To fill the shortcomings of the lack of identity layer, how to build a decentralized identity in the enterprise blockchain?
The adoption of Permissioned Blockchain is a challenging road . The application of Decentralized Ledger- based Web3 stack technology in complex enterprise business processes is still not mature. In the missing modules of the enterprise blockchain platform , the importance of identity as a next-generation enterprise solution has been raised to the top. We often face the challenge of enabling identity management capabilities in licensed blockchain solutions. Therefore, the identity layer of the enterprise blockchain solution is particularly important .
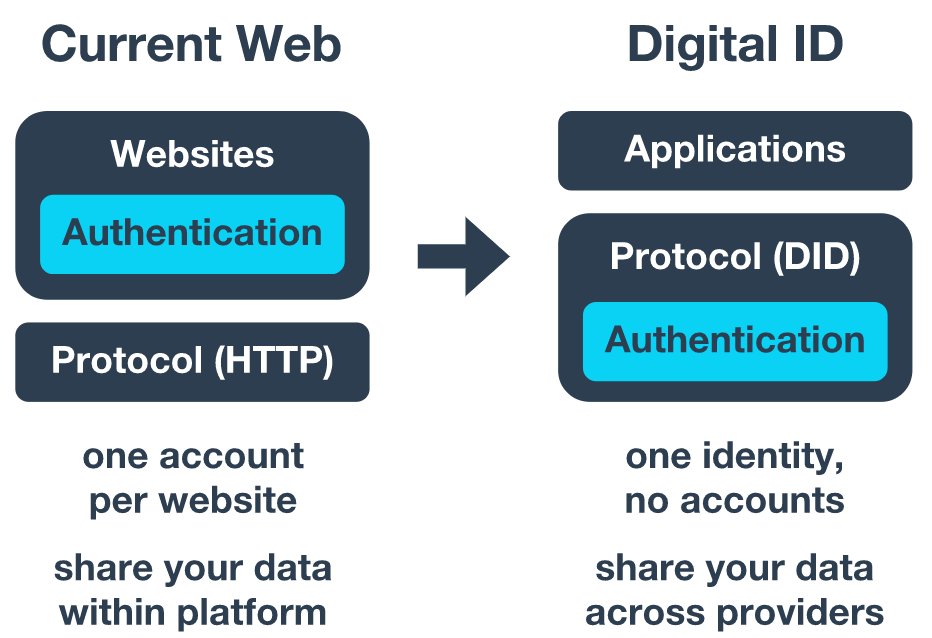
Over the past five years, with the advent of next-generation technologies, the identity management space has undergone a renaissance that transitions from complex systems such as CA and Microsoft Active Directory to more open systems such as Okta, Ping Identity, One Login, etc. API-driven platform, and the corresponding stack in cloud platforms such as AWS, Azure, or Google Cloud . These platforms move the capabilities of identity from private systems to open protocols such as SAML, OpenID Connect, and more.
- The first anniversary of the election of Wenzhou Gang and the left-behind node 丨EOS node
- Foreign media: Samsung is developing a blockchain based on Ethereum, and may issue coins in the future.
- Morgan Valley founder Pomp: Bitcoin may grow 20-50 times in 5 years, with a market value of more than 5 trillion US dollars
However, this does not mean that identity management technology is simple and easy to use. On the contrary, with the development of identity functions, the needs of identity management solutions have become more and more complex . The current enterprise identity management architecture has the following salient features:
Centralized identity providers : Identity management solutions typically rely on centralized identity providers who receive some form of user credentials as input and output for identity credentials .
Identity-based protocols : Currently, a large percentage of identity management solutions use protocols such as SAML and OAuth2 to interact.
· Segmentation : User identities in an enterprise environment are distributed across different business systems or user directories. Therefore, different applications tend to interact with different forms of identity .
Basic contradiction in enabling identity in the licensed blockchain
Putting all of these together, we get a picture where the user identity in the enterprise is distributed across many systems, but is enforced by the centralized identity provider. When it comes to identity, we need to address two fundamental contradictions between current enterprise architecture and blockchain technology .
· consensus vs approval
· Centralized vs decentralized identity assertions (Assertions)
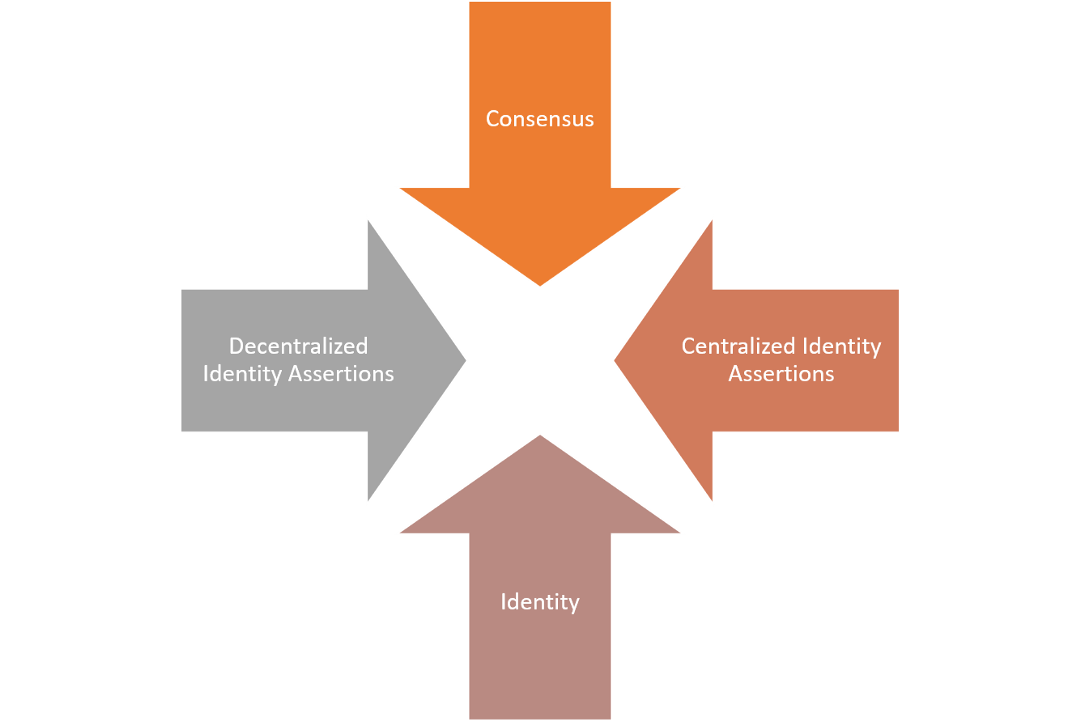
1) Consensus Vs recognition
Enabling identity management in a licensed blockchain scenario is not only a technical challenge, but also a contradiction with the underlying principles of the decentralized layer . The biggest contribution of blockchain technology is that in the history of computer science, we have a model for the first time that can trust mathematics and cryptography rather than relying on centralized parties. Based on this principle, blockchain architectures are developed based on consensus protocols such as Workload Proof (PoW) or Proof of Entitlement (PoS), which rely on calculations to make decisions. In the decentralized world, identity is not a basic building block because dynamic networks can achieve optimal decision making .
The computation-based blockchain consensus model is in stark contrast to enterprise solutions . In this sense, in a world of known identities, consensus agreements provide very little information.
2 ) Centralized vs decentralized identity assertion
The current architecture of the identity management system relies on a centralized gateway administrator to create assertions about user identities , and it is no easy task to coordinate this model with a distributed ledger architecture. Ideally, we need a model that allows identity assertions to be encoded and distributed to the relevant network in an encrypted manner over the chain .
Building a decentralized identity module in the licensed blockchain
To address these challenges, there are some technical components that are very relevant to the licensed blockchain architecture.
1) Proof-Of-Authority
Proof of Authority (PoA) is a consensus mechanism proposed by Gavin Wood, co-founder and former chief technology officer of Ethereum in 2017. This consensus model leverages the value of identity and relies on a limited number of block verifiers, which means that being selected as a block verifier relies not on the cryptocurrency of the mortgage but on the personal reputation. Therefore, the authority proves that the blockchain is protected by an arbitrarily selected verification node with a trusted entity.

In an enterprise blockchain scenario , the PoA consensus is important because it leverages the existing identity of users and systems , rather than relying on computational challenges. There are a number of license chain PoA consensus implementations that have several implementations related to the licensed blockchain, including parity and Microsoft Azure.
2 ) Decentralized Identity Agreement
In the decentralized world, the emerging decentralized identity domain appears to have made significant technological advances in identity methods and standards. In order to achieve decentralized identity , we need to re-architect identity and dynamically transfer many traditional identities to the decentralized network.
For the past 20 years, Microsoft has been one of the leaders in identity management, but even they realize that the blockchain needs a new identity model to run. Inspired by DIF, Microsoft recently proposed a forward-looking architecture to support the decentralized identity of the blockchain.
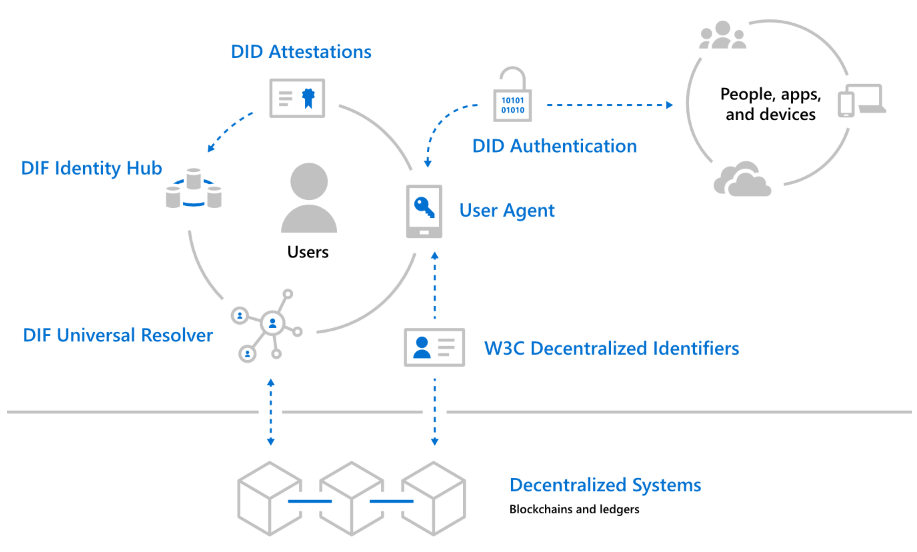
The Microsoft architecture includes the following components :
W3C Decentralized Identifiers (DIDs) : IDs users are created, owned, and controlled independently of any organization or government. The DID is a globally unique identifier that links to Decentralized Public Key Infrastructure (DPKI) metadata, which consists of JSON documents containing public key material, authentication descriptors, and service endpoints.
Decentralized systems : DIDs are rooted in decentralized systems that provide the mechanisms and features required for DPKI.
DID User Agent : The User Agent application helps create DIDs, manage data and permissions, and sign/verify claims with DID links . Microsoft will offer a wallet-like application that acts as a user agent for managing DIDs and related data.
DIF Universal Parser : A server that uses a set of DID drivers to provide standard lookup and parsing methods for cross-system DIDs.
DIF Identity Center : A replicated encrypted personal data storage network consisting of cloud and edge entities such as mobile phones, PCs or smart speakers for easy identity data storage and identity interaction.
DID Certification : Certifications signed by DID are based on standard formats and protocols. They enable identity owners to generate, present, and validate claims , which form the basis of trust between system users.
Under the framework of the licensed blockchain, the decentralized identity protocol establishes a clear bridge between the traditional enterprise identity management system and the blockchain DApps.
3 ) Zero knowledge proof identity storage
The concepts of authentication , declaring, and decentralization are some of the most important principles of the decentralized identity model. An interesting idea is to combine the concept of decentralization with a zero-knowledge proof protocol (such as zk-SNARKs) to add another layer of privacy to DIDs while allowing other protocols to verify identity . This concept can be called zero. Knowledge identity is stored and accepted by protocols such as uPort.
In the zero-knowledge identity storage model, assertions related to user identity are encoded using zk-SNARKs and published on the chain. Smart contracts can verify assertions about a user's identity without revealing any information about the underlying user's identity, while the underlying user performs a higher level of privacy while executing on the chain .
As a new technology, decentralized identity has some relevant cases to provide inspiration for the securities-based certification agreement .
uPort : uPort has been steadily building a set of protocols and solutions for managing identities in decentralized applications. The current stack is compatible with Ethereum Smart Contracts and can be used in licensed blockchain applications .
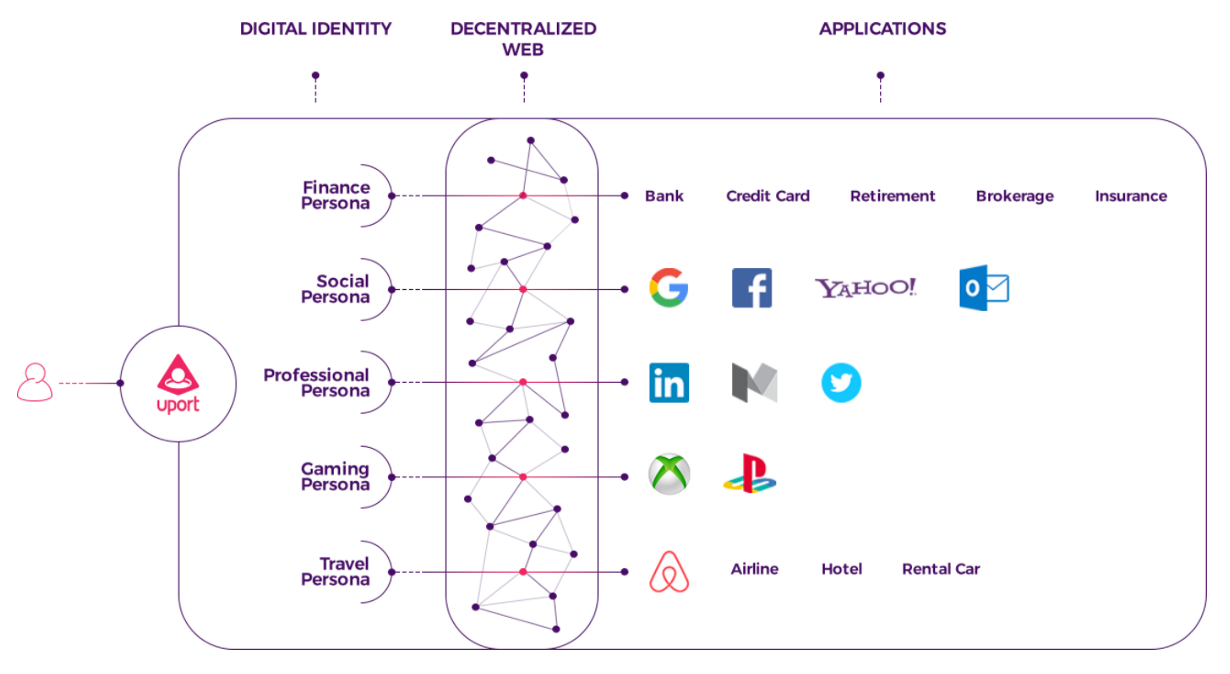
Azure BaaS : The Azure team has spoiled the core protocols of different blockchains to take advantage of Azure Active Directory identities. A recent example is the implementation of the PoA Consensus Protocol in the Ethereum application .
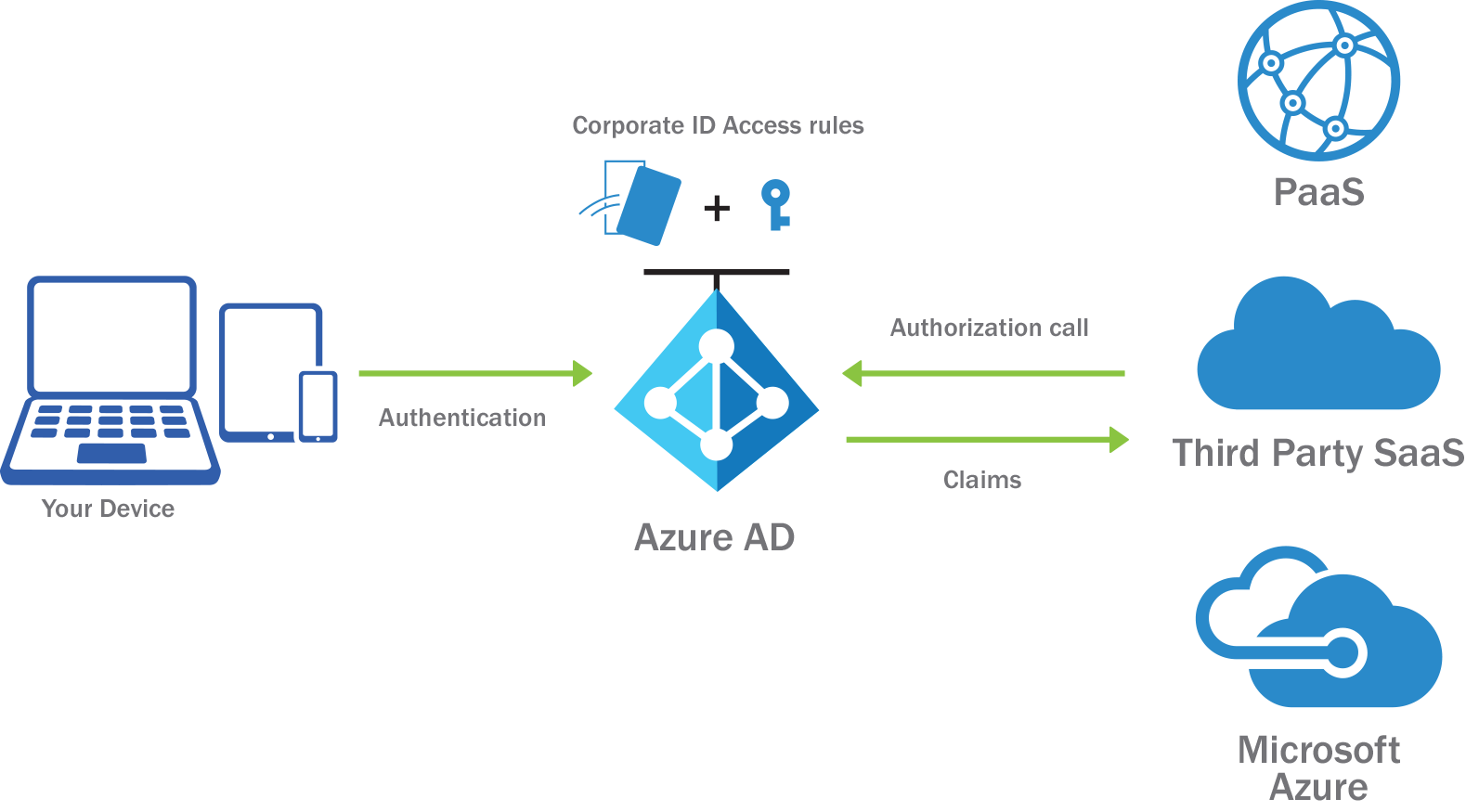
Sidetree : It is a combination of code-level components, including deterministic processing logic, addressable content storage abstraction, and stateful verifier that can be deployed in a Tier 1 decentralized ledger system (such as a public blockchain). On to generate a Layer 2 DID network without permission .
Hyperledger Indy : Indy provides one of the most complete stacks to support identity management . The current version of Indy includes tools and libraries that are some of the most common modes of implementing a decentralized identity solution.
As one of the basic modules of the blockchain application , decentralized identity is still in the process of being adopted by the mainstream , and still needs to solve the problem of how to connect with the real world . However, some organizations are working hard in this area. For example, the Decentralized Identity Foundation (DIF) is working to bridge the gap between traditional identity systems and blockchains . Although there are some protocols and tools in this area, enabling identity capabilities in enterprise blockchain solutions will still be a fairly complex task that requires the joint efforts of the blockchain industry and technology companies .
(Source: IDHub Digital Identity Institute)
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Identity Privacy and Compliance for Cryptographic Finance: About Zero Knowledge and Securities Pass Agreement
- Is the lightning network still far from life? Lightning Labs launches Alpha version of the desktop app
- Tulip foam or new generation internet? The New York Times talks about the future of Bitcoin
- Global giants are rushing to launch the BaaS platform, and the future lifeline of the blockchain is imperative
- From 9.3% to 1%, what does the blockchain-based transfer method bring to Africa?
- Babbitt column | Cai Weide: The rise of the blockchain industry, this time is true, but is there any regulatory preparation? (under)
- Stabilized Coin Series 3: DAI, a stable currency with hidden dangers?






