Introduction to Asymmetric Encryption: Vernacular Analysis of Private Keys, Public Keys, RSA
All previous encryption methods were symmetric encryption, and the straightforward point is that both encryption and decryption are the same password.
For example, if you use the password corresponding to the bank account, you can take out the cash. If you hold this card, you can tell him that the password can also take out the cash; for example, your email login password, such as WeChat, Alipay login password, etc. These are symmetric passwords. Applications.
As long as the same key is opening a lock, it is a symmetric password.
However, there is a problem with symmetric passwords that is difficult to solve, that is, the transmission of secret keys.
- Love and mourning of the alliance chain: development is difficult, where is the source?
- Visit: What is behind the brush of the digital currency exchange?
- Interview with famous economist W. Brian Arthur: historic changes are taking place, blockchain will enter everyday life
The quantum communication mentioned earlier is also the most advanced and secure key distribution method currently known for key transmission, but in general, it is difficult for ordinary users to use. Imagine the following scene, your wife gave you a call, said that he is shopping online, you need your credit card password, you told her, he will shop, if this time, someone is also monitoring your phone, he is also shopping Just wait for this password, he also went to swipe the card, what should I do at this time?
The problem is in the transmission of the key.
The more links, the easier the error, can you cut off the key transmission?
can. Encrypt with a public key, that is, use a pair of keys.
Two keys? Open a lock with two keys. Isn't this lock a bad lock? it's not true.
There are now two secret keys: public and private.
The public key is the public key. This key can be known to anyone; the private key is local, the private key, only you know, the private key is not sent and not transmitted, because there is no transmission problem without transmission.
For example, if you want to send an email file to your family, this is a very secret thing. Your family generates a key pair on the Internet, that is, the public key and the private key, and then sends the public key to you, the private key. Record it yourself, don't put it online.
After you receive the public key, you encrypt the information you want to send with the public key, and then send it to your family. After receiving it, the family will decrypt it with your private key and you will see your important information.
There are a few points in it, the public key, which is also sent to you by the family. What if it is intercepted by others?
It doesn't matter, even if many people know that the public key is okay, because the public key can only be encrypted, and the private key corresponding to the public key is decrypted, that is, others know your public key, it is only convenient for them to send you information. They can't solve it when they finish the secret.
This is how asymmetric encryption works, because public keys, something that was not historically available, so asymmetric encryption is also known as public key encryption.
The method of generating the private key public key is available on the Internet and need not be described here.
Summarize the characteristics of public key encryption:
1. The public key and the private key must appear in pairs and cannot be generated separately.
2, the public key can be known to anyone, the private key is only known to the person receiving the information;
3, A process of sending B information is: A holds B's public key to encrypt a piece of information to be sent, and when B receives it, it uses its own private key to decrypt it.
What is the use of public key encryption?
Bitcoin encryption is public key encryption. So you have a private key public key and address, the public key can push the address, the address can not push the public key, even if it is launched, it does not matter, because the public key is the public key, who wants to know. Essentially, the so-called Bitcoin-generated account is to generate a secret key pair. With the public and private keys, the public key then launches an address, and a bitcoin account is generated. This method of generating accounts is more convenient and safer than opening an account in traditional finance. Of course, traditional banks are also very safe. Centralization will protect your account. Bitcoin is the first time in human history to solve security with technology. problem.
We will soon talk about the encryption principle of Bitcoin. Let's talk about it today.
What is RSA ? Why do many people talk about RSA?
RSA is the most widely used encryption method in asymmetric cryptography. Of course, there are others. For example, there is a magic elliptic curve encryption in Bitcoin, which is an asymmetric cryptography, but not RSA. Once, the choice of this elliptic curve encryption method, praised by the Ethereum promoter vitalik, said that Nakamoto may be Mongolian, the selection is so good.
RSA encryption is called RSA encryption because the initials of the founder's name are R, S, and A. When they send the article, they use Alice and Bob's names to represent A and B. Therefore, cryptography forms general management, "Alice Send a bitcoin (or a piece of information) to Bob, and such a sentence begins to appear. The eavesdropper is always called Eve.
Well, after reading the above content, in fact, the main knowledge of asymmetric encryption has been understood today. The following content is more difficult, and readers can read it selectively.
What is the approximate method of RSA ? Why do some experts always mention "the prime factor decomposition of large numbers"? What is the relationship between "factor decomposition of large numbers" and RSA asymmetric encryption?
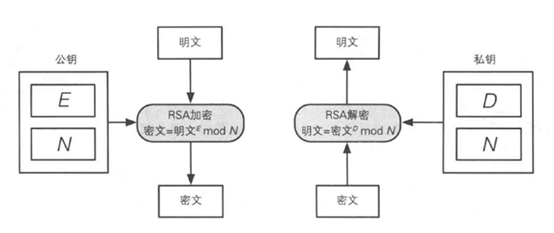
The encryption process is the E-th power of the plaintext and then mod N. Mod represents the operator of the multiplication remainder.
The combination of E and N is the public key, and the combination of D and N is the private key. E is taken from the word encryption encryption, D is taken from the word Decryption, and N is taken from the word number.
N=p * q, p and q are prime numbers, very large prime numbers, so it is difficult to crack. If it is a very simple prime number such as 2 and 3, it is too simple, of course, the real operation is binary, 512bit Multiplying the prime numbers is one of the reasons why it is difficult to crack the private key. Because humans have not found an efficient method for mass factor decomposition of large integers, RSA is safer . The security of the current banking system is also RSA encrypted. The N requirement is greater than 300. If you want to decompose such a number, the required time unit is in the order of 100 million years. The billions of years to crack a password, assuming that the technology is not at the current level. Breakthrough words.
Why add something like mod N? Because no such is a logarithm problem, it is easy to solve. If you have mod N to find the plaintext, it becomes the problem of finding the discrete logarithm. Similarly, humans have not found an efficient method for finding the discrete logarithm .
In view of the many mathematics formulas in the previous article, today's explanation about RSA is controlled within 500 words. This is an introduction. If you are interested in RSA, you can also use the private communication to search for more information online, but for the district. For blockchain practitioners or digital currency investors, you only need to understand the key points of this article. After all, when you see discrete logarithms, many readers can't stand it anymore. It doesn't matter, master the key and absorb the essence.
Understand that asymmetric encryption (public key encryption) is very important for understanding the public key of Bitcoin and the wallet and working principle, so today we will explain the asymmetric encryption technology.
If I send out money instead of a letter, the public key is encrypted for you, you can use it with a private key, is it bitcoin? Or, conversely, I will send you a ledger information, you can open this account information, so the last one of this ledger information is written, I transferred 10 bitcoins to you, is this information you have 10 A proof of bitcoin, that is to say, this book information itself proves that you have bitcoin? Information becomes money, and follow this line of thinking to understand bitcoin. I will talk about it later.
The door to this world is slowly opening, thanks to the hidden method, the displacement replacement method, the Virginia encryption method, the Enigma machine, and the core of the bitcoin and blockchain will soon be touched. bumped into.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Viewpoint | Say goodbye to traffic and funds, is there still value in digital currency?
- How blockchain technology can improve the lives of 22 hospitals
- Viewpoint | If these three technologies improve, blockchain technology will be more widely used
- Explore: Blocking and expansion of blockchains
- Analysis: The DAO governance trend is gradually rising, and the blockchain needs no braking mechanism?
- The Bank of International Settlements economists propose a new method for financial market monitoring based on DLT
- Weizhong Bank issued a “good” social governance framework and used blockchain for social governance






