Dismantle MimbleWimble's Privacy Magic – part II
Mimblewimble is a Transformer assembled from many parts. I will introduce in this chapter how the various parts of MW work to complete the agreement. According to the agreement, I think MW's private currency trading has three trading characteristics.
1. No transaction amount
2. No transaction address
3. In one block, multiple transactions are merged, there is no way to see the details of each single transaction.
- Market Analysis: On the day of the college entrance examination, you will be rewarded for eating a hot dog
- The CFTC chairman who is going to retire in a month has found a successor. Will he support cryptocurrency?
- On June 7th, the market analysis of Bitcoin repeated bottoming, the market started near the eyes
To accomplish this feature: you must have three large parts separately:
1.Confidential Transactions (secret transaction, referred to as CT)
2.CoinJoin (coin trading)
3. One-way Aggregate Signatures (OWAS)
In disassembling MimbleWimble's privacy magic (part I) , we analyzed the first part. This article will continue to explain the second and third parts.
2, CoinJoin mixed transaction
In the past, many people thought that on Bitcoin's trading chart, it was a very easy place to reveal privacy when it was able to see which output corresponds to which output, so Gregory Maxwell (yes, he is) There is a concept called CoinJoin. The thing he has to do is very simple, which is to mix two transactions.

In the MW agreement with money, there are many wallets or extra services, there are services to configure CoinJoin, such as WasabiWallet and Tumblebit, JoinMarket, but Coinjoin is still not safe, you can still try to go from the transaction amount Restore, and because it is an individual service, the number of participants is too small, and it takes a certain amount of time to match the funds. At this time, in the MW agreement, Fodi Magic combined CoinJoin's technology with confidential trading (CT) to avoid the transaction being able to be deduced from the "digital" aspect, and at the same time, the trading path can be confused by CoinJoin's technology. . And unlike the previous use of CoinJoin's services, this is Mimblewimble, which completely writes CoinJoin on the protocol layer, so that you don't need a third-party wallet or service to help you do this, and you have the opportunity. Make hybrid trading more efficient.
But now it’s too early to celebrate the magic of private transactions, because even if we mix the transaction amount, we can still know the public keys of both parties, and we can try to reconstruct each through these public key addresses. Pen transactions, so in this situation, we must have a new public and private key system to ensure privacy.
3, OWAS (One-way Aggregate Signatures, one-way aggregation signature)
In his preliminary white paper, Jedusor proposed that it can be done with Yuan Horas Mouton's One-way Aggregate Signatures (OWAS). The more interesting point is that Andrew Poelstra is in his detailed version. In the white paper, the word OWAS was not used. Instead, the technology was verified in the Sinking Signature and compact chain. Even the MW profile of Github, which later developed Grin's Ignotus Peverell, did not appear in the OWAS. Directly speaking, TransactionAggregation, do not know this proper noun, why in the three important MW files, the way it appears will be slightly different, but here is still referred to as OWAS (I know that there is already like Boneh before) Other scholars are studying the aggregation signature).
The so-called aggregated signature means that when you see the input and output of many transactions, we will no longer be able to re-disassemble the public keys of these inputs and outputs, and put together a complete transaction order, so we will aggregate all the signatures. Together, and can not make him reversed.
OWAS consists of two parts, one is Kernel Excess and the other is Kernel Offsets. Do you remember the difference in blinding factor? Yes, Alice has to transfer money. To Bob, he didn't want Bob to know his private key (blinding factor), so he gave him (blinding factor difference) *G. At this time, in order to avoid people guessing the trading route from the public key in the transaction, we Using a one-way aggregation signature to reduce the possibility that everyone knows this value, so we have the following formula

In this way, we can split the remainder of the public key (for example, 50*G in the above-mentioned confidential transaction) into two parts, for example, X*G is split into (x1+x2)* G, at this time everyone can construct the value x1*G that the outside world sees is the so-called Kernel Excess, you can think of it as a public key; the other part is x2*G, called Kernel Offsets, he will and this area The KernelOffsets of all the transactions in the block are added together, and when they are added together, then you can't see which Kernel Offset is in which transaction, so this method will be called a single Sign the aggregate because he can't do reverse engineering. Therefore, when a transaction on MW is verified to the miner, we can imagine that KernelExcess is the public key and Kernel Offsets is the private key.
At this point, the part of the privacy transaction is completely completed, we repeat here briefly
1-1. Confidential Transaction-Additional Homomorphism: Ensure that the equations are established without knowing the transaction amount.
1-2. Confidential Trade – Scope Proof: Ensure that each input and output value is greater than zero with zero knowledge proof, avoiding creating extra money out of thin air.
2, mixed currency trading: let us not be able to push back the trading path from the transaction amount
3, one-way aggregation signature: let the transaction's public key not be exposed to the transaction path
Third, Cut-through write-off: reduce miners' storage status
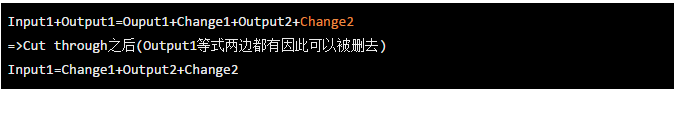
Cut-through is a sophisticated design for miners in MimbleWimble. He can ensure that miners don't need to store so many trading states for long periods of time, and the concept of cut-through is when a transaction has been determined to be owned (also After being verified, as long as the input is equal to the output (input=output), the excess content in the process can be deleted. For example, the original few transactions may look like this.
However, it must be specially stated here. I think the concept of Cut-through is not able to achieve good privacy in the two projects currently implemented (Grin & BEAM). For example, in Grin, the function of Cut-through is able to be shut down. Drop, just put the archive_mode of ~/.grin/main/grin-server.tomlar from
Archive_mode = false
become
Archive_mode = true
In ~/.grin/main/grin-server.toml
As a result, the miner's node will not perform the write-off action. Therefore, I think that some outsiders may think that Cut-through can solve the privacy by deleting the information. It may be a misunderstanding on the current implementation.
Fourth, the follow-up effect and limitations of MinbleWimble
MimbleWimble is not only a privacy currency blockchain protocol composed of many privacy protocols, but also a good scene for many good methods that could not be implemented on Bitcoin when many problems encountered by the past Bitcoin community, but MimbleWimble It is also like a warrior with some sequelae after practicing some kind of magical power, so in the end, I tried to explore what subsequent influences MimbleWimble will have and what restrictions may be imposed on development.
1. Challenge the status of other privacy coins and the principles of public chain design
The author believes that the impact of the MimbleWimble agreement is first of all to challenge the status of existing privacy coins, such as Monero and Zcash. The MW agreement does not need to verify the legality of the transaction, but retains the list of validated transactions, and Cut-through. Its utility also allows miners to reduce the unreasonable way of storing verified status. In addition, I think the MW protocol is also a minority, using a data chain design to reduce scalability to achieve scalability, and he also reduced the number of blocks in the blockchain that should be recorded by the miners. In MW, a transaction What the miners need to know: The most important thing is the effectiveness of the transaction and inflation, which may affect future monetary projects that do not have highly intelligent contractual requirements, and develop in this direction.
2. Limitation
Although MW took a very clever approach to privacy agreements, it implemented anonymous transactions. However, there are still some restrictions in itself. Here I divide him into three points: one is that the capacity occupied by RangeProof affects the capacity of the transaction state storage; the other is the experience of the transaction implementation; the third is the smart contract, etc. The ability to implement blockchain functions other than currency trading.
2-1. The capacity occupied by Range Proof affects the capacity of the transaction state storage.
As mentioned above, through Cut-through, we can reduce the storage contents of miners and avoid the problem of large accumulation of state. However, in the MW blockchain, it is impossible to be deleted in each input and output. Range proof, Range Proof is a simple zero-knowledge proof (688 bytes), the capacity is actually a very large gap compared to the transaction message itself (a single transaction is about 33 bytes), which also affects Future miners store data and the key to future scalability.
2-2. Constructing a transaction experience
In the case of the MW agreement, we must have the parties to jointly complete a transaction, for example, Alice sends money to Bob, Bob must prove that he knows the transaction amount, and returns the message to Alice, after the transaction is verified by Alice. Only after the completion of this process, such a process does not need to be synchronized online, but it needs to be constructed jointly by the two parties, and the concept of bitcoin, Ethereum and other cryptocurrencies is only required to transfer the amount of the signature to the blockchain. Currently, for example, on Grin, there are two ways to trade:
- Sending the file: Bob needs to receive the transaction file and generate a response file and send it back to Alice.
- Web page (HTTP): Bob's Grin wallet must listen to a port. Whenever Alice's wallet is sent to him, Bob's wallet will automatically perform the existing steps. But there is a more demanding condition, that is, the wallet needs to be under a fixed IP address, and your wallet client needs to continue to operate.
- These processes are actually very inhuman and difficult to use in the future . At present, Grin has developed a new wallet grinbox, the goal is to be able to trade like Bitcoin, but it is still in development, if there is any news in the future, I will continue to update.
2-3. Expansion of functions such as smart contracts outside currency trading
MimbleWimble and Bitcoin are different in that it is more difficult to support trading scripts in the blockchain, which also leads to simple smart contracts such as Bitcoin, or lightning networks, etc. However, I think this may be no longer The shocking MW is shortcoming, and as far as I can see, there have been some interesting projects being developed, such as the author of the precise version of the MW white paper: Andrew Poelstra of Blockstream, currently working on scriptless-scripts The way to create a simple application on MimbleWimble, while also implementing atomic switching on Grin. Perhaps there may be a lighter smart contract implementation in the future.
This article reprints the public number: Blockchain Research Laboratory
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Facebook currency plan speeds up: anchoring multinational currency, bringing 2.7 billion new users to the blockchain
- Anonymous coin Grin will smile in July to meet the first hard fork upgrade
- Node recruitment plan, Bystack detonated side chain management and application
- Read the text of Hong Kong's digital currency regulation
- Video|"8 Questions" ViaCion Yang Haipo: Code is an art, not a technology
- A white paper was released on June 18, and Facebook’s cryptocurrency is really coming.
- It is a good job to cut interest rates and return to the monetary easing. Is it good for the cryptocurrency market?