The cryptography of Wanli fifteen years to Xianfeng ten years: Virginia encryption
Today's content is a prelude to cryptography entering modernization. Although there is no encryption algorithm for the Bitcoin blockchain, today there is a real thing: the key. Please take a closer look, the examples in the text are made in the Excel table, for the sake of simplicity and clarity, you will understand at a glance.
This article will talk about the alchemist from French diplomats, from the Ming Dynasty Wanli fifteen years to Xianfeng ten years, serious. – Foreword
After the frequency analysis method comes out, the shift and replacement method is not easy to use, so how can we eliminate this probability?
- Turkey announces new strategy: building a nationwide blockchain infrastructure
- Ripple and Ethereum led the rise and the competitive currency market was reactivated?
- Can 0.28BTC be a bitcoin "big whale"? Maybe this day will come soon
Wanli fifteen years


"Small high, what books have you read recently?"
"Recently watching Huang Renyu's "Wanli 15 Years""
"We are also looking at Wanli for fifteen years."
"I feel that this book explains the history of the Ming Dynasty."
"Look at the history to compare and see, then do you know what happened in the fifteen years of Wanli in France?"
"How do you tell the history of vertical and horizontal, I really don't know?"
"Do you know Virginia encryption?"
"I do not know"
"Small high, the light is too bright, you pull the curtains up, I will give you a good talk about Virginia encryption."
– Adapted from the TV series "The Name of the People"
Everyone has heard or read a book called "The 15th Anniversary of Wanli" (the 15th year of Wanli is 1587). The author, Mr. Huang Renyu, wrote that the Ming Dynasty turned from bad to bad, Virginia encryption. Born in the 14th year of Wanli, that is, in 1586, at that time, if this encryption method was passed to China, it would be a kind of Qimen armor.
This is not a joke, because at that time the European chemists were called "Alchemists", and the word chemist was only two hundred years later, after the birth of the chemistry master Lavoisier. There are also alchemy in China. For example, the Eastern Jin Dynasty Ge Hong and the Southern Song Dynasty Wang Chongyang are all alchemists or alchemists. China's alchemy did not develop into chemistry, and China's Zhouyi gossip did not develop into cryptography. Therefore, it will be beaten after two hundred years.
Closer to home, the Virginian cryptography inventor is a French diplomat, called Bryce de Virginia, and it’s no surprise that diplomats at that time were often in a place called the “black room”. Encrypt the letter and send it out. Sometimes, the colleagues in the black room will pick up the work outside, encrypting and decrypting the mail, and it is charged.
The Virginia encryption method is a third-generation encryption method. The main purpose is to combat the decryption of frequency analysis. After using this encryption method of diplomats, the probability of letters appearing disappears.
How to do it? Quite simply, when the same original letter appears in a letter, it is a different ciphertext expression.
Directly on the map.
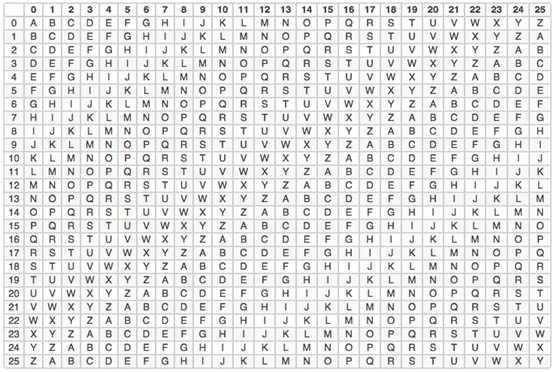
This is the password table for the Virginia encryption method.
This is a 26X26 table with 26 English letters in the first row and first column. The first line represents the original information, and the first column represents the key to encryption. The convergence of the two is ciphertext.
Estimated to be a bit embarrassing, so that the key is simple, just a letter C, then, the order of the ABCDEFG alphabet is also the order of the table, C is the third letter. So, what do you get after the first row of D encryption?

It is F, which is equivalent to shifting two bits, and D becomes F. The first row of D in this figure is the original text, the C in the first column is the secret key, and the F where the arrow meets is the encrypted ciphertext. Similarly, if the original text is C and the key is F , then the ciphertext should be H.
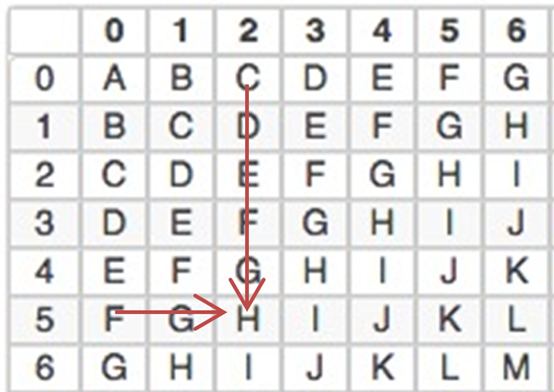
So, if my key is not a letter, but a few letters, for example, ABC, ABC, ABC will cycle like this, but this ABC is too strong for the key, it can be CASH, COIN You see that BCH is not suitable for the key, because B and C are weaker when they are encrypted.
Do you see such a string of letters to understand? CVGDQPO
Of course, I don't understand. This is what it looks like after encryption. Of course I don't understand. I now tell you that the key is BCH.
This means that the BCH three-letter cycle is used as the key. Can you solve the original text?
Well, the first ciphertext is C, the key corresponds to B, first find the key in the table is the first column, which is B, then see C on the right and then B is up, these several The letter is too close, I find a far point, the J in the ciphertext is the third letter, the bch in the corresponding loop is h, so h is the key, look at the order of the arrows in the figure, you know how to crack .
Ok, here I will present the examples from the Excel spreadsheet directly to everyone, and then try to figure it out.

Is the above encryption method very good?
No, the above encryption method seems to be ingenious, but it has made a big taboo, too slow . Encryption must take into account security and efficiency. Just like doing encryption and decryption, the person who writes the letter is very tired, and the person who decrypts it is very tired. The transmission of the key B/C/H is still confidential, and it is troublesome if anyone knows it. Symmetric encryption is like this, what is symmetric encryption? That is, encryption and decryption are reversible. Just give me the key and give me some time. I can decrypt it at any time – this is a postscript.
Xianfeng began to apply in ten years
Therefore, the two hundred years after the invention of this encryption method has basically no great use, just an entertainment game in a small circle. Later, during the American Civil War (1861 to 1865), this encryption method was used on a large scale. The reason was that there was a mechanical method, and a machine crack was specifically designed for decryption. Such a machine would have some famous ones in the future. For example, you are a horse machine (Enigma, the Enigma in German), which means that the French invented this encryption method during the Wanli Period of the Ming Dynasty. It was only after 1860 (that is, the 10 years of Xianfeng) that it was burned in the Yuanmingyuan. use.
why? The answer is the industrial revolution. In 1860, the steam engine was available. The motor is also available, and the boring physical cracking work can be handed over to the machine, and the design of the crack law is just fine.
From this point of view, the Qing government at that time was only a big gap in cryptography.
If the wars of the two sides are repeated again, it is likely that the British and French coalition forces intercepted the Qing army intelligence and directly cracked it. After the Qing army intercepted the documents of the British and French coalition forces, it was directly forced. How do you fight this? Let's not say that the Western ship is so powerful, you will have to abolish this cryptography . Moreover, the Qing army still has nothing to say, say something!
Backing out "Sun Tzu's Art of War", "Know Yourself and Know Yourself, What Are You Worried?" How do you know yourself and know yourself? There is no modern technology, you don't understand the method of deciphering. You don't know. The ancestors gave you the method, you have to find out the path.
In fact, from the context of this article, you can also see that the following cryptography has developed.
Cryptography originated in war and will return to war. From the hidden law, the displacement replacement method to the Virginia encryption method that is spoken today, it is not accompanied by war . The following cryptography has been greatly developed. The above encryption is still traditional and not enough. Why is it big? The First World War, the Second World War is coming, there is no world war, mankind will not get nuclear fission so quickly; without the world war, cryptography will not be so leaps and bounds; without economic crisis, Nakamoto will release Bitcoin may take some time.
The wheel of history is rolling forward. If you want to look at the world from another angle and look at the current blockchain industry from another angle, please understand some cryptography.
The reason why I talked to the alchemists from French diplomats, from the Ming Dynasty Wanli fifteen years to the Xianfeng decade, on the one hand, the development of cryptography, China was left behind (note that it was before), on the one hand to increase some fun Only when the concept of science and technology enters everyone's mind will it usher in a real development. Another point is that cryptography itself is very boring, secret, and everyone does not care.
Cryptography has never been a manifestation, just as some truth is always in the corner of history .
Author: village two old
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Financial Times: Central banks should learn to include digital payments in China instead of issuing digital currencies
- DeFi is the future of the blockchain? See what the top international investment institutions say
- Viewpoint | Synthetic assets and values on Ethereum
- Iran re-examines the details of encryption mining supervision, electricity prices rise or "capital flight"
- The Fed may cut interest rates again on Wednesday, will the encryption market benefit?
- The era of bitcoin payment is coming soon? Maybe the Burger King incident is just a flash in the pan
- The market is blooming everywhere, but the faucet is not performing well, and the vigilance is falling back at any time.





