Data sharing empowers AI-driven networks based on blockchain technology, taking mobile network operator MNO as an example
Author: Sachin Devmurari
Translation: Huohuo Sauce
Source: Blockchain Base Camp
Editor's note: The original title was "Enable AI-Driven Networks for Data Sharing Based on Blockchain Technology."
- Microsoft: All in blockchain, BaaS services overpowering tech giants such as Alibaba Cloud and Amazon
- Will the NFT that has tripled in three years become the meme in 2020?
- Hong Kong wants to increase cryptocurrency laundering supervision, the world will act in concert to impact the value of cryptocurrency "black market circulation"
Recent advances in artificial intelligence and machine learning algorithms have provided momentum for network automation. Recently, mobile network operators (MNOs) are using artificial intelligence-based modules to automate networks by distributing data authorized in their leased / owned areas.
The emergence of 5G networks has gradually disrupted the traditional network paradigm. Super heterogeneous networks are needed to coordinate and organize various types of network base stations, such as macro base stations, micro base stations, home base stations (Femto), pico base stations (pico), and management of large-scale multiple input Output (MIMO), millimeter wave, or device-to-device (D2D) communication.
However, the problem is that data access is limited for several MNOs. Blockchain-based data sharing can change this situation and enhance the performance of artificial intelligence-driven network systems.

What is an AI-driven network?
Artificial intelligence is not new to us, but earlier versions of artificial intelligence algorithms were limited to certain specific applications, and these applications were limited to the limited computing power of the system.
Then, as artificial intelligence became more applicable, network operators began to explore AI-driven network systems to better organize and distribute networks.
The basic idea is as follows: first, use the clustering method to obtain the optimal partition of the network, and then use the neural network calculation algorithm to obtain the optimal traffic routing. And, with the development of data-driven intelligence, algorithms can now learn by accessing large amounts of data.
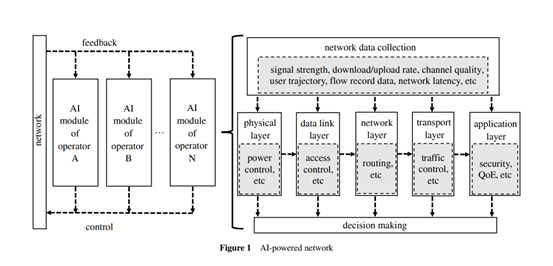 Source: AI-powered networks
Source: AI-powered networks

What is blockchain-based data sharing?
With the advent of smart contracts, blockchain-based technologies have become very attractive to many businesses. The basic problem of the early blockchain was verification. Many experts believe that the democratization of data in blockchain-based data sharing is threatening data security.
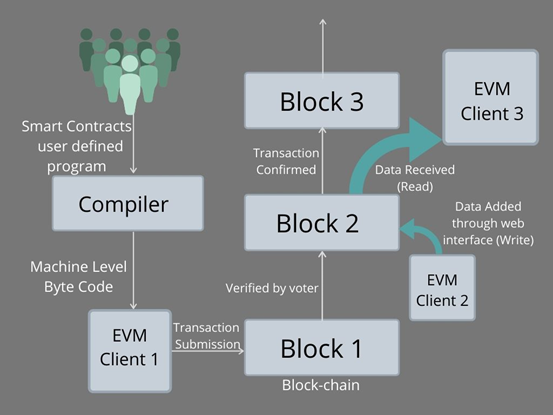
In addition, a third client can read verified data through the blockchain block. As a result, smart contracts are more democratized and data can be verified through a verification system.
Businesses generally prefer licensed smart contracts over public smart contracts because the latter are less secure than licensed smart contracts.

Blockchain-based data sharing in AI-driven networks
- Blockchain-based data sharing uses AI-driven network smart contracts. The system is divided into three layers.
- User layer-participants in the system (MNO)
- System management layer-contains the following components:
- MSP (Member Services)
- Consensus Nodes
- Verifier
- Gatekeeper
- DataChain
- BehaviorChain
- Data storage layer-cloud-based data storage

Important part of the system layer
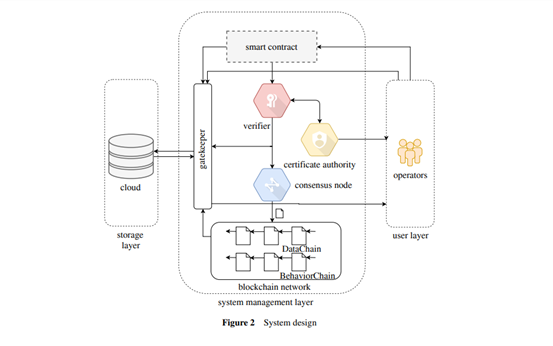
Source: System Design
1. MSP (Member Services)
Member services are responsible for issuing membership certificates, authorizing and registering system participants.
It holds a root certificate like the master key and issues a second key (Cu) certificate to registered members. Whenever a new member joins the system, a "Cu" key is provided as a new certificate. The private key is used for identity registration and verification of each member.
In our case, the members are different mobile network operators (MNOs). The identification of each MNO requires a specific certificate provided by the MSP layer.
2. Verifier:
The validator uses the "Cu" certificate issued by MSP for any user calling the API. The application program interface acts as an intermediary between the system and the user. Specific GUIs turn their application ideas into reality.
3. Consensus Nodes:
The consensus node is responsible for implementing the AI algorithm. Here we integrate the AI algorithm in the blockchain-based data sharing system.
Consensus is used to ensure the consistency of the ledger. Consensus algorithms involve endorsing transactions, where transactions involve compiling raw data into bytecode for the blockchain.
In addition, the order in which transactions are uploaded to the blockchain needs to be determined. During the transaction endorsement process, if both blockchain nodes want to upload transactions to the blockchain, they need to use smart contracts to determine who confirms the transaction.
The method used by Hyperledger Fabric is to sort the transactions in the system. Here, transactions represent patterns and data usage behavior.
4. Gatekeeper:
The gatekeeper is the bridge between the data layer and the system. Controlling access to the data layer through smart contracts helps maintain the correct data flow and the system's correct access to the original data.
Blockchain (BlockChains): Share its network infrastructure and data access rights to reduce the complexity of expenses and operations.
However, there are also competition and trust issues with multiple MNOs in a real environment, and these issues can be reduced through certificate authorities. In order to authorize higher certificates on shared data, we can use the DataChain and BehaviorChain for the alliance chain similar to the super ledger structure.
The "super ledger" is actually an open source ledger with a modular architecture, which can quickly use components such as consensus nodes and MSPs in the system.
The data chain provides control over data access, and the behavior chain is used to record each piece of data. Therefore, combined, these two blockchains provide data authorization, control of data, and auditing of large amounts of data.

data permission
In any system that allows access to raw data, data permissions are a primary consideration. Data permissions can be divided into four different levels based on their risk factors and other security parameters.
- Data is only visible to the user (L0)
- Collective use of data without exposing raw data (L1)
- Raw data is accessible to definitions and authorized parties (L2)
- Data is public (L3)
Note: Users can set their own data permission levels for complete permission control

In order to speed up the process of data sharing through fast user query and data access, the system specially designed a data structure. Let's first look at how transactions occur in the data chain.
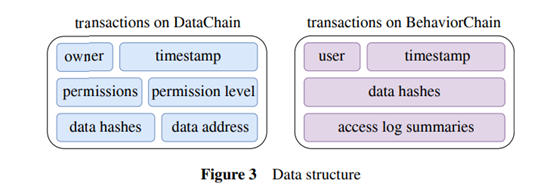
Source: Data Structure
The transactions in the data chain mainly include the following components:
Data owner
Timestamp of transactions that occurred in the block
Data permission levels
Level L2 coded as a hash table
Data hashing-maintain data integrity
Data-to-data link pointer
The transactions in the behavior chain mainly include the following components:
Users requesting access to the data
· Timestamp of when data was accessed.
Data address
Access log summary

How is the system implemented?
Member management
2) After the user is authenticated, a digital certificate is issued to the new user for identification.
Data collection
There are two basic types of data, one related to user privacy and the other not related to user privacy.
The contract uses a validator to verify the identity of the data provider.
The contract then identifies raw data related to user privacy, such as user ID and other data. Once identified, it will be encrypted using an asymmetric key.
The contract sends data to the gatekeeper, which stores the data in the cloud and returns the data address. The contract initiates a data transaction request based on the data address, as shown in the following figure:
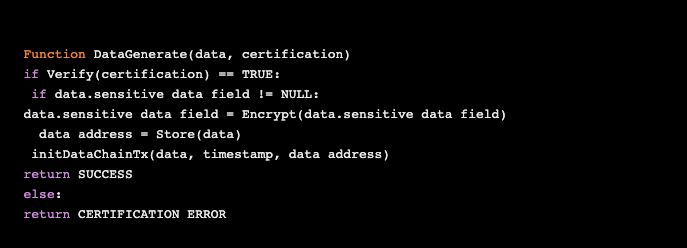
This is the pseudocode for the data generation contract.
Data generation contract: https://link.springer.com/article/10.1007/s41650-018-0024-3
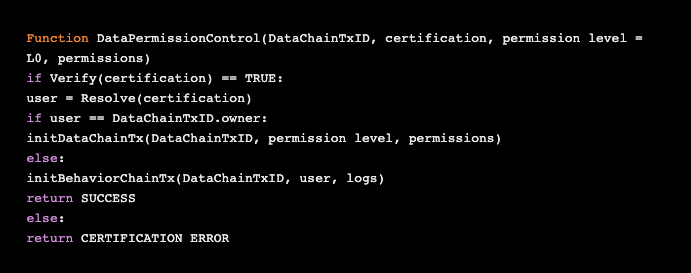
3. Data permission level
As we have already discussed, users can define different data permission levels for others to access data owned by the user. Users can assign data permissions using the following code:
4. Data sharing
If you need to perform data calculations without exposing the original data, you need to form an agency composed of other validators and the government as a potential participant, and apply the algorithm together to avoid malicious access to the data.
Data requests appear with digital certificates and digital signatures.
· The contract verifies the legitimacy of the data request through a validator.
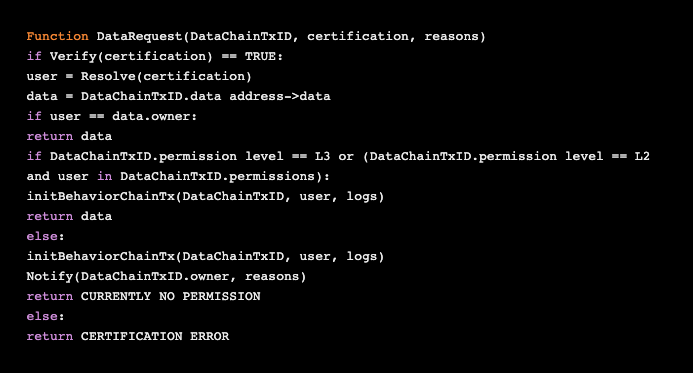
5. Data review
Each data provider (MNO) receives regular data reports. Any malicious activity or data misuse can be identified through authentication in the system.
The user has full control over the data, so can the data be withdrawn in any malicious activity?

in conclusion
With the advent of 5G networks, an organized and optimal AI-driven network can help MNOs and even enterprises to complete the required data requirements and data intensity.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- CFTC Technical Advisory Committee Holds Public Meeting to Discuss Stablecoin
- Interview with Chen Weigang, Former Vice President of the Banking and Insurance Regulatory Commission: Digital currency trading must be cracked down
- We sorted out 40 "running road" cryptocurrency exchanges, all of which share these common routines
- Analysts: Five reasons will drive Bitcoin to a bull market in 2020
- Depth | A Comprehensive Interpretation of Lightning Loans: Why Will Lightning Attacks Become the New Normal?
- Research Report | January 2020 Digital Asset Exchange Industry Report
- Blockchain under epidemic situation: Revitalize "IOU" to help small and micro enterprises loan






