Symmetric Cryptography in the Computer Age: From $100 Franklin to Binary XOR to AES
The era when computers did not appear was classical cryptography, and after the advent of computers, modern cryptography. what differences are there?
Everyone recalls the hidden method, shift replacement, Virginia encryption, including the Enige code machine during World War II, all of which are English letters. For example, the 26 gear slots of Enige code machine correspond to 26 English. letter.
The computer reads 0 and 1, which is related to the basic structural unit diode of the chip. Then, after the computer appeared, linguists retired to the second line. Nowadays, English letters are not needed. The process of encryption and decryption is all done by computer, and the binary world of 0 and 1 comes.
After the bit sequence begins to rule, you need to find a way to turn the language text into a binary bit sequence. The operation of mapping real-world objects into bit sequences is called encoding. This code has a specification called ASCII.
- Digital Money Market Investment Logic Change | Token Watch
- Zhongan Technology Wu Xiaochuan: Blockchain+ composite technology can better protect data privacy
- Libra Association officially released the first road map, after four milestones will start the main network
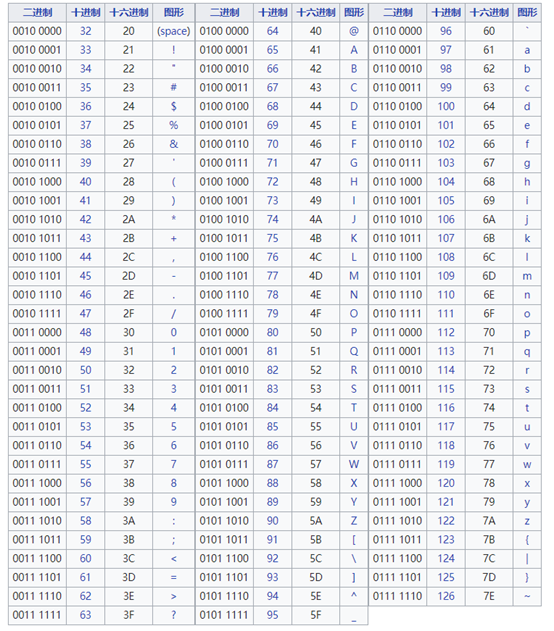
The above is a partial binary comparison table, which is easy to find online.
There is something interesting behind this. ASCII is one of the landmark works of the IEEE. IEEE is very interesting, the full name is: American Institute of Electrical and Electronics Engineers. Headquartered in New York, USA, “having 420,000 members from 175 countries”, it began to develop in 1963. So now many blockchain projects can't be said to be 100 million fans. This is very difficult. You can look at the development of IEEE. Of course, you said that the blockchain industry is distributed and smart communication will be Accelerate all processes, and right, the technical organization of 100,000 members is very difficult, and 100,000 people who are concerned are feasible.
The earliest IEEE landmark work was Benjamin Franklin's famous book "The Experiment and Discovery of Electricity" published in 1751. Franklin was the avatar on the US 100-dollar bill.

One of the pioneers in the disciplines of electrical and electronic engineering, communications, computer science, and engineering was Franklin, not the US President Franklin Roosevelt during World War II, which was the birthplace of the United States. Cryptography and these disciplines are intertwined, so the interesting thing is that cryptography has something to do with money from the beginning . The amnesty printed on the $100 bill is more because of his academic contribution because he is the Minister of Finance, the Minister of Foreign Affairs, the printing director, the drafting of the Declaration of Independence, and the first true meaning. The Americans represent the achievements of the American spirit.
You can look at the history of IEEE development, the link is as follows:
https://en.wikipedia.org/wiki/IEEE Milestone List
Going back to our binary code, ASCII, the language text becomes 0 and 1 at this time, that is, we don't need to slap the letters, just need to change 0 and 1 to encrypt the content .
Let's talk about how to encrypt in a very straightforward and simple language.
What is XOR ?
XOR is called exclusive or, which is XOR, which is an extremely simple operation. You think of it as a kind of addition, subtraction, multiplication and division that you learned in elementary school. Of course, this is an overestimation of the simplicity of the operation. Let's just say that a primary school student can see XOR operations, which is much easier than addition, subtraction, multiplication and division .
1 XOR 0 result is 1;
0 XOR 1 result is 1;
1 XOR 1 result is 0;
0 XOR 0 result is 0;
The same before and after is 1, the difference between before and after is 0. From the above table to find a letter such as a, a is 01100001. Just find a secret key (key), such as 01010101. Of course, can be arbitrarily chosen, below will talk of.

This is the result of using the secret key, XOR, 00110100 is the ciphertext. In contrast to the table, this binary representation is: 4
Thus, the original a becomes a ciphertext 4, of course, sometimes it seems that such a rule is more garbled.
Remember the mouth: the same is 0, the difference is 1. This is much easier than the multiplication method, the children can quickly grasp.
Give a graphical expression that is easier to understand:

The result of the XOR text operation with the key can be pushed back by the key. This is the symmetric encryption method of the computer age.
Popularize knowledge:
What is Bit Bit? What is a byte Byte?
In the above, you can express an English letter with an eight-bit binary. Then, an English letter is a byte. English is called Byte, which is 1 byte=8bit=8 binary bits. Because a bit is a bit in the binary. For another example, a Chinese character is two bytes. Punctuation marks are calculated separately.
Let's talk about the classification: one-time password book and block password
In symmetric cryptography, a one-time password book belongs to a stream cipher. The definition of stream ciphers is broader and this chapter does not expand.
To understand, you have a piece of information that needs to be encrypted. For example, your information consists of 10,000 English letters and 80,000 bits after conversion to binary.
I am now generating a binary random number. What is the length? 80,000, that is to say, I have XOR every bit of this original text, and there is no law, because the key itself is a random number (or pseudo-random number).
However, such encryption is cumbersome, security is good, efficiency is not high, and the key is as long as the original. You have a 1GB file, 1GB after encryption, but the key also has 1GB. Delivery and storage are all problems. Remember: there are also logistics problems in cryptography, mainly the transmission key.
At this time, use a fixed-length encryption key to encrypt the original text loop. After simplifying the model, it can be said that the original text of 80,000-bit length, I use an 80-bit key to encrypt, it takes 1000 cycles. Remember, this is a simplified model, and the actual operation is more complicated than this.
The grouping key is an encryption method widely used in communications, e-commerce, and financial systems.
Note that instead of asymmetric encryption in the future, symmetric encryption is useless. Symmetric encryption has symmetric security. Asymmetry has asymmetric troubles . It is not directly killed by a stick.
What is DES and AES?
"Data Encryption Standard (DES) is a symmetric cipher block cipher selected by the US National Bureau of Standards in 1976 as the official Federal Information Processing Standard (FIPS) of the United States, and subsequently widely used internationally. ""
Later, with AES (2001), A is advanced is more advanced and advanced is not American, AES encryption method selection is open to the world, AES is both American and global. The selection was held by NIST, a US standardization body, and the review was not for them. It was completed by global companies and cryptographers and entrants. If cryptographers around the world can't find the weakness of the encryption method, and then consider efficiency and security, they will be selected.
The chosen algorithm requires free disclosure to the world. It's a bit like playing a battle station to see who's working hard, choose who, and after choosing it, hand over this set of internal skills to the people of the world. For example, the AES we use nowadays is actually the Rijndael algorithm, which was selected from the candidate algorithms in 2000.
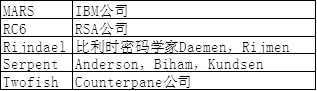
The five of the pictures are candidate algorithms. RSA has emerged, and the RSA algorithm is the most widely used cryptographic algorithm among asymmetric ciphers. RSA has held several competitions at the end of the 20th century. What are you doing? The symmetry algorithm for deciphering DES was really successful. The block cipher in symmetric cryptography can be cracked. RSA found someone to crack the DES algorithm, and later submitted the AES algorithm, and successfully "nominated Oscar". Only the last moment was lost, and the best algorithm was awarded to Rijndael.
However, in the field of asymmetric cryptography, RSA is the existence of God, and it is precisely with the asymmetric cipher that the birth of the blockchain is possible.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Opinion | What does Google's “quantum hegemony” mean for the future of the blockchain industry?
- For the first time in five years, it took 2 hours for the Bitcoin network to dig a block for the first time.
- Innovation defines the bitcoin price model, the bank believes that BTC can reach $90,000 in 2020
- Research: 64% of cryptocurrency transactions are fraudulent, but the “false rate” has been reduced by 35.7%.
- CME does not intend to launch physical settlement of bitcoin futures
- Market Analysis: Mine machine warehouse suspected fire, BTC did not come out for two hours
- Block.one was fined $24 million, and the SEC opened the "toll booth" model?






