From the network layer, consensus layer, data layer, smart contract layer and application layer, talk about the technical architecture of blockchain commerce
Source: “ Blockchain Business ''
Production: Blockchain Base Camp
The underlying technology architecture under the application of business scenarios is not accessible to most people. However, all commercial applications and services obtained on the blockchain are inseparable from the support of the underlying technology architecture.
Today we will talk about what the technical architecture of blockchain commerce contains.
- Venezuelan President Maduro claims to revive Petro Coin in State of the Union address
- What data have we neglected during the ten-year development of Bitcoin?
- Blockchain written into Chinese government decision-making documents on a large scale: the experimental period has passed
Interpretation of the technical architecture of blockchain business (1)
In general, the blockchain's infrastructure can be divided into five layers, including the network layer, consensus layer, data layer, smart contract layer, and application layer, as shown in the following figure. Each layer completes a core function, and each layer cooperates with each other to achieve a decentralized trust mechanism.
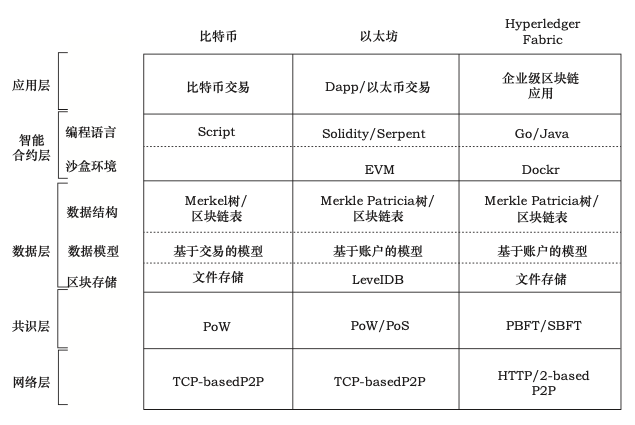
Blockchain application architecture diagram a
Network layer
The main purpose of the network layer is to realize the information exchange between the nodes of the blockchain network. The essence of the blockchain is a peer-to-peer (P2P) network. Each node can both receive and produce information. Nodes maintain communication by maintaining a common blockchain.
In the blockchain network, each node can create a new block. After the new block is created, it will notify other nodes by broadcasting, and other nodes will in turn verify this node. When more than 51% of the users in the blockchain network pass the verification, this new block will be added to the main chain.
2. Consensus layer
The consensus layer enables highly decentralized nodes to reach consensus on the validity of block data in a decentralized system. The more commonly used consensus mechanisms in the blockchain include multiple proofs of workload, proof of equity, and share authorization. This part has been explained in detail in the previous chapter.
There are two main functions of the consensus mechanism, one is reward and the other is punishment. Bitcoin and Ethereum use PoW proof-of-work mechanism. This mechanism rewards and punishes according to the computing power. If the node cheats, the computing power will be lost.
Bitshares, Steemit, and EOS use the DPoS share authorization certification mechanism. People with tokens can participate in the voting of nodes, and the nodes selected by everyone participate in bookkeeping. Once cheated, they will be cast by the system.
The incentive function mainly refers to giving token rewards and encouraging nodes to participate in the security verification of the blockchain. For example, before the total amount of Bitcoin reached 21 million, there were two types of Bitcoin reward mechanisms: Bitcoin rewarded by the system soon after the new district was created; and Bitcoin (deduction fee) deducted for each transaction. When the total amount of bitcoin reaches 21 million, the newly generated block will no longer produce bitcoin, and the reward at this time is mainly the commission deducted by each transaction.
3. Data layer
The data layer is the lowest-level technology, and its main functions are the realization and security of data storage, accounts, and transactions. Data storage is mainly based on the Merkle tree, which is implemented by means of blocks and chain structures. Most of them are persisted in the form of KV databases, such as LevelDB used by Bitcoin and Ethereum.
Based on a variety of cryptographic algorithms and technologies such as digital signatures, hash functions, and asymmetric encryption technologies, as well as the implementation and security functions of accounts and transactions, it ensures that transactions can be performed safely in a decentralized situation.
The starting node that the technical staff who designed the blockchain system first established was called the "genesis block", and then under the same rules, the same specifications were used to create blocks with the same specifications, which were connected in sequence through a chain structure. A main chain. With the increase of running time, new blocks are continuously added to the main chain after the verification, and the main chain will continue to extend.
Each block also contains many technologies, such as the time stamping technology. Its role is to ensure that each block can be connected in chronological order. For example, a hash function is a method that passes messages of any length. Hash algorithm is a function that compresses a fixed-length message digest. It is mainly used in the field of information security for encryption algorithms, file verification, digital signatures, and authentication protocols.
4. Contract layer
The so-called contract layer mainly refers to various script codes, algorithm mechanisms, and smart contracts. A smart contract is a piece of code that can be executed automatically without intervention on the blockchain. EVM is a virtual machine that runs on smart contracts. Humans can achieve asset transfer through smart contracts without any intervening agents, and can also develop Some valuable decentralized applications.
Taking Bitcoin as an example, it is a programmable digital currency. The script encapsulated in the contract layer specifies the Bitcoin transaction method and various details involved in the transaction process.
You can also build a blockchain application based on smart contracts, and you can easily develop your own blockchain application (DAPP) without learning blockchain technology from scratch. For example, based on the Ethereum public chain, developers can use the Solidity language to develop smart contracts and build decentralized applications; based on EOS, developers can use the C ++ language to write their own smart contracts.
5. Application layer
The application layer encapsulates various application scenarios and cases of the blockchain, such as a blockchain-based cross-border payment platform, etc. It is also a decentralized application DAPP. A complete DAPP contains a smart contract and a web system. The web system calls the smart contract through an interface.
This layer is similar to various software programs in a computer. It is a product that ordinary people can really use directly, and it can also be understood as the browser end in a B / S architecture product.
From the current situation, for many users, in addition to digital currencies, there are no ready-made blockchain applications. If the blockchain technology is to quickly enter the common people and serve the public, there must be a large number of applications combined with people's living and entertainment tools.
Interpretation of the technical architecture of blockchain commerce (2)
China Academy of Information and Communications Technology and the Trusted Blockchain Promotion Program have jointly prepared the White Paper on Blockchain (2018), which summarizes the technical system of the blockchain and also proposes a set of reference architectures, including Basic components, ledger, consensus, smart contract, interface, application, operation and maintenance and system management 9 parts. The following are worth studying in depth.
1. Basic component layer
The basic component layer can record, verify, and disseminate information in the blockchain system network.
In the basic component layer, the blockchain is a distributed system based on the propagation mechanism, verification mechanism, and storage mechanism.
2. Ledger layer
The ledger layer is responsible for the information storage of the blockchain system, including collecting transaction data, generating data blocks, verifying the validity of local data, and adding the blocks that pass the verification to the chain.
The ledger layer has the following two data recording methods.
① In the asset-based model, the asset is modeled first, and then the ownership of the asset is recorded, that is, ownership is a field of the asset.
② In the account-based model, an account is established as the object of assets and transactions. Assets are a field under an account.
3. Consensus layer
The consensus layer is responsible for comprehensive coordination to ensure the consistency of data records of all nodes in the entire network. Common consensus mechanisms can be divided into two broad categories.
(1) Probabilistic consensus mechanism
Write data first, and then reach consensus, such as PoW, PoS, DPoS. Consensus is reached with a high probability, and the calculation complexity is high. If there are multiple accounting nodes in a consensus, a fork will occur, and the longest chain will prevail. The number of nodes can be changed arbitrarily. The more the number of nodes, the more stable the system.
(2) Deterministic consensus mechanism
Consensus is reached first, and then written. After consensus is reached, consensus is reached. Consensus is confirmed, and network complexity is high; it requires a quorum to vote, and each node uses P2P broadcast communication without fork, such as PBFT, BFT variants ; As the number of nodes increases, performance decreases, and the number of nodes cannot be changed arbitrarily.
From the application point of view, in order to improve the efficiency, in the use of the consensus mechanism, trade-offs need to be made in terms of security, reliability, and openness, and the consensus mechanism is evolving from a single direction to a hybrid direction.
4.Smart contract layer
Responsible for implementing, compiling, and deploying the business logic of the blockchain system in the form of code, completing condition triggering and automatic execution of established rules, and minimizing manual intervention.
According to Turing's completeness, the smart contract layer is divided into the following two categories.
① Turing's complete smart contract has strong adaptability and can program more logical business operations, but it may fall into an endless loop.
② Turing's incomplete smart contract cannot perform complex logical operations, but it is simpler, more efficient and safer.
Smart contracts are a high-risk area for blockchain security risks. In terms of improving security performance, there are several reference ideas: formal verification, smart contract encryption, and standard contract language syntax.
5. Application layer
As the part finally presented to the user, the main role is to call the interface of the smart contract layer, adapt to various application scenarios of the blockchain, and provide services to users. This white paper divides applications into 3 types: value transfer, certificate storage and authorization management.
(1) Value transfer
Digital assets are transferred between different accounts.
(2) Certificates
Information is recorded on the blockchain, but there is no asset transfer.
(3) Authorization management class Use smart contracts to control data access, such as data sharing. In summary, the block is a container for data storage, and the P2P network is the basic protocol to ensure the operation of the blockchain. The consensus mechanism ensures that the nodes participating in accounting can work normally without human intervention. The application layer gives people a mature product to use.
At present, the blockchain platforms built by some companies, such as Hyperledger Fabric, R3 Blockchain Alliance (R3CEV), and Ethereum Enterprise Edition, all have unique features. For example, after several years of development, Ethereum has more than 500 application scenarios.
The blockchain applications of domestic financial institutions are still dominated by foreign Fabric platforms. However, the larger players have successively open-sourced the underlying technology, which is similar to the way that smartphones such as Android, iOS, and BlackBerry used to go through. For example, Shenzhen Qianhai Weizhong Bank Co., Ltd., Shanghai Wanxiang Blockchain Co., Ltd., and Matrix Element Technology (Shenzhen) Co., Ltd. jointly announced that the open source three-party blockchain platform BCOS (Block Chain Open Source) jointly established by the three parties, The formation of a distributed business ecosystem was further promoted, and the pattern of the underlying platform of the blockchain appeared.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Comments | There is no "prospect" for the public chain. Is it easy for the alliance chain?
- Morning Quotes: Crypto Markets Collective Up, Bitcoin SV Goes Crazy
- "No madness, no survival" —— The refining of the demon coin BSV
- "Blockchain First Share" Financial One Account Suddenly Dropped Over 20%
- Bitcoin mining difficulty soared again by 7.08%. In 2020, the halving of the currency has skyrocketed across the board. Is the market halving?
- "Learning Times" article: Blockchain invoice is a good thing
- Chongqing Daily: Blockchain's "hot", Yuzhong blockchain industry innovation base competitiveness ranked fifth in the country





