DeFi development is limited, how to break the next stage?
Author: Hou Zhengpeng
Translation: Yang Zhiang
Source: Blockchain Outpost
Lead:
Blockchain transparency has both advantages and disadvantages. The author predicts that the next wave of DeFi is to explore the privacy protection mechanism combined with the distributed network, while taking advantage of the advantages of blockchain technology to ensure the adaptability to the growing regulatory regulations worldwide.
- ECB President promotes development of central bank digital currency
- DeFi cannibalize PoS security? Increase opportunity cost and reduce risk
- IRS: Cryptocurrency transactions do not report taxes or will pay a high price, tax evaders may face fines of up to $ 250,000
Since the advent of the dark horse in 2009, Bitcoin has raised the banner of the blockchain, and many new technologies have emerged in the blockchain field, which has led to countless applications of decentralized infrastructure. Although the comprehensive application of many technologies shows great potential, decentralized finance (DeFi) has quickly become one of the most well-invested market segments. By using a decentralized architecture to mimic traditional financial instruments, cryptographic enthusiasts around the world expect to build a currency system that is not controlled by an intermediate medium. However, the transparency of the public chain network is still an obstacle to the widespread promotion of the blockchain.
Best DeFi Product (Source: DeFi Prime)
Privacy and regulatory pressure
Although the industry is flooded with countless rhetoric, successfully developing and implementing DeFi solutions is a real and daunting task. Despite the hardships, a large number of companies from all walks of life still unswervingly pursue economic transformation. According to Deloitte's 2019 Global Blockchain Survey, 53% of organizations rank blockchain technology as a key priority , and 83% of organizations remain focused on the convincing use cases of blockchain technology.
However, 50% of companies consider privacy-related regulations to remain worrying, and blockchain transparency has both advantages and disadvantages. In order to meet this challenge, some insiders have begun to explore privacy protection mechanisms combined with distributed networks. These solutions are designed to take advantage of the advantages of blockchain technology, while also ensuring adaptation to this growing and relevant regulatory regulation worldwide.
However, before properly considering the impact of these privacy protocols, it is necessary to understand the basic differences between a decentralized framework and the existing client-server infrastructure.
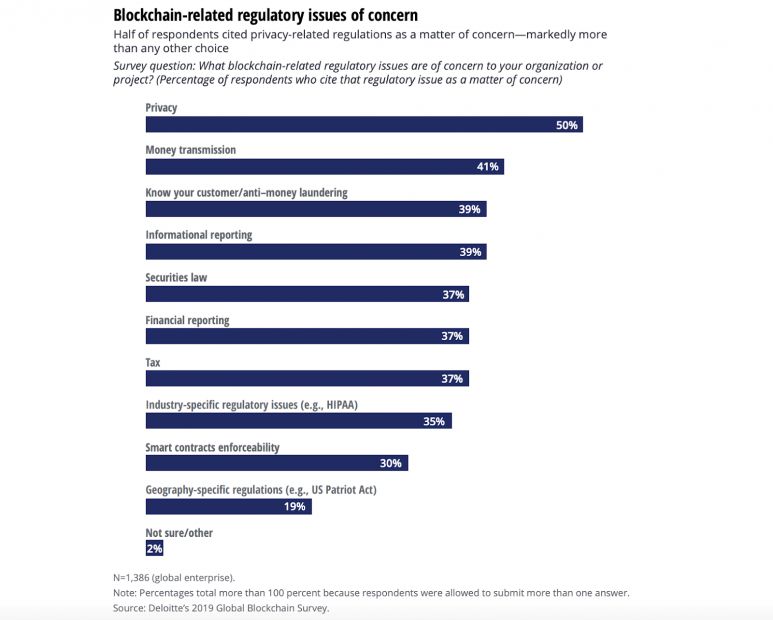
Blockchain-related regulatory issues deserve attention (Source: Deloitte Global Blockchain Survey 2019)
How does a decentralized network improve security?
Although DeFi continues to generate a large number of related news reports and investments, it is often the basic framework that is not often noticed. In addition to being able to bypass monopoly intermediaries, blockchain technology has several security advantages over traditional client-server networks.
In the overall architecture, the client-server controls the entire network through a centralized server, that is, all other network participants are clients. In contrast, the blockchain runs the network as a peer-to-peer (P2P) platform, which allows each network participant to act as a client or server.
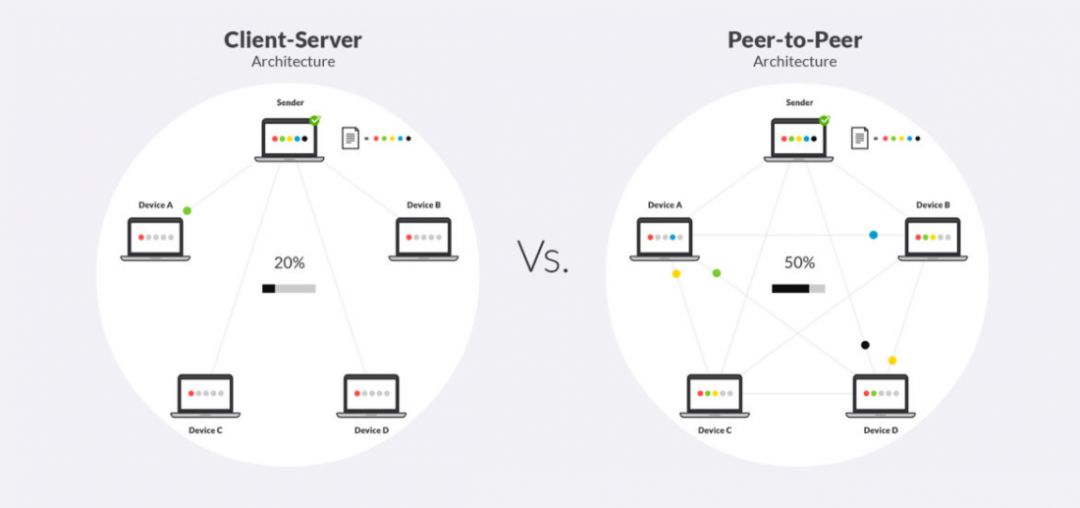
Client-server and peer-to-peer architecture (Source: Resilio)
As a result of this structure, there is a single point of failure when the client-server network is running. In other words, such networks are still vulnerable to hacking and technical failures, and these threats can cause the entire system to be disrupted. In contrast, blockchain networks rely on a distributed network of computers (nodes) holding copies of the same information. In this case, the failure of one device has little effect on the overall network function, because there are hundreds of other machines that continue to operate normally.
Although long considered safe, persistent data breaches and service interruptions have become synonymous with client-server networks to some extent. Since the Cambridge Analytica scandal, consumers have grown increasingly skeptical about the organizations that process their personal information.
Data leak on client-server network
Although it can be said that the consumers affected are the biggest losses after the data breach. However, many companies also suffer losses from centralized server attacks. According to a 2019 data breach loss report from IBM, the average cost of a data breach in a U.S. company has increased from $ 3.54 million in 2006 to $ 81.19 million in 2019, which means an increase of 130% in 14 years. Unfortunately, cybersecurity breaches will only increase, especially in the financial services sector.
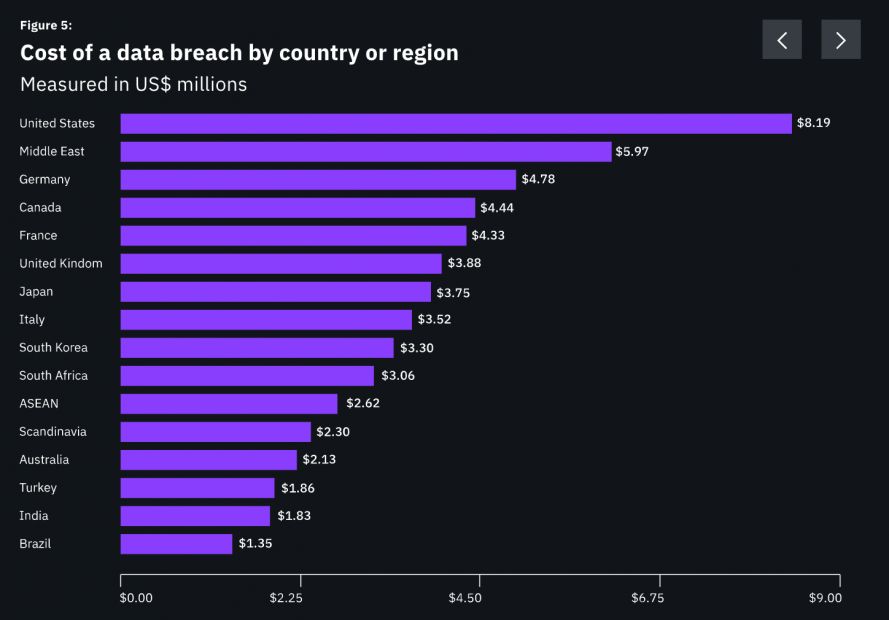
Costs of data breaches by country (Source: IBM Security-Data Loss Loss Report 2019)
For example, in March of this year, a hacker hacked into Capital One's app and illegally obtained consumer and small business credit card information dating back to 2005. In another recent case, First American Financial Corp. also suffered a cyber breach, which involved leaking approximately 885 million personal and financial records dating back to 2003. In Canada, the Desjardins Group unknowingly leaked the personal information of up to 2.7 million members, including their home addresses, names, email addresses, and social security numbers.
Naturally, these ongoing data breaches support a decentralized financial alternative. However, existing regulations must also guide the implementation of potential applications.
Privacy layering on the blockchain network
As blockchain technology and cryptocurrencies occupy a place in our daily lives, governments in various countries have also continuously issued appropriate regulatory regulations in response. Many recent privacy-related regulations, such as the European Union ’s General Data Protection Regulation (GDPR), California ’s California Consumer Protection Act (CCPA), and Brazil ’s General Regulation on Personal Information Protection (LGPD) Data "storage and transmission.
When applying privacy-related regulations to blockchain platforms, these intentionally used broad languages can cause problems. Because not all blockchains are the same.For example, blockchains are also divided into private and public chains, and different blockchains will use different levels of encryption. The interpretation of compliance with these privacy regulations is still one. A very challenging thing. Therefore, companies wishing to comply with regulations must conduct extensive and detailed investigations in advance. Through these investigations, these companies can ensure the implementation of appropriate privacy protection mechanisms and ensure the future expansion of their business.
In the blockchain ecosystem, several privacy-related implementation measures have been put into use. However, the zk-SNARKs protocol and its subsequent iterative development versions have been leading the way.
Concise non-interactive zero-knowledge knowledge proof zk-SNARKS
zk-SNARKS, also known as "concise non-interactive zero-knowledge knowledge proof", represents a cryptographic proof structure in which a party (certifier) can prove that it owns certain information, but does not need to submit The other party (verifier) disclosed the specific content of the information, that is, the certification process does not require any interaction between the two.
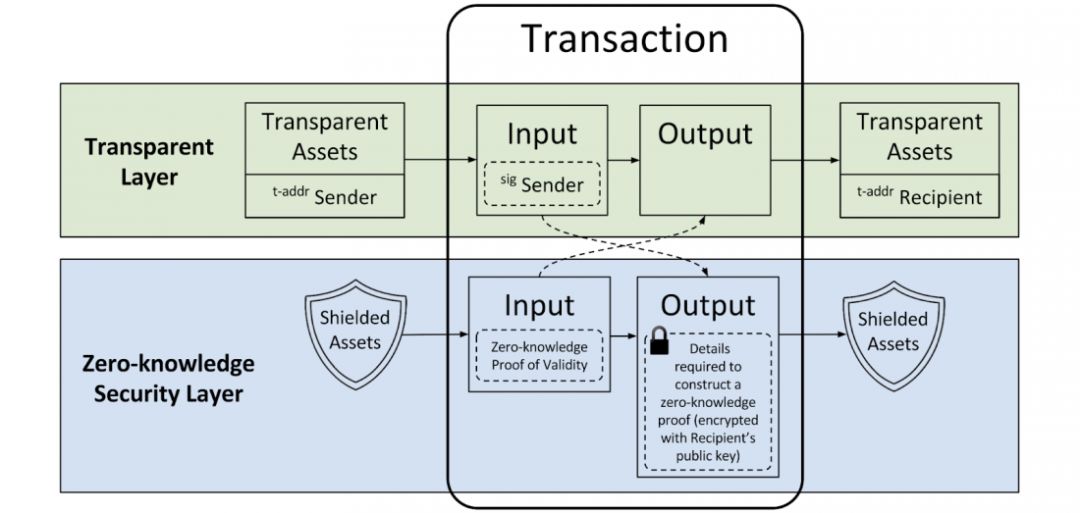
Concise non-interactive zero-knowledge knowledge proof zk-SNARKS (Source: Coindoo)
Compared with the earlier iterative version of the zk-SNARKs protocol, the constant-level trusted setting of the zk-SNARKs protocol, also known as the zk-ConSNARKS protocol, has significant advantages. The early zk-SNARKs protocol required a lot of computing resources to deploy. In comparison, the zk-ConSNARKS protocol is much more efficient. In the eyes of developers who grasp the trend of privacy protection, this makes blockchain technology more efficient. Attractive.
Privacy and Decentralized Finance
As the DeFi platform continues to expand rapidly, the impact of regulation will surely unswervingly promote the introduction of more robust privacy protocols. Although the newly introduced regulatory rules deliberately set a broader definition, enterprises can take decisive action to resolutely support user safety. By combining the inherent security of the decentralized technology with the privacy protection mechanism, the new project can challenge the status of existing industries, promote the growth of these industries, and promote the widespread application of blockchain technology.
About the author: Hou Zhengpeng, the founder of Suterusu, is currently the CEO of the company. A senior expert in the open source field, he has more than ten years of successful experience in contributing and establishing an open source community. Previously, he worked for companies such as Ubuntu and is now involved in the blockchain industry. He focuses on open source project development, the Internet of Things and cloud computing, and is a loyal believer in decentralized technology.
Original: The Next Wave of DeFi: Coupling Security and Privacy
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Perspective | Comparison of Digital Asset Trading Markets in Asia and Europe in 2020
- A major Brazilian bank announces closure of accounts on cryptocurrency exchanges
- Inventory 2019: The rise of DeFi (Decentralized Finance)
- Featured | Ethereum: Money Game View; StakerDAO — New DAO Based on Tezos Blockchain
- How is the development of overseas blockchains? We analyzed 34 blockchain companies at the 2020 CES show
- 2020 "Yield Reduction" Year, Surprise or Fright?
- "Secret" in the Cloud: Building Non-Interactive Zero-Knowledge Proofs — Exploring Zero-Knowledge Proofs Series (5)






