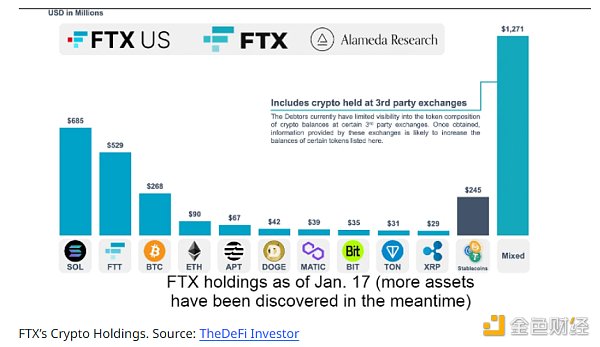
The copy of the private key is stolen, the address transfer is anti-lost, and the data security of the blockchain C is guaranteed.
Recently, Ethereum's famous browser extension MetaMask has been exposed to security breaches, which may cause the user's Ethereum address to be unwittingly obtained by third parties such as DApp developers. We are already in safe question? Still a compromise in user experience? Analyzed in the MetaMask Privacy Leak Problem .
In fact, the problem with MetaMask is essentially the problem of excessive openness of private data permissions, making a security sacrifice for the user experience. Similar problems exist on the Android app side, especially in the use of apps such as digital wallets and exchanges. Beijing chain security expert C00lMan introduced the following scenario: For example, when we back up the private key or transfer money through the wallet address, we need to transfer the private key information or address information to other App. The strategy of most wallet apps at this time is to use the clipboard of the Android system as the transmission medium of data. Is this really safe? The answer is: not safe.
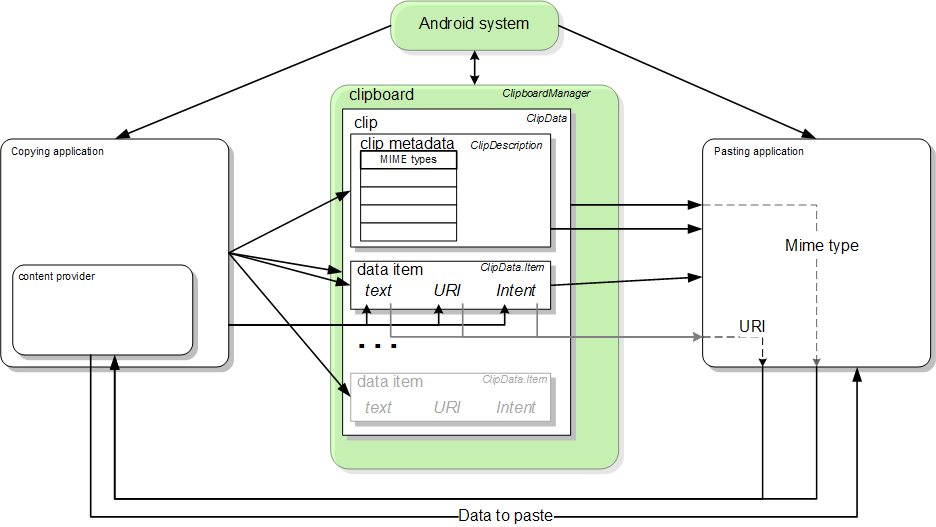
(Android system clipboard framework)
- Getting started with blockchain: Why should Ethereum set a block for the block?
- What is the relationship between Bitcoin and terrorism? This report is enough to explain everything.
- How do we tell the truth about the currency in the currency circle?
All apps in the Android system can be copied and pasted through the system clipboard, and the data stored in the clipboard can be accessed by all apps. An App registers a listen event through the interface that comes with the system. When new data is stored in the clipboard, the app can know what the copied data is.
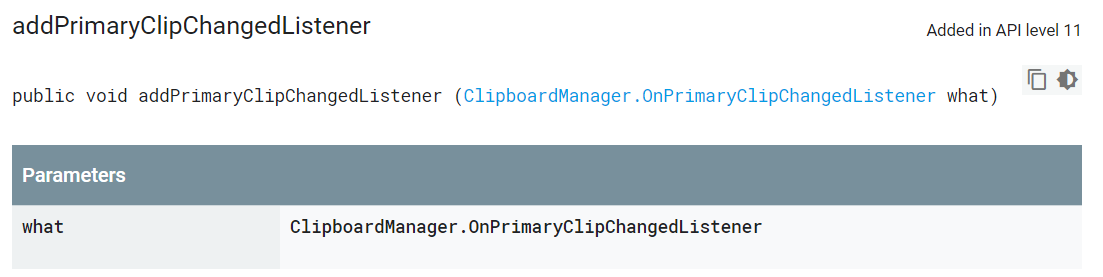
(Register clipboard listener event function)
Imagine if you copied your private key data in the wallet app at this time, the app that registered the listen event can steal your private key information.
(wallet copy private key interface)
The figure above shows the digital wallet export private key interface, which illustrates a series of security tips that need to be paid attention to when the private key is saved. Since this article aims to explain the security of the Android system clipboard, it shields the interface that may reflect the specific characteristics of the wallet brand. . In fact, when you choose to copy the private key, it triggers a clipboard listener event.
(Stealing private key attack example)
As you can see from the above figure, after this event is intercepted, we can read the contents of the clipboard, steal the private key, and put your assets in an extremely dangerous situation.
Even the contents of the clipboard can be further modified. For example, if you copy the transfer destination address, the app can clear all the data of the clipboard first, then write a fake transfer address to the clipboard, so that when you pass When the system's "paste" function is used to enter the transfer address, you actually entered a fake address. This caused a phishing attack. The funds you transferred were stolen by hackers, and all this is in the unknown. Not finished.
It can be seen that the clipboard brings some convenience in sharing data between applications, but should important data be transmitted through the clipboard? How to better ensure the security of important data of users while ensuring convenience?
In this regard, we can actually adopt a safe data clipboard solution.
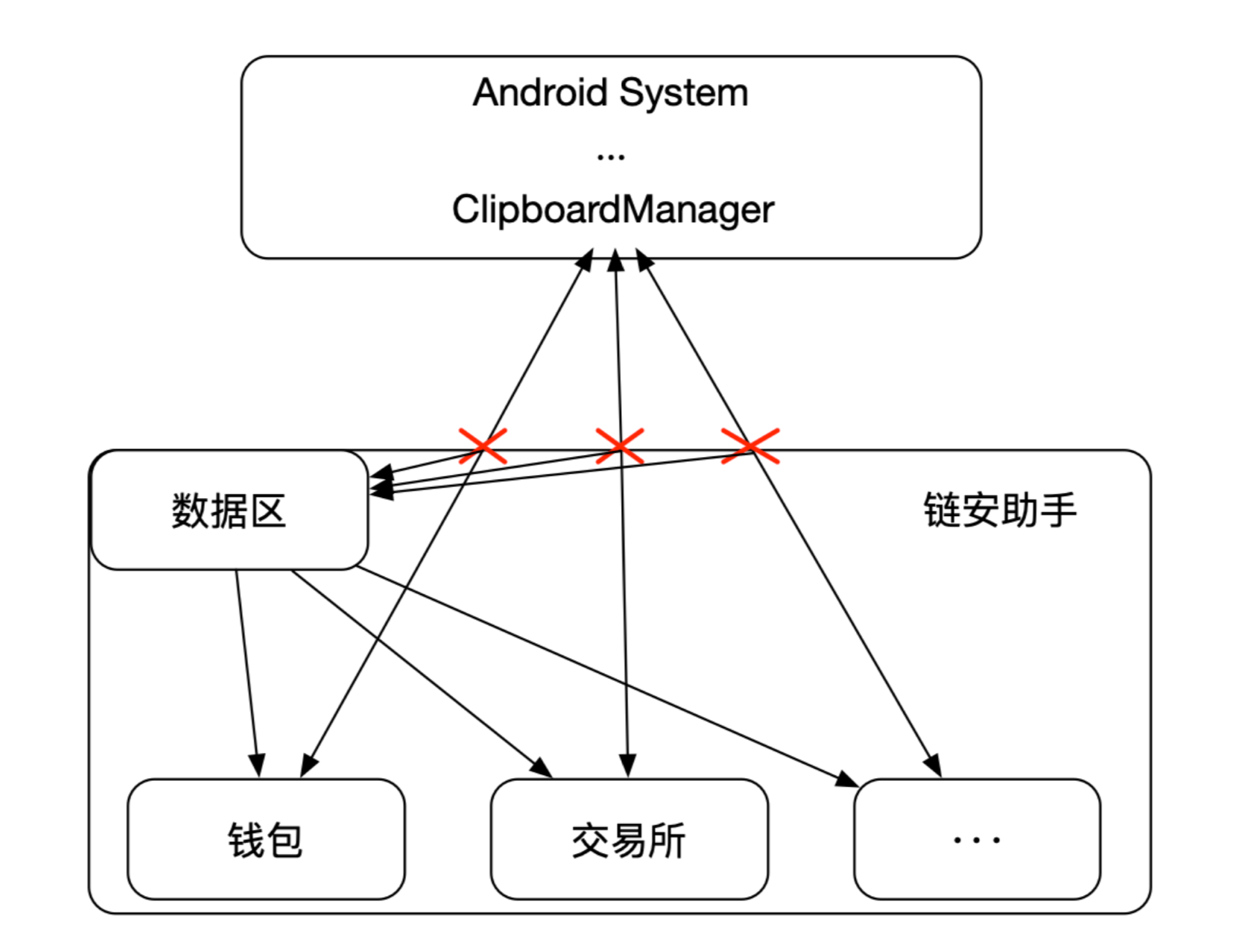
According to Zer0dMan, a mobile security expert from Beijing Chain Security, in the security sandbox technology, we can use high-intensity encryption of the data copied by the user through a special security technology and store it in a memory area created by the secure container. The area is the system. The clipboard is isolated, only the blockchain app launched in the security sandbox can be used, and applications outside the sandbox have no access to this zone. This solution not only ensures the security of user data, but also achieves a good user experience.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Violence is rising! Is Bitcoin a return to value or a castle in the air?
- Trading volume may be fake, but the value of Bitcoin is real.
- Watching on April 2: What is the cause of the bitcoin skyrocketing?
- The tens of billions of dollars in the pan-PoS ecosystem: What issues need us to seriously consider?
- Market Analysis | Bit market strong breakthrough, mainstream currency can highlight
- Which cryptocurrency should I use for cross-border payments? Coinbase recommends XRP and USDC
- Blockchain needs people who are truly "decentralized" thinking