data in an identity wallet, he / she can become an interoperability provider of services. This is a way to communicate between services and networks without any direct API integration. We can even think of the customer as an API that processes all customer-related information while protecting data privacy.
Killer features include strong user-controlled interoperable identities and strong authentication credentials. Identity can sign transactions in a decentralized business network, and counterparties to transactions can verify the legitimacy of their identity. This has revolutionized the way today's digital business processes operate. Legally binding business transactions no longer need to rely on any particular platform or service provider. And you don't need to know who the counterparty of the transaction is, just verify the credentials provided. Of course, for business and compliance reasons, we need to trust certain parties, but it is up to the user and service provider to determine the level of trust required. Just like today's paper world.
Users can control identity data anonymously and verify only the credentials needed. Identity-linked transactions can automatically execute smart contract-based business processes, and the participants can be unknown. Even more, transactions may use optional credentials from users. For example, a user can use a power of attorney to represent the company. So this means that legally binding business processes can be programmed directly between companies. We are not talking about personal digital identities, but digital identities of companies or any other representative entities. No third party is required to provide trust and interoperability services.
Due to over-regulation, the financial and medical fields have been regarded as one of the most complex digital fields. Identity authentication can be costly and risky, as every organization is required to replicate the verification process at a high level. In these isolated environments, interactions between business processes seem to be a burden, not an opportunity. The impact of the new decentralized identity and business networks on these sectors will be huge. Strict privacy requirements, coupled with a multi-participation process, may become easier to implement.
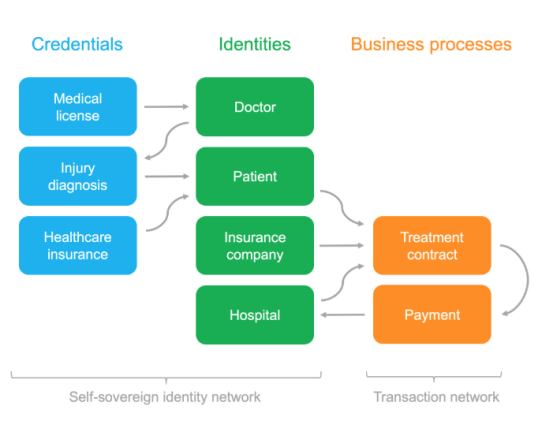
Example:
Marty's knee was injured and he went to the doctor. The doctor wrote an injury diagnosis to Marty, telling Marty that he needed to go to the hospital for knee surgery. Marty began signing treatment contracts with selected hospitals and his insurance company. First, hospitals and insurance companies need to verify the diagnosis and doctor's medical license. The insurance company also verified that the medical insurance purchased by Marty covers the diagnosis and treatment of the selected hospital. After that, the parties signed a treatment contract. The treatment contract allows the insurance company to pay the hospital directly based on the treatment provided by the hospital.
Because the customer is in the middle of the process, the network environment becomes frictionless and efficient. Decentralized networks are devouring some business services, just as the social media industry is devouring the advertising industry. Finally, and importantly, these networks are also well-suited to replace current social media platforms.
Original: https://medium.com/@pekkakaipio/best-of-both-worlds-identity-based-blockchain-transactions-66d7d054a7b2
Source (translated): https://first.vip/shareNews?id=2648&uid=1
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- 2020 Central Bank Working Conference: Continue to steadily advance the development of fiat digital currencies
- SAFE lays out work in 2020: supports new business formats, and promotes the construction of cross-border financial blockchain service platforms
- Filecoin Ultimate Guide: An Overview of How It Works, Parsing Protocols, and Possible Improvements
- Bitcoin 12th year: building tools for the future in the "chaotic era"
- One week in review | Ethereum implements "Muel Glacier" upgrade; Bitmain launches personnel optimization plan
- Why are these 7 areas of blockchain worthy of attention in 2020? Pantera partner Paul Veradittakit shares his views
- Securities Times: The most significant application of China's securities industry in blockchain technology is the promotion of ABS business