Multi-party secure calculation of MPC is hot, how to manage keys through MPC?
Source: Lianwen, the original title "Secure multi-party calculation of MPC is hot, how to manage keys through MPC? 》
Interviewed: Xie Xiang, Algorithm Scientist at PlatON
Interview / Writer: Li Hua
Key management is a concept that is becoming more and more important and has become an important infrastructure in the field of blockchain. When digital currencies or tokens are more traded and used, not just stored once and for all, the way of using assets through private keys or wallet passwords is neither secure nor friendly, and it is more difficult to meet the needs of many application scenarios.
- Nasdaq Research launches Bitcoin futures, fierce competition on digital currency track
- Technology Sharing | "Junk Input and Junk Output" of Blockchain Technology
- Crypto assets regulatory rules updated in the UK: up to £ 10,000 is required to apply for a license and registration fees are non-refundable
Threshold signature method and multi-signature method based on MPC (Secure Multiparty Computing) are two different key management methods. In this article, we interviewed Dr. Xie Xiang , a PlatON algorithm scientist, who will introduce us to the secret of MPC. Key management , and the essential difference between this method and the multi-signature method.
Xie Xiang is a professional in mathematics and cryptography. Now he is a PlatON algorithm scientist and KeyShard product leader, focusing on the research, implementation and productization of crypto algorithms. KeyShard provides MPC-based key management services, providing solutions to the pain points of digital currency key management and recovery.
What is MPC-based key management
Q: Why do we need key management?
Xie Xiang : Individuals can freely register accounts and transfer funds on the blockchain or the Bitcoin network without any third party. This function is accomplished through a set of digital signature mechanisms. In digital currency, the core is how to manage this signature, because everything depends on this signature.
For users, managing signatures is really about managing keys . So we say that keys are money, and key management is important.
In traditional industries, you can manage money through banks or through a series of process designs. For example, you can manage multiple people. The investment manager agrees, the investment director agrees, the finances agree, and the CEO agrees. This money can be transferred out. But once moved to the digital currency industry, the traditional set cannot be done. Why? Because anyone who has a private key can transfer money, the traditional approval process is useless and has no meaning.
So our first idea of doing key management was whether we could move the traditional authorization management mechanism for money into the world of digital currency. This is definitely needed, because many people have already started to use Tokens to invest, such as funds, such as family VCs, they need to have an internal management mechanism, but the traditional approval mechanism is technically too Not coming.
Q: Can multiple signatures solve this problem?
Xie Xiang : Multi-sign is based on scripts or smart contracts . It is to design a rule, for example, three people signed at the same time or two people signed at the same time, pass these signatures to a smart contract, the contract starts to run, and the money is transferred out. Multi-signature can solve some problems. It has actually been used in many enterprises, but as time progresses, more and more problems will be encountered. Where is the problem?
Multi-signature needs to implement different smart contracts for different main chains. At present, there are more than a thousand chains. The smart contract system of each chain is different, and everyone writes contracts differently. Take VC as an example. VC may invest in many chains. How can these tokens be managed? Do you want them to write more than a dozen contracts, all of which have to go through security certification? This is a big labor cost.
In addition, any details of the contract on the blockchain will be seen, and this is where there is a layer of security issues. Anyone can see if there are loopholes in this contract, and many new chains are not time-tested like Bitcoin or Ethereum. It is unknown whether there is any problem with its contract system itself. You will find that some new tokens are out of order. 90% of them are out of contract. This is a big risk.
So in the case of multiple chains, can multi-signature easily support key management? At present it is actually very difficult. Using multiple signatures to manage keys through contracts, the use cost is high, and the security risk is high.
Question: If these different chains are based on the same digital signature algorithm, such as Schnorr, can the key management methods of different chains be universal?
Xie Xiang : No, the logic is not like this, let me draw it for you. Multi-signature is like this. The bottom is the blockchain and the middle is the digital signature. It has a signature algorithm, which can be ECDSA , Schnorr, etc., and the top is a smart contract.
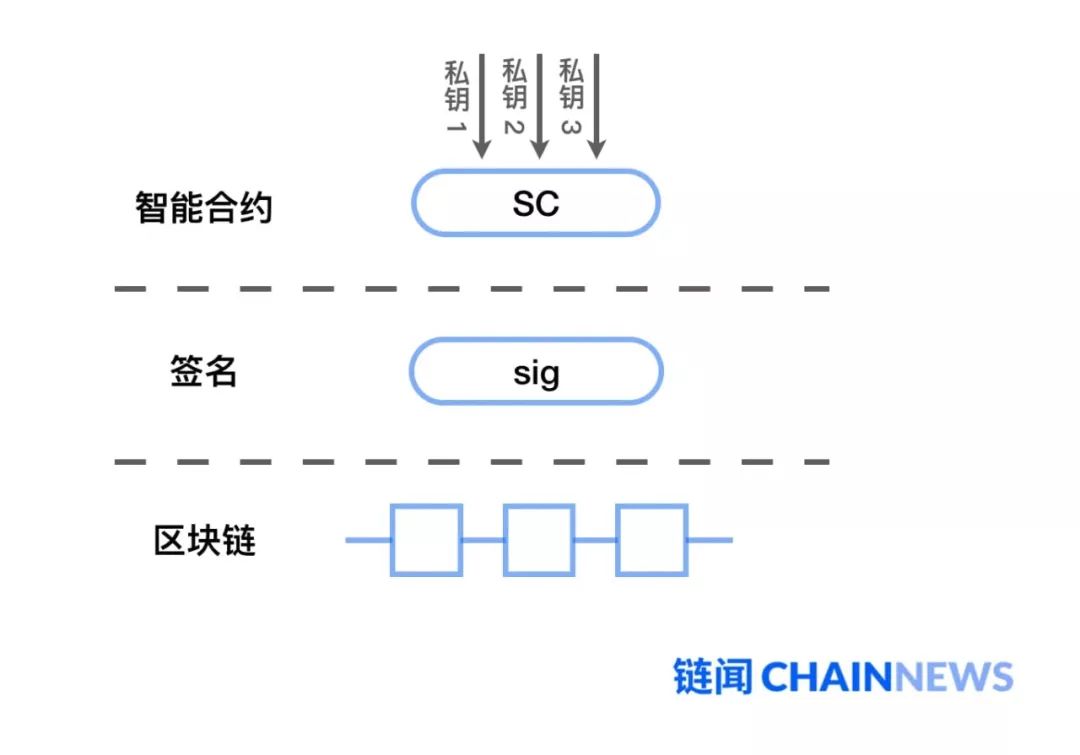
How does multi-sign work? It is to count the number of legal signatures in the top smart contract part, one, two, three … enough, then transfer the money. This method does not care what signature algorithm is used below, whether it is Schnorr or BLS , there is no difference to it.
This is a basic principle of multi-signature, and it can be said to be a benefit. It can be decoupled from the underlying signature algorithm to a certain extent. But its problem is that to adapt to different chain systems, a thousand chains require a thousand smart contracts, and the compatibility of multiple chains is very weak.
Q: What is the threshold signature based on MPC?
Xie Xiang : I redrawn this picture. The bottom is still this chain, the middle is still the digital signature, and the top is the smart contract. The threshold signature based on MPC does not care about the lower chain, nor does it care about the upper contract. It does not care about both ends. It only cares about the right part, which is the part that creates the signature off the chain .

The idea is that a signature must have a private key. It divides the private key into many " fragments " in some way. These fragments can be held by many people at the same time, and then a set of MPC protocols are used to guarantee these fragments. You can directly generate a legitimate signature without being spelled together. "No need to be spelled out" means that the real private key is never present and does not need to appear.
Q: Is the signature done off-chain?
Xie Xiang : When a signature is needed, for example, three people in our company will run an agreement off the chain, generate a signature, and then put the signature on the chain. The logic for generating the signature is implemented in the MPC, and a standard signature comes out, but how to run this protocol is unknown to others.
Put this signature result on the chain, others can't tell whether it is signed by one person or multiple people, because its form and appearance is a signature, which is exactly the same as signing it out directly with a private key. This set of signature mechanisms can be completely independent of the chain and deployed inside the enterprise.
Found no, multi-signature is mainly to count the number of legal signatures, it does not depend on the signature algorithm, but to adapt the chain system; threshold signature based on MPC is mainly to generate a signature, it depends on the signature algorithm , but No need to adapt the contract and chain system.
The threshold signature based on MPC is completely decoupled from the contract module. It does not care how the contract is written and how the chain is. It only needs to distinguish the signature algorithm, as long as the signature algorithm is supported by the chain system, it can connect well. The algorithm may now be ECDSA, Schnorr, BLS (Ethereum 2.0 may use BLS) , so compatible algorithms can be compatible with many chains. MPC-based key management can be multi-chain friendly , which is a big advantage.
Another advantage is that the strategy of this signature mechanism is off-chain, so it is more secure, it avoids the risk of hacking the contract, and the design strategy can be more flexible, because most processes except the signing check are moved off-chain. Now, the user can formulate his own fragment management strategy according to the scenario.
Q: What is the role of MPC in this process?
Xie Xiang : MPC is a collaborative computing framework based on cryptography. The broad understanding is that multiple parties have private inputs to complete a computing task. While successfully completing the task, they can ensure that their private inputs are not in the entire process. Will leak.
For example, a " 2-3 mode " MPC-based key management protocol means that there are three fragments in total. As long as any two fragments participate in the implementation of the protocol, a legal signature can be generated. The signature generation process here, including the fragment generation process, can be regarded as a kind of secure multi-party calculation, because during the execution of the protocol, all intermediate data generated and exchanged will not directly or indirectly cause the leakage of the fragmented plain text.
Q: Why is the threshold signature based on MPC related to the signature algorithm?
Xie Xiang : I have multiple pieces, how can I achieve this signature? This is strongly related to the algorithm structure, so there is a problem that some algorithms are easy to do MPC, and some algorithms are not easy to do MPC. Bitcoin needs to be upgraded to Schnorr. Schnorr is very compatible with MPC. ECDSA is not so compatible with MPC.
Q: Where is the real private key stored in MPC-based key management?
Xie Xiang : You will find a very interesting thing is that throughout the life cycle of key management, the real private key has never appeared, and there is no question of where the private key is stored. This is the essence of MPC-based key management, which guarantees that keys can be used but do not exist.
In traditional key management, a key is a data asset that does exist and it is very difficult to keep it. The threshold signature based on MPC directly strips the key from the system at the physical level, which is completely different from the traditional system in terms of security concept.
In the traditional way, hackers just stare at one point, because the private key exists at that point; but MPC-based key management spreads the security of the key among multiple escrow nodes , and the private key will be divided at any time Multiple copies in multiple places, hackers may have to break through the first, second, third, and fourth. All four fragments must be completed to get the key, and they must be taken at the same time within a certain time range. Keys are not available until four shards, because key shards are constantly being refreshed.
For example, the key is 10, and it is split into two pieces and divided into two places. You can split 10 into 5 + 5, but split it into 1 + 9 after one minute, and split it into 2 + 8 after another minute. The hacker must break both points within one minute to get 10. If the first place is breached in the first minute and the second place is breached in the second minute, the hacker will get 5 and 9, which is not the correct secret. key.
Q: Multi-signature cannot do this refresh?
Xie Xiang : No way. For multi-signature, for example, three people participated in the multi-signature, and one of them's private key was stolen. The corresponding method is not to refresh the key, but to quickly change the address and transfer the money to the new address. It is a pain point in many application scenarios; or, for example, three people are now involved in multi-signature, and a fourth person needs to be added. At this time, the address must be changed, and then a new multi-sign contract is required. There is a handling fee for money to the new address.
But these are very easy for MPC, it can guarantee that the external address is always the same, and the internal refresh is just fine. This benefit is also what we value.
Application of MPC-based key management
Q: Can MPC-based key management lower the threshold for using private keys? This is probably the most headache for ordinary users.
Xie Xiang : It can be done in the same way as the traditional centralized method, so that the user experience is the same: the operation when using digital currency is the same as when you use WeChat wallet, you do not need to memorize mnemonics Or save the mnemonic words in hardware, write them down in a book, and so on.
What's a fun thing with MPC? Let's say A and B use MPC to manage an account together, then they can control the account at the same time, but they don't need mnemonic at the same time. If A wants to use it, he needs to send a request to B. After B agrees, A and B use a set of rules to calculate some intermediate variables locally using their respective fragments. Through information exchange, A can be generated locally. A legal and complete signature. After the signature is passed, A can transfer the money in his account.
Of course, there is still a problem here, how to generate fragments for A and B. In fact, using MPC technology can realize that A and B each generate a fragment locally, and these two fragments can be implicitly spliced into a private key. Note that this splicing is only an implicit mathematical relationship. The fragments are never actually Spliced at any moment.
At this time, the role of B can also be a third-party server. The server confirms the KYC and verifies whether it was initiated by you. After you initiated it, it will automatically pass, that is, it will automatically give another fragment to generate a signature together. KYC is through texting, face recognition, emailing, etc. In this way, the user's operation is exactly the same as the traditional operation. This is tied to the actual application scenario.
We made an app called KeyShard to tell users how MPC-based key management can be used. Try it out. Currently, only Ethereum is supported. It is a simulated traditional rights management, which requires two people to agree before moving the account.
Q: Back to the beginning. You said you moved the traditional authorization management mechanism for money to the digital currency field. In the traditional approval process, it may be necessary for A to pass first, then B to sign, and then C to sign. Is this what the MPC can do now?
Xie Xiang : This is actually a very critical issue. In the traditional process, this is called pass signing , and there will be some obstacles in the MPC. Let me draw the general logic of the MPC.
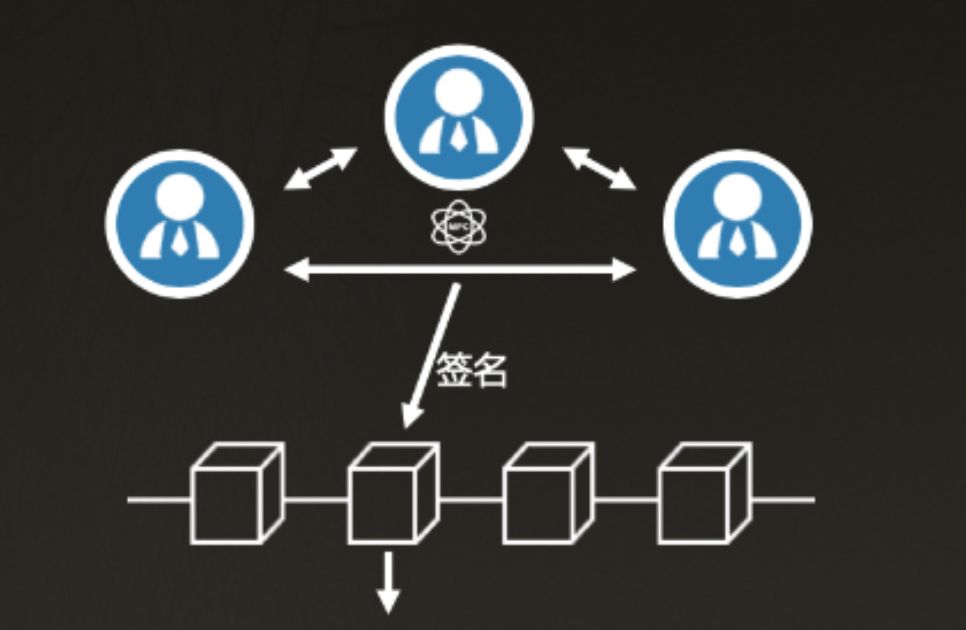
The algorithm agreement of MPC is to be connected and interact with each other. For example, three people, namely manager, finance, and CEO, participate in generating signatures. It requires these three people to be online at the same time. Therefore, pure MPC algorithm itself is difficult to pass the signature.
However, we can use the engineering architecture to implement the signing function at the product level, so that upper-level users do not need to worry about it or think about how the bottom layer works. For users, the product operation experience is the same as traditional signing. So there is a big difference between algorithms and products. Here are two sets of things. In addition to the algorithm itself, technology and business logic need to be combined.
Q: Can you understand it this way? MPC-based key management is not only for the secure storage of keys, but also for individuals or businesses to use the keys conveniently and satisfy business logic?
Xie Xiang : It has multiple advantages. Secure storage is one aspect; letting individuals or businesses use keys more securely and conveniently is another aspect. The former refers to the "custody capability" of keys or assets based on MPC key management, which reflects static security; the latter refers to the fact that MPC-based key management can actively design a variety of policy management, which is a kind of Dynamic business empowerment.
Question: If there is an investment institution that needs to manage multiple tokens, can it buy a set of MPC-based key management algorithms, and then use this algorithm to implement signatures on different chains, and then manage assets on different chains? ?
Xie Xiang : It is unlikely to buy algorithms directly, it will buy products, such as a set of MPC-based key management software installed on the company's internal server, and then can manage assets through an interface. You can understand that it bought a MPC-based financial management system.
The lowest level of key management is a set of algorithms, but it can be packaged as a product, it can also be packaged as an App , and it can be packaged as an SDK (Software Development Kit) .
Q: If there is a wallet company, and I hope that the wallet adds a function that allows users to manage private keys based on MPC, can I find a professional company that provides MPC solutions for cooperation?
Xie Xiang : Right. You can understand that there are investment institutions, wallets, exchanges, and other business companies in this market. They each have their own business, but they must have the problem of how to manage money. We are providing a set of MPC-based The key management ability, which is based on MPC's ability to manage money, is connected with their own current system.
From the perspective of the company's positioning, KeyShard is actually a technology provider or an infrastructure company. It sinks itself a little more and does not touch the business above. It dominates the underlying key management SDK, and hopes to integrate the business process of authorization management into the SDK. Of course, the difficulty lies in abstracting a relatively flexible and easy-to-use SDK.
Challenges of MPC-based key management
Q: What are the difficulties encountered by MPC-based key management now?
Xie Xiang : Both technical and non-technical. Non-technical is someone asking why it is safe? Give me a certificate. Traditional KMS (Key Management Service) has a certificate, but because MPC-based key management time is not so long, there is no authentication.
This is a problem caused by the particularity of this discipline. Although cryptography has a solid theoretical foundation, it is divided into theoretical security and actual security. It takes time to verify whether actual security can reach the level of theoretical security. So one is the need for standards bodies, and the other is the promotion of academic research. We will actively promote similar standards and promote industry's recognition of this technology, but it will take time, not so fast.
The technical difficulties are just mentioned, we need to combine this new set of technology with complex business logic. In addition, MPC is a set of distributed technologies. If distributed, there will be synchronization, that is, the problem of consensus .
The original authorization management is a purely centralized thing, and business processes will be well matched; but in a distributed scenario, there will be certain difficulties, such as the problem of users being offline, the quality of the network, and the key There is a delay when refreshing, whether to use the next fragment or the previous fragment. There will be many such details that need to be considered.
Q: Is it true that MPC-based key management is not accountable? That is to say, I don't know who signed and who didn't sign, can't trace the responsibility?
Xie Xiang : In fact, you can know, from the algorithm level, you can catch who signed it. The bottom layer of the algorithm can track down who has not signed by introducing a check and report mechanism, and even know who gave the wrong error message during the signing process.
Demand from use:
Key management is a concept that is becoming more and more important, and it may even become an important infrastructure in the field of blockchain . Because when digital currencies or tokens are more traded and used, not just stored once and for all, the way of using assets through private keys or wallet passwords is neither secure nor friendly, and it is more difficult to meet the needs of many application scenarios.
Multi-signature and threshold signature based on MPC are both methods to achieve key management, but they are completely different design routes: the former is on the chain and relies on the number of legal signatures of smart contracts; the latter is off-chain and depends on MPC. Fragmentation generates a legal signature. This article focuses on the latter, which is MPC-based key management. I hope it can help you understand this technology and solution.
Revisiting the "private key": the private key is not the key
The intuitive reaction of the word "private key" is that it is a kind of "key" that is used to open a safe that holds digital currency. It also seems to make sense to think about it. You can get coins with a private key. But in fact, in the field of blockchain and digital currency, the private key means the asset itself .
Imagine that you lost your safe key and your money is still there. You can get another key; but if the private key is forgotten, the money will disappear forever. Your safe key is stolen, and your money may still be safe, because the thief still needs to slip into the building and pry open the door lock of the room; but if the private key is stolen, the money will almost never belong to you immediately.
The private key is not the key that opens the safe, it is the asset itself that is to be placed in the safe. And how to design a safe system to store the private keys, so that the private keys in the cabinet are both secure and easy to use, which is key management. At that time, it is not the private key that is handed to the user, but a set of keys to open the safe.
Multi-signature and threshold signature based on MPC are both methods to implement key management, but they are completely different design routes: the former is on the chain and relies on the number of legal signatures of smart contracts; the latter is off-chain and relies on MPC to use Fragmentation generates a legal signature. This article focuses on the latter, which is MPC-based key management. I hope it can help you understand this technology and solution.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- MasterCard CEO: Libra's financial inclusion fails to meet expectations, and compliance is too vague
- Want to buy Bitcoin? Understand these 4 points first
- Should a single anchor and a basket of currencies be more imaginative?
- Babbitt Column | Can blockchain help food companies such as Sibe to survive?
- MIT shot! Researchers open "spider" routing solution to increase blockchain speed by 4 times
- Blockchain Weekly Report | Blockchain companies' aid in Ecuador has successively arrived in Europe and the United States to introduce new policies related to cryptocurrencies
- China's blockchain industry under the shadow of the epidemic: conference postponed, mining machines suspended




