For ten years, the blockchain is still a toy for the technical house, but this is not a bad thing.
The cryptocurrency and blockchain technologies have been flourishing for more than a decade, and while achieving great success, the number of users it faces is very limited. At present, the main user group of the blockchain is still the “geek group” dominated by password punk and technology, and the mainstream population is still excluded from the system.
For this situation, this paper proposes a more systematic view: the cryptocurrency and blockchain technology stacking (that is, the "abstract" in the text) is a key step towards the general public, allowing different stack layers to adapt to different users. The needs of the group will enable the technology to achieve its goal of making the best use of its services. Of course, the text also mentions that different stack layers (abstract) are accompanied by different levels of risk. The lower the stack, the stronger the control over property and services, but the greater the personal liability and transaction friction.
The above paragraph may sound a bit difficult to understand, explain in the vernacular:
The technology stack is a bit like building a house. It usually has to be layered up, built into a rough room, and then renovated to become a product that can be sold directly to users. If you don't take such a multi-layer, let you live on the foundation directly, you can't stand it.
- Technical Perspectives | How do ordinary users earn miners in cross-chain?
- Opinion | US Senator: Blockchain may be widely adopted, but it still does not address financial inclusion issues
- Zhou Xiaochuan's latest speech: If piloting digital currency, you should consider 100% cash payment
Now the product of the blockchain is to let the user live directly on the foundation. But many of these users are fanatics of architecture, so for them, living on the ground is not a problem (letting geeks keep their private keys is not a big problem), on the contrary, they may enjoy directly The process of DIY on the foundation.
Of course, for mainstream users, this is definitely the worst house in the world. There is no doubt that the blockchain needs to continue to stack more abstract layers to create a more comfortable house, but each time a new layer of material is added, users will face an additional layer of risk.
Because of this so-called abstraction, it is a bit like burying complex foundations, water pipes, and circuits underground, allowing users to see only the faucet and socket interfaces. This is certainly a lot easier, but most of the time they are provided by the centralized supplier. Each additional layer means that you need to trust more than one supplier. Trust the contractor will not cut corners and trust the decoration company will not exceed the standard. and many more.
Understand this metaphor, and then look back at the above paragraph, is it a lot to understand?
It is worth mentioning that the choice of stacking (abstracting) or centralization is not at fault. The goal of this field is to give users the right to choose , more in the choice and preference of users. Therefore, information and personal perception are the key to all issues. Therefore, continuous learning of knowledge, continuous enrichment of self can better understand security and risks, and truly protect the sacred private property from infringement.
text
The abstraction of cryptocurrency is a key part of its large-scale application. The simpler user experience is usually at the expense of centralization. Technology users can skip abstraction and solve the technology and its related friction problems at the localization level, but for the average user, they are more willing to have a third party to help in this process.
At the moment, I believe that the vast majority of established systems to date (whether the global monetary system or the NFT DApp) are mostly purely for a handful of technical fanatics. Of course, this is not a bad thing – because the design idea focuses on bringing new users into the system. The abstraction of technical components is also clearly at risk. The higher the degree of abstraction, the stronger the centralization and the higher the risk of end users. But if you remove and break the abstraction from the system, then the accompanying risks are in the hands of the user, and the user will face all the friction associated with it.
Abstraction is accompanied by risk, and abstraction means personal responsibility and friction.
The goal in this area is to give users the choice of choice: choose to join a centralized abstraction service or choose to control their own financial situation and application interaction. I would like to briefly introduce my current view of the abstraction hierarchy and the services associated with each layer.
Abstraction stack
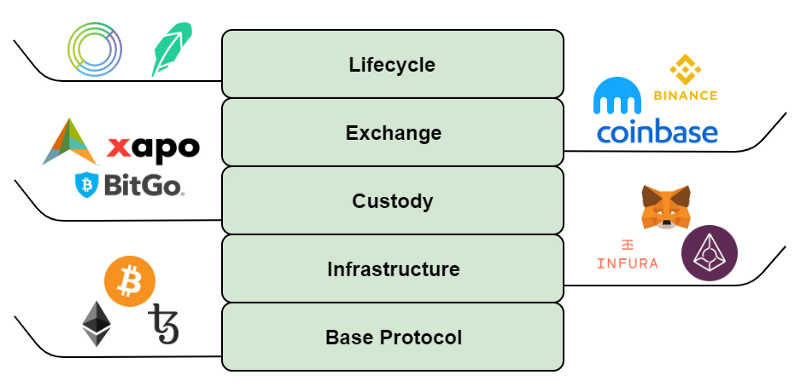
The abstraction stack has five different levels: lifecycle, exchange, custody, infrastructure, and base protocol. The abstraction layer at the top of the list is the lifecycle layer, which hides everything from the end user to give them the best possible user experience. Centralized exchanges often control the lifecycle of assets and capture elements such as exchanges, hosting, infrastructure, and basic agreements. This may include consumer services, such as providing debit cards based on asset conditions. Some exchanges can even provide a more extended abstraction (and thus rise to the lifecycle layer), such as the trading of the 'behind the curtain', and as an online broker to provide trading experience for retail investors. Services that hide everything like Robinhood and Circle are classified in the lifecycle layer, while the general cryptocurrency exchange belongs to the exchange layer.
Given that speculation remains the most widely used use case for these assets, the abstraction of the exchange experience is critical to the large-scale application of cryptocurrencies. As localization services add more friction, uncertainty and risk, centralized exchanges will continue to be the gateway to people's access to and use of cryptographic assets. The most successful centralized exchanges can provide sufficient trading depth for a smooth and smooth trading experience and transaction security (sometimes in the form of insurance).
Under the lifecycle and exchange layers, we also have centralized hosting providers who hold assets on behalf of users. These hosting providers mainly use institutional investors as customers, because institutions also hope to reduce investment risks through third parties. Large organizations do not regard blockchain wallet key management as their core competency, and many service providers have their own liability insurance business. If the customer wants to eventually sell their assets, these hosting providers usually also provide asset transfer services to quickly transfer assets to the exchange in a short period of time.
If the centralized wallet provider does not allow users to choose to connect to a particular network node, they may sometimes belong to this level of abstraction. As long as the user connects to the network using the node of the wallet provider, they actually allow the wallet provider to verify the transaction on their behalf. The wallet provider may allow the user to control their private key, but the process of verifying the transaction remains hidden from the user's field of vision. However, wallet providers that allow users to connect to private nodes give users greater control and less abstraction (the infrastructure is now under user control), but given the technical needs of the user, this It will also increase the friction.
DApps are still part of the infrastructure layer, which provides users with a more "peer-to-peer" experience, but still uses trusted certifiers by default, such as Infura. For example, when running Augur, users can connect to their own nodes, but usually only connect to one of the nodes by default, so the user's experience is much better. However, this process trains users to be "provided" to provide trusted verifiers' services – this is not a bad thing, just some trade-offs and compromises on the trustlessness abstraction. Services like MetaMask are used in almost all Web-based DApps, and it relies heavily on Infura to connect to the Ethereum main network.
The bottom level of the abstraction layer is: fully localized running personal nodes and trading from individual nodes. Of course, from the perspective of retail users, this approach is increasingly popular with technology users, as this often requires users to be technically savvy and eager to gain extreme control. The purpose of writing this article is not to criticize abstraction or lack of abstraction, but to illustrate that different users can use the network in different ways. Nor should we exclude users who use the network through a centralized service or treat them as outsiders.
Some people may never run their own nodes, or leave an abstraction layer that focuses on ease of use. While recognizing the risks of using these services, “doing your own bank” is not that fascinating. There is a reason for the banking industry to be so prosperous, even if they are involved in all economic scams. This is why most people are still more willing to make digital transactions after they know the privacy risks behind such services. People naturally use ownership for convenience.
However, the significance of these systems is that if the user is willing, they can opt out of the centralized service. First, I would like to praise developers who are working to reduce friction in the abstraction layer, but future systems will probably consist of providers of aggregation services and abstract networks.
Risk of abstraction
Using a centralized service may simplify the experience of the network, but as the level of abstraction increases, so does the risk. The following are some of the risks associated with the abstract stack layer that should be considered under certain convenience conditions:
Security risks and damaged assets
As new exchanges continue to emerge, there will certainly be many exchanges that are closed for security reasons. They hold a large number of assets, making them always the target of hacking. In 2019 alone, we have seen Cryptopia, the famous New York exchange, bankrupt due to hacking. Recently, the currency has lost $40 million due to hacking. Although both companies have their own remedies, they continue to remind people that exchanges are not foolproof, and sometimes assets may be completely lost when exchanges are damaged. However, if the user breaks the abstraction layer, acts as his own custodian before the transaction time, and continues to host his own assets after the transaction, it can effectively avoid losses.
Identity risk and blacklist
Any centralized service will risk losing identity data. In February of this year, the cryptocurrency exchange Coinmama suffered a data breach crisis, and the username and account password of 450,000 users were leaked. Considering that most users have a poor sense of security management, such as the reuse of account passwords, the destructive nature of such security incidents is often underestimated. Data breaches from other services in the past also included KYC record leaks. In addition, the use of addresses that may accept assets involving the dark market or hacking may result in issues such as blocking the account or prohibiting transfers.
Stop service completely
Abstract, centralized services can shut down and stop providing existing services at any time.
It is a significant move to build an assessment framework based on the risks faced by users interacting with different entities at different stack levels. Such a framework can instill more confidence in the user when the user interacts with the above entities, and also encourages the service entity to manage its risk rating as much as possible. As people move down the abstract stack, as the services that the entity can provide become more limited, the scope of the risk problem shrinks.
But the more important job is to let end users realize that they can probe the abstract stack in a variety of ways. For example, the lifecycle layer is reduced to the exchange layer by encouraging withdrawals from the personal wallet for cryptocurrency transactions. Users are even encouraged to build their own nodes and use them to verify their wallet transactions.
Information is the key to all of this – well-informed users can feel safe even at the highest level of abstraction.
(Finish)
Original link: https://medium.com/alpineintel/on-abstraction-and-risk-e981e06830f3
Author: Rocco
Translation: clockworkprince@橙书书志愿者
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- From the cathedral to the bazaar, the charm of hackathon and the soul of the developer community
- The US SEC plans to run Bitcoin and Ethereum nodes, eToro analysts: I never expected that I will wait until this day.
- Founded for nearly 8 years, the Blockchain wallet company, this time and the currency, Coinbase died?
- The bitcoin community has a big brain, only because the smallest unit Satoshi needs a symbol.
- Can I invest in real estate for 1,000 euros? Europe unlocks STO new pose
- South Korea's MangoBerry announced its participation in the Wanchain Galaxy Consensus Node Program, which will jointly develop the Korean market.
- Mining machine dealers go to the US road: Jia Nan Zhi Zhi tends to the New York Stock Exchange, Bitland favors Nasdaq





