Breaking the Impossible Triangle of the Blockchain (6)-Blowing a Whistle on the Activity of the Blockchain
Author: maxdeath, Click "breakthrough Block Chaining impossible triangle" series
Finally, we return to the "security" quoted in the previous article, because there happened to be such a paper on the security of Lightning Network recently: https://arxiv.org/pdf/2002.06564.pdf , and we take this Let's talk about the off-chain technology and the security of the blockchain.
Lightning network activity risk
First, let's review the two basic meanings of the consensus that I mentioned earlier on Byzantine fault tolerance:
1. Consistency.
- Beijing issued the first blockchain electronic invoice, parking tickets and park tickets will be included
- "Half" and "Fed rate cut", the two big exams Bitcoin faces
- Heavy! Indian cryptocurrency ban unconstitutional by Supreme Court, Indian crypto community wins victory
2. Active.
Both are equally important, both are indispensable, because in fact, neither of them can be called a "consensus", nor is it a safe and usable system.
But people, including many blockchain algorithms, always ignore activity. Indeed, in reality, our requirements for "consistency" are much higher than "activity". For example, we always say that the nature of the blockchain is "cannot be tampered with", but in fact, the blockchain is not under any conditions. Are "unable to tamper", for example, the security of Bitcoin POW actually depends on the synchronization of the network. When the network is experiencing extreme conditions, Bitcoin cannot escape what FLP cannot prove-only one can be chosen in terms of consistency and activity. In other words, if the World War breaks out and the network between China and the world goes down, then yes, the Bitcoin chain will grow, but this growth no longer meets the conditions of consensus: you can say that it guarantees activity, However, the new transactions cannot reach consistency, because it is impossible to determine whether this chain will be replaced in the future; if you require consistency, then the newly growing chain will not count at all, because it seems that the new district is increasing fast , But these blocks do not meet the conditions that are guaranteed to be tamperable with a high probability.
And back to the "security" that we quoted before-the reason for quoting is because HTLC's mechanism can protect consistency, and rational malicious nodes must attack costs higher than revenue due to the deposit, so they cannot attack consistency. .
But what about activity?
For RSMC, which is the most basic Lightning Network, malicious nodes can also be active in attack-for example, a malicious A and B say, let's each issue 1btc to build a Lightning Network payment channel, B said OK. Then the Lightning Network was established, but A completely ignored B afterwards, so this Lightning Network channel would have no effect, so B could only initiate a refund transaction, but would need to be punished by the refund time lock of 1000 blocks. .
This is actually an active attack initiated by A against B, but it does not seem to be so cost-effective. A spent the cost of locking 1btc by himself, and the result was that he locked B's 1btc 1000 blocks. Moreover, it seems not so practical-you can say that this is B's own problem: you shouldn't have believed in an untrustworthy A and established an off-chain channel with him.
However, HTLC makes the scope of this active attack no longer limited to one node, but the entire payment chain:
It is still the previous scenario, but after the HTLC contract is constructed, the malicious node C refuses to provide X. Thus, both B and A's contracts are useless, but the channel needs to wait until the agreed time is reached, that is, one day before it can be unlocked-note that because an HTLC transaction on the chain can only open one channel, no matter what the transfer is Whether the amount is 1BTC or 0.01BTC, as long as the contract is established, the entire channel will be locked. Similarly, if this payment channel includes many intermediate nodes, the channels of these intermediate nodes will be locked, and the closer the lock is to the transaction initiator, the longer it will be.
These are actually not new issues, but the latest paper by Ayelet Mizrahi and Aviv Zohar not only mentions this method, but also explains the attack based on actual network conditions and current network parameter settings. The cost is actually quite low and difficult to guard against.
https://arxiv.org/pdf/2002.06564.pdfarxiv.org
The specific problem is that first of all, the nodes in the Lightning Network actually provide relay services to earn transaction fees, so the entire network structure must be transparent to users, so that users can choose the line with the least cost. Therefore, an attacker can also use this to create a transaction initiator and transaction receiver (in fact, it can be just a node), and then find a line with the most relay nodes, and then use the above methods to cause channel locking. Then, each node will set aside enough response time for itself. The default value of this time in different payment networks is different, and it can be up to 144 blocks-that is, one day. Therefore, a long payment chain may lock the channels of some nodes for several days or even ten days. And, another problem is that because the payment does not really take place, the only price for making such a payment is to mortgage a money on the chain to open the channel, but because the function of the Lightning Network is small payment, this money Not much. And the result given by the final paper is quite sensational-1/4 bitcoin can lock almost 3/4 of the payment capacity of the entire Lightning Network. In addition, there is another point that is beneficial to attackers. In order to prevent transactions from being tracked, the Lightning Network uses a technology similar to the onion network when establishing a payment relay chain-that is, each relay node only knows its own Who were the previous and next nodes without knowing the initiator and receiver of the transaction. Therefore, the relay node cannot blacklist nodes it does not trust.
The above is an active attack on the entire network. There is also another kind of attack-censorship attack, which attacks the activity of a specific user-that is, to lock the channels of all nodes connected to it so that it cannot use the Lightning Network, the cost of this attack is even lower.
In fact, although this paper uses the Bitcoin Lightning Network as an example, it is not aimed at the Bitcoin Lightning Network-in fact, the above attack applies to all systems that use the same logic as an off-chain payment channel. At the same time, some solutions are also proposed in the paper, for example, it is mandatory to reduce the reaction time reserved for each node, add some credit evaluation mechanisms, and charge a part of the fees when establishing the channel … but in fact the paper It is also acknowledged that these solutions cannot actually solve the problem fundamentally. In fact, don't forget that this is an environment of trust at all times. How much effort did Bitcoin spend to solve the problem of consistency in the environment of trust? Problem, then Lightning Network hopes that in this insecure environment, it can bypass the entire consensus scheme to reach consensus, and then use economics to ensure that consistency is not destroyed, then the active attack itself cannot be avoided.
Therefore, since the design of the lightning network could not guarantee the activity, all relay nodes should know that their relay service is not simply to help send a few messages, establish a channel, and earn a commission, but Need to risk the channel being locked. For example, relay nodes now generally think that they are driving a ride, and they can make a little money by personally. But in fact, the company that hired them was not qualified, so it became an illegal operation, and some police pretended that the passengers were fishing to enforce the law, and arrested them for a week. At this time, will anyone still drive a ride?
I believe it will, but correspondingly, due to the risks, the fare naturally cannot be the same as that for people to take a ride. In fact, there have been studies on the costs of Lightning Networks that the current transaction fees in Lightning Networks are not enough to make relay nodes profitable, and this is still under the premise of not considering active attacks.
However, if the transaction costs increase, it will conflict with the setting of small fast payment for the entire Lightning Network.
But at this time, someone may ask-why would anyone want to attack the activity of Lightning Network! Are you full? What benefits can he get from it?
In fact, this question can also be used on the blockchain, and we just said the answer to this question.
——————————————————————————————
Risks of Bitcoin, Ethereum, and similarly structured blockchains
One thing that many people don't know about Bitcoin is that Bitcoin does not guarantee the viability of every legitimate transaction .
Bitcoin, and most public chains, only guarantees the activity of the chain itself, that is, there are always new legal transactions that can be confirmed. This activity is actually quite weak, because neither Bitcoin nor Ethereum guarantees how many transactions can be confirmed in how long. For example, in theory, Stardust Attack, or dust attack, can block the network for a short time and make transactions impossible to confirm. In fact, the first round of FOMO3D game results was a successful use of the feature that "Ethereum itself does not guarantee liveness"-the attacker first constructs a contract with a high gas fee, and then generates a transaction with a high transaction fee. Occupying a full block makes other FOMO3D transactions unacceptable for a period of time, and the attacker eventually takes away the first round of FOMO3D rewards. Here, the attacker attacks the activity made by Ethereum for a short time, and attacks the FOMO3D, which is built on Ethereum, and actually relies heavily on the activity to ensure fairness.
In other words, as mentioned above, for payment systems, consistency is much more important than liveness, because it is well known that the destruction of consistency can lead to double payment attacks, which is not wrong. Therefore, Bitcoin and blockchain consensus algorithms have emerged at the historic moment. In the design, the guarantee of consistency is also higher than the activity, which is not wrong. Then, people think that Bitcoin and Bitcoin's consensus algorithm are safe, because it can guarantee consistency, and it can also ensure that new transactions can always be confirmed. This is not a problem, because in the scenario of the payment system, people require activity. It's really not that high, and it doesn't matter if a transaction is confirmed a bit faster or slower, because Bitcoin transaction confirmation is slow enough, and people take it for granted:
"What's the use of sabotage? Attackers can't make money."
However, next, if users use the blockchain as a consistent and active infrastructure to build applications other than payment systems, the problem will come-
This thing does not guarantee activity!
Therefore, when there is a game in which FOMO3D's fairness depends on activity, this behavior of profiting by destroying activity will occur. Ironically, after FOMO3D, countless smart contracts are still built on liveness guarantees that Ethereum does not exist.
Review attack risk
Above, we discussed the activity of the entire blockchain. In addition, there is also the activity of a single transaction-most public chain consensus algorithms do not guarantee the activity of a single transaction, that is, it does not guarantee that all legitimate transactions can be confirmed. Among the few consensus algorithms that can guarantee this, this feature has a specific name, called Fairness, or Censorship Freeness.
For example, Bitcoin does not actually have this nature. A legitimate transaction can not be chained for many reasons, such as insufficient transaction fees, or a block full that cannot be ranked, or even simply because the node is unhappy. So this gives a lot of room for censorship attacks.
For example, suppose the attacker wants my transaction tx to be unchainable. In addition to attacking the activity of the entire network through the above method, the attacker can also launch an attack on this transaction:
He can buy some miners and let them announce: "We don't accept any blocks that package tx." That is, if someone packages tx, they pretend they didn't see it and forked-this is the censorship attack. Attack).
The general public and many articles about this type believe that the prerequisite for the success of this attack is 51% hash power, that is, the same as a double payment attack. So it doesn't look like it deserves special attention.
However, there have been many researches on this kind of attack in the academic world. In fact, you do not need to control 51% of the computing power to launch this attack.
Let's consider a simple case-suppose there are three people, A, B and C, each of whom has 1/3 of the computing power. At this time, A announces a censorship attack. Therefore, for B, if he also reviews and C also reviews, then this transaction will not appear on the chain, and B can still get 1/3 of the mining reward. If he also reviews and C Without review, then C's chain will be isolated and B can get 1/2 of the mining reward. If B does not review C and does not review, then A's chain is isolated and B can get 1/2 of the mining reward. If B does not review and C reviews, then B's chain will be encouraged without any reward .
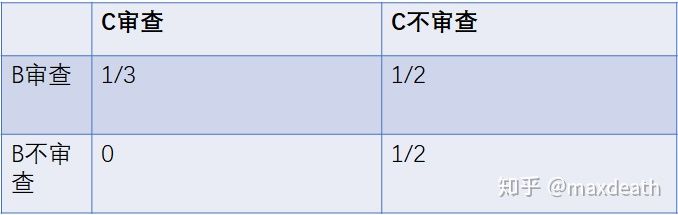
So, as B, unless he can confirm that C and he are united against A without reviewing, your best strategy is to also participate in the review, because participating in the review will not cause you to lose any revenue, and not participating in the review will May cost you money.
In reality, the situation in front of you may be simpler-when you mine, there are only two options in front of you: including transactions or not. If you choose to include, then no matter how much hash power the initiator occupies , you need to run the risk that the final block will not be packaged and lose your profits, unless you can be sure that most people are on your side. Otherwise, the best option is to exclude the deal silently.
The logic is like bullying on campus: A tall boy bullies another weak student. You can choose to stand up and help the weak student and believe that most people are behind you. But in reality, many people choose to walk away silently, thinking "I'm not familiar with him anyway", because they feel that most people will make the same choices as them.
Of course, many people think that in reality, censorship attacks are not realistic at all-because this requires someone to announce such attacks with high profile, and of course, all miners should stand up against him.
But is that really the case? Not all "censorship attacks" will be opposed by most people. What if this transaction contained some illegal remarks? For example child pornography-this is already available on Ethereum.
If you think this example is too far away, then there is a more realistic example:
What if someone adds extremist or separatist remarks to Bitcoin or Ethereum?
The public chain can be borderless, but both miners and users have borders. Including this transaction may lead to the entire chain being boycotted and even suspected of being illegal, because from any perspective, while the miner is broadcasting the chain, It is spreading illegal information.
Therefore, not including whether the transaction is not only advantageous, reasonable, but also the only legal choice.
This then constitutes a censorship attack. The censorship attack itself may not be fatal, but the subsequent impact may be very far-reaching-as long as censorship attacks on certain transactions are no longer considered as attacks, then censorship attacks on transactions are no longer in general It is a problem that can be ignored.
————————————————————————————————
Application scenarios of Lightning Network's off-chain technology
Having said so many questions about censorship attacks and blockchain activity, what's the point?
First, this is in response to the question "why would anyone want to attack the liveliness of the Lightning Network"-
We used to naively think that no one would attack the activity of Bitcoin or Ethereum: "Isn't it just to make transactions late to be confirmed? What benefits can an attacker get?" At the same time, we are optimistic that Bitcoin and Ethereum are Providing the viability of legitimate transactions is common sense, and no one is stupid enough to rely on the security of a large sum of money for their viability. In the end, we see that the activity problem that we previously ignored has become the basis for many new technologies and applications, such as FOMO3D, such as Lightning Network, such as DeFi. At the same time, we see that there are always people who, driven by their interests, intentionally or unintentionally make mistakes that we think "no one is so stupid", such as quoting data from unsafe "predictors".
Similarly, the activity of the Lightning Network may now look okay. We also believe that "the activity of the Lightning Network is completely based on trust in all nodes in an insecure network. How can anyone be stupid enough to think that it can guarantee activity?" But now I am fully convinced that one day in the future, there will definitely be applications that establish security based on the activity of the Lightning Network, and there will also be methods that can profit by attacking the activity of the Lightning Network.
The second question is the question we have already said–
The security of Lightning Network is not only based on the observation of nodes on the chain, but also on the need to promptly challenge transactions.
But we have just introduced that the blockchain does not guarantee the activity of transactions. For an attacker, he can block all transactions for a period of time by blocking the entire network. A transaction cannot be chained.
We originally thought that it would not be a big deal for a transaction to go online later. And now, the problem is not coming—
If the challenge transaction is not uploaded in a timely manner, it means that one of the parties may lose all the money received in the channel, and for the HTLC relay node, it means that they paid but may not get the money. The reason is what was said earlier-the consistency of the Lightning Network is built on the activity of the first layer of the network. The first layer of the network is not guaranteed to be active.
For RSMC users, if this happens, they can only sigh and say that they really should not establish an off-chain channel with someone they don't trust.
But for HTLC relay nodes, it is very pit, especially before-this is equivalent to driving a downwind car, not only the car may be detained, the car may also be robbed. So, I took such a big risk to drive a windmill, how much should I charge?
————————————————————————————
So, should we say that Lightning Network is not feasible at all?
No.
To sum up, Lightning Network has the following characteristics:
1. The Lightning Network cannot replace the general payment function. It can only realize the functions of stored value cards and point cards.
2. As a stored value card, because Lightning Network only has the advantages of transaction fees and confirmation time, it needs to pay the opportunity cost and the cost of initiating a mortgage transaction first, so only when the off-chain transaction fee is less than the on-chain and It only makes sense when users have a lot of small transaction needs.
3. If used as a score card, then users need to have the ability to observe the chain at any time and initiate countermeasures, which almost determines that users have only professional institutions instead of ordinary users. In addition, the risk of activity of the main chain needs to be considered.
4. Due to the activity risk of the Lightning Network itself, if the Lightning Network itself is not safe, low transaction costs will bring higher activity risks. Therefore, transaction fees in relatively insecure networks should also be relatively high.
There are many contradictory points which further limit the application conditions-low transaction fees will lead to low cost of Lightning Network active attacks, but high transaction fees will cause users to lose the significance of using the Lightning Network; small transaction amounts will also cause Lightning The cost of network activity attacks is low, but a high transaction amount means a high amount of locks, so if the lightning network activity is attacked, or the main chain activity is attacked, the loss will be greater …
Therefore, to sum up, the more suitable scenario of Lightning Network is to provide high-frequency trading users with security needs as a service of the exchange-that is, transactions that were originally centralized only in the exchange database can now be used. Moved to Lightning Network. Although the handling fee is a bit more expensive, it is better than the handling fee on the Bitcoin chain, and even if the exchange runs, the money off the chain can still be taken back, I believe it is also attractive to users. However, since these transactions are not on the chain, this scenario does not seem to help reduce the pressure on the chain.
Other similar scenarios are also possible. For example, exchanges can use this to conduct transactions, but the core elements are nothing more than: 1. professional institutions; 2. high-frequency trading; 3. trusted networks. It is not only difficult to promote or unrealistic problems to cover the entire second layer of the Lightning Network or even replace daily transactions. It is a problem that cannot be realized in principle. The wider the coverage, the more insecure this network will be. The greater the risk of the relay service, the higher the transaction fee should be, so low-frequency traders will be screened out, and finally there will be a balanced, small network between professional trading institutions.
The Lightning Network is already the most feasible, off-chain technology based on collateral. For other off-chain technologies, the first thing to overcome is how to design a feasible solution for the scenario, so that any breach of contract will lose the deposit; secondly, a mathematical proof that can describe all the breaches is needed; again, a deposit mechanism needs to be designed The guaranteed amount exceeds the losses caused by default. The above three points should not depend on any center, otherwise the meaning of adopting the blockchain will be lost. And if we design a solution that meets the above conditions for a certain scenario, then we are equivalent to just reaching the starting point of the Lightning Network-and all the security issues and limitations in the previous Lightning Network still apply to this off-chain solution. . Therefore, I do not object to the second layer network, and I can agree that it is a feasible route to throw a lot of extra functions to the second layer, but please do n’t think this is an established fact or existing technology- Regarding how to move the first layer to the second layer, the existing technology may not even be an entry point.
Then someone may ask-then if we do n’t know how to move to the second layer in many scenarios, and the first layer cannot meet the performance requirements, what should we do?
What I want to say is very simple-it means that this problem is not suitable for blockchain at all now. If we say how to move the problems of the first layer to the second layer, we ca n’t even get started, then how to move the real scenes to the blockchain, we can only be regarded as just getting started.
1.5-layer capacity expansion plan Rollup
Recently, with the difficulty of production of Ethereum's lightning-like network plasma solution, Rollup based on the Ethereum network's expansion plan has received the most support. At present, it is divided into two groups, namely Optimistic Rollup (OR) and Zk Rollup (ZR) .
In fact, I prefer the Rollup solution to segwit. For an introduction to segwit, see the previous article:
maxdeath: Another Perspective of Bitcoin (5)-About Capacity Expansion and Forking (Part 1)

Both are based on minimizing changes to the original structure and rules of the blockchain, moving the most "big" and most occupying output of the block out of the chain, while ensuring the self-consistency of the chain itself — — That is, the node can not obtain or verify the off-chain part, directly trust the results verified by those who have the off-chain part, and then directly operate based on the result-for Bitcoin and Segregated Witness, it is directly changed based on the transfer UTXO status, and for Ethereum and rollup, the status is directly updated based on the calculation results. If most of the verified people are honest, then the chain itself is self-consistent-compared to the mechanism such as Lightning Network that puts a part of the state off the chain through mortgages, all states here are on the chain, only However, the proof of reaching these states is put off-chain, so it is called a 1.5 layer scheme.
The difference between the two is:
1. Without changing the existing structure and parameters of Bitcoin, the bottleneck of the output is the block size. Therefore, Segregated Witness is to throw out the relatively large "signature" part, leaving only the input and output. Ethereum does not change the existing structure and parameters. The bottleneck of the output is the upper limit of gas, so rollup is to throw the most gas-consuming calculation part to the side chain, and only the state change is left on the main chain.
2. Segregated Witness is a soft fork scheme, that is, a scheme in which all nodes should be upgraded. In terms of design, including the following practical applications (this briefly appeared some controversy, but it became less and less), it is believed that Segregated Witness can increase the capacity by up to 4 times, and this level of expansion is due to the network and hardware The network and hardware have long been inconsistent, so it is unlikely that there will be problems with node overhead. Therefore, Segregated Witness mainly considers the issue of forward compatibility of soft forks, that is, during the upgrade, it is hoped that the un-upgraded nodes can still keep the upgraded nodes on the same chain without generating a hard fork. During this time, indeed, because only the upgraded nodes can be verified, the security has decreased, but in the end, everyone should upgrade, so Segregated Witness essentially expands the block, but only uses a more clever and not hard Forked transition method. Regarding the fork, see this article:
maxdeath: Another Perspective of Bitcoin (6)-About Expansion and Forking (Part 2)

Rollup is different from Segregated Witness in that rollup hopes that most nodes do not need to manage transactions on the side chain, while the side chain has only a few nodes. Therefore, these nodes need to put a deposit on the chain that will be taken away if they do evil, to ensure that they have the incentive to honestly verify the transaction. One of the big reasons for this is that, unlike Segregated Witness's maximum expansion of 4 times, rollup is also at least a hundred times the expansion-it is difficult to ensure that all Ethereum nodes are able to cope with the increase. 100 times computational difficulty (based on gas). So, in fact, the essence of the rollup scheme is to change the verification rule from "all nodes verify all transactions" to "select some nodes, or some nodes voluntarily pay deposits to replace all nodes to verify some transactions." Then, in operation, a method that does not hard fork is made.
So the question arises, what if these people do evil?
Here, the method of OR is that all rollup transactions have a lock-up period, for example, two weeks, other nodes can go to the sidechain for verification. If the rollup node is found to be evil, it can roll back the transaction. The advantage of this method is that it is universal for any transaction type, and the disadvantage is that the node that wants to verify must download the entire sidechain.
ZR's approach is that when rollup is uploaded to the main chain, in addition to the state change, a "zero-knowledge proof" that the state change is true is added, and then all nodes on the main chain need to verify this proof. The advantage is that the node does not need to download the entire side chain to verify the transactions on the side chain. The disadvantage is that this solution is not universal at present. It can only generate zero-knowledge proofs for certain specific types, such as transfers.
Therefore, it must be clear that, in terms of security, the rollup solution is still a mortgage-based off-chain solution. For transactions that were moved to the sidechain, they originally needed to pass the entire network verification, but now they are safe Sex is guaranteed by the mortgage nodes and their deposits on the chain. So in a sense, the rollup scheme lies between "POS where all transactions are verified by trusted nodes with deposit collateral" and "Off-chain technology where some transactions are verified by nodes with deposit collateral and stakeholder verification" between. I personally think that implementing Rollup on Ethereum or a state-based blockchain similar to Ethereum is a very feasible expansion solution, because first of all, centralization is the trend of all public chains, because no matter in principle, demand or status, a center The blockchain is all too easy to use. And Rollup is such a centralized solution that has been accepted by the public, technically feasible, and not so "centralized".
Whistle about blockchain security
In the second half, I raised a lot of security issues.
The blockchain circle has not been stable recently, and there have been multiple security-related incidents in a row. Except for not knowing how to blame hackers who can only declare their own run, this circle is used to collectively refer to all such incidents as "hacking attacks", and then call on exchanges to freeze their attack proceeds. However, in my opinion, through some issues that have long been concluded in academia, countless people have called for it, and everyone, even developers, has benefited from problems that are not really "hackers."
You spent 10,000 to buy a brand-name bag, and then used it several times to sell it on the idle fish. The buyer said that your bag was fake. If you took a fake, you would pay ten, and you found that the bag was his. Sold to you. So you call the police and sue him for extortion, that's fine. You spend 50 yuan to wholesale a bunch of bags that claim to be brand-name, and then sell them on the free fish 5000. At this time, a buyer comes to your door and asks you to take a fake and pay ten. Then you also call the police and tell him to blackmail and say When I bought it, I wrote a brand-name bag, how do I know that this bag is fake …
Why is this thing professionally fake? It is because in the absence of perfect market rules and supervision, it is necessary to use benefits to drive some people to actively find these illegal acts. Otherwise, the entire market will be flooded with 5,000 bags of 50, so that no one will Selling genuine goods. Now, the blockchain field is a market with inadequate rules and supervision. If we do not allow anyone to benefit from security vulnerabilities, then more and more people and projects will ignore security, and even ignore the previous Researchers put white paper and black holes and problems in front of them and whitewashed the project to market.
This is not a whitewash for "hackers". It is a hacker who steals personal or institutional keys and gains profits through illegal means stipulated by the law, but in the blockchain world, algorithms and codes are laws that use known vulnerabilities in algorithms and codes to gain profits. Why? Not the proper use of system characteristics? If the security holes in the algorithm can be solved by calling it a hacker attack and calling on everyone to freeze the profits of the attack, then we may not need bitcoin, no mining, and no blockchain-we should be full The society turns out to maintain a ledger. Whoever tries to tamper with it will declare him a hacker, and call on the exchange to freeze his coin. The whole society will block it, right?
In this article, I have listed a series of known issues about Lightning Network and Blockchain-none of them are new issues that I have discovered and raised. The examples of FOMO3D have been passed for two years. It dates back to 2013. These are all whistle about the security of blockchain activity, and these whistle have been blown more than once. I hope this time, when someone designs a system without considering these issues in the future, and someone benefits from these issues, please do n’t call it a hack.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Open up on-chain and off-chain assets, Chainlink and DMM aim to create the first blockchain-based currency market
- Lies of the trading platform——how to dynamically check the authenticity of transactions on the exchange
- U.S. Federal Reserve cuts interest rates sharply
- Babbitt Column | Why Don't Use Leverage in Investment Coins
- Market analysis: the market rebounded weakly, the market bulls have not recovered
- "Is Ethereum a currency?" Pomp refutes that only Bitcoin and gold have both currency and value storage characteristics
- Analysis: Legal issues of blockchain within the framework of the EU's General Data Protection Regulation (GDPR)






