Identity Privacy and Compliance for Cryptographic Finance: About Zero Knowledge and Securities Pass Agreement
Privacy is one of the missing elements in current cryptographic financial solutions . The regulatory and cryptographically introduced identities in crypto finance are challenging many of the pseudonyms and anonymity concepts of cryptocurrencies . However, crypto-finance needs to have its own set of privacy requirements that are still largely ignored by the ecosystem.
Most people think that the idea that encrypted financial transaction information should be disclosed on public ledgers is not only naive, but also runs counter to many recognized best-in-class scales in the securities industry. Recently, we have been researching the application of zero-knowledge technology in the field of crypto finance to enable a more powerful identity privacy layer.
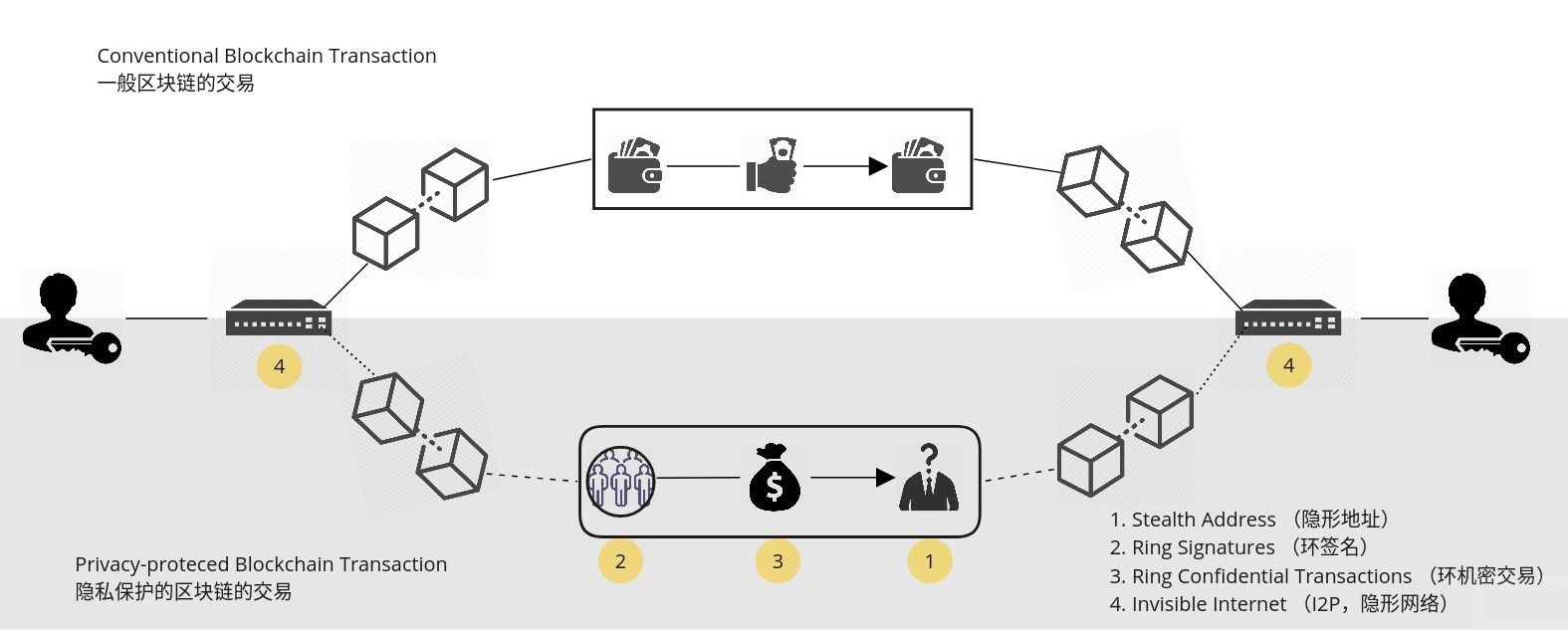
Identity challenge
Securities trading is subject to regulations such as “know your customer” (KYC), which requires participants to disclose their identity. However, these restrictions are primarily intended to demonstrate an investor 's compliance with certain securities terms , rather than to understand the identity of the investor itself. In other words, identity compliance is more of a " proof " than a " knowledge " , and understanding this difference is critical to enabling a new set of features in a cryptographic financial application. 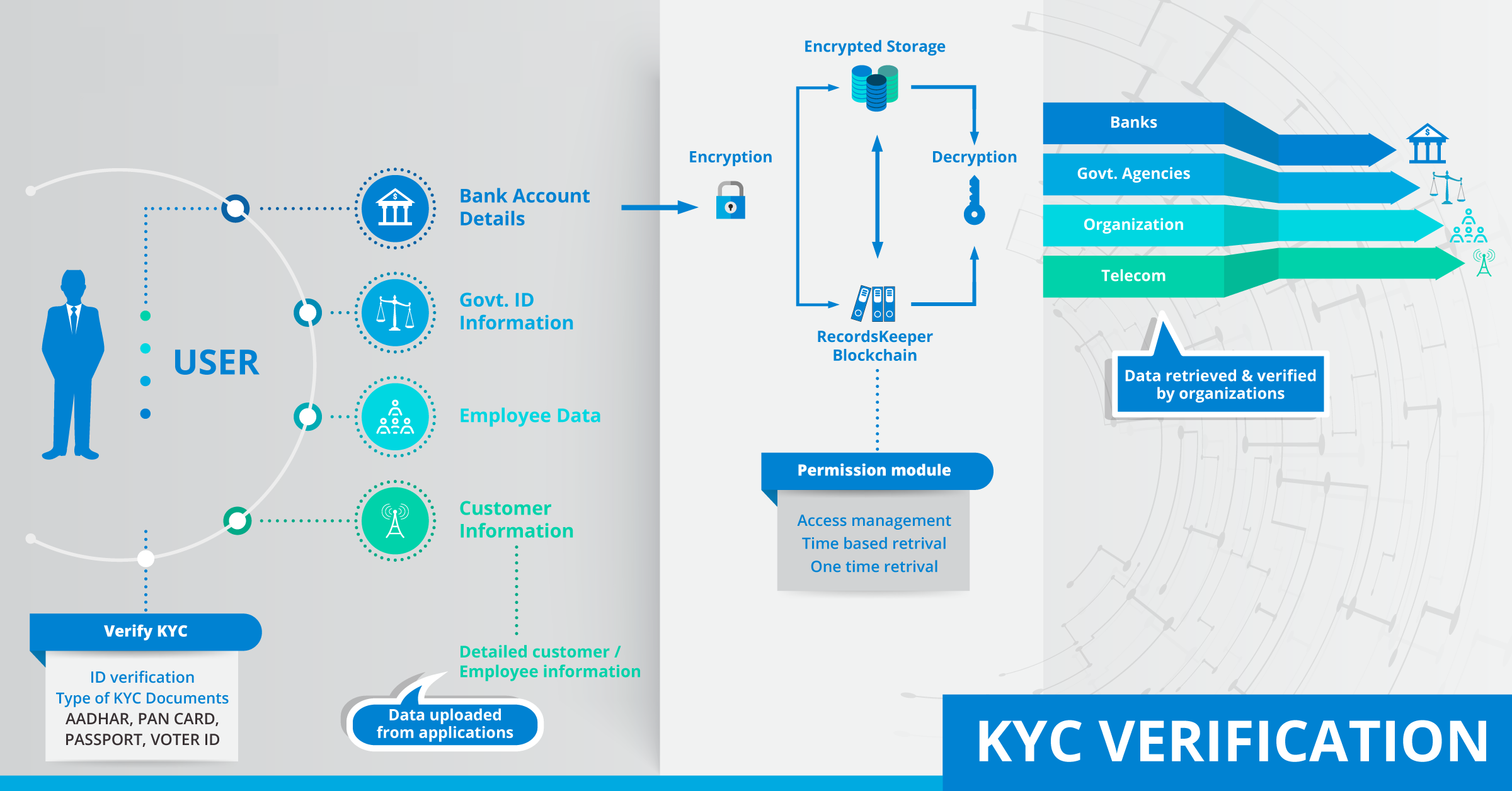
- Is the lightning network still far from life? Lightning Labs launches Alpha version of the desktop app
- Tulip foam or new generation internet? The New York Times talks about the future of Bitcoin
- Global giants are rushing to launch the BaaS platform, and the future lifeline of the blockchain is imperative
Conceptually, identity can be expressed as a series of unique assertions that define an individual or entity. In the field of crypto finance , the process of establishing identity by users has two main steps :
1) Identity creation : In this step, the trusted party compiles information about the investors and creates an identity based on those claims . For example, a KYC provider can collect investor identity or financial documents and assert that investors comply with specific regulations.
2) Identification : During the transaction, the investor's compliance requirements are verified to approve or reject the transfer.
In many current crypto-finance platforms, the identity creation step is enabled by a trusted KYC provider, and the authentication step is typically performed by a centralized service invoked by the smart contract . 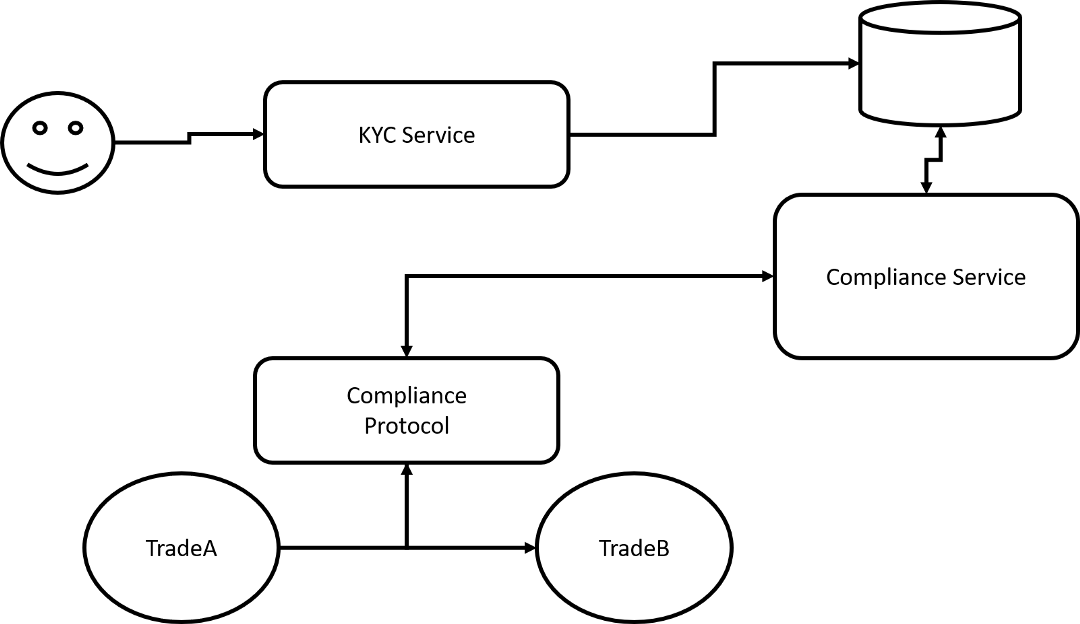
Although this model is simple enough for many use cases, its results are very limited for other use cases, and these limits are related to the level of concentration of the model. Not only do you need to trust the KYC provider to post your identity information during the login process , but you also need to trust the compliance of the securities pass provider during the transaction . Although the identity creation step obviously requires a trusted party to maintain the investor 's identity statement, decentralization can be used during the identity verification phase , which opens the door to a variety of interesting scenarios.
Imagine if we were able to take an identity declaration in a way that is compatible with different protocols, while ensuring the complete privacy of the underlying participants. This model will enable the verification process to take full advantage of the blockchain consensus mechanism and naturally combine it with other encryption protocols.
A scaled type such as KYC on the chain is currently an active research area. One of the most interesting ideas about how to achieve this goal is to use a technology such as zero-knowledge proof to declare the identity of investors on the chain without disclosing potential identities.
What is zk-SNARKs?
If you are in the field of cryptography, you know that zk-SNARKs is the underlying protocol for encrypted networks like zCash. zk-SNARKs can be applied to multiple distributed ledgers , some of which are well-known examples include Quorum, or the AZTEC protocol of the Ethereum blockchain.
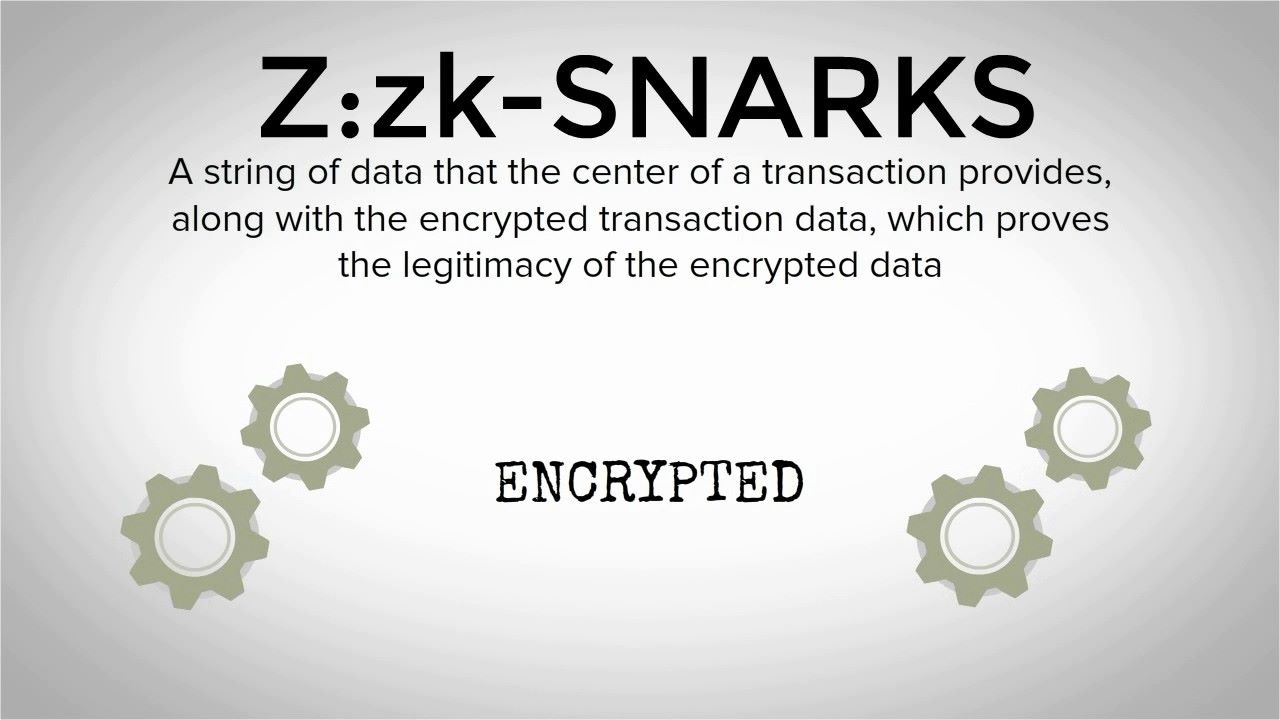
Fundamentally, zk-SNARKs outlines the interaction between the prover and the verifier. During the interaction, the prover attempts to prove to the verifier some assertion about his identity. If Zk-SNARKs is directly applied to the field of crypto finance, it will have the following benefits :
• Integrity : If the statement is true and the verifier and prover are honest, the proof is accepted.
• Robustness : If the statement is false, the cheater cannot convince the honest verifier to believe it is true unless the probability is small.
• Zero knowledge : If the statement is true, the verifier will not know anything except that the statement is true .
• Simplicity : The generated zero-knowledge evidence message is small enough to be verified in a few milliseconds compared to the actual calculated length .
• Non-interactive : The certifier only needs to send a message to the certifier according to the agreement , and the certifier can verify it according to the agreement.
• Knowledge : For a certifier, it is impossible to construct an effective zero-knowledge evidence without knowing the specific proof .
zk-SNARKs and encryption finance
If some of the principles of zk-SNARKs are applied to cryptographic finance , we can consider a model in which assertions about specific investors or entities are handled by the zk-SNARKs function and stored as part of an encrypted financial intelligence contract . Assertions can include citizenship, liquidity levels, certification, and more.
During the transaction, the investor acts as a certifier and the compliance agreement acts as a verifier. Different passes can have different compliance requirements based on specific zk-SNARKs assertions . A compliance protocol verifies a specific assertion without requiring access to the multiparty identity involved in the transaction . At the same time, zk-SNARKs indirectly decentralized the compliance part of the pass. This small change brings huge benefits because the protocol can now be used in other DApps without having to trust the pass-through distribution platform.
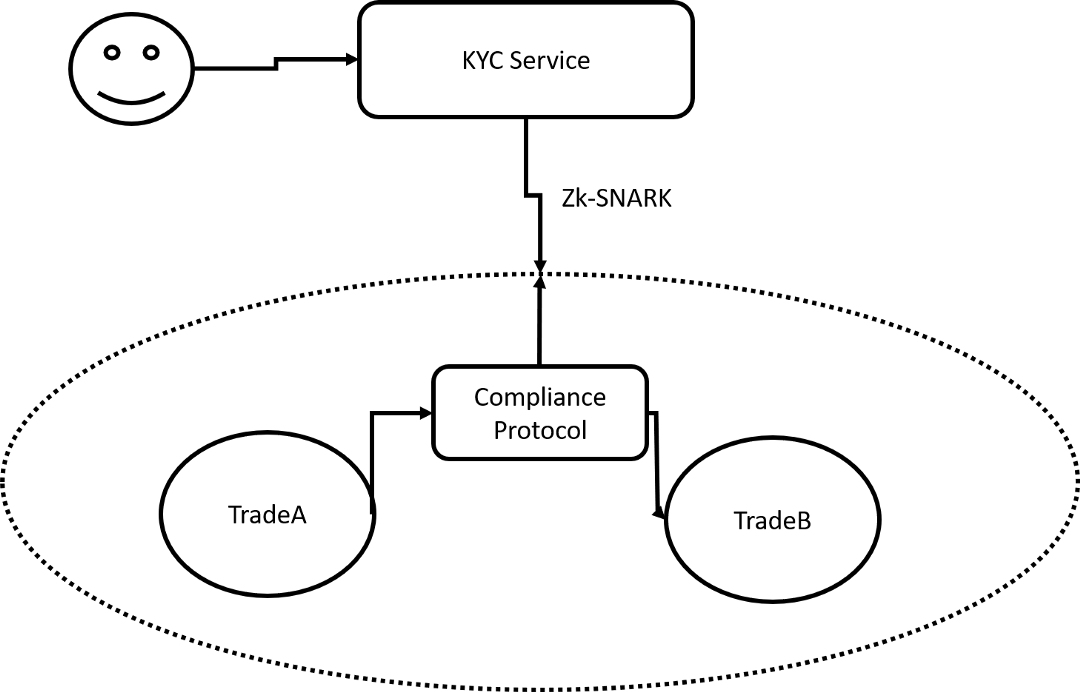
zk-SNARKs alternative
zk-SNARKs are not the only choice for implementing knowledge privacy in cryptographic financial protocols. In the blockchain of cryptographic financial protocols, several alternatives are gaining attention.
CryptoNote and Ring Signatures : CryptoNote is one of the originators of blockchain privacy and is the protocol behind Monero. CryptoNote uses an encryption technique called traceable ring signature to confuse messages between a group of nodes in a decentralized network. Improvements to the CryptoNote protocol have proven to be highly anonymizable when run at a scalable level. Therefore, CryptoNote can enhance privacy protection for specific parts of the pass .
zk-STARKS : One of the challenges of zk-SNARKs is that it is difficult to apply on a large scale because the complexity of the proof grows linearly with the size of the database. Not long ago , Professor Eli-Ben Sasson of the Israel Institute of Technology published a paper describing the alternative to zk-SNARKs, which he named zk-STARKS. In the paper, Professor Ben Sasson explained : “zk-SNARKs use public key (asymmetric) cryptography to establish security. In contrast, zk-STARKs require more succinct symmetric encryption, ie anti-collision hash function, so no need Trusted setup. These same techniques also eliminate the digital theoretical assumptions of zk-STARKS, which are computationally expensive and vulnerable to quantum computer attacks. This makes zk-STARKs faster and safer to generate. ”
Trusted Execution Environment (TEE) has become a popular way to remove confidential computing in blockchain technology . TEE technologies such as Intel's Software Guard Extensions (SGX) isolated code execution, remote authentication, secure provisioning, secure storage of data, and trusted paths to execute code. Applications running in a trusted execution environment are secured and are almost impossible to access by third parties. The pass can remove privacy calculations from the core blockchain using a trusted execution environment .
Secure Multi-Party Computations (SMC) is a cryptographic technique that allows calculations to be performed on a set of inputs while maintaining the privacy of the input . SMC can be used by parties in a pass-through transaction to exchange assertions about information while maintaining actual information privacy .
In the field of crypto finance , the idea of using zk-SNARKs to achieve compliance is complex, but an area that absolutely needs to be explored. This model not only introduces a very important privacy layer in cryptographic financial transactions , but also supports decentralization , opening the door to new scenarios for crypto- dealing transactions.
(Source: IDHub Digital Identity Institute)
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- From 9.3% to 1%, what does the blockchain-based transfer method bring to Africa?
- Babbitt column | Cai Weide: The rise of the blockchain industry, this time is true, but is there any regulatory preparation? (under)
- Stabilized Coin Series 3: DAI, a stable currency with hidden dangers?
- This hack is not normal! By guessing the private key, I successfully stolen 45,000 ETHs.
- Remember the coins? Venezuelans really started using it.
- Blockchain city map
- Babbitt Column | How will blockchain technology transform the “Great Moving Cloud” system? (on)






