Babbitt column | Blockchain in the digital economy helps face recognition applications new ideas
At present, face recognition technology is widely used in the construction of smart communities and smart cities. The face recognition system built from this is also the core support platform for public safety command facilities, and it is also a key part and an important source of information for the entire smart perception system. Face recognition is a kind of biometric recognition technology based on human facial feature information for identity recognition. It uses the features of facial feature information such as high accuracy, easy to use, strong stability, and difficult to imitate. In a video stream containing a human face, the human face is automatically detected and tracked, and then a series of related technologies are applied to the detected human face, thereby quickly realizing identity recognition. It is often called portrait recognition or facial recognition.
With the further maturity of face recognition technology and the continuous improvement of social recognition, face recognition systems have been widely used in many fields. For example, in terms of enterprise and residential security management, there have been access control and attendance, face recognition and anti-theft doors, etc .; in terms of information security, electronic passports, ID cards and other documents are compared; for public security, public security, border defense, and judicial departments have adopted Face recognition for criminal investigations, search for fugitives; information security, such as face recognition for mobile phone unlocking, computer login authentication; when conducting business in e-government, e-commerce, and banking, pass the original password, ID card and current The face recognition technology is used for authentication comparison, so as to complete the authentication verification of the party's identity efficiently and safely, thereby greatly increasing the security and reliability of related fields. In addition, some advertising companies apply face recognition technology to outdoor advertising to count human traffic, and even facial expression recognition and face-changing techniques developed based on face recognition technology can be used in fields such as entertainment, games, and commercial drainage.
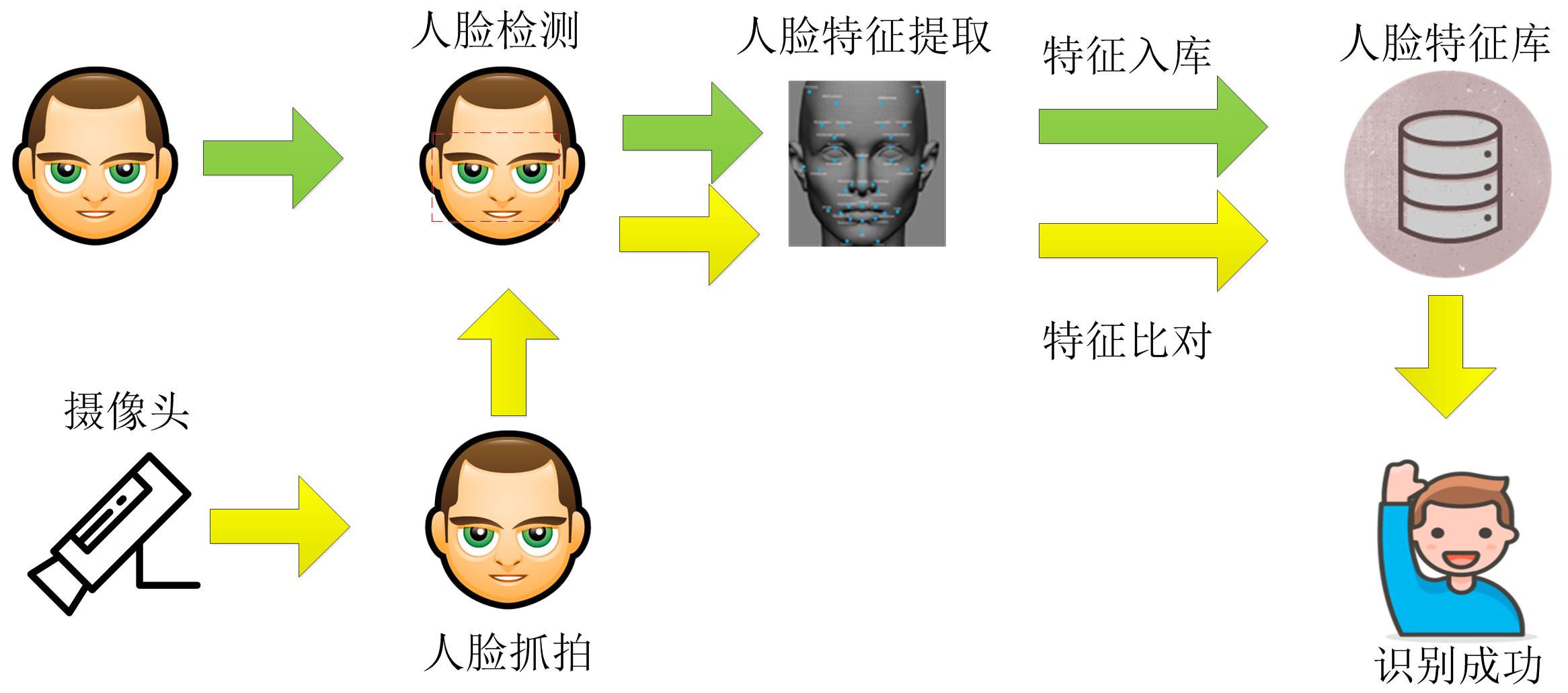
(The picture is from the book "Zero Basics Blockchain")
- BCH halving is approaching, are you ready?
- YeeCo Guo Bin: Blockchain + 5G, how to unlock the new scene of the Internet of Everything 丨 Chain Node AMA
- Analysis | Bitcoin's dual structure breaks at the same time, and $ 8,000 has become a thing in the bag?
Face recognition technology is mainly divided into three parts: face detection, face feature extraction and feature comparison.
Face detection: accurately locate the position and size of a human face from a static picture or a dynamic video stream output from a camera, that is, key areas of the human face, including eyebrows, eyes, nose, mouth, chin, and facial contours. Due to factors such as illumination, posture, and occlusion, accurate detection of key areas of the face is an important step.
Face feature extraction: Also known as face representation, it is a process of feature modeling for face. Feature modeling first requires face feature points, that is, feature data of key areas of the face. These feature data reflect the local relationships of various parts in the key area and the mutual relationships between them. For example, the shapes of human face organs such as eyes, nose, mouth, and chin constitute the local feature points of the human face, and the characteristics such as Euclidean distance, curvature, and angle between these local feature points form the geometry of the structural relationship between them. Description, also known as geometric features, these local features and geometric features together constitute face feature data, which are used as important data to identify faces.
Feature comparison: The final result of face recognition will be presented in this step. The extracted facial feature data to be analyzed are sequentially compared with the feature data stored in the feature library, and the identity information of the human face is determined according to the degree of similarity. By setting a threshold threshold, when the similarity between the feature data to be analyzed and the library feature data reaches or exceeds this threshold, it is determined that the face recognition is successful, and the identity information corresponding to the feature data in the feature library is the camera The identity information of the captured portrait.
Before running the face recognition system, it is necessary to establish a face feature database, that is, to establish an object face database that needs to be recognized, that is, we often say a snapshot library, a face registration library, and a black and white list library. We generally detect the object's face from the object's photo or video containing the object, and then extract the feature data of the object's face and put it into the database. The face feature database is essentially a face database, which is used to store face feature data that needs to be recognized.
Secondly, the front-end camera installed indoors or outdoors captures real-time face pictures, and sends the pictures to the back-end face recognition system for comparison. If the comparison is successful, the face recognition results are output.
The above is the working principle of the face recognition system.
With the continuous exploration and application of blockchain technology in various industries, the fusion application of blockchain + face recognition has also received more and more attention.
The current application scenario mainly uses the decentralization of blockchain technology. The data on the chain cannot be tampered with, open, transparent and traceable. By creating an exclusive confidential box containing personal privacy, personal privacy data such as identity information and loved ones Information, photos, etc. are placed in the safe box and uploaded to the blockchain storage, while using the unique characteristics of the human body-face feature data, as one of the keys of the exclusive safe box, other keys may be lost, but people The facial feature data is taken from the facial information of the exclusive person, so it will not be lost or tampered with. In addition, the identity information in the confidential box can be used as the digital identity of the exclusive person in the blockchain network, and the facial feature data becomes the key to the digital identity, which can achieve decentralized user identity verification. Personal digital currency assets, personal medical data, personal education information, Internet of Things information, etc. stored on the blockchain can all be associated with it, thus realizing the identity connection between the blockchain network and the real world.
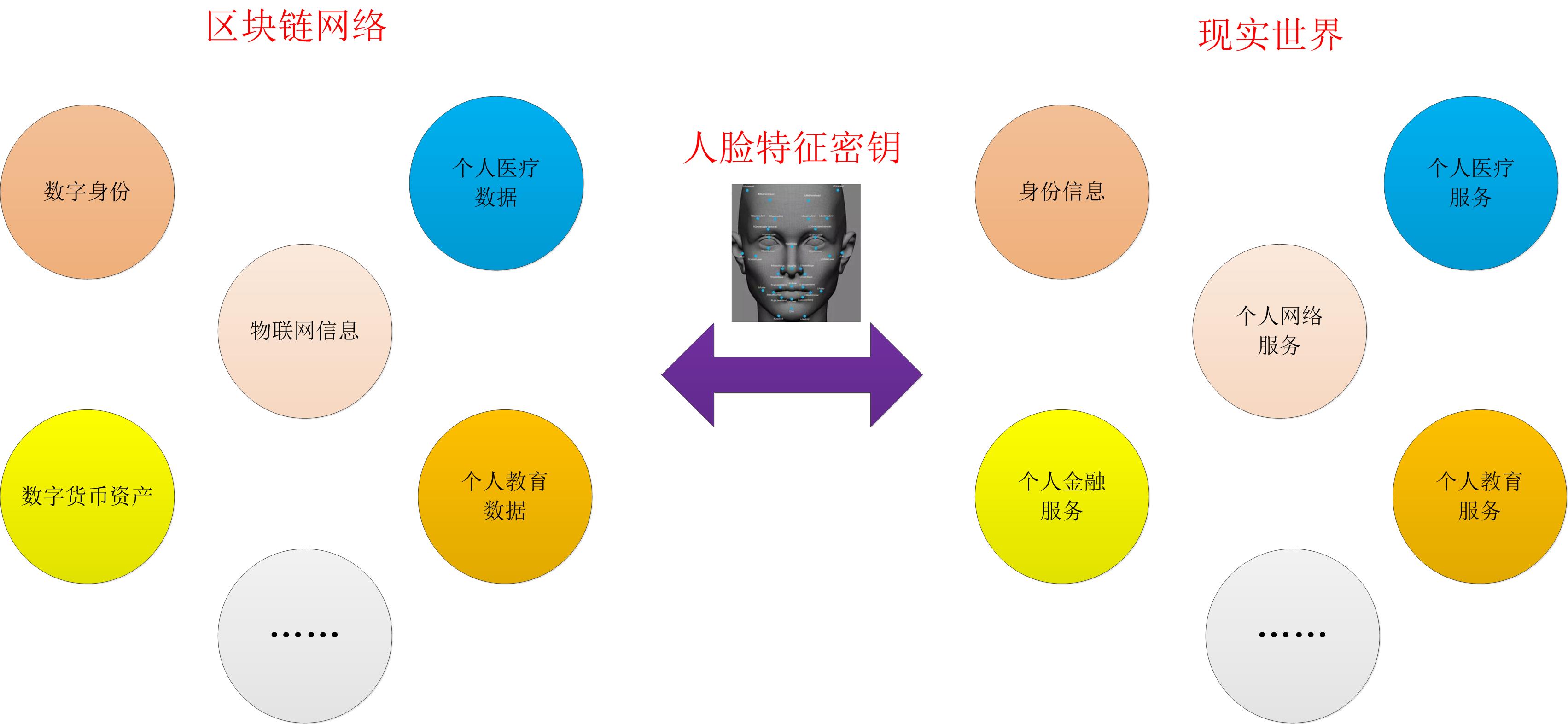
Face features become the link between the blockchain network and the real world
In addition to the facial feature data introduced earlier as the exclusive token key on the blockchain, you can also store the facial feature data in the blockchain. Here is a special application-finding child trafficking and disappearance population. For example, the facial feature data of each age group of a child from birth are uploaded to the blockchain as the key to the child's unique digital identity (including birth certificate, biological parents and relative information, etc.). At present, most of the children who are trafficked belong to the younger age group and cannot describe personal information. Then, face recognition technology can be used to collect the facial feature data of the children, and then use it as a key to access the digital identity stored on the blockchain to be related According to the information of their biological parents and relatives, it can be judged whether the person with children is a human trafficker, which makes child trafficking more difficult and the success rate of arresting human traffickers is greater. For the rescue of missing people or homeless people, you can use cross-age face recognition technology to find their digital identity on the blockchain.
The above is the current main application of blockchain + face recognition, then this article will explain the application of a combination of blockchain and face recognition from a new perspective.
All along, the industry believes that the key factor affecting the promotion and application of face recognition technology is the quality of the recognition algorithm. The algorithm model trained by massive sample data is bound to be better than the model trained by a small number of samples. The model must be better than the model trained from indoor sample data. However, after several years of practical tests, it was found that the factors affecting the promotion of face recognition are no longer the difference of the algorithm, nor the lack of massive sample data. The mainstream deep learning algorithms are already mature, and the algorithm models have also been trained by big data. Its stability has been significantly improved, and the current bottleneck has been transformed into a subjectively considered computing power problem. The algorithm of face recognition has high requirements on computing power resources. In addition to GPU, a general-purpose chip with powerful computing power, chips dedicated to processing neural networks have also emerged in an endless stream and processing performance has also continued to improve, but with the future With the rise of networking, video image data will usher in explosive growth, so the application of face recognition technology will become more and more restricted by computing power. Large companies can accumulate hardware resources to increase computing power to cope with the growth of video data, but small and medium-sized enterprises have difficulty bearing huge hardware costs. At the same time, these costs will eventually be transferred to users, which will give people a face The comprehensive promotion of identification technology in society has caused great obstacles.
Here we use blockchain technology to create a low-cost, scalable face recognition system. The main idea is to use blockchain technology to achieve the integration of idle and scattered computing power to complete recognition tasks, so that enterprises or users do not have to Investing too much hardware cost to build a traditional face recognition system, thereby reducing operating costs.
The block diagram of face recognition system based on blockchain technology is shown in the figure below.
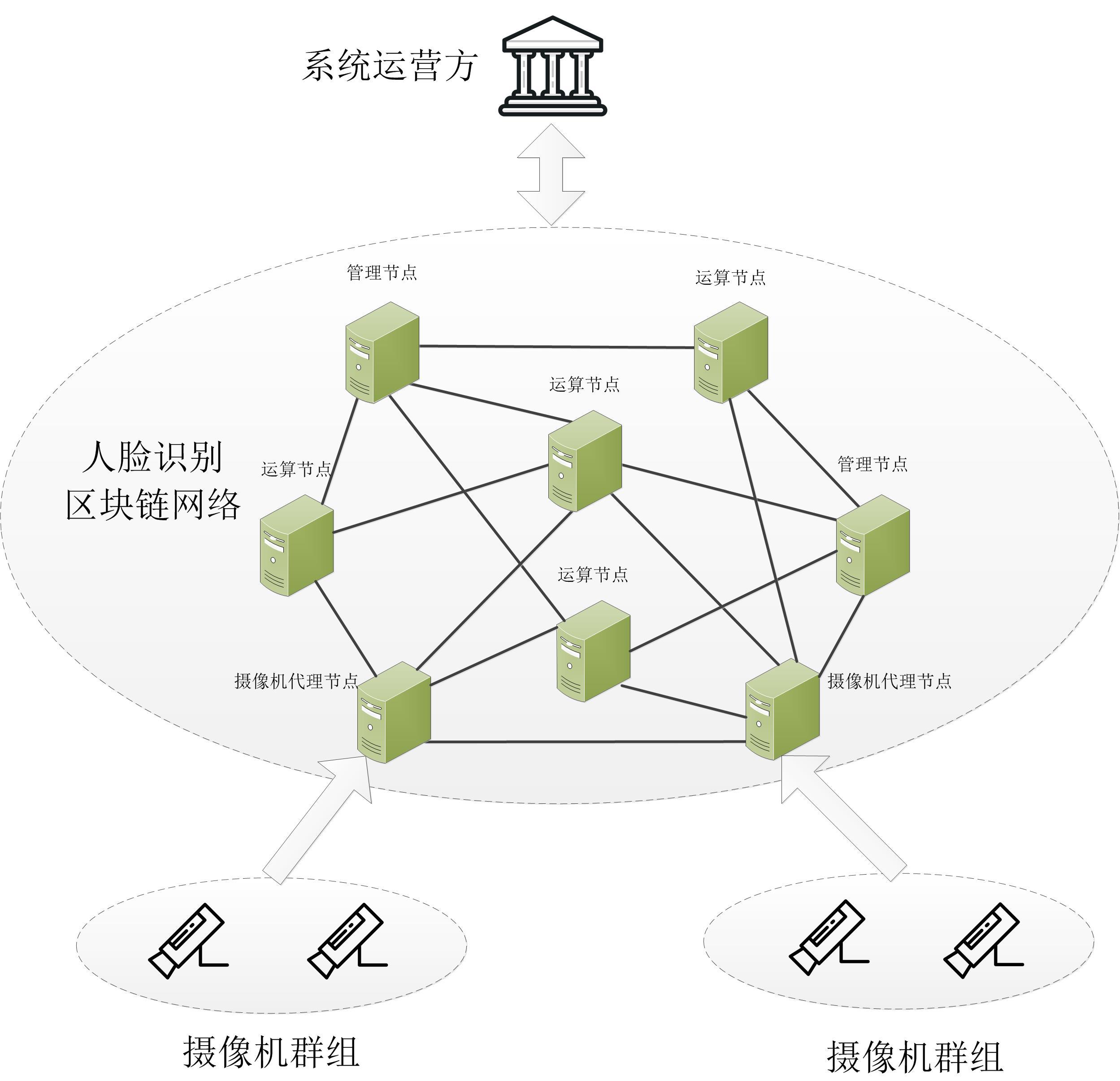
Block diagram of face recognition system based on blockchain technology
The whole system consists of camera groups, face recognition blockchain network and system operators. The functions of each part are described in detail below.
(1) Camera group: The camera group is mainly composed of several cameras deployed in different areas. They are responsible for transmitting the data collected on the scene to the corresponding camera agent node in the back-end face recognition blockchain network. The traditional surveillance network camera transmits the live real-time video stream to the back-end. The real-time video stream not only occupies the network bandwidth, but also increases the computing burden of the computing nodes in the back-end face recognition blockchain network, because the computing nodes need The face is detected from the real-time video stream. Even if there is no face in the video stream, the computing node still has to do face detection, which greatly wastes computing resources. Therefore, a dedicated face capture camera can be used. This type of camera has a built-in face detection algorithm in the internal chip. As long as the camera detects a person in the field of view, the captured face image will be passed back to the back end. Video transmission saves a lot of network bandwidth, which not only reduces the transmission burden on the face recognition blockchain network, but also reduces the computational burden on computing nodes.
(2) Face recognition blockchain network: The network adopts the alliance chain network architecture, which is composed of three types of nodes: management nodes, computing nodes, and camera proxy nodes.
Management node: It is a high-authority node, responsible for member access, designating internal supervision nodes, limiting query permissions, providing face recognition component download and update services, and maintaining blockchain data.
Operation node: It mainly completes face recognition tasks, including facial feature extraction and feature comparison; if it is selected as a supervision node, it is responsible for supervising whether the recognition result is accurate and maintaining the internal data of the blockchain.
Camera proxy node: Responsible for broadcasting the face pictures sent by the camera group to other types of nodes in the network. The node does not participate in the supervision work, nor does it participate in recording blockchain data.
(3) System operator: Mainly responsible for economic rewards and management of face data and face recognition components. The economic reward is to reward others for providing computing power to complete the recognition task; the face database is highly private information, and the ownership is in the system operator. The face database needs to be encrypted and then distributed to each computing node. Only the face recognition component can decrypt The data in the face database cannot be viewed by other nodes.
The workflow of the entire system is as follows:
The management nodes in the face recognition blockchain network are directly deployed and managed by the system operator. The system operator sends the face recognition component and the encrypted face database to each management node; if the face recognition component or face If the database is updated, it needs to be synchronized to each management node, and then the management node notifies the computing node to download the update.
The new computing node joins the network after being approved by the management node, and then downloads the face recognition component and the face database from the adjacent management node.
The camera proxy node uploads the face pictures from the camera group to the blockchain network. The pictures reach the computing node and the management node through broadcast. These nodes put the pictures in the local picture pool and follow the face pictures. The image blocks are constructed in order of timestamps. The computing nodes compete for image recognition through computing power. The computing node that wins the competition broadcasts the packaged image blocks throughout the network. After receiving the image blocks, other nodes first verify whether they should Whether the node really competes for the recognition right, after verification, delete the pictures that have been included in the block in the local picture pool, and then repackage the pictures to compete for the recognition right again. In addition to broadcasting picture blocks in the entire network, the winning computing node also notifies the management node that it has obtained the recognition right. After the management node is verified, the winning node is authorized to start the face recognition component to recognize the face picture, and the recognition result In the broadcast of the whole network, the node with supervision function shall verify the validity after receiving the result. Because the winning operation node is compared with 1: N, that is, the one with the highest similarity is identified from the N face database pictures, all N pictures need to be compared, and the verification of the supervising node only needs to take a snapshot The face image and the recognized library image are compared 1: 1, so the verification can be completed quickly, and the recognition result of the verification is recorded in the local blockchain. The blockchain can only be accessed by the system operator or a third party authorized by it.
The system operator gives economic rewards to computing nodes according to the recognition workload, which can encourage more and more idle computing power to join the recognition task. In the future, the system can settle by issuing national legal digital currency.
The above system flow is not suitable for application scenarios with high real-time requirements due to the packaging of face images and competition in computing power between nodes, but it is suitable for applications such as post-personnel search, trajectory analysis, and behavior analysis. This application idea is only a general plan for the face recognition system based on the blockchain. For the specific implementation and subsequent promotion of the business model, it is still worthy of in-depth study.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- ETH's single-day increase is close to 20%, and mainstream coins have followed suit
- Babbitt column | Case study: Exchange "downtime", does the holder lose any compensation?
- Millions of people watched, and the entire industry participated heavily. This cloud summit is stirring the "online rivers and lakes" of the blockchain
- Bitcoin is up 8%, and the bull market is in doubt?
- A week in review: Zhou financing event fell to 3, CMC was resigned by the founder of Binance M & A
- The Secret History of Bitcoin: The bitter Bitcoin puzzles of those years
- Yao Qian: What is the role and value of blockchain construction in epidemic prevention and control?






