Five major problems read through the PoA consensus algorithm
This article will answer the following questions: What is a Proof of Authority (PoA)? How does it work? What are the pros and cons? Which blockchains use PoA? What is PoA compared to PoW and PoS?

Since the advent of Bitcoin in 2009, the field of cryptocurrency has undergone tremendous changes. In addition to the well-known PoW and PoS algorithms, there are other alternative mechanisms for reaching consensus within the blockchain. The emergence of the PoA (authoritative proof) algorithm is by no means accidental, because the above algorithms are insufficient, and PoA appears to make up for the shortcomings of the above algorithms.
Currently, PoA has been put into practice and is considered a more efficient alternative because the PoA algorithm can handle more transactions per second . However, PoA is not only an advantage of faster transaction processing. What is the PoA feature? This guide will help you understand the principles of the PoA algorithm.
- Analysis | Pre-selection and pre-submission mechanisms for Byzantine fault-tolerant consensus
- Unlock Bitcoin for more apps, Miniscript yesterday, today and tomorrow!
- Technical Guide | Teach you to discuss Wasm contract development: (C++)
What is PoA?
PoA is a reputation-based consensus algorithm that provides a practical and efficient solution for blockchains , especially private blockchains. The word PoA was proposed in 2017 by Ethereum co-founder and former Ethereum technical expert Gavin Wood.
The PoA consensus algorithm uses the value of identity, which means that the miner is selected as the block verifier by virtue of the cryptocurrency of the mortgage but the personal reputation . Therefore, the PoA blockchain is protected by a trusted authentication node .
The PoA model is based on a limited number of verification nodes, which makes the PoA system an extensible system . Blocks and transactions are verified by approved participants, and the approved participants are the system administrators.
The following is a wonderful introduction to PoA by Oracles.org (which can be opened by connecting to an external network):

The PoA algorithm can be applied to a variety of scenarios and is considered an excellent choice for logistics applications. For example, when it comes to supply chains, PoA is considered a more efficient and reasonable solution .
How does PoA work?
The verifier runs the software to package the transaction into blocks. The process of packaging transactions into blocks is automated and does not require the verifier to continuously monitor the computer. However, the verifier is required to ensure that its hardware facilities are always in good condition.
The three basic conditions for becoming a PoA verifier :
1. The verifier must officially verify the identity on the network and can find identity information in the public domain;
2. The verifier must first have the right to confirm the proceeds and evaluate the block to gain power (for example, a potential notary must obtain a national notary license to formally become a notary );
3. Establish authoritative inspections and procedures should be consistent .
Under the PoA algorithm, it is possible to become a verifier by obtaining the verifier's rights, so those who succeed in becoming verifiers want to hold this hard-won seat. In order to avoid undermining the credential's reputation, the verifier is rewarded for maintaining a normal trading process. Therefore, most participants value the hard-won identity – the verifier .
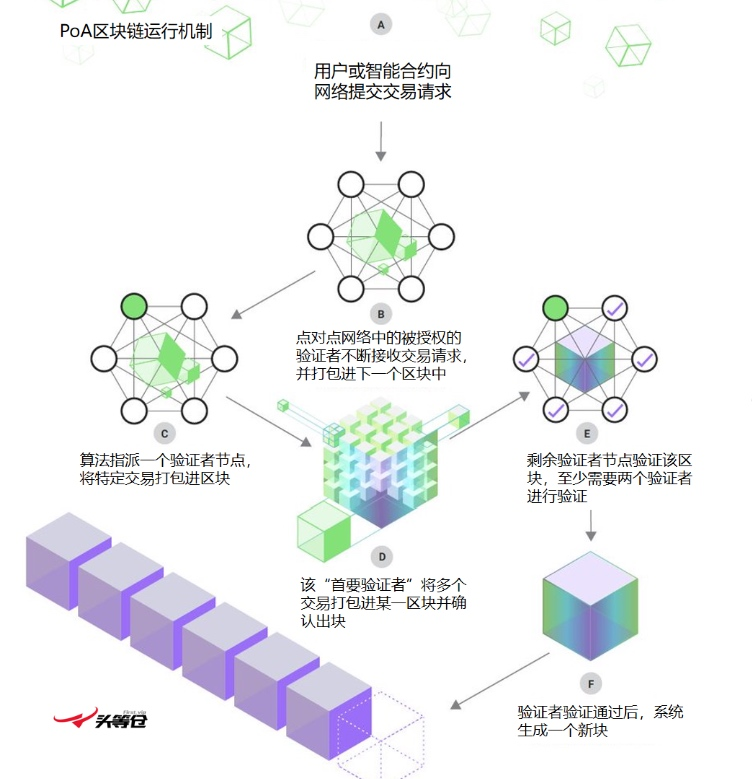
Advantages and disadvantages of the PoA algorithm
The PoA consensus algorithm is not without its drawbacks, so let's take a look at its strengths and weaknesses:
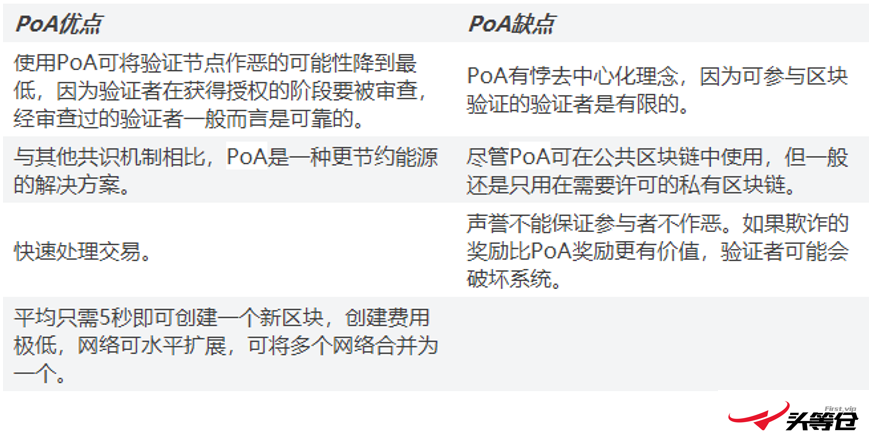
PoA certifiers (or “miners”) have the same size (reputation) and influence on the network from 0% to 100%, but are initially consistent. In other words, as a verifier, your influence on the network may be greater than the influence of some big banks. The operation of the PoA is achieved by the scope of the miners' work and the size of the rights. Each transaction must be verified by at least two nodes, and their power must be greater than the initial node. For example, if the initial node's entitlement is 40%, then the nodes participating in the verification should have a rights greater than 40%.
Therefore, miners under the PoA mechanism do not earn rewards by mining like PoW miners. Accredited and influential miners can participate in verification transactions and blocks. In other words, the miners participating in the verification can verify and reward all operations of the transaction . This significantly reduces the cost of network maintenance. Because PoA networks do not rely on power consumption to mine and earn rewards, miners using PoA are more energy efficient than miners who use PoW and PoS.
Which blockchains use PoA?
The PoA model allows companies to use blockchain technology to protect trade secrets. Speaking of PoA, by the way, Ethereum is the best example of using this technology . Although PoA is one of the most advanced working models, PoA has not been widely used in practice. The PoA protocol is best suited for private blockchains because there is essentially no bifurcation in the private blockchain system. The term PoA was first proposed by Gavin Wood, co-founder of Ethereum and Parity Technologies.
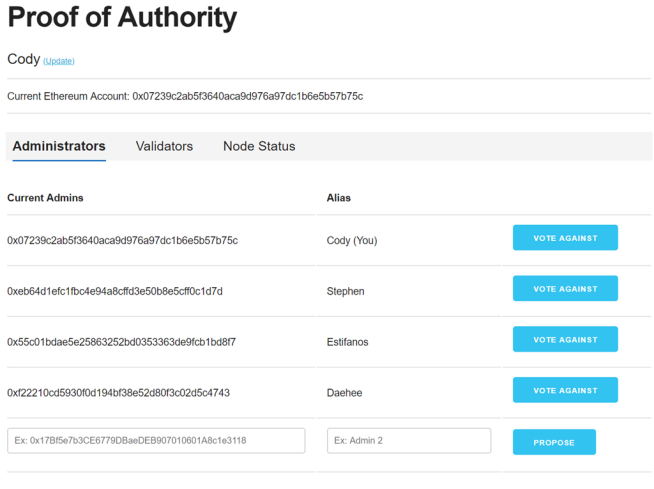
Another use of Ethereum PoA technology is the Azure platform. The Azure platform provides a solution for private networks, and its system does not require its own tokens. For example, Azure does not require fuel costs like the Ethernet, because Azure does not mine.
In addition, according to the latest information, Pavel Durov plans to use PoA to dig Gram coins, a cryptocurrency based on Telegram.
Other blockchains that use PoA include POA.Network, Ethereum Kovan testnet, and VeChain.
What are the advantages of PoA compared to PoW and PoS?
The PoW used by Bitcoin is by far the most reliable and secure consensus algorithm. However, PoW is not scalable. Bitcoin and other PoW-based blockchain transaction volumes (TPS) per second are limited. The reason for the limited transaction volume per second (TPS) is that Bitcoin is based on a distributed node network that needs to reach a consensus, that is, all nodes participating in the verification must agree on the current state of the blockchain to confirm the transaction. This means that the new trading block must be verified and approved by most network nodes before the new trading block is confirmed. So we say that the decentralization of Bitcoin provides a safe and reliable economic system, but it is also not conducive to the widespread adoption of PoW.
Using a PoS blockchain is usually more transactional than processing (using PoW) bitcoins per second. However, the difference between the two transactions per second is not large, and the network using PoS cannot solve the scalability problem. But Ethereum's PoA can come in handy—increasing the amount of transactions processed per second and solving the scalability problem of the network.
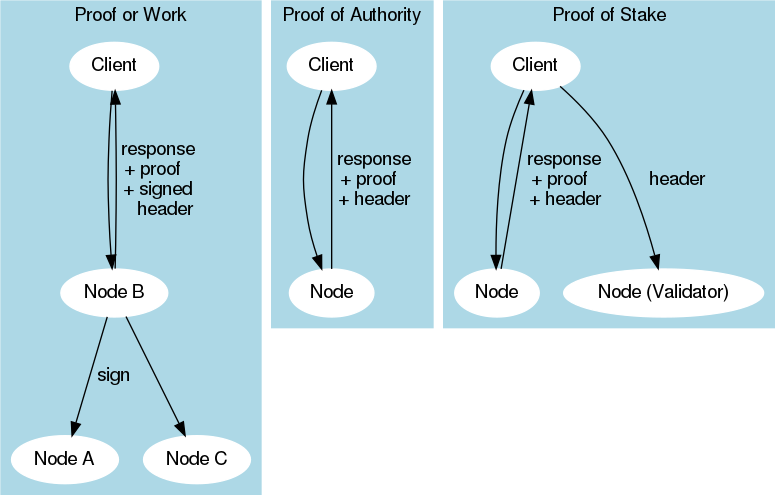
Some people think that PoA is a revision of PoS, but the rule of using currency to participate in verification is changed to use identity participation. Since most chained networks are decentralized, PoS is not always suitable for certain companies and companies. In contrast, for private blockchains, PoA systems may be the best solution because PoA performs better than PoS.
Consensus clause in PoA
Although the conditions may vary from system to system, the PoA consensus algorithm is based on:
- An active and trustworthy verifier (the verifier must verify his identity);
- The difficulty of becoming a verifier: verifying that candidates must be prepared for the possibility of losing their reputation and reputation, the process of selecting a verifier is complicated, but this process reduces the risk of selecting a suspicious verifier and helps Achieving long-term commitments with miners;
- Certifier Accreditation Criteria: The method of selecting a verifier is the same.
The essence of the reputation mechanism is trust in the identity of the verifier. The process of selecting a verifier is not simple, the reputation mechanism will have a process of survival of the fittest, and finally a verifier that is considered to be trustworthy. Ultimately, this ensures that all certifiers go through the same process, ensuring system integrity and reliability.
Limitations of PoA
The PoA mechanism is essentially decentralized. Therefore, the consensus algorithm of the PoA model is only an attempt to make the centralized system more efficient. Although PoA is an attractive solution for large enterprises with logistics needs, in the field of cryptocurrency, PoA will cause some price fluctuations. PoA systems have high bandwidth, but when features such as censorship and blacklisting are easily implemented, the functionality of the PoA is questioned.
Another common key issue is that everyone has access to the identity of the PoA certifier. In retrospect, only recognized participants can become verifiers, and the goal of the recognized participants (opened identity) is to become a verifier and fight for it. However, the disclosure of the identity of the verifier may be subject to hacking . For example, if a competitor wants to break a PoA-based network, they may start with a publicly authenticated verifier and improperly destroy the system from the inside.
in conclusion
There is no optimal consensus mechanism, and each existing mechanism has shortcomings, such as the lack of scalability of PoW and PoS. As we all know, the cryptocurrency community places great emphasis on decentralization, but as a consensus mechanism, PoA has abandoned decentralization in order to achieve high throughput and scalability. The inherent functions of the PoA system and the function of the blockchain are still different. However, PoA is an excellent technology that cannot be ignored as an emerging blockchain solution, and it may be very suitable for private blockchains.
Original: https://changelly.com/blog/what-is-proof-of-authority-poa/#Why-PoA-is-superb-to-PoW
Source: https://first.vip/shareNews?id=2132&uid=1
Translation|First Class Cathrine, Proofreading|First Class Maggie, please reprint this information for any reprint.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Getting started with blockchain | Ethereum 2.0 terminology at a glance
- Defects of the heaviest chain rule: "The Crown Prince" in the "Public Ancestral Blocks"
- Technical Perspectives | Reflections on Citation Dynamic Language Object Models in Virtual Machines
- Technical Guide | Teach you to discuss Wasm contract development
- Getting started with IPFS | 50 questions about IPFS (4)
- How To | Install IPFS and IPFS Clusters on Raspberry PI
- PoD-Tiny – the simplest protocol for zero-trust transactions
