Bitcoin extorted new tricks, Canon SLR was hacked, and White Hat used a hole to redeem the photo.
Including the hacking of computer ransom bitcoin events in the early years, everyone may feel that these messages are too far away or too small, and they will pass.
But if I say that you often take this item that you are playing with and very cherished, is it possible to recruit?
The latest potential victim of Bitcoin: SLR camera
According to the National Enquiry Report, a group of security researchers successfully exploited the vulnerability of the Canon EOS 80D digital camera and redeemed the camera owner's photo with Bitcoin. (Report original: https://www.theinquirer.net/inquirer/news/3080359/canon-dslr-ransomware )
- Soul torture: What is missing in the blockchain?
- A brief history of distributed computing: the development path from mainframe and time-sharing systems to DApp
- The long-awaited Bitcoin competitors of the central bank are "almost" coming.
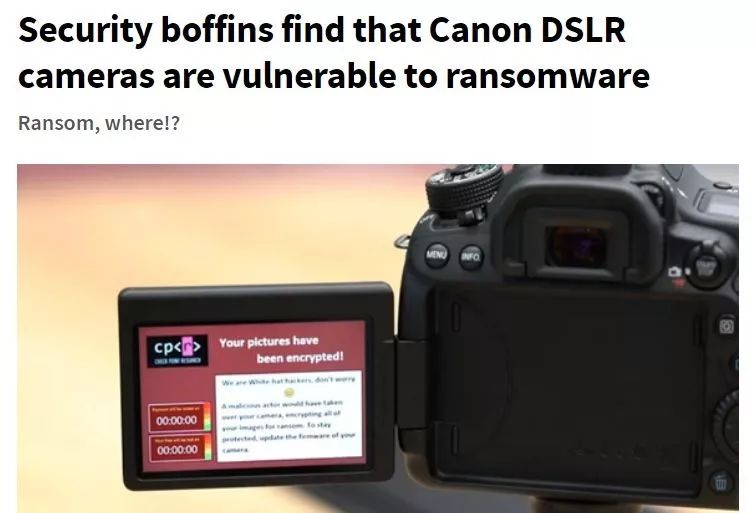
note!
This operation may open the door to hackers.
With the development of technology, most cameras now support the use of WiFi connections to transfer pictures, eliminating the need to forget to bring a card reader or USB.
This feature is called PTP/IP (Internet Picture Transfer Protocol). However, this feature is convenient for users and is also prone to security risks. Because you can enjoy the WiFi transmission and never use USB transmission, you may be targeted by hackers. Because the image transmission based on the Internet, it is a valuable attack carrier for hackers.
Why is that?
As the inspection study pointed out, PTP is an unauthenticated protocol that can support dozens of complex commands. Therefore, it may be abused by hackers to inject malicious code into unsuspecting cameras.
In this particular vulnerability, our researchers were able to set up a ransomware program via WiFi to encrypt the camera's storage.
When the attack starts, there will be only one extortion message on the camera screen asking the owner to exchange photos with Bitcoin, otherwise it will be destroyed or published for other purposes. (Interested friends can check out the hacking practice on YouTube https://www.youtube.com/watch?v=75fVog7MKgg )

But everyone doesn't have to worry too much. Although this may seem a little scary, research shows that the possibility of hackers successfully exploiting this particular vulnerability is very embarrassing.
In general, if the photographer does not have a way, it will not use WiFi for picture transmission. After all, the WiFi transmission picture is directly slower than the SD card and the WiFi transmission speed is not slow.
On the other hand, the researchers told Canon about the vulnerability. Canon's response speed is still very fast. A camera firmware patch was released last week and a security warning notice was issued. However, it is unclear whether other brands of cameras will have this vulnerability?
In the same way, various emerging technologies are helping everyone to improve, but at the same time, they hope to avoid bringing new hidden dangers to everyone, and immediately appear harmful loopholes, and they can also find and promptly remedy them.
Finishing | Carol
Produced | Blockchain Base Camp (blockchain_camp)
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Who is the best salesman in the cryptocurrency market?
- Dialogue Wang Yuanming: From Web1.0 to Web3.0, what have we experienced?
- The central bank’s digital renminbi is coming out, and the Bitcoin Librae currency is going to be cool?
- Repurchase tokens, concentrate on destruction, do you accept such a "retirement ceremony"?
- QKL123 market analysis | short-term change is imminent, uncertainty increases (0813)
- Nakamoto's curse: There is no mainstream currency, only bitcoin and the altcoin that will disappear in the end?
- How to find "dead loyalty powder" in the blockchain project






