Getting started with blockchain
Digital Signature: A digital signature is considered a digital simulation of a handwritten signature.
The important features of handwritten signatures are:
1. Your own signature can only be made by yourself;
2. Your own signature can be verified by anyone else;
- Proficient in IPFS: IPFS startup init function
- Video|"8"" domain name circle "Buffett" Dai Yue: not enough cognition, is to make leek
- CFTC Chairman: Facebook Stabilization Coin project design is "very smart" and is determining whether it is regulated by CFTC
3. Your own signature only contacts a particular file and cannot be used to support other files;
Before explaining digital signatures, you need to understand some basic concepts of cryptography:
Clear text: the initial form of the message
Ciphertext: Encrypted form
Key: A secret message used to complete cryptographic applications such as encryption, decryption, and integrity verification.
If we write the plaintext as P, the ciphertext as C, the key as K, the encryption algorithm as E, the decryption algorithm as D, then C=E(P), P=D(C); The system satisfies P=D(E(P)).
Symmetric encryption and asymmetric encryption:
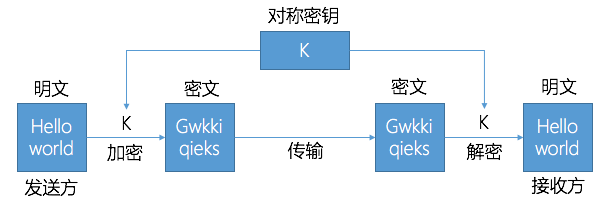
Symmetric encryption algorithm refers to the same secret key used in encryption and decryption. The same key can be used as both information encryption and decryption.
The encryption algorithm that requires the key is written as: C = E (K, P), and P = D (K, E (K, P)).
The working process is as shown in the figure:
An asymmetric encryption algorithm requires two different keys for encryption and decryption. These two keys are generally called public and private keys.
The encryption and decryption keys are different: P=D(KD, E(KE, P)). The public key and the private key appear in pairs. A key pair is obtained by a certain encryption algorithm. The public key is the part disclosed in the key pair, and the private key is the non-public part. When using this key pair, if one piece of data is used to encrypt a piece of data, it must be decrypted with another key. For example, encrypting data with a public key must be decrypted with a private key. If it is encrypted with a private key, it must be decrypted with a public key, otherwise the decryption will not succeed.
The working process is as shown in the figure:
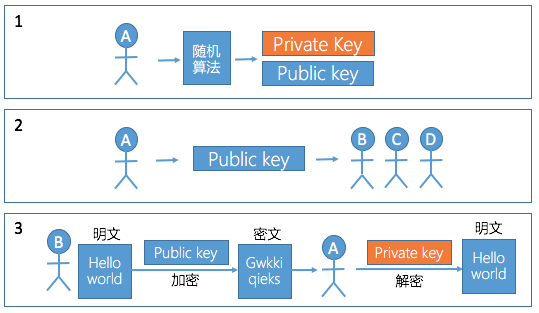
Steps 1-3
Step 1: A generates a pair of keys through a random algorithm, having a public key and a private key;
Step 2: A publicizes the public key and sends it to B, C, and D respectively;
Step 3: B wants to send a message to A. First, encrypt the information with A's public key, and then propagate the encrypted information (cryptotext) to A. After receiving the information, A uses its own private key. Decrypt, and get the original text of B to A.
Then digital signature is a series of digits that only the sender of the information can produce that cannot be forged by others. This digit string is also a valid proof of the authenticity of the information sent by the sender of the message. The process of generating and using digital signatures is shown in the following figure:
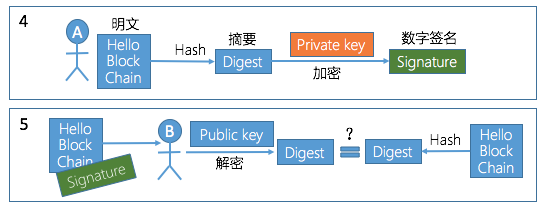
Step 4-5
Step 4: The information to be sent by A is hashed to obtain a digest, and is encrypted with a private key to generate a digital signature of the information.
Step 5: A sends the information to be sent and the digital signature to B at the same time, and B uses A's public key to decrypt the digital signature, thereby determining that the information is indeed from A. In addition, B compares the digest obtained by hashing the information sent by A with the decrypted digest, and can determine whether the information has been tampered with.
Source: BitTribe Lab
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Depth | Blockchain drives the cloud computing market to create a new generation of IT infrastructure
- 10 key words to give you a comprehensive understanding of Voice
- Week review | Kin Foundation launches fundraising challenge SEC, Australian Securities Regulatory Agency launches ICO guide
- Quiz, pyramid scheme, Ponzi scheme? Be careful with the blockchain game these "pits"
- Market Analysis: BTC turned into a downtrend channel, the bull market is coming to an end
- Sun Yuchen: This time I can finally eat a big waist with the stock god.
- Monthly News | May blockchain industry financing decreased by 8.2% month-on-month, both China and the United States are at a low point





