Hardcore: Declassified U.S. Department of Justice sues Chinese OTC acceptor for money laundering
On March 02, 2020, the U.S. Department of Justice initiated indictments against two Chinese people named Tian Yinyin and Li Jiadong on the grounds of conspiracy to launder money and remittances without a license, and frozen all their assets. The reason is that between December 2017 and April 2019, the two of them helped the Lazarus Group, a hacker organization under the North Korean government, to provide a laundering service worth more than $ 100 million.
As the U.S. Department of Justice did not disclose the specific source of these stolen funds, the cryptocurrency trading path involving money laundering, and even the client Li Jiadong claimed that he was only a victim. For a time, this case became the focus of hot discussion in the media and in the field.
Which exchanges were stolen (the source of the stolen money), what is the specific money laundering path of the hacker (the crime process), and where did the two acceptors Tian and Li participate (on-chain evidence collection)?
As the U.S. Department of Justice did not disclose the names and addresses of the stolen exchanges and the key details of Tian and Li's involvement in the case, the blockchain security company PeckShield was involved in tracking research and analysis for the first time. 2. Obtain evidence and restore the ins and outs of the entire case with visual graphics.
- Dismantling the bZx event: just another advance transaction
- Watch out for "coronary virus": "death game" is questioned
- New crown epidemic hits the United States, CME Group suspends offline trading, Coinbase and other open remote offices
(Source: U.S. Department of Justice indictment document)
As shown above, things are briefly summarized as:
In the following pages, PeckShield will start from the source of the stolen exchange, systematically disassemble and analyze the specific path of hacking money laundering, and review and decrypt the entire process for you.
Generally, after a hacker succeeds, the money laundering process is roughly divided into three steps: Graphic dismantling: OTC acceptor money laundering case
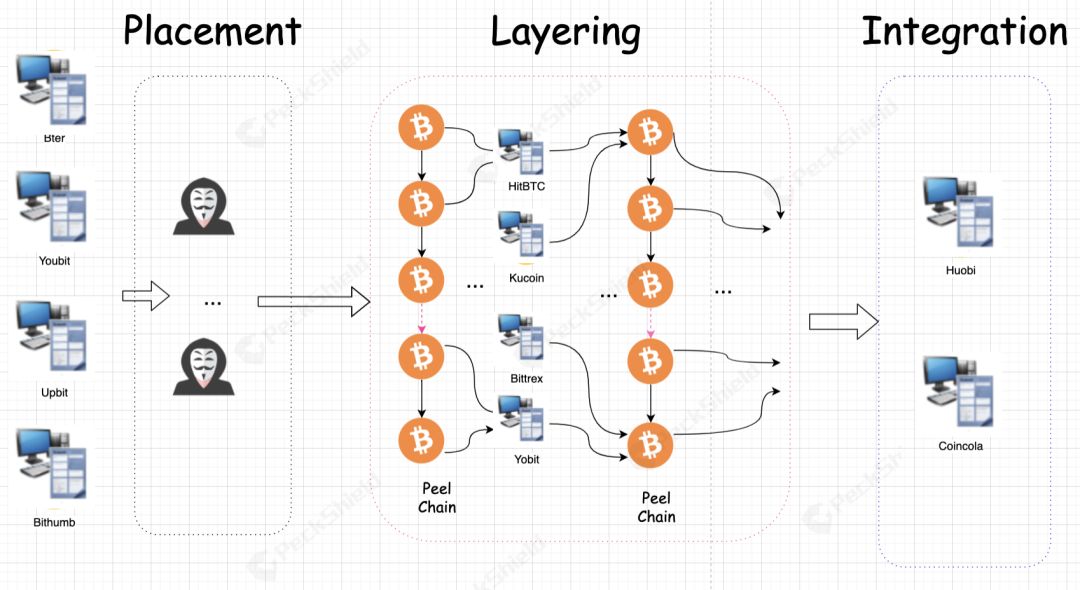
2) Layering: Layering is a systematic transaction and the most critical technology in the entire process. It is used to confuse the source of assets and the ultimate beneficiary, making the original illegal assets "legitimate income" ;
3) Integration: The "washed-out" assets are transferred "legally". After that, the traces of the illegal assets in the hands of the attackers have been wiped out and will not cause the attention of relevant departments.
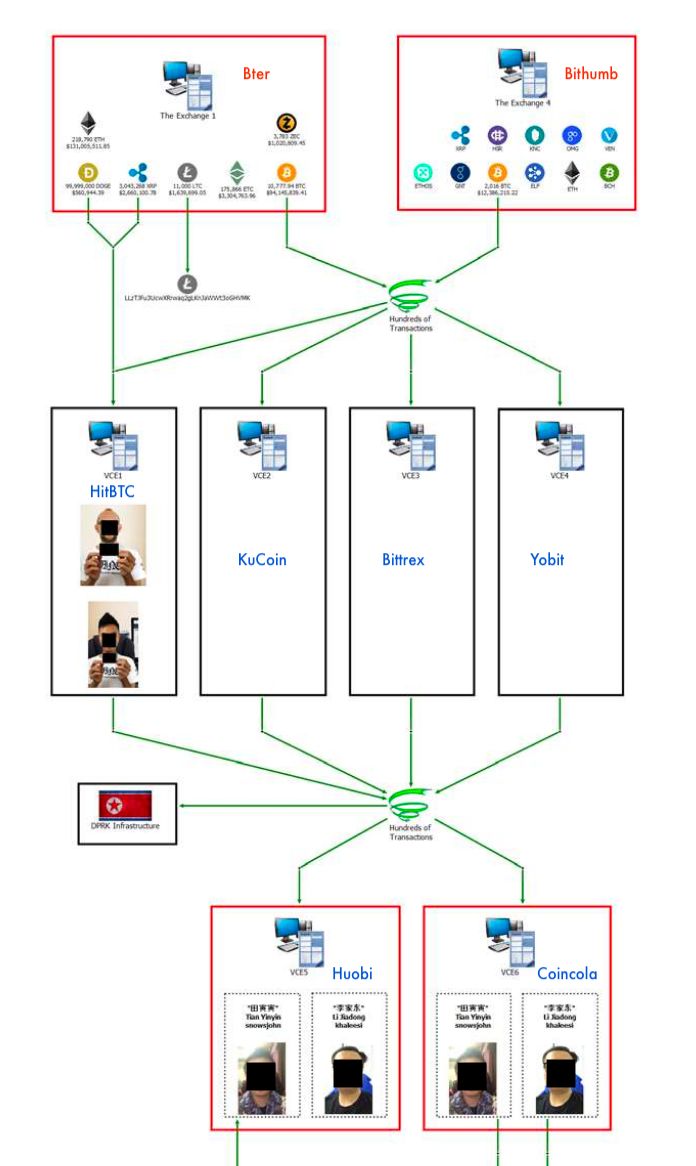
According to the information provided by the U.S. Department of Justice, four exchanges were stolen. The PeckShield security team traced the data of the 20 associated Bitcoin addresses of Tian and Li on the chain. According to the behavior characteristics of these chains, combined with the PeckShield exchange, The data of the theft database was eventually locked as the following four exchanges were stolen:
(Note: After the Bter exchange closed in 2017, its assets were taken over by another exchange. We still use the Bter name here)
I. Disposal phase: placing assets in the cleaning system
Within months of the theft of Bter, Bithumb, Upbit, and Youbit exchanges, attackers began to deal with their illegal profits through various means. Flow the profitable assets into an account that you can control to prepare for the next cleaning.
2. Separation stage: layered and confused assets escape tracking
During the analysis, the attacker tried to use Peel Chain's technical means to continuously split the assets in his hand into small assets and deposit these small assets into the exchange. In the following figure, we have selected a more typical splitting process. The first 2,000 BTC process is described in detail below (the other transaction processes are similar and will not be repeated).
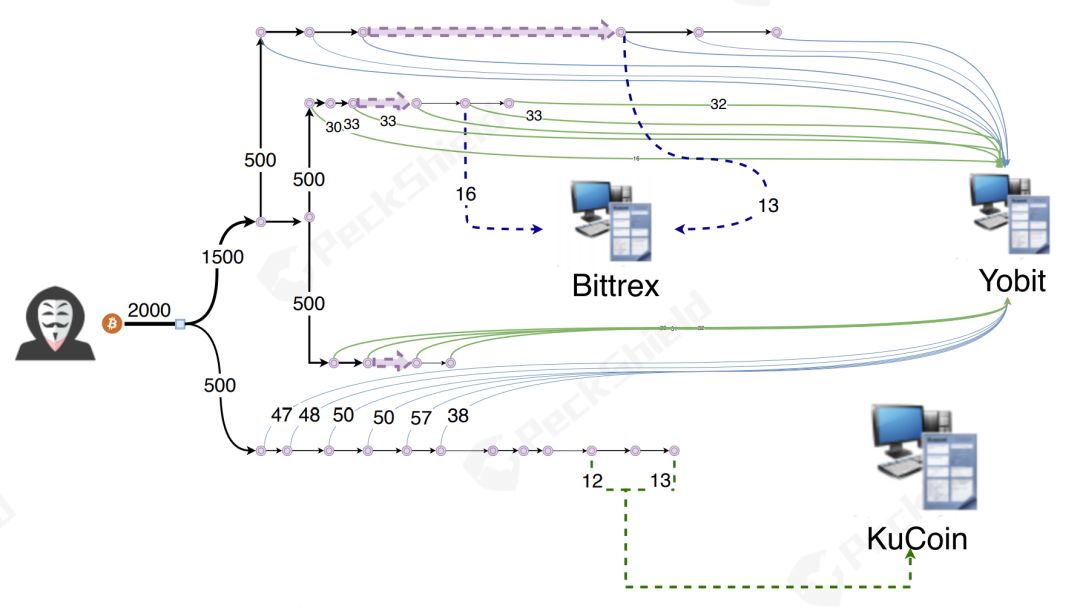
2) 1,500 BTC is split into three 500 BTC addresses. At this time, the original 2,000 BTC is split into four new addresses, and the balance in the original address has returned to zero.
3) 500 BTC will be converted into 20 ~ 50 BTC and recharged to the Yobit Exchange, and the remaining assets will be changed to a new address. At this time, a recharge is completed;
4) Repeat step 3 with the new address until the original 500 BTC is deposited in the exchange. During this process, the attacker also recharged records to other exchanges, such as Bittrex, KuCoin, HitBTC.
After the attacker went through this split process hundreds of times, all the original illegal BTC assets flowed into the major exchanges and completed the initial money laundering operation.
As shown in the following figure, we further analyzed and found that after completing the initial money laundering operation, the sly attacker did not directly transfer to his wallet, but used the Peel Chain method again to transfer the original illegally obtained BTC into OTC transactions in batches. Monetization. The attacker only separated dozens of BTC from the main account at a time and deposited it into the OTC account for cash. After dozens or hundreds of operations, the attacker successfully obfuscated and cleaned thousands of BTC.
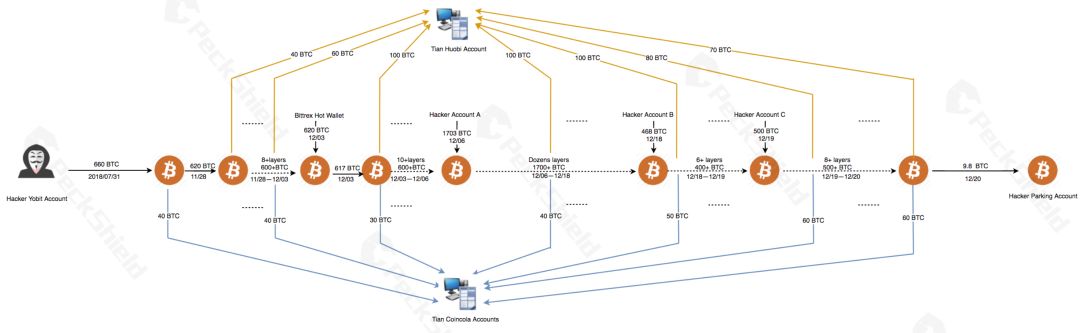
Third, the merger phase: integration of assets and opportunistic cash
After completing the previous money laundering operation, the attacker began to try to carry out OTC sell-off of illegal income.
In the process described in the figure above, from November 28 to December 20, 2018, the attacker deposited a total of 3,951 BTC into the OTC account of Tian Yinyin's Huobi and Coincola more than one hundred times, and the remaining ones 9.8 BTC are currently stored at the attacker's transit address.
Conclusion
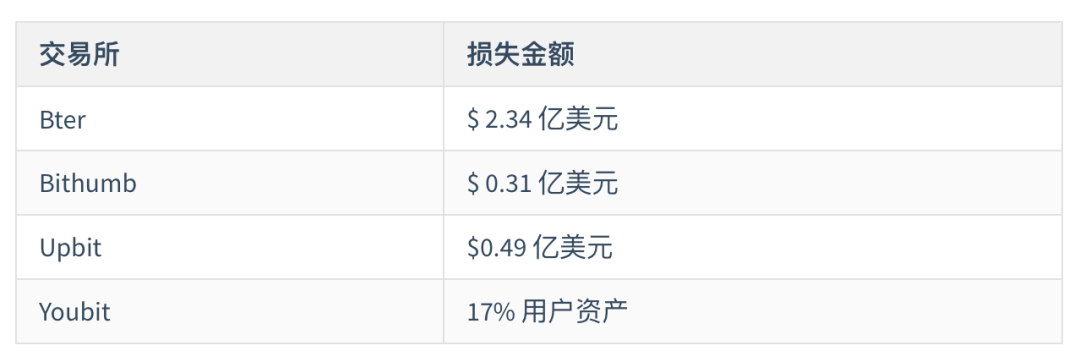
In summary, the PeckShield security team analyzed the ins and outs of the OTC acceptor's money laundering incident by tracking a large amount of on-chain data for analysis. The affected exchanges were Bter, Bithumb, Upbit, and Youbit. According to incomplete statistics, the loss was at least US $ 300 million. After the attack succeeded, the hacker implemented a professional, thorough, and complex decentralized money laundering operation in three steps. Partial cash.
According to PeckShield, hackers steal assets and carry out money laundering. Regardless of how thorough and complicated the process is, they generally use the exchange as part of the cash flow channel. This undoubtedly raises the requirements for the KYC and KYT businesses of major digital asset exchanges, and exchanges should strengthen the review of AML's anti-money laundering and fund compliance direction.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Cointems Chief Strategy Officer Meltem Demirors: US values align with cryptocurrencies
- U.S. stocks melt down and the currency market plummets. How should assets be allocated in 2020?
- Jeffrey Wernick: Wall Street is a slave to debt, and Bitcoin is free
- Upcoming SheKnows Event | What if the global economic crisis happens?
- Viewpoint | The premise of halving the price of bitcoin is that there is no financial crisis and focus on crypto assets out of the circle
- Anti-51% attack: Harvard MIT scholar proposes new theory of fighting double spend
- Market analysis: the market is still weak, holding the bullet in his hand






