Hackers are getting smarter, with the largest number of exchange attacks ever in 2019
Source | bitcoinmagazine
Translation | Huohuo Sauce
Production | Blockchain Camp (ID: blockchain_camp)
Currently, major cryptocurrency exchanges are constantly strengthening their security to defend against cyber attacks, and hackers are also improving their technology in the same way-according to the data, they are constantly achieving their goals.
- Cosmos director broke: Jae Kwon stepped down as CEO to avoid responsibility
- Is the option market, which suffered a shrinking trading volume at the beginning of the year, still worth watching?
- The central bank's trading gold blockchain platform helps corporate financing, and national project support breaks through development difficulties
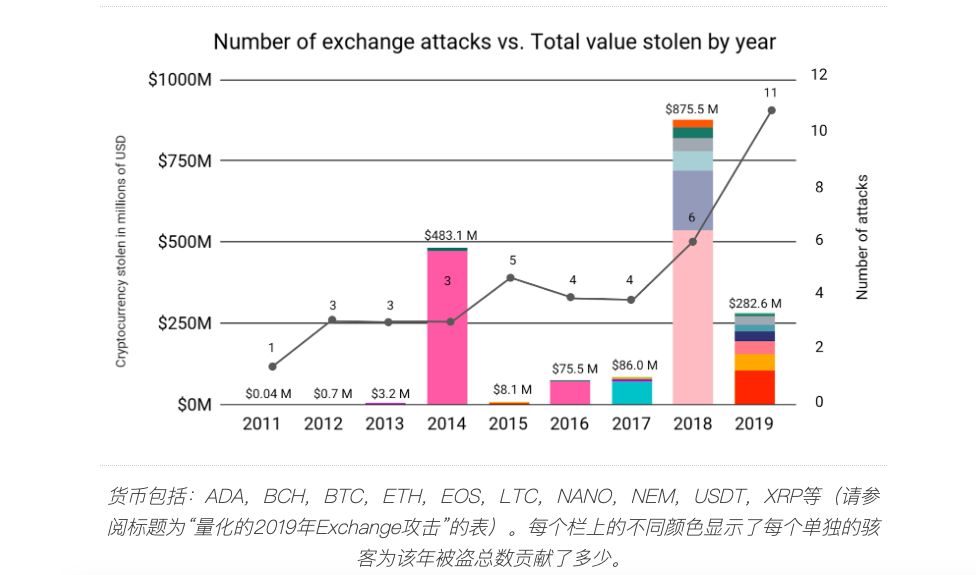
According to data compiled by blockchain analysis company Chainalysis for a recent report, since Bitcoin began trading on public exchanges in 2011, cryptocurrency exchanges have faced more successful attacks in 2019 than in any other year.
Although the number of 11 attacks recorded in 2019 was almost double the number in 2018, the overall loss was significantly reduced (the value of stolen cryptocurrencies in 2019 was $ 282.6 million and the value of stolen cryptocurrencies in 2018 was 875.5 million USD).
Report data connection: https://blog.chainalysis.com/reports/cryptocurrency-exchange-hacks-2019
The total amount of stolen funds in 2014 and 2018 (both more than the total amount of stolen funds in 2019) were the results of a far-reaching Mt.Gox attack (2014) and a $ 500 million Coincheck attack (2018).
Mt.Gox: https://bitcoinmagazine.com/tags/mtgox Coincheck: https://bitcoinmagazine.com/articles/following-massive-cryptocurrency-hack-coincheck-pledges-improve-operations-refund-losses
Excluding these two cyber attacks, 2019 is actually the year with the highest total amount of stolen assets through cyber attacks or similar attacks (such as phishing). However, the average number of assets stolen by each hacker last year was down from 2018. Chainalysis pointed out that by strengthening security and regulatory measures, this damage has been mitigated to a certain extent. For example, compared to previous years, more and more exchanges have reduced the amount of funds deposited into hot wallets.
"Although the number of individual hackers has increased significantly, data shows that exchanges have done a better job of limiting the damage caused by hackers than in the past," Chainalysis wrote in a blog post.
Cryptocurrency exchange hacker improvement strategy
Nevertheless, as exchanges improve their defensive capabilities, hackers are also improving their attack strategies.
For example, in a $ 40 million hacker attack on cryptocurrency exchange Binance in 2019, the attacker used a combination of malware and phishing attacks to bypass security measures and cover the multi-key signatures required for withdrawals .
40.02 million attack links: https://bitcoinmagazine.com/articles/binance-hacked-40m-ceo-backpedals-recoup-block-reorganization
As evidenced by Chainalysis's numerous studies, in this data warfare, as attacks become more complex, blockchain analysis becomes more and more complex. However, malicious actors will respond accordingly to closer scrutiny.
Specifically, they will use CoinJoin and mixers (actually never used before 2019, partly because reliable joining markets did not appear until the end of 2018), but with little effect, Because Chainalysis can still track funds relatively accurately.
Chainalysis economist Kim Grauer said in an interview with Bitcoin Magazine: In fact, in order to ensure that its methods are not exposed, researchers must be very careful when publishing research reports, so as not to give hackers a blueprint. "Since criminals can adjust their strategies to our capabilities, to what extent can we allow them to understand our capabilities?"
She added: "We have reason to believe that they know our capabilities." What this means is that hacking groups have discovered its urgency: not only to mix coins together, but also to transfer them to exchanges for liquidation. For example, before 2019, it was not uncommon for the infamous North Korean Lazarus Group to wait 500 days before transferring funds. But in the last year, the time has been shortened. Usually, the funds will be transferred to KYC's relatively loose exchange for settlement within less than 2 months after the hacking. Lazarus Group: https://bitcoinmagazine.com/articles/lazarus-hacker-group-continues-target-crypto-using-faked-trading-software
Although Chainalysis considers Lazarus to be the culprit behind many attacks, Chainalysis only released its $ 7 million DragonEx hacking data-as mentioned earlier, Chainalysis was reluctant because it feared that it would provide opportunities to evade surveillance. Revealed his suspicions that Lazarus was involved in other attacks.
cash
Although it is not possible to talk directly about the Lazarus Group, which is believed to have been involved in multiple exchange hacking attempts to fund North Korea's nuclear program, Grauer said "Tether is a cash for most other group funds important parts of". In other cases, criminals will want to convert altcoins to bitcoins.
It turns out that this is the last line of defense against cybercrime. It is true that Chainalysis and law enforcement have no control over what happened after the theft, but by working with exchanges, they can prevent funds from flowing out of exports.
Grauer cited a positive investigation into hacking in 2019 and said that these incidents have caused great attention from law enforcement. Now, Chainalysis hopes that exchanges can use their "know your trading know-your-transaction (KYT)" tool to monitor stolen funds and directly mark large transfers from the mixer, which may come from illegal gains.
According to the data from Chainalysis, about 50% of the stolen funds are still waiting to be liquidated in 2019. KYT measures (currently only adopted by Binance company) may help officials recover funds after the fact, but they also rely on law enforcement agencies to track and arrest criminal. Because as Grauer reminded, blockchain analysis is just one of the weapons in their arsenal.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Blockchain + epidemic fight: expose data to the sun
- Baton secures another $ 4 million in funding and completes $ 12 million in Series A financing
- Lava Interpretation | PoC2 + Upgrade: What Can the New Standard Bring to the PoC Field?
- Libra launch or meet resistance again: retreat storm, more rivals, can be launched in 2020?
- Multi-party secure calculation of MPC is hot, how to manage keys through MPC?
- Nasdaq Research launches Bitcoin futures, fierce competition on digital currency track
- Technology Sharing | "Junk Input and Junk Output" of Blockchain Technology




