I understand the most common cryptographic techniques in blockchain: zero-knowledge proof
The verifier asks the prover based on a certain randomness. If the prover gives the correct answer, the prover will have a high probability of possessing the claimed "knowledge". A zero-knowledge proof can verify that you did spend money without revealing which currency to use .
Today, zero-knowledge proof has been recognized by many blockchain projects as one of the best privacy protection options. The ability to prove the authenticity of the data without revealing the data.
In this article, we will explain the mysterious Zero-Knowledge Proof and its current applications.
Why is ZKP so important?
Data privacy is one of the most important topics in today's society. Protecting personal data (birth date, bank certificate, transaction history, education certificate) related to personal identity is critical and its importance will continue to increase.
- BTC succumbs to the $10,000 mark, and mainstream currencies continue to fluctuate
- Finally landed! Bakkt physical settlement bitcoin futures trading platform officially launched
- Ping An’s account is intended to be listed in the US in mid-November: the blockchain business has served more than 200 banks.
In the age of technology, we are creating vast amounts of data that we have never seen before, and we are constantly creating data about our own plunder.
Big companies like Google and Facebook use our data to become the technology giant in today's world. However, recent breakthroughs in cryptography and the rise of blockchains have provided new ways to protect our data and identity information. Zero knowledge proof may be the answer.
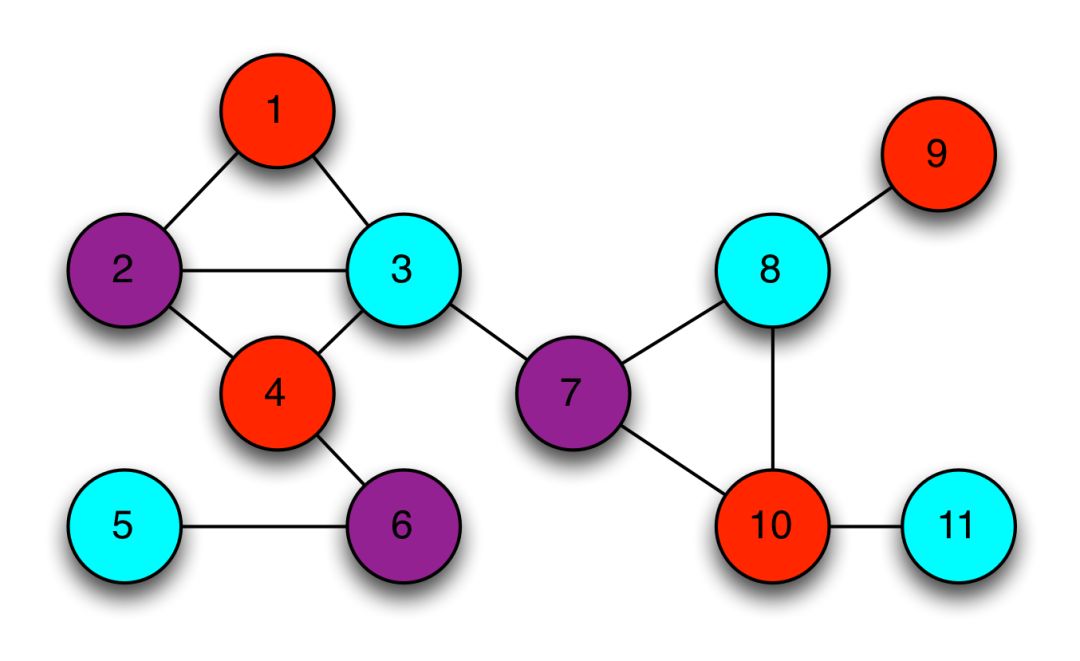
Principle of zero knowledge proof
Zero-knowledge proof is an encryption scheme proposed by researchers at the Massachusetts Institute of Technology in the 1980s. A zero-knowledge proof agreement means that one party (certifying party) can prove that something is true to the other party (verifying party) . Nothing other than this particular statement will be disclosed.
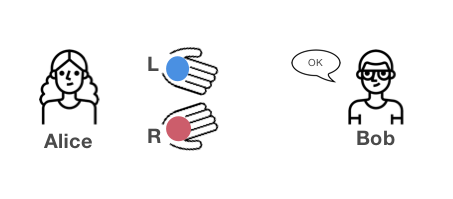
For example, the current website stores the hash hash value of the user's password in its web server. In order to verify that the client really knows the password, most websites currently use a method that requires the client to enter a hash hash of the password and compare it to the stored result.
Zero knowledge proof can protect user accounts from being leaked. If zero-knowledge proof can be implemented, the client password is unknown to anyone, but the client login can still be authenticated . When the server is attacked, the user's account is still secure because its password is not stored in the web server.
Zero knowledge proof can be divided into "interactive" and "non-interactive". Next, let's take a look at the differences between the two proofs.
Interactive zero-knowledge proof
The basis of the zero-knowledge proof protocol is interactive. It requires the verifier to continually ask a series of questions about the "knowledge" that the prover has.
For example, if someone claims to know the answer to the Sudoku game, the process of zero-knowledge proof is that the verifier needs to be randomly specified to be validated by column, row, or nine squares.
Each round of testing does not need to know the specific answer, only need to check whether the numbers 1~9 are included. As long as the number of verifications is sufficient, there is reason to believe that the prover knows the answer to the Sudoku question.
However, this simple approach does not convince people that both the prover and the verifier are real. In the case of Sudoku, the two can collude in advance so that the prover can still pass the verification without knowing the answer.
If they want to convince a third party, the verifier must also prove that the verification process is random and he will not disclose the answer to the prover.
Therefore, it is difficult for a third party to verify the results of an interactive zero-knowledge proof. To prove something to multiple people requires extra effort and cost.
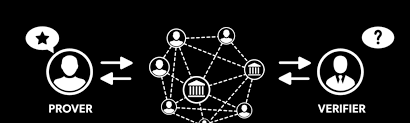
Non-interactive zero knowledge proof
As the name implies, non-interactive zero-knowledge proofs do not require an interactive process, avoiding the possibility of collusion, but may require additional machines and programs to determine the order of the experiments.
For example, in the case of Sudoku, the program determines the column or row to verify. The verification sequence must be kept secret, otherwise the verifier may pass the verification without knowing the true "knowledge".
Zero knowledge proof on the blockchain
Both Bitcoin and Ethereum use public addresses to replace the true identity of the parties, making the transaction part anonymous, and the public only knows the addresses sent and received and the number of transactions. However, the true identity of the address can be found through various information available on the blockchain (such as interactive records), so there is a possibility of exposing privacy .
Zero knowledge proves that the transaction can be valid if the sender, receiver and other transaction details remain anonymous.
ZCash is probably one of the most famous blockchain projects that have successfully achieved zero-knowledge proof. Zcash implements a modified version of ZKP, called zk-SNARKS, which stands for Zero-Knowledge Succinct Non-Interactive Argument of Knowledge.
The zk-SNARK technique reduces the size of the proof and the amount of computation required for verification. It demonstrates that valid trading conditions are met without revealing any critical information about the address and associated value.
zk-SNARK converts the transaction content that needs to be verified into a proof that the two polynomial products are equal, and combines homomorphic encryption and other advanced techniques to protect the hidden transaction amount when performing transaction verification.
The process can be described simply as:
- Split the code into verifiable logical verification steps, and then split the steps into an arithmetic circuit consisting of addition, subtraction, multiplication, and division;
- Perform a series of transformations to convert the code to be verified into a polynomial equation, such as t(x)h(x)= w(x)v(x);
- In order to make the proof more concise, the verifier randomly selects several checkpoints s in advance to check whether the equations of these points are true;
- With homomorphic encoding/encryption, the verifier does not know the actual input value when calculating the equation, but can still verify it;
- On the left and right sides of the equation, multiply by a secret value k that is not equal to zero. When verifying that (t(s)h(s)k) is equal to (w(s)v(s)k), the specific t(s), h(s), w(s), and v(s) are not available. Know, so as to achieve the purpose of protecting information.
But zk-SNARK is not perfect. One drawback in current zk-SNARK implementations is the need to set parameters in advance. If these parameters are leaked, the entire network will face a devastating blow . Therefore, when using these networks, users must be convinced that parameters will not be leaked.
Possible solutions include the use of modern "trusted execution environments" such as Intel SGX and ARM TrustZone. For Intel's SGX technology, the private key is secure even if the application, operating system, BIOS, or VMM is compromised.
In addition, a recent white paper reveals its innovation in zero-knowledge cryptography: ZK-STARKs (Zero-Knowledge Scalable Transparent ARguments of Knowledge).
According to the zk-STARK white paper, zk-STARK is the first system to implement blockchain verification without relying on any trust settings. As the calculated data increases, the computational speed increases exponentially.
It does not rely on public key cryptosystems, and its simpler assumption makes it theoretically more secure because its only cryptographic assumption is that Hash hash functions (such as SHA2) are unpredictable.
It is undeniable that the zero-knowledge proof and the testing and adoption of the zk-S(T|N)ARK technology will take some time. But for the blockchain underlying development platform, how to balance performance and security is critical. Blockchain technology can be better promoted when cryptographic techniques such as zero-knowledge proofs are used more.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Is bitcoin mining still okay? This is the latest sharing of more than ten mining big coffee | New Era Mining Summit
- Interview with Fortune: Will Bakkt help Bitcoin become mainstream?
- Bitcoin should become the industry benchmark, the founder of the senior fund reveals the investment strategy
- Observations | Does everyone's concern about EOS come true?
- Monroe, zcash, Dash, etc. have been taken off the South Korean big exchange Upbit, the privacy of the currency really reached the end of the road?
- President of Ant Financial Service: Blockchain has become the core "technical" capability of ants
- Decentralized autonomous organization: development status, analytical framework and future trends




