Anatomy of blockchain defects (below): scenario security
In fact, innovative technologies will spread like wildfires, and only in the practical stage will there be limitations. The same is true for blockchain technology.
A new technology, we will find its advantages, and then Imagine can be ideally applied in a variety of scenarios, from personal private clouds to precision poverty alleviation, from original articles to charitable donations, but the actual "killer application" is still Bitcoin and Ethereum are limited to cryptocurrencies in purely virtual economies. According to the survey report, in the world in May, a total of 84 blockchain application projects were disclosed, with 37 in the country. Distributed in the three major areas of finance, traceability, and government affairs, and even new blockchain application pilots such as blockchain electronic deposit platform, housing mortgage loan platform, land acquisition and resettlement fund management, and valuable watch traceability. Although the blockchain system that solves the actual needs in the real society is numerous and full of flowers, it is a small-scale exploration and attempt, and even forcibly manufactures application scenarios. There are very few successful scalers.
Each technology has its limitations, and they will eventually evolve or become obsolete. Since the birth of Bitcoin, the blockchain has come a long way, featuring decentralization, traceability, irreparable modification, unforgeability, non-repudiation and programmability. In the previous media, you can always see the wrong habit of unifying the blockchain and bitcoin, as if the two are basically synonymous. I have hardly heard non-programmers talking about SQL and NoSQL databases, although they have different storage styles for relational and non-relational databases. Blockchain is also a kind of database storage technology, but it is concerned by the public because of the value-added prosperity of Bitcoin. Of course, this is inseparable from the media's help. Any related phenomenon involving cryptographic signature and data reconstruction is placed under the umbrella of “blockchain”. Traditional companies and institutions also find a fashionable buzzword and distort it. It claims to belong to its section.
The book "Block Chain Core Technology Development and Application" published by Mechanical Industry Press believes that the current blockchain technology has limitations in mathematical tools, game theory, cryptography, code, etc., and there is still much room for improvement. The "Journal block security issues: research status and prospects" of the Journal of Automation also comprehensively discusses the security challenges of blockchains facing actual network conditions.
- Blockchain thinking – prologue
- Business 3.0: A community-oriented, community-owned and operated $100 trillion economy
- Staking: New wave of mining under the PoS era | PoS series (1)
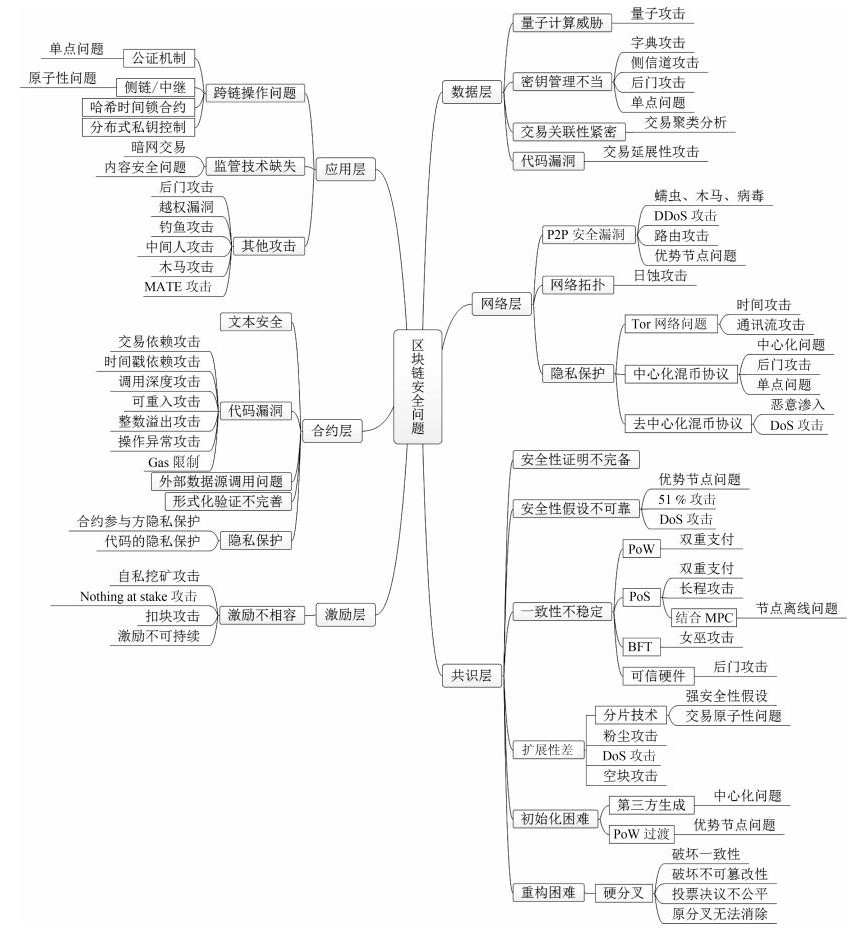
The transaction and block entities in the blockchain data layer involve various cryptography such as public key cryptography, digital signature, hash function, and privacy protection technologies such as component ring signature and zero-knowledge proof, but with quantum computing The rise of existing cryptographic algorithms will face the danger of reduced security or even compromise. Blockchain applications generally lack effective key management technology, and key leakage and loss caused by improper use and storage bring great benefits to digital asset users. The blockchain allows users to have multiple pseudonyms, providing only weaker user identity anonymity. Through transactional profiling and transaction clustering analysis, the true identity of the owner can be inferred based on transaction characteristics. Some cryptographic components may also have defects and vulnerabilities during the compilation process. Transactional extension attacks are often used for attacks against cryptocurrency trading platforms.

The security problems of multiple network technologies included in the blockchain network layer will inevitably bring security risks to the blockchain network layer, including P2P networks lacking identity authentication, data verification, and network security management mechanisms. The network topology of nodes will also be It is convenient for the attacker to carry out the attack, and the association between the network transmission user IP address can also be monitored and tracked.
The consensus layer is the core of the blockchain architecture. According to the basic protocols adopted, it can be divided into five series, including PoW, PoS, Byzantine fault tolerance, fragmentation technology, and trusted hardware. The development of the consensus mechanism on the blockchain is not yet Perfect, there are widespread problems such as incomplete security, unreliable security assumptions, poor scalability, unstable consistency, difficulty in initialization and reconstruction, and different types of consensus mechanisms face different threats.
The incentive layer and the consensus layer of the blockchain are interdependent and jointly maintain the security and stability of the blockchain system. The main problem that the incentive layer needs to solve is the incompatibility of economic incentives, which means that the miners involved in maintenance will not implement A malicious attack that jeopardizes security, but will guide its mining strategy with maximum self-interest. This strategy conflicts with the overall interests of the blockchain, destroying the efficiency and stability of the blockchain system, including self-propelled mining attacks. Nothing at stake attacks, block attacks, and incentives are not sustainable.
The smart contract is the core of the contract layer. It was first proposed by Nick Szabo and later redefined by Ethereum. However, because the smart contract code is open source and involves digital asset transfer, once the code vulnerability is exploited, it will cause irreversible damage. In addition to the text security issues of smart contract creators when designing business logic, the contract layer also faces issues such as smart contract code vulnerabilities, external data source calls, lack of formal verification, and difficulty in implementing privacy protection.
The application layer refers to the blockchain technology has a wide range of application scenarios in the fields of finance, supply chain, energy, etc. As a blockchain hierarchy that directly interacts with users, it is generally required to have an API interface, a cross-chain heterogeneous and Regulatory technology, and currently seems to face problems such as cross-chain operation difficulties, lack of regulatory technology and application layer attacks.
In summary, we will always “perfect” the blockchain technology. In the eyes of economists, cryptographers, and computer scientists, there are still many areas for improvement in blockchain technology.
Blockchain is an undeniable ingenious invention, but there are also a lot of deficiencies that plague technical experts and industry practitioners, including security, performance, cost, energy, privacy, supervision, redundancy, complexity, loopholes, speculation, and original data. Pseudo. Undoubtedly, the inherently liberalized technical features of the blockchain will also lead to contradictions and conflicts between the game of ideals and reality and the inner workings of the real society.
How to make full use of the new technical characteristics of blockchain, explore realistic scenarios suitable for blockchain technology, and obtain data from the underlying blockchain data structure, cryptography, communication network, consensus game, economic incentives and programmable contracts. Breakthrough and gradual innovation have made the blockchain technology truly land, which is the common ideal and task of the industry.
Please also read the same series of articles:
1. Analyze the defects of blockchain (top): impossible triangle
2. Anatomy of blockchain defects (middle): tool cost barriers
Article source: Youyou Finance
Author: Fu Hui
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Babbitt column 丨 G20 began to implement a unified encryption asset standard
- Dismantle MimbleWimble's privacy magic (part I)
- Lightning Network (on)|How to break through the ternary impossible: Re-implement the principle of lightning network technology with Solidity language
- V God personally wrote an article explaining the US Treasury’s Encrypted Assets Supervision Act
- Twitter Featured: Facebook Encryption Project Launched This Month; Wu Jihan will launch a new company Matrix by the end of July
- What is the recent popular Staking, is it worth investing?
- Listed company tracking | Zhongan Online: Pushing insurance products to pass






