Introduction | Lightning Network Routing: Privacy and Efficiency Issues in Positive and Game
The line between the two points is the shortest. This is a well-known truth. But this sentence is not completely correct, at least in non-European geometry, it is wrong. Anyone who has seen lightning knows that lightning does not go straight, but in the process of going from one point in space to another, it avoids the resistance and automatically finds the most efficient path. Just a little bit of it.

– Four or four is a bit beautiful? (Source: wikimedia)-
Lightning network payment also encountered the same challenge, but it does not come with an optimization program like nature. We need to invest a lot of energy in the thinking, development and adjustment of the lightning network to make it robust and efficient. This article will explain how payment routing works on lightning networks, what areas still need improvement, and where the future direction of routing technology is going.
- Can fish and bear's paws have both? Discussing the interoperability of digital securities agreements from a compliance perspective
- Does the DeFi market have no ceiling? How to introduce quality assets is the key
- Lightning Network and US General Election: Andrew Yang becomes the first presidential candidate to accept LN payments
Current development of routing technology
The first thing to note is that routing technology has been put into use on the Lightning Network, and it works quite well, both on Android and on the iPhone.
Basics: nodes, channels, onions
The basic components of a lightning network are nodes and the payment channels (ie, edges) that connect them. A node can be any user, seller, or Lightning Network Service Provider (LSP). The nodes are connected to each other by a payment channel. Each node in the network is connected to at least one other node. However, nodes like light clients are unlikely to open a payment channel with another node, such as Tschego and Lonny, the best honey merchants in Johannesburg. Opening a payment channel is a chain transaction. If you want to open a payment channel for each new counterparty, what is the significance of building a second-tier network? Therefore, if you are paying between two unconnected nodes, it is best to find a path through the existing payment channel.

– It doesn't matter if they don't have contact with them. You can buy them by others (Source: wikimedia) –
How routing works
Currently, lightning networks use source routing and onion routing. Through source routing, the source node is responsible for calculating the entire path from source to destination. To do this, the source node needs to download a complete public payment channel table in order to calculate a path and calculate the commission cost and the required number of hops based on the load of all channels involved in the path. In peer-to-peer transactions, this process involves a large amount of data, and the amount of data increases as the network expands.
Lightning Network also implements onion routing, which greatly enhances privacy. Onion routing works like this: Suppose I have to pay Adam a sum of money, but there is no payment channel between us. But there is a payment channel between me and Nick, there is a payment channel between Nick and Jameson, there is a payment channel between Jameson and Andreas, and Andreas has a payment channel between ̶V̶i̶t̶a̶l̶i̶k̶ (joking!) Adam. therefore,
- I locked the payment in a box, locked the box in a larger box and attached the recipient's address;
- I locked the second box in a larger box and attached the address of a node closer to the receiving path.
- This is repeated until I form a chain of boxes, keys, and addresses (ie, transactions) with Adam.
I sent the largest box to Nick, and Nick opened the box and found the second box and the address of Jameson. He sends the second box to Jameson, who will open the box with his own key and will find the third box and the address of Andreas. Andreas opens the third box with the key and finds the last box and Adam's address. He sent the box to Adam, and Adam used the last key to open the box and received the payment data.
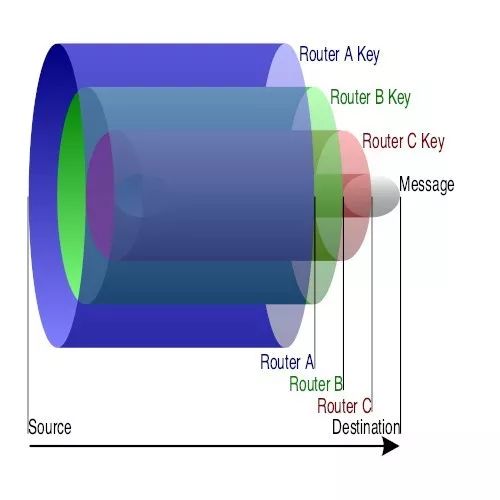
– The engineer said this is like an onion, and then it is unexplained by everyone! (Source: wikimedia)-
Each node only knows the addresses of the two nodes before and after, but cannot restore the entire chain or determine the identity of the payee. This is the onion route: the middle party only transmits on the basis of the information to know.
The onion network can further enhance user privacy. After using the onion route, the identity of the intermediate node can be hidden to a large extent, but the payer can still grasp the payee's IP address and the approximate geographic location. Tor can completely hide the user's IP address, ensuring that no one else on the network—even a direct channel partner—is aware of the identity or address of those intermediate nodes.

– You don't know how valuable it is before losing privacy. (Source: reddit)-
Significantly increase efficiency through PBMC
Transactions are time-limited. If the speed is not fast enough, it will be invalid. Therefore, increasing the speed of transaction propagation will also increase the efficiency of the lightning network. In the beginning, if the route is interrupted because of a node or payment channel, the algorithm will only ignore the situation and discard the message after a few seconds. If there is no way to store and use this information, payments that occur at or after the same point in time may take into account the failed node when calculating the routing path, wasting time and data costs.
Probabilistic Based Task Control (PBMC) solves this problem by understanding previous successful payment cases. Each node has a default success rate at the beginning and increases or decreases according to the actual transfer completion rate. The more payment transactions a network route has, the more the task control component understands the characteristics of the network and will be better able to plan the payment path in the future.
The future of routing technology
As the lightning network continues to mature and developers become more aware of current implementations, they no longer see basic functionality, efficiency, and privacy as three unrelated issues. Each new development will consider these three aspects and find the best balance between the three.
Trampoline payment
As mentioned above, once the network is expanded, the routing table will expand. At this time, source routing is not practical for mobile nodes with limited bandwidth and storage space. Someone has proposed a method called trampoline payment, which is to outsource the route to the "trampoline node", reducing the burden on the data node and the amount of calculation of the mobile node.
The trampoline node is the lightning network node that masters the routing table of the whole network and is responsible for finding a path between the payer and the payee. The node client does not need to download and continuously update the route map, just connect to a reliable trampoline node. Payments will jump from one trampoline node to another until the payee is reached.

– The boosting effect of trampoline payment is the same, but it is not so fun (source: djromanj)-
However, outsourcing routing to a trampoline node also presents a privacy risk: the trampoline node needs to know both the payment and the payment to find the payment path. However, before the trampoline payment technology went live, someone has come up with a reliable solution to solve the privacy problem.
The solution is to use two layers of onion routing: one layer for the payer and the payee, and the other for a randomly selected trampoline node chain. As is the case with onion routing, each node on the payment path can only obtain the necessary routing information. Because the chains are randomly chosen, it is difficult for intermediate nodes to identify sensitive information. The biggest drawback is that the more hops between nodes, the higher the transaction fee, but then, how low is the transaction fee for this low transaction rate of 10 times.
Ant route
After the detective ants randomly find the food, they will secrete pheromone on the way back to the ant colony. The more ants that walk on this trail, the more attractive it is. But after the food was evacuated, the pheromone on this trail disappeared. Ant colonies have found the best path for information transfer and communication by combining random and ordered behavior. Is it amazing?
– If you want to find the best path, don't choose the road where no one is going. (Source: wikimedia)-
The clever behavior of ants inspired Cyril Grunspan and Ricardo Pérez-Marco. They are committed to eliminating the hierarchy in the lightning network and letting all nodes perform all functions. Their "ant route" works as follows:
- The two nodes generate a large random number and each generate a "pheromone seed" (ie, a partial hash) that requires the other's pheromone seed to reconstruct the random number.
- They broadcast their respective pheromone seeds to neighboring nodes.
- When the node receives the pheromone seed, it verifies whether the seed exists in the memory pool of the network and whether the neighbor node has received the seed.
- If the node finds that it is receiving a new seed, it stores the seed in the memory pool and hands it over to the neighboring node.
- When two parts of the seed match somewhere in the network, they will return along the adjacent node until the payer and the payee are connected, so that payment can be made.
After the time period specified by each node has elapsed, all local data about the verified seed will be erased (just like the pheromone disappears!), and then all transaction data will be deleted in a short time. If the path is not found within the valid time, the transaction will fail.
Since each node only needs to know the immediate neighbors of the transport seed, the authors claim that the algorithm ensures the anonymity of the payer and the payee. Moreover, they also said that this solution eliminates the need for a local storage network routing table, which will greatly reduce the amount of related data and flatten the network structure. However, each node must perform some additional computational work.
Ant routing will be another very effective solution that will enhance the scalability of Lightning Networks while increasing privacy and efficiency.
(Finish)
Original link:
Https://medium.com/breez-technology/lightning-network-routing-privacy-and-efficiency-in-a-positive-sum-game-b8e443f50247
Author: Roy Sheinfeld
Translation & Proofreading: Min Min & A Jian
This article is authored by the author to translate and republish EthFans.
(This article is from the EthFans of Ethereum fans, and it is strictly forbidden to reprint without the permission of the author.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Opinion: Even if BTC rises to $100,000, 79% of the coins cannot return to historical highs.
- Digital Currency in the Eyes of Economists – Trends: Creating a Future
- I want to use the blockchain to innovate my SWIFT, but I still can't resist the subversion of the blockchain.
- God turns! The Belgian Debo hits the face of CSW and is exposed to the court.
- Horizontal resolution of the deposit certificate panorama: Will the deposit certificate become a large-scale application scenario for the blockchain?
- Even if it is a bull market, it will not save the competitive currency market.
- Accept Bitcoin to buy a ticket, open an exchange, Norwegian Airlines CEO loves cryptocurrency






