Make wedding dresses for others? Cryptocurrency mining virus may be secretly letting your computer help others mine
Source: changelly
Compilation: First Class (First.vip)
According to Kaspersky Lab data, the number of computers and mobile devices invaded by the mining virus (CryptoVirus) increased by 44.5% last year.
- Sheknows | Together, the alliance chain and the public chain have the same goal?
- The last decade of blockchain: Looking back at 2010 to 2020
- Learning to Power: Hainan's Blockchain Development Attracts Global Attention

Hackers no longer rely on encrypted viruses to blackmail money—they just implant a virus on your computer to hide it. This encryption virus is a mining virus. What harm will they do to your device? How can I get rid of them?
What is a mining virus?
In short, a mining virus is a piece of code or software that runs a mining program quietly on a user's personal computer or smartphone. Attackers can use the computers of unsuspecting victims to mine cryptocurrencies.
The most common mining virus is used to get Monero or ZCash. There are also many applications dedicated to mining small altcoins, because it is more efficient to dig some small altcoins with a personal computer than mining Bitcoin. In addition, these viruses can even run on the Android operating system. There are also cases where hackers use NiceHash and MinerGate.
Generally, developers of mining viruses are not limited to mining based on CPU or graphics card. They also use various spyware functions to complement their virus programs. For example, some mining viruses can steal encrypted wallet files, social network data, or credit card data. In addition, after this attack, your computer will become very vulnerable and insecure.
How does a mining virus work?
The working principle is very simple. The program performs a hidden mining startup operation and connects the computer / mobile device to a mining pool. These operations will seriously occupy the processor of the device and obtain unauthorized "free" computing power for fraudsters. The fraudsters will directly put the cryptocurrency earned by "free computing power" into their wallets.
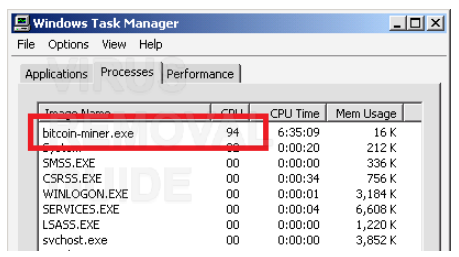
(Hidden mining process in task manager)
Mining pools are the ideal way to create such "botnets" because most mining pools support an unlimited number of users connected to the same address, and their ownership relationship does not need to be proven. After connecting to hundreds of computers, hackers can enjoy a pretty good income and use the services of large mines.
How does the mining virus spread and how is it detected?
Generally, a mining virus enters a computer by:
Download files from the Internet. Hackers have found many ways to publish their programs and embed them on some suspicious websites. Torrents are a common way for viruses to spread.
· Physical contact with a device that has been compromised by a virus. For example, other people's flash drives and other hardware storage devices have been invaded by your mining virus and connected to your device.
· Unauthorized remote access. Classic remote hacking is also carried out this way.
Many people will try to use hidden mining software at work by "infecting" computers throughout the office. In some cases, hackers also spread their software through Telegram. Maybe you thought you downloaded 100% safe software (games, patches, tools, etc.), but it may still be hacked during the update process.
The "hidden" way of mining viruses
Sometimes it is almost impossible to detect a mining virus. There are three common ways to hide mining viruses:
· Virus as a service. In this case, you will not see any separate process task manager. Some svchost.exe will use system resources but are absolutely legal system processes. If you disable them, chances are your computer will stop working.
What to do in this case? You can search for a service with a suspicious name through msconfig.exe, but there is a more effective way-use Process Explorer free software.
· Moderate consumption, slow mining. In this case, the virus software is not designed for fast cryptocurrency mining, but to ensure the longest lifetime of the mining virus. Such software will not consume all available system resources, but will consume them in moderation. At the same time, if some programs that consume a lot of resources are started, the virus will stop running, so as not to slow down the operating system and complicate detection. Advanced mining viruses even monitor fan speed to avoid overloading the system due to excessive use of computing power. Since some viruses stop working when the task manager is opened, it is unlikely that they will be detected in this way.
· Rootkit mining virus is the most complex type of malware. Neither Task Manager nor the most effective antivirus software can detect this type of mining virus. So how do you find out? The point is that such viruses must remain in constant contact with the mining pool. If you are in idle mode, ordinary computers can't actually access the Internet. When you notice that your computer is connected to the Internet, it may be invaded by a mining virus. At this time you can ask the experts for help.
How to remove mining virus?
You can easily detect a simple mining virus: open the task manager and find any task that uses more than 20% of the CPU power, most likely a "hidden miner". All you have to do is end the task process.
If you think your computer is contaminated with malware, you should scan with the latest version of an encrypted virus scanner, such as Reimage or SpyHunter 5. Such tools generally detect and remove mining viruses immediately. In addition, experts recommend using Dr. Web, CureIT and Malwarebytes anti-malware solutions.
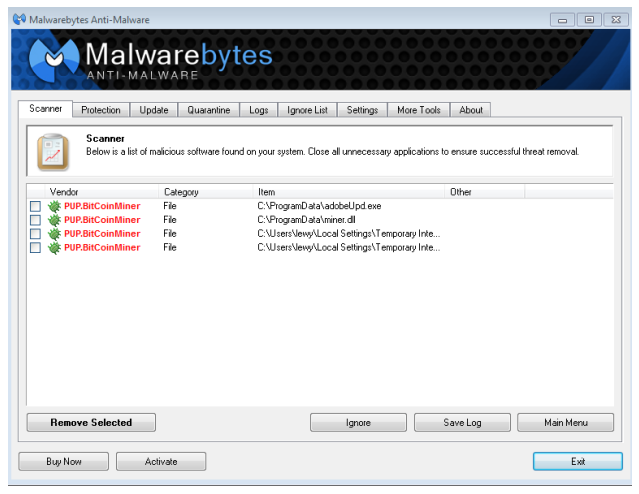
(MalwareBytes scheme)
Be sure to check the system frequently and pay attention to changes in the speed of the computer. If you have a bitcoin virus on your computer, you can see if there are other accompanying viruses-remove them to prevent the loss of sensitive information.
How to prevent mining viruses?
Taking the following measures at the same time will effectively prevent the intrusion of mining viruses:
· Install and regularly update anti-virus software, checking the system for suspicious programs from time to time.
Keep your operating system up to date.
· Pay attention to what is downloaded and installed. Viruses are usually hidden in hacked software, and free software is often the “hardest hit area”.
Do not visit websites without SSL certificates.
· Try some specific software. There are plugins that can be very effective in protecting your browser from hidden mining, such as MinerBlock, anti-webminer and Adblock Plus.
· Regular backups. If your device is accidentally infected with a mining virus, you can eliminate it by rolling back the system to the latest "healthy" version.
In short, like other malware, mining viruses can invade when a user's computer does not have adequate security measures. Keep an eye on downloaded files, websites you visit, and the devices you use. If you notice that your computer performance is severely degraded, you need to see if someone is secretly mining with your computer.
The source of this article is Chanegelly. The translation was provided by First.VIP_ Maggie. Please reprint the information at the end of the article. Thanks for reading.
original:
https://changelly.com/blog/beware-of-bitcoin-mining-virus-how-to-detect-and-prevent-it/ manuscript source (translation): https://first.vip/shareNews?id= 2560 & uid = 1
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- 38,000 new addresses added in one day, DeFi and Istanbul upgraded to inject new blood into Ethereum
- Xiao Lei: Blockchain is the next Internet + dollar super system, and the only US opponent is China
- Microsoft blockchain cloud platform Azure launches non-homogeneous tokens to reward active community participants
- Zhu Jiaming: Blockchain is likely to bring a "paradigm revolution" in the scientific field
- Interview with Qu Shuangshi, Development Research Center of the State Council: Stablecoins with specific issuers and anchoring certain collateral may become real "payment currencies"
- DeFi week selection 丨 DeFi cannibalizing PoS security? Vitalik debates with researchers
- Zhu Jiaming's latest speech: people, space-time, public welfare and blockchain






