Report: Malicious cryptocurrency mining affects 38% of companies worldwide
According to the Cyber Security Report of Check Point Research, the cryptocurrency industry, like any other industry, is extremely vulnerable to cyber attacks in 2020.
Cloud infrastructure is the main target of crypto mining attacks
In 2019, no matter how large or small an organization is, it will inevitably be affected by cyber attacks. Of course, cybercrime is indeed profitable and therefore attractive to unethical individuals. Researchers estimate that cybercrime generated $ 1.5 trillion in losses in 2018.
The reason why Bitcoin is flexible is because of the randomness of data exchange in its blockchain and strong encryption functions. Therefore, blockchain and data cannot be copied or penetrated by malware or other malicious technologies. Nonetheless, once transactions in cryptocurrencies are still vulnerable to cyber attacks.
For example, for 2020, the Cybersecurity Report highlighted threats to cloud infrastructure related to cryptocurrency mining attacks. Despite the decline in the value of cryptocurrencies last year, cloud infrastructure provides a huge target for crypto malicious activities.
- Technology Sharing | Safe and Fair Block Dag Sorting
- United Kingdom: Issuing digital currency or plastic notes is a problem
- Stablecoin will become a global regulatory focus in 2020: who are the main regulators and what is their current position?
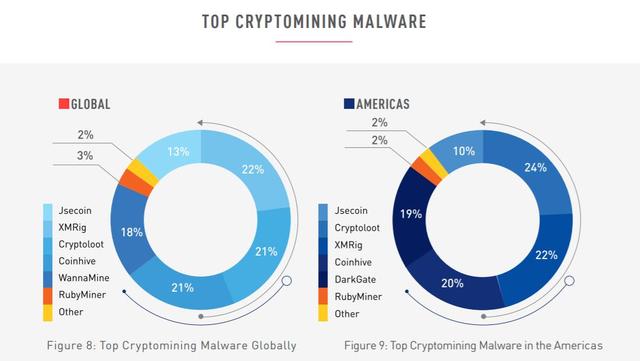
Malware in cryptocurrencies is defined as software programs and malware components that take over computer resources and use them for cryptocurrency mining without user permission.
Ransomware is getting more complex
Ransomware is another threat that will become more complex and targeted in 2019. Compared with 2018, mobile banking malware attacks increased by 50% in the first half of 2019. According to the report, "27% of all organizations worldwide are affected by cyber attacks involving mobile devices."
The report describes malware that specifically uses Bitcoin and not any other cryptocurrency. For example, Glipteba updates via command and control addresses of the public Bitcoin list. Therefore, Glipteba is used by browser thieves or stealing router permissions.

Cryptoloot can also be used for online mining of Monero tokens when intruders access the web without user authorization. In addition, Danabot is a banking Trojan for Windows platforms, which can also be used to steal browser passwords and wallets.
The researchers also highlighted how hackers used Ryuk ransomware to withdraw large sums of Bitcoin from victims.
The scope of cyber threats is becoming more extensive and complex. As a result, the report recommends that in order to stay ahead of criminals and avoid cyber attacks, rather than just discovering and remediating cyber attacks, organizations need to implement aggressive combat plans and keep threat intelligence current.
To prevent attacks, organizations first need sharp, real-time threat intelligence to provide the latest information on the latest attack vectors and hacking techniques. Threat intelligence must cover all attack surfaces, including cloud, mobile, network, endpoint, and IoT, as these vectors are common in enterprises.
Check Point Software Chief Intelligence Officer Lotem Finkelsteen said:
"2019 presents a complex threat landscape, with cybercriminals and private contractors speeding up the cyber arms race and increasing each other's capabilities at an alarming rate, which will continue until 2020. Even if the organization is equipped Advanced security products cannot completely eliminate the risk of damage. "
"In addition to detection and remediation, organizations need to take proactive plans to stay ahead of cybercriminals and prevent attacks. Detecting and automatically blocking attacks early can prevent damage."
The original text is sourced from bitcoinist, compiled by the Bluemountain Labs team.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- New survey: 36% of U.S. small businesses accept virtual currency payments
- As the leader of DeFi, how does Ethereum promote the trillion-dollar financial market?
- Prediction 2020: Who Will Dominate the Spring of the Industrial Blockchain?
- Research Report | Finance must be the most suitable application area for blockchain (Part 1)
- Blockchain + notarization sets off a wave of landings, another example in Shanghai
- Listed company's blockchain business dynamics: 7 companies disclosed blockchain dynamics, and 5 new entrants
- The big brothers in the currency circle have shrunk the battlefield, and the popularity of traditional venture capital institutions has plummeted. How will the primary market of the blockchain play in the second half?





