Detailed DeZ protocol bZx hacked twice: What is the attack method and how to defend it?
Author: yudan @ slow fog security team
Editor's Note: The original title was "Detailed DeFi Protocol bZx Secondary Hacked"
Foreword
On the morning of February 18, bZx was suspected to have suffered a second attack. The difference is that this time the target is the ETH / sUSD trading pair, but some people may have doubts that sUSD is not a stable currency against the USD. Can this be attacked? What is the specific attack method? With such doubts, in response to this incident, the Slow Mist security team will review the two attack processes next.
In the first attack, the attacker combined the Flash loan and the loan from Compound to attack bZx, which was divided into the following steps:
- On-chain documentary: the last week of FCoin, the crisis may come to light in 2018
- U.S. Presidential candidate Michael Bloomberg: proposes "clear regulatory framework" for cryptocurrencies
- Research Report | Case Study of 2020 Global Technology Company Blockchain Layout
-
Borrowed 10,000 ETH from dYdX -
Borrowed 112 BTC to Compound for 5500 ETH, ready to sell -
In bZx, I used 1300 ETH to open a 5x leverage to go short, and exchanged 51.345576 BTC, and the BTC exchanged here was obtained through the Kyber Network. However, Kyber Network eventually called Uniswap to obtain the price. After the 5x leverage was opened, The exchange of 51 BTC actually raises the price of BTC / ETH in UniSwap, and the exchange price is 1/109, but the price of the broad market will not be pulled so much. -
Use 112 BTC borrowed from Compound to sell in UniSwap. Since the 5x leverage in bZx in the third step has already raised the price, it is definitely profitable to sell ETH at this time, and then sold 6871 ETH -
Repayment of borrowings in dYdX
The second attack is slightly different from the previous one, but the core lies in controlling the price of the oracle machine and making profits by manipulating the price of the oracle machine.
Note: WETH appearing below is a tokenized token of ETH, which can be considered as ETH uniformly. Conversion ratio to ETH is 1: 1
Anatomy
The transaction hash for this attack is:
0x762881b07feb63c436dee38edd4ff1f7a74c33091e534af56c9f7d49b5ecac15
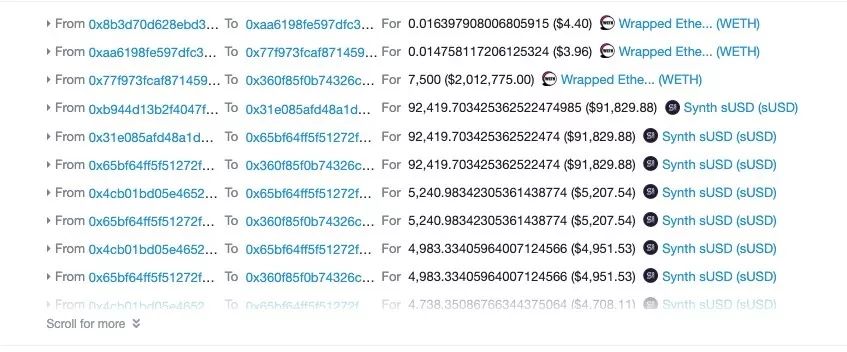
In so many transfer transactions, the attacker bought a total of 20 sUSD and finally made a profit and left the market. So how does the attacker operate? We use the block browser bloxy.info for further analysis.
1. Preparation before the game
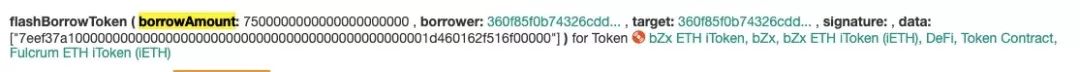
As with the first time, the attacker first needs to borrow a certain amount from the Flash loan to start the attack. The first attack was to borrow 10,000 ETH from dYdX. This time, the attacker chose to start from the Flash loan supported by bZx and borrow it. 7,500 ETH.
2.Serve
After completing the borrowing from bZx, the attacker started a sUSD purchase operation through Kyber. For the first time, 540 ETH was used to purchase 92,419.7 sUSD. This operation instantly lowered the price of WETH / sUSD and raised sUSD. s price. The exchange ratio of this transaction is about 1: 170, and Kyber is finally converted through UniSwap, so at this time, the WETH / sUSD of Uniswap is at a low level, and conversely, sUSD / WETH increases.
After completing the first exchange of 540 ETH, the attacker again made 18 small amount exchanges in Kyber, each time using 20 ETH to exchange sUSD. From etherscan we can see that the amount of sUSD exchanged each time It is decreasing.
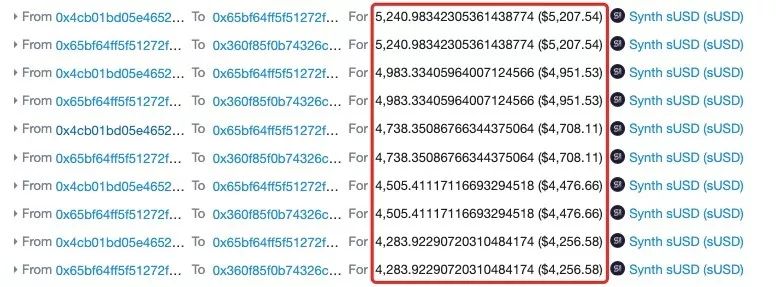
This shows that the price of sUSD / WETH has been further increased, which has exacerbated the price of sUSD / WETH in Uniswap. At this time, the price has reached its peak, about 1: 157.
After completing the above two steps, the attacker has completed preparations for hunting and can start the attack at any time.
3.One hole
After completing the pull up of sUSD / WETH, the attacker needs to collect a large amount of sUSD at this time to prepare for the subsequent exchange of WETH. In order to achieve this, the attacker initiates an sUSD purchase to Synthetix. By sending 6000 ETH to Synthetix to purchase sUSD, the sUSD in Synthetix is directly shorted, and the Synthetix contract returns 2482 ETH to the attacker.
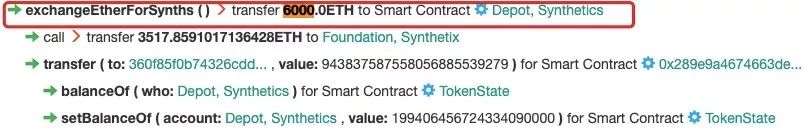

After completing the above operations, the attacker directly launched a total attack on bZx and directly exchanged a total of 1,099,841 sUSD from the previous operation to bZx for WETH. At this time, due to the bZx exchange, it is still necessary to check the price of sUSD / WETH of Uniswap, and this The price has been artificially high by the attacker. At this time, you can exchange a large amount of WETH through 1,099,841 sUSD. In this transaction, a total of 1,099,841 sUSD is exchanged for 6,792 WETH. At this time, the attack has been completed.
4. Repayment of loans
After completing the attack on bZx, 7500 ETH was returned to bZx to complete the lightning loan process. From bZx and back to bZx, bZx suffered a loss.
Resume after the game
By analyzing the attacker's attack methods, we statistics the attacker's expenditure and income during the attack.
income
7500 => bZx Lightning Loan + 2482 => Synthetix Refund + 6792 => Use sUSD to exchange WETH for bZX = 16774 ETH
expenditure
540 + (20 * 18) => pull up sUSD / WETH price + 6000 => buy short sUSD + 7500 => return bZx lightning loan = 14400 ETH
Total return is: 16774-14400 = 2374 ETH
Defense recommendations
The main reason for the two attacks was that the sharp changes in the price of Uniswap eventually led to the loss of assets. This should be normal market behavior, but by maliciously manipulating the market, attackers can reduce prices in various ways, causing the project party to cause losses. . In response to such a profitable attack by manipulating the market, the SlowMist security team gives the following suggestions:
When the project party uses the oracle to obtain the external price, it should set up an insurance mechanism. Each time the token exchange is performed, the exchange price of the current transaction pair should be saved and compared with the last saved exchange price. Large, trading should be suspended in a timely manner. Prevent the market from being manipulated maliciously and bring losses.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- New research: 0.5 Bitcoin can lock most liquidity, payment channel loopholes paralyze Lightning Network
- How to support dual offline payments for digital currencies: the central bank and ICBC have prepared three sets of plans
- Coinbase: Cryptocurrency is a solution to racial inequality in the financial sector
- Forbes: Why use a fixed investment strategy to invest in Bitcoin
- Analysis of hard core technology | bZx protocol attacked by hackers
- Kraken January Crypto Market Fluctuation Report: Earthquake Level Transformation?
- In a year, 27 items of landing applications were disclosed. The IBM blockchain is only for nurturing cloud services?






