Getting started with blockchain | Hash lock for cross-chain technology solutions
In the vernacular before the tweet " Dr. Xiao Feng's praise of the two major cross-chain technology projects Cosmos and Poca " mentioned cross-chain technology, one of the implementation models of cross-chain technology is the hash lock, today white Let's explain in detail what is a hash lock.
01
Hash Lock and Lightning Network
Hash lock, the full name Hash TimeLock Contract, is a new form of technology implementation proposed in Lightning Networks.
The hash lock mode is a mechanism for the user to make a guess for the original value of the hash value for a specified period of time. To put it simply, on the basis of smart contracts, both parties first lock the assets. If they input the original value of the correct hash value within a limited time, the transaction can be completed.
Under such a mechanism, rapid confirmation of micropayments can be realized, that is, the goal of fast confirmation of lightning network is realized.
- Technical Perspectives | How much does the Python Smart Contract Execution API know?
- Comparison of IPFS and EdgeFS for Secure Edge/IoT Computing Use Cases
- Five major problems read through the PoA consensus algorithm
Next, Dabai will use the hash-locked application scenario asset exchange as an example to show how the lock of the popular science is achieved.
02
How to achieve hash time locking?
In order to understand how the hash time lock is locked, here is a comparison of two locks, one is a hash lock and the other is a time lock.
1, hash lock
After the hash value is locked, only the original value that generates the hash value is unlocked after the lock, assuming the number 123, the value after the hash is a03a, locked by a03a, regardless of the hash collision, only Can be unlocked by 123.
2, time lock
The time lock requires that the password for the hash lock be entered within the specified time. If the time lock is 1 hour, then the user is required to enter the password for the hash lock within 1 hour. If the password for the hash lock is entered after 1 hour, the time lock will still not be turned on.
That is to say, the condition for opening the two locks at the same time is to input the original value of the hash value within the specified time . The above example is to input "123" within 1 hour, and both locks are turned on. .
Now Dabai will use the hash time locking mechanism to convert his bitcoin to Ethereum in Xiaohei. The specific steps are as follows:
(1) Mr. Dabai becomes a random number S, and then the hash value H(S) of the random number is given to Xiaohe through the network, assuming that the random number is 123 and the hash value is a03a.
At the same time, the time is locked and hashed, and the time lock is assumed to be 1 hour. The hash of the hash lock is a03a. After the lock is completed, the bitcoin to be converted is locked on chain A.
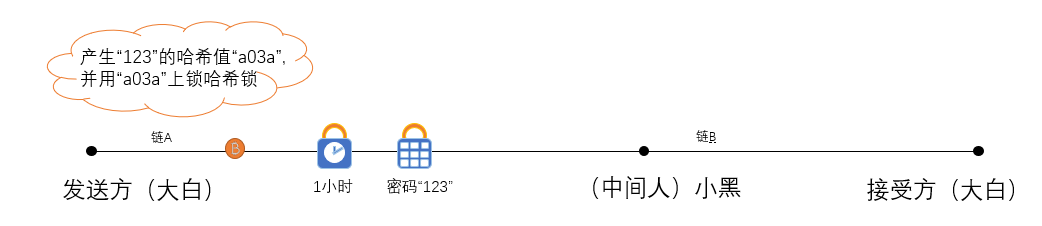
(2) After Xiaohe receives the hash value "a03a" given by Dabai, Xiaohe deploys the smart contract on Ethereum according to this hash value, and stores the equivalent value of Ethereum in the contract. Xiaohei's smart contract requires Dabai to provide the password "123" within the specified time to take the Ethereum in the smart contract.
This process is equivalent to, Xiao Hei also has two locks on his own. The hash lock is the same as the hash lock of the big white. It needs to be opened with the same password. The time lock is half an hour.
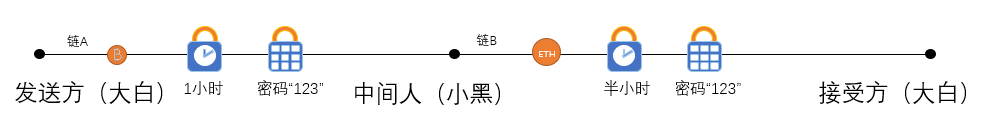
(3) Dabai uses this smart contract of Xiaohe, and enters his password "123" in half an hour, it can open the hash lock of Xiaohei on chain B, and can take away the black black smart contract. Ethereum (equivalent to the black Ethereum, because the smart contract is created by Xiaohei, the Ethereum in the contract is also Xiaohei).
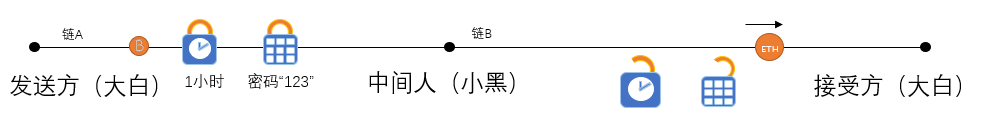
(4) Because Dabai entered the password when calling Xiaohe's smart contract, Xiaohe also knows that the password is "123". He only needs to open the hash lock on chain A through this password within one hour. Bitcoin will be transferred to Xiaohei.
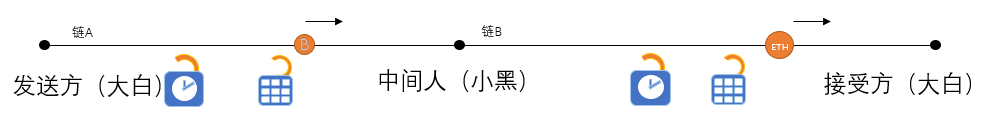
Through the above process, it can be seen that Dabai can realize the exchange of bitcoin to Ethereum by means of hash time locking. Of course, this often requires a lot of bitcoin to pay for the black money as a fee. After all, there is no free labor in the world.
03
Advantages and disadvantages of hash locking
After listening to the explanations on the white, some of the little friends will be confused? Is there a hash lock? After all, you must enter the password of the hash lock to remove the black etheric currency. Xiaohe can only open the hash lock on chain A after entering the hash lock password on chain B. It seems that the hash lock can be done, why do you want to add a time lock?
In the hash time locking mechanism, if the time exceeds the specified time, the token locked in the system will be reclaimed . Therefore, the addition of time lock effectively promotes the breaking of the hash lock on chain B in the time specified by Xiaohei. Xiaohe will also unpack the hash on chain A for the time specified by himself. lock. There is no mutual understanding between the entire process chain and the chain, which in turn promotes the speed of the transaction. And if the transaction fails, Hash Lock does not charge an additional fee.
However, the application scenario of hash lock is limited, and it supports fewer functions.
Do you hope that the current trading platform will vigorously promote hash locks and move toward decentralized DEX? why? Feel free to share your opinion in the message area.
——End——
『Declaration : This series of content is only for the introduction of blockchain science, and does not constitute any investment advice or advice. If there are any errors or omissions, please leave a message. You are not allowed to reprint this article by any third party without the authorization of the "Baihua Blockchain" sourced from this article. 』
Author | Yuxing
Produced|Baihua blockchain (ID: hellobtc)
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Analysis | Pre-selection and pre-submission mechanisms for Byzantine fault-tolerant consensus
- Unlock Bitcoin for more apps, Miniscript yesterday, today and tomorrow!
- Technical Guide | Teach you to discuss Wasm contract development: (C++)
- Getting started with blockchain | Ethereum 2.0 terminology at a glance
- Defects of the heaviest chain rule: "The Crown Prince" in the "Public Ancestral Blocks"
- Technical Perspectives | Reflections on Citation Dynamic Language Object Models in Virtual Machines
- Technical Guide | Teach you to discuss Wasm contract development
