Analysis | Ethereum's expansion problems and solutions
Ethereum developers have long recognized that Ethereum network expansion is a topic worth exploring and investing. However, until the end of 2017, the scalability issue began to emerge: a decentralized application (dApp) called CryptoKitties created a lot of traffic, causing network latency. In addition, the price of gas (the cost of running each operation in the Ethereum blockchain contract) has soared as users compete to conduct transaction verification.
Although this story has now been over-reported and consumed, the CryptoKitties event does reveal a reality: the current state of capacity of the Ethereum network may not be ready for the huge traffic that a successful dApp brings. The slowness and cost instability make people respect the Ethereum platform and decentralized applications. DApp developers are working on the first applications that can be truly adopted, so developers must continue to overcome blockchain expansion issues.
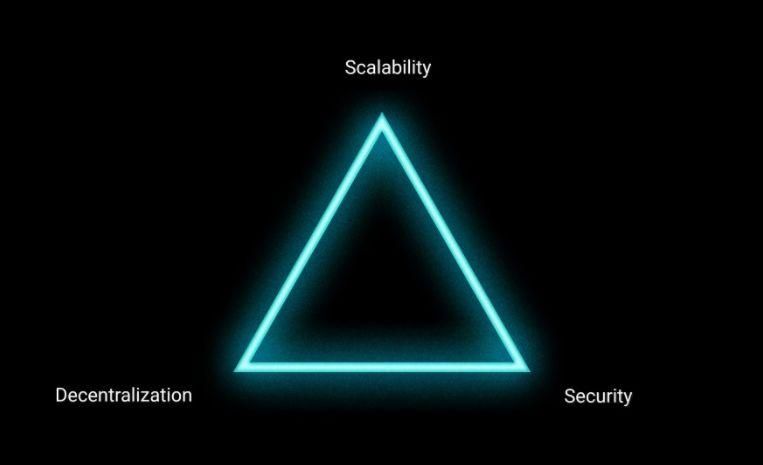
Capacity expansion solutions face "three yuan paradox"
- Why does Walmart need a "Walmart Coin" cryptocurrency?
- Comment: Bitcoin market leading rate will reach 80%, the era of altcoin and hard fork coins has ended
- The first anniversary of Shenzhen blockchain electronic invoices: nearly 6 million invoices, amounting to 3.9 billion yuan
Figure source ConsenSys
- In theory, the use of tokens is one of the solutions to the expansion problem. This solution abandons the idea that all transactions take place on a blockchain, adopting a pattern in which multiple tokens coexist but run on separate blockchains. Capacity expansion is achieved by distributing the operating pressure to other blockchains. However, as the number of nodes in each blockchain will decrease, the blockchain will be more vulnerable to attack or fraud. Therefore, the use of token solutions to balance decentralization and scalability, but the security is stretched.
- Expanding block capacity is another theoretical solution to the problem of scalability. If the capacity of each block increases, all nodes can still run various operations, but can accommodate more transactions at the same time. However, as block capacity increases, higher costs are required to package transactions, which is unaffordable for many miners. This may cause the network to be controlled by some supercomputers in the future because they have enough resources to verify each block. From this point of view, increasing the block capacity can ensure security and scalability, but significantly reduces the degree of decentralization of the network.
Indeed, at the beginning of the development of the blockchain, our focus is mainly on security and decentralization. Therefore, the biggest obstacle to achieving scalability is that each node needs to handle each transaction in person. Even with absolute security and decentralization, the system has not reserved much space for a scalability solution. Then the question is coming, how do we expand the Ethereum without affecting the premise of security and decentralization.
There are currently four protocols under development to address scalability issues, namely sharding, Plasma, and lightning networks. As for the fourth protocol, Casper is more widely available, but still for Ethereum and even others. The blockchain network provides a scalability reference.
Fragment Sharding
Sharding allows nodes to operate in parallel at the same time, which increases the transaction throughput per second for the entire blockchain. Under the fragmentation scheme, the Ethereum network can be divided into multiple groups of nodes. Each set of nodes constitutes a slice, and each slice handles all transactions within the group. This allows each shard to process different transactions simultaneously.
Within each shard, some nodes act as "collators", periodically creating "collations," or a collection of information about the shard. Each collation will include the following information:
1. The fragmentation information of the collaboration;
2. Information on the status of the fragment before the transaction is completed;
3. Information on the status of the slice after the transaction is completed;
4. 2/3 summarize the person's digital signature to verify the information in the collation.
In the network, the summary information in each shard is integrated into a single block and then added to the Ethereum blockchain. That is, the sharding technique allows the node to combine and process the transaction, but only the summary information is added to the blockchain. Assuming there are 10 shards, each shard handles 5 transactions, then the block in the next blockchain contains 50 transaction information, and the node is no longer required to process the 50 transactions in order.
But the sharding technique is accompanied by two problems. First, each shard must have enough nodes to ensure the security of the network. If there are too few nodes, then 2/3 of the aggregators are likely to collude, resulting in malicious behavior. Second, the transaction between two shards is very difficult. If there is only one shard, there will be no similar problem because it represents the entire blockchain. The current method also requires detailed receipts and proofs.
Plasma
With Plasma, all calculations in the sub-chain are boosted by the root chain, but the root chain only needs to be calculated personally when a dispute arises in a sub-chain. This approach allows all transaction information on the blockchain to be shared by the sub-chains to optimize speed and efficiency. Based on the wishes of the child chain nodes, they can withdraw the transaction information and output the transaction record to the root chain.
This program has a unique advantage. Each Plasma chain has its own standards and specifications, which means that different sub-chains can support transactions for different needs (such as privacy), while all transactions are in the same, secure environment.
Lightning network
Lightning networks are useful for regular and regular payments . For example, users need to pay a company for $10 a week to get a service, or to make regular purchases at a supermarket. Recording and verifying such transactions between two nodes without mobilizing the nodes in the entire blockchain, so that the root chain can free up a lot of space.
At any time, the participants in the status channel can choose to close the transaction, but the final result of all transactions is recorded on the root chain and then included in the next block. This means that if you pay $10 a week for a year, the final transaction record in the block is $520 instead of 52 $10.
Thunderbolt network solutions have advantages and disadvantages. The problem is that nodes can only communicate with their "neighbors", that is, if a state channel is opened between node A and node B, node B and node C also have a status channel before, and A cannot directly send funds to C. But trading in this channel can prevent funds from being stolen or locked. Although A cannot transfer money directly to C, B can be regarded as a “middleman”, and B cannot be stolen due to restrictions imposed by A and C.
The main advantage of the lightning network is that it can greatly reduce the cost of the transaction. Because the transactions that occur under the chain between nodes are less costly than transactions on the root chain.
Casper
In proof of interest (PoS), the verifier replaces the miner's verification of the block in the blockchain (verified to replace the mining). Verifiers verify the cost of resources required to calculate a problem by validating assets on a block. The block with the highest amount of pledge will be verified and added to the blockchain.
Essentially, the verifier will be added to the blockchain by locking the funds in the contract and will be rewarded until the next block is added and proved to be the correct block. If the verifier performs an improper act, the funds they pledge will be fined.
Conceptually, the PoW to PoS transition can prevent blockchains from being maliciously attacked. Under the PoW algorithm, a failed blockchain attack only causes the attacker to lose time and resource costs. However, under the PoS algorithm, a failed attack directly leads to economic losses, because the funds they pledge in the wrong block will be immediately fined.
The final deployment of Casper will be based on two iterations of the protocol: Casper FFG and Casper CBC. These two protocols will be deployed on the Ethereum for network testing PoS and identify potential problems before the algorithm transition is complete.
Casper FFG
(Casper the Friendly Finality Gadget)
Casper CBC
So how does CBC adapt to the problems that may arise in the process? This requires a protocol called “ideal adversary” to make assumptions, mistakes, and possible future issues for the CBC.
The Casper family of agreements includes not only expansion issues, but also energy conservation and security considerations. However, as the energy loss required to increase the block is reduced, it will be more challenging to achieve network expansion. Although Casper is not specifically designed for capacity expansion, it still contributes positively to the traffic carrying capacity of the network.
Conclusion
Reprinted please specify: ECN Ethereum China
WeChat public number: ETH Chinese network
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Analysis of the trend of gold and bitcoin in the first half of 2019 – Who is the king of risk?
- Samsung's blockchain ambition: from bystanders to layout people (with Samsung blockchain events)
- The situation is getting more favorable to the market, why the BTC does not rise and fall
- Standard Chartered Ventures Launches Mainland Business: Investment Blockchain Project
- MoneyGram CEO Tan Ruibo xRapid: It’s really cool to settle the currency in a few seconds!
- BTC is blocked from retracing, short-term into break time
- The blockchain star project of Top50, which is fundraising, is still alive?




