Depth | Inspiration from distributed intelligence brought by Ethereum 2.0
Summary
In the mobile era, the encounter of various types of intelligent terminals in distributed networks will collide with more imaginative scenarios. The architectural idea of Ethereum 2.0 beacon chain + sharding provides meaningful inspiration and opens up the imagination space of distributed intelligent networks.
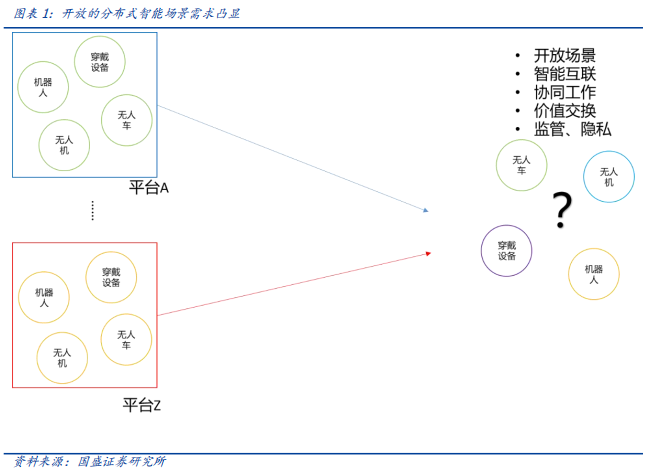
Distributed networks face more complex consensus, privacy and regulatory models, and value exchange models. In the era of 5G edge computing, considering the popularity of the Internet of Things and the improvement of real-time requirements, the working logic and management of network nodes are becoming more and more distributed and open. Distributed networks face four important issues: consensus, privacy, regulation, and value exchange. In terms of supervision, the supervision under the cloud-centric network model is more aimed at cloud platforms, and the permissions of user terminals are also fully controlled by the platform. In terms of consensus communication, cloud platform control brings obstacles to user interaction between different platforms. The behavior of distributed user terminals is highly self-organizing and scalable, and issues of privacy and supervision are particularly prominent. The biggest pain point is that the establishment of communication, data exchange, and intelligent collaboration between multiple intelligent terminals requires unified work instructions and logic, that is, a set of consensus is needed to solve the problem of "headless dragons." Value exchange may be more complicated than data information exchange, because value exchange requires a strict and consistent ledger, that is, the blockchain ledger consensus mechanism, to ensure the finality and atomicity of transaction results.
The shard chain is the core feature of the future scalability of the Ethereum 2.0 network, and the beacon chain is the backbone of the system. In the Ethereum 2.0 plan, a beacon chain scheme was proposed, and all independent and parallel shards were coordinated through the Casper protocol (casper is the consensus layer of the entire system, responsible for managing the verifier, implementing rewards and punishments) through the proof of stake Shard Chains (equivalent to edge clouds), use Crosslink as the anchor point of each shard to achieve cross-shard communication and provide final deterministic guarantee for shards. Sharding is similar to the current serial working method of block tasks in Bitcoin and Ethereum. This processing method is very similar to the working mode of edge computing or logistics warehouse nodes. The throughput and efficiency of the network are very suitable for open distributed networks. The beacon chain can be understood as the consensus mechanism of the sharding system-providing the sharding system with a consensus mechanism for cross-slice communication, protocol, and value exchange. One of the functions undertaken by the beacon chain is to allow validators to participate in the pledge system and replace the role of miner to become the builder of the chain, so as to manage and serve the validator well. The other function of the beacon chain is to store the index of the shard status-the beacon chain does not need to store the specific transaction information of the shard.
The idea of sharding is similar to edge computing + asynchronous parallel networks, providing advantages such as consensus, ledger value, privacy protection, and friendly supervision for distributed networks. On the one hand, sharding solves the problem of networking of scattered nodes. Edge computing terminals can easily perform terminal networking according to requirements. The consensus rules within the sharding provide a basic platform for the intelligent self-organization of nodes within the sharding. Asynchronous parallel mechanism brings sufficient performance to the network for distributed and scalability. On the other hand, the beacon chain provides a central mechanism for the entire network consensus and cross-chip communication. There is another layer that is more interesting. The beacon chain provides the basis for the separation of supervision and fragmentation services. Open interfaces without interfering with the data privacy issues of the shard's internal business. In addition to information communication, the system can use the distributed ledger of the blockchain to realize value transfer between terminals. This is to introduce financial attributes to the system, such as payment, digitization of assets, and even transactions.
- Babbitt Column | Deng Jianpeng: The "gaseous" trend of blockchain challenges the government's supervision ability, and the rule of law supervision requires great wisdom
- When Tesla becomes a Bitcoin node, is it reliable?
- Quick Tour of Ethereum 2.0 Update (7): Phase 1.5 Means Ethereum Says Goodbye to PoW
Investment suggestion : The main investment lines include: IoT module suppliers: China Telecom, China Mobile, Guanghetong, Mega Intelligent, Youfang Technology, Gaoxin, China Mobile (839956.OC), Lierda ( 832149.OC), etc .; government affairs scene: Yi Jian shares, Donggang shares, Annie shares, Yuanguang Software, Huayu Software, Zhejiang Commercial Bank; Operator: China Unicom.
Risk Warning : The business model of the blockchain has fallen short of expectations; the development of blockchain technology has fallen short of expectations.
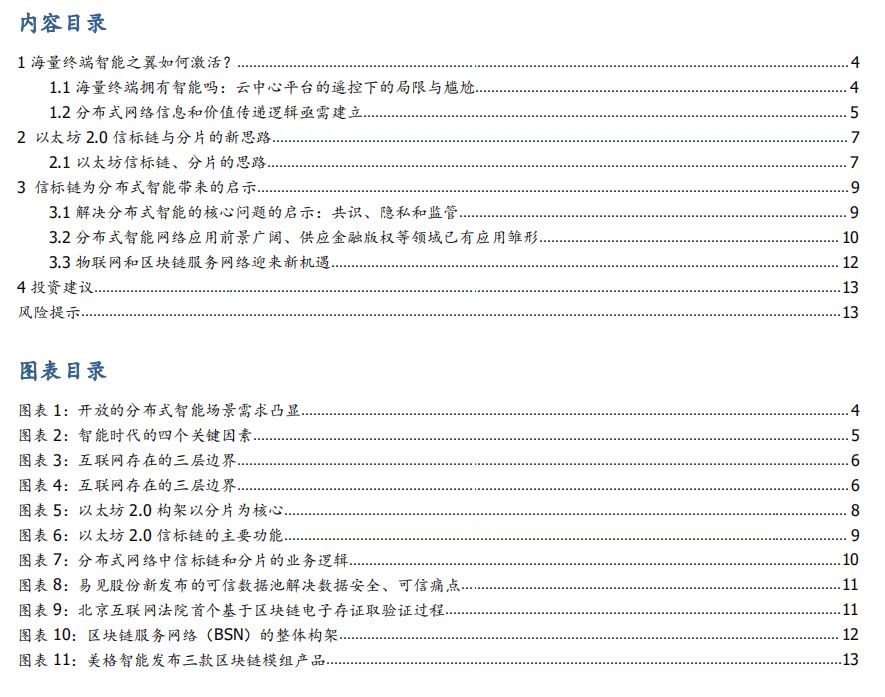
1 How to activate the intelligent wings of mass terminals?
In the future, how can mass terminals have intelligence?
Imagine that in the intelligent era, multiple driverless cars, drones, robots, or other terminals meet in a certain scenario, and there is the possibility of information data, value exchange, and even collaboration with each other. We can believe that in the mobile era, multiple devices will not be offline when they meet anywhere, but we cannot extravagant what stories can happen between smart terminals under unpredictable circumstances-they may belong to different account systems and they may not Knowing who you will meet, this is a completely open network.
However, in the era of intelligence, the importance of terminal intelligence is constantly increasing (especially with the help of edge computing and distributed AI). It cannot always rely entirely on cloud centers to provide "thinking and decision-making"; the development of AIoT is bound to promote the growing network Decentralized, terminals have higher privacy requirements and intelligent algorithms. In open scenarios, intelligent terminals may meet at any time in the physical space or network to generate exchanges. The future network is distributed and open, so we cannot accept an Alibaba driverless car driving in front of a vending machine because of the embarrassment of not being able to use WeChat payment, and in some special scenarios such as emergency situations Expectations are controlled from the same cloud platform to work together. Especially in some special and urgent scenarios, it is unacceptable that smart terminals cannot effectively “talk” and coordinate work. The requirements for more open and intelligent collaboration scenarios will become increasingly prominent.
In fact, with the development of the Internet today, there are three layers of user terminals: physical, protocol, and network boundaries. Due to the popularity of 5G and cloud computing, the physical boundary is largely not a problem-no matter where they are, as long as they can connect to the Internet, they can normally provide services through the cloud platform.
Differences in data communication protocols may lead to protocol-level exchange obstacles; and network boundaries have become increasingly prominent for the development of the Internet—the so-called network boundaries refer to the boundaries between different network protocols or more generally different network account systems. For example, various applications and apps are installed on the same phone, but different Internet applications such as WeChat and Alipay accounts cannot interact, and even basic data sharing cannot be achieved. We can further imagine that in the future intelligent world, due to the existence of network boundaries (belonging to different core vendor systems), two end users (may be robots, driverless cars, etc.) will not be able to interact at the data level. Is it smart? Entities in various fields today monopolize the data of their user systems to varying degrees, and user accounts cannot break through network boundaries to interact with data information and value, which is only controlled under the remote control of their respective cloud centers.
In a core network system with large-scale users, of course, there are intelligent application scenarios of cloud center + terminal mode, but as the privacy requirements of terminal data become higher and higher, the limitations of network boundaries will become an obstacle in the intelligent era. With the development of privacy requirements and intelligent algorithms, the terminal will inevitably develop in a direction with more autonomy, and the network will thus become decentralized and open. The distributed networking between terminals will increasingly reduce the dependence on the cloud center, and perform point-to-point communication and collaboration. After all, AIoT gives the terminal intelligence, and the value of data generated from the terminals needs to be further explored. With the development of privacy requirements and intelligent algorithms, the terminal will inevitably develop in a direction with more autonomy, and the network will thus become decentralized and open. The distributed networking between terminals will increasingly reduce the dependence on the cloud center, and perform point-to-point communication and collaboration. After all, AIoT gives the terminal intelligence, and the value of data generated from the terminals needs to be further explored.

Value exchange is also a new challenge for distributed open networks. Value exchange may be more complicated than data information exchange, because value exchange requires a strict and consistent ledger, that is, the blockchain ledger consensus mechanism, to ensure the finality and atomicity of transaction results. For more complex distributed network scenarios, the distributed ledger is undoubtedly a reliable solution. One of the goals of the birth of Bitcoin and blockchain is to deal with the issue of value transfer between distributed and open node networks. The open network depends on a set of consensus mechanisms. Therefore, we believe that distributed network intelligence needs a more open consensus mechanism. For example, how to complete the payment of the value output corresponding to the collaborative work, resource invocation and consumption between smart terminals? Especially when the terminals belong to different manufacturers, payment settlement is an issue that must be considered.
Therefore, under a set of open consensus mechanisms, the intelligent computing power, data, and value of the terminals in the distributed network can effectively exchange and collaborate.

2 New ideas for Ethereum 2.0 beacon chain and sharding
The essence of improving the performance of the blockchain lies in the improvement of consensus algorithms and a variety of auxiliary means inside and outside the chain, seeking balance in the impossible triangle. The core difference between the blockchain and the existing Internet resources (computing, storage and network) related technologies is the introduction of a decentralized distributed network. In simple terms, the current Internet is basically based on a central server (central cloud ) Centralize the scheduling and management of Internet resources. Users send and receive instructions and data through a local client. These instructions are managed and forwarded through the central platform. For example, chat information, users directly send messages to chat, messages are sent from the user to the central platform and then forwarded to the receiving users. This type of centralized operation mode is the same as that of transportation and logistics express networks-in general, most Internet applications are not point-to-point users who directly communicate data to users. At present, one of the biggest problems that public chains face is performance (expansion). Compared with centralized network systems, the processing speed of decentralized blockchains is too slow. For example, in 2018, Taobao generated 200 billion orders in the 24 hours of the Double Eleven Day. If the current processing speed of Ethereum is 3 to 4 transactions per second, it will take 1600 years to process. The slow processing speed will cause Outstanding transactions block the entire network. Therefore, if the blockchain is to be commercialized, it must maximize its performance.
Ethereum 2.0 will shift from PoW to PoS, using sharding and beacon chains to solve performance and scalability bottlenecks. Ethereum introduced smart contracts to bring the Internet into the blockchain era. It is the asset issuance function of smart contracts that directly created the big bull market in 2016-2018. As a result, the number of DApps has developed rapidly, while user activity and user experience are still at a relatively early stage, which is closely related to the basic performance of Ethereum and other blockchain public chains. According to the planning of its founding team, Ethereum's development path is divided into four stages, namely: Frontier, Frontier, Metropolis, and Serenity. Each stage will be upgraded through a hard fork, and each stage of the upgrade is to introduce more features and fix problems. Ethereum 2.0 will switch from PoW consensus mechanism to PoS consensus mechanism. The core logic is to find a new balance in the impossible triangle.
The shard chain is the core feature of the future scalability of the Ethereum 2.0 network, and the beacon chain is the backbone of the system. In the Ethereum 2.0 plan, the Beacon Chain is the central part of the entire system. Through the Proof-of-Stakes Casper protocol (Casper is the consensus layer of the entire system, responsible for managing validators, implementing rewards and punishments) and coordinating all independent parallel (Shard Chains), using Crosslink as the anchor point of each shard to achieve cross-shard communication and provide final deterministic guarantee for shards. According to the Ethereum 2.0 specification, the beacon chain will support 64 shard chains, and there will be 128 nodes on each shard chain for verification. Sharding refers to separating the data processing responsibilities of many nodes in a database (decentralized database or other types of databases), allowing simultaneous transactions, storage, and information processing. The sharding concept is completely different from the current Ethereum main chain model, which requires each full node to process and verify each transaction. It can be simply understood that the current Bitcoin or Ethereum are based on the entire network consensus-every transaction is witnessed on the entire network, and in order to improve performance, the entire network is divided into areas, each of which is independent Handle limited data services, and the communication and coordination between the shards is completed through the beacon chain, which leads to improved performance. This is similar to distributing huge ledger data to multiple servers for independent processing to improve speed, and then interconnecting and communicating between servers through a similar central traffic system (that is, a beacon chain) to ensure consensus across the entire network and a unified ledger. OK result.
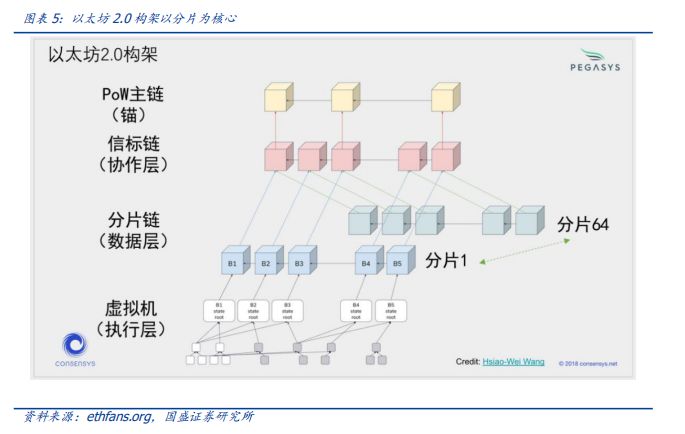
The main function and role of the beacon chain is to manage the proof-of-stake agreement for itself and all shard chains, and it is the central nerve and signal beacon of the system. The beacon chain is the backbone of the sharding system, solving the consistency of the sharding network and cross-slice communication, providing the system with final certainty. A set of consensus mechanisms is needed between the decentralized terminals within a specific shard, and the beacon chain can be understood as the consensus mechanism of the sharding system-providing the sharding system with a consensus mechanism of cross-segment communication, protocol, and value exchange . One of the functions undertaken by the beacon chain is to allow validators to participate in the pledge system and replace the role of miner to become the builder of the chain, so as to manage and serve the validator well. The other function of the beacon chain is to store the index of the shard status-the beacon chain does not need to store the specific transaction information of the shard. The current Ethereum blockchain stores data information for transactions on the entire network, but the beacon chain is different from the current Ethereum main chain. It stores a series of hash-mapped strings-the result of the hash operation is The only and irreversible change of one character of the source data will produce different hash values, but the source data cannot be inferred by the hash value.
In the beacon chain, the verifier verifies and signs the transaction, such as a transfer transaction, and then hashing it into a string. This string is stored in the beacon chain. At this time, this string represents a transaction. The benefit of transaction data is that you don't need to delve into the shard in which the transaction happened to still ensure that the transaction is valid. Once the state in the shard changes (such as a small change in the balance of an account), the verifier will report this change to the beacon chain. Therefore, the beacon chain tracks the changes of the shards in real time, and also establishes the contact and communication between the shards. Therefore, the shards can track each other's changes through the beacon chain to achieve asynchronous (that is, non-real-time) communication between the shards.
In short, the main function and role of the beacon chain is to manage the proof-of-stake agreement for itself and all shard chains, similar to the central nerve of the system, supporting and connecting the shards to work better, and specifically manages the verifiers and their rights Wait for 5 aspects. The beacon chain is like a semaphore, it directs various actions of the system, and stores a large amount of authentication data; but it is still decentralized. For example, the voting behavior of the participating verifiers is determined by the verifiers themselves. The tag chain cannot be left and right.

3 Implications of beacon chains for distributed intelligence
The idea of sharding is similar to edge computing + asynchronous parallel networks, providing consensus, ledger value, and privacy protection for distributed networks. On the one hand, sharding solves the problem of networking of decentralized nodes. Terminals in the mobile era can facilitate terminal networking according to needs. The consensus rules within the sharding provide a basic platform for intelligent self-organization of nodes within the sharding. Asynchronous parallel mechanism brings sufficient performance to the network for distributed and scalability. On the other hand, the beacon chain provides a central mechanism for the entire network consensus and cross-chip communication. There is another layer that is more interesting. The beacon chain provides the basis for the separation of supervision and fragmentation services. The beacon chain can completely provide supervision Open interfaces without interfering with the data privacy issues of the shard's internal business. In addition to information communication, the system can use distributed ledgers such as blockchain to achieve value transfer between terminals, which introduces financial attributes to the system.
The beacon chain provides the central neural function for the entire network shard, so that the decentralized network has a complete and unified consensus and business logic. Specifically, when some mobile terminals (unmanned vehicles, drones, robot terminals, etc.) perform ad hoc networking (ie, sharding) according to demand, the instruction control logic in the shards becomes the core issue (how do the terminals Communication and coordination to reach a decision), this is equivalent to the consensus mechanism of distributed networks-the command control within the shard is solved by the consensus mechanism of the shard, so as not to have no heads. Outside the shard, cross-slice communication, consensus consensus (information, value transfer), and supervision interface for all shards of the system can be deployed on the beacon chain. As shown in the following figure, distributed systems can work synchronously across the entire network, that is, tasks are serial, or asynchronous and parallel. The former is typically a variety of public blockchains (single chain), and the latter is a beacon chain + fragmentation. logic. The peer-to-peer relationship between the participating nodes of a single chain, then the supervision function is one of the nodes, and the business nodes are transparent to the supervision, which brings the problem of data privacy-for example, the Bitcoin network, all nodes are It is a witness, and all nodes can act as miners to complete a decentralized ledger; this model is more challenging for the current cloud-centric model to regulate. The working mode of beacon chain + sharding can solve this obstacle: the sharding works in a single chain mode to ensure mutual trust, peering, and consensus among participating nodes, and the unified coordination between shards is provided by the beacon chain Completed, supervision can be deployed as a node on the beacon chain. The business data inside the shard is not transparent to the supervision, but it can still be traced back to meet the supervision needs.

Sharding is more suitable for distributed and open intelligent networks, helping intelligent terminals quickly network, reach consensus, and work together. In the mobile era, decentralized network terminals can combine shards anytime and anywhere according to their needs. It is not difficult to implement physical communication within the chip, but how to control and manage the protocol layer, application layer, and even value exchange in the shard, so that when processing tasks It is very important to reach consensus and be supervised in accordance with the rules-because today's intelligence is constantly evolving, avoiding terminal evils is becoming more and more a reality. The terminal within the shard can complete internal decision-making through some kind of blockchain consensus mechanism, and the cross-slice communication and shard supervision need to be completed through the beacon chain.
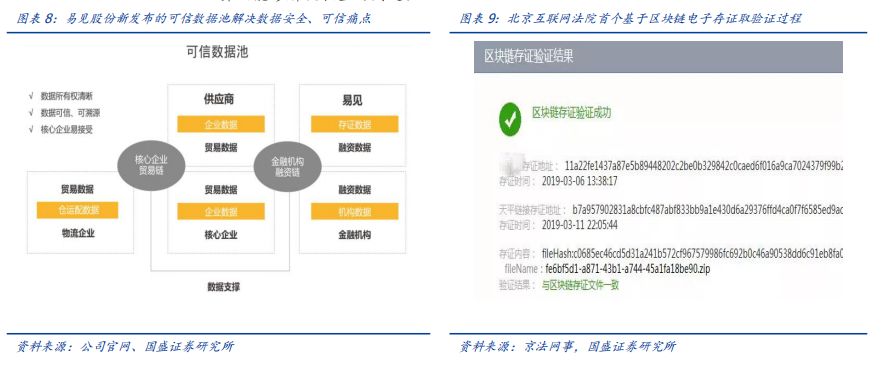
The beacon chain achieves the separation of business data and supervision, and has typical application requirements in supply chain finance. This need for separation of regulatory and business data is very common. After all, any enterprise or individual is unwilling to expose its private data to other nodes completely transparently. This kind of pain point is particularly prominent in supply chain finance-the need for confidentiality of business data is strong, and financial institutions are worried about the authenticity of business data, and the industry has proposed a solution similar to the beacon chain. The trusted data pool launched by Yijian shares is similar to the idea of the beacon chain: the enterprise uses a trusted data pool (on-chain) under its own control. This is for enterprises to control their private data independently. There is a logical mapping between the audit chain, the audit chain and the trusted data pool, which provides an interface for supervision and banks to prove that the business data of the enterprise is true and not tampered with, while ensuring the privacy of the enterprise data. Similar cases include Beijing's first verdict on the use of blockchain to deposit certificates. On April 9, 2019, the Beijing Internet Court's first judgment using "balanced chain" evidence came out. This case involved copyright infringement, and electronic certification of the blockchain was the key evidence for this judgment. Electronic evidence is difficult to store, obtain, and identify because of its variability and easy to change without traces. Therefore, on September 9, 2018, the Beijing Internet Court built the first electronic evidence open ecological platform, Tianping Chain, which was led by the Internet Court and actively participated by all parties in the industry, to solve the difficulty of electronic evidence storage, difficulty in obtaining evidence, We find difficult problem. The balance chain does not directly record the copyright and evidence information, but records the hash value. Of course, in these simple scenarios, only a hash operation is needed to solve a considerable problem.
1. Someone was stuck on the road in a drone. At this time TA happened to be thirsty, so he used the terminal (such as a mobile phone) to place an order to buy a bottle of TA's favorite drink. Nearby, drones need to communicate with the car at this time-instead of forcing the drone and car to happen to be under the control of the same cloud platform manufacturer, a distributed intelligent network is necessary to solve the problem Communication and coordination between cars. Especially in some very urgent situations, for example, passengers need some kind of emergency medicine.
2. Parking in the parking lot, communication and coordination between unmanned vehicles is very necessary. A distributed sharding network can be combined on site to allocate parking spaces in a certain way (such as random) to avoid parking space conflicts.
3. For some special patients, in case of sudden acute illness, the wearable device needs to quickly contact the nearby unmanned vehicle to provide service and send it to the nearest hospital for rescue. It not only needs to solve the problem of information and data communication, but also involves the issue of account payment.
…
In the process of a large number of terminal point-to-point communication, we also need to pay attention to the evolution of data value and AI algorithm. The terminal generates a large amount of data and the intelligence possessed by the terminal, making it possible for data value sharing between terminals and collaborative evolution of AI algorithms.
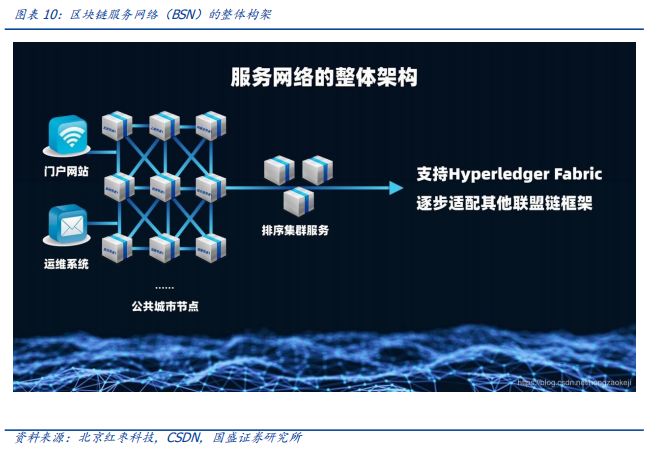
Considering the basic needs of distributed intelligence in physical networking, related basic network services will be spawned. The market has been looking forward to the application of the blockchain, and we believe that the Internet of Things and the blockchain have a natural connection. In the future, "Blockchain + Internet of Things" will become standard. On October 15, 2019, led by the National Information Center, China UnionPay and China Mobile will jointly release the Blockchain Service Network (BSN). The goal is to build a national-level blockchain service infrastructure that is unanimously recognized by the industry, open and inclusive, business innovation, advanced technology, and complete standards. The BSN platform does not focus on the business itself. It focuses on the bottom of the technology and provides a real infrastructure for everyone. Its composition is relatively simple. It connects the cloud resources of China Mobile all over the country in a blockchain fashion, and gives them the blocks they want to use. The service, application, and developer of the chain provide low-cost infrastructure services. Corresponding developers can publish their applications on the network, and business parties can theoretically use such networks if they have their own business needs. On December 1st, the first Blockchain Service Network Partner Conference and Blockchain Service Network helped social governance and the launching ceremony of the Urban Brain City Platform pilot was held in Hangzhou Xiacheng District. At the meeting, the pilot of the Blockchain Service Network (BSN) to help social governance and the urban brain city platform was officially launched. At the same time, the permanent site of the Blockchain Service Network (BSN) Global Operations Center and Partner Conference was settled in Hangzhou.
Enterprises jointly launch a blockchain module alliance to build the future of the smart chain. On October 24 last year, the Politburo meeting set the tone of using blockchain as an important breakthrough in independent innovation of core technologies, and accelerated the development of blockchain technology and industrial innovation. On December 25, the "Internet of Things + Blockchain Joint Innovation Center 2019 Industry Ecology Salon" co-sponsored by China Unicom IoT and Wanxiang Blockchain was held in Nanjing. Domestic mainstream IoT access communication product and service providers are also actively responding to industry needs. 11 domestic companies have jointly launched a blockchain module alliance, which will work together to independently develop end-to-end blockchain technology and enrich the industry. The application exploration of the scene will truly realize the vision of “the future of the smart chain and the growth of all things” in the 5G era. The 11 companies are Guanghetong, Quectel Communications, Mega Smart, Youfang Technology, Xinxuntong, Gaoxing IoT, Yike Communication, Lierda, Shanghai Domain, Matrix, and Molink. In addition, Wanxiang Blockchain, China Unicom Internet of Things and Guoke Chengtai also announced that they will jointly create a smart animal husbandry public service ecological platform. Xinrong Agriculture and Animal Husbandry Technology is the first demonstration partner.
The IoT smart terminal data upload is the most urgent need. Not long ago, companies such as Mega and Yiyuan have released the world's first batch of blockchain modules. As an important starting point for the integration and innovation of blockchain and the Internet of Things, the blockchain module will greatly simplify the industrial customers' "Blockchain +" application pilot based on the Internet of Things devices. Rapid transformation to realize the on-chain business of IoT device data. Industry customers can focus more on how to rely on blockchain capabilities to achieve business model innovation in industry scenarios. As the most direct source of data generation, IoT terminal data upload is the most basic requirement for the most distributed intelligence. The interconnection of the IoT with the blockchain and intelligent AI has become the most basic change in the hardware architecture. With the continuous enrichment of application scenarios The Internet of Things industry will usher in new scenarios and needs.
4. Investment advice
IoT module suppliers : Quectel, Guanghetong, Mega Smart, Youfang Technology, Gaoxing, Mobile Ke Communication (839956.OC), Lierda (832149.OC), etc .;
Government affairs scenario, smart city: Easy to see shares, Donggang shares, Annie shares, Sifang Jingchuang, Yuanguang Software, Huayu Software, Zhejiang Commercial Bank;
Operator : China Unicom.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Analysis 丨 How the blockchain broke through the financial industry's dilemma
- Industry Blockchain Highlights of the Week | 13 Blockchain Listed Companies Expected to Double Net Profit for the Year
- General Manager of Tencent Blockchain Technology: Screening Blockchain Application Scenarios in Three Dimensions
- Technical Dry Goods | How to Learn Full Homomorphic Encryption
- Viewpoint | Meditations on Fault Proof (1)
- Ethereum 2.0 client test online for several weeks, running 22,000 validators
- Twitter Picks | Slamming? Satoshi Aumoto was exploded by lawyers who do not own $ 8 billion in Bitcoin private keys






