Microsoft's project is comparable to Facebook's currency, but many people still don't understand it and "make it" in the drums.
Each of us needs to have our own set of digital identities to store all of our digital identity-related information securely and privately. This set of own digital identities must be easy to use, and only the user himself can fully control the storage and use of identity data.
—Ankur Patel, Chief Product Manager, Microsoft Identity When you rent a shared charging treasure or rent a car through Alipay, you can enjoy the deposit-free policy if your sesame credit score is up to standard. This credit is based on your consumption behavior data in the Alipay ecosystem. These data are stored in the Alipay server, and you may not be aware of it yourself, and the use of the data does not require you to know or authorize it.
If you want your personal information, degree diploma, on-the-job status and other personal information to be securely stored in multiple nodes rather than an organization in encrypted form, others or organizations need to query your relevant information. Authorization, the results of the inquiry are provided to the other party in the form you approve.
Earlier, the " Block Chain and Bitcoin's "No. 1 Iron Powder": Microsoft " in the vernacular blockchain highlighted the important strategic significance of Microsoft's DID project.
- QKL123 market analysis | The number of coins destroyed in the day, the pot of the hearing? (0730)
- The storm set off a storm, the Internet "old" is difficult to grasp the blockchain "straw"
- The bitcoin transfer advantage is once again highlighted! Whale transfer of $468 million requires only a few hundred dollars in handling fees
In fact, ION (Identity Overlay Network), which was released by Microsoft not long ago, has been widely debated in the industry. ION is a decentralized ID (DID) implementation.
Microsoft's DID represents a large Internet company that embraces decentralized technology and has launched a grand blueprint for using DID technology to build a future identity account system.
01 What is a DID?
According to the definition of the W3C, DID is a digital identity system for verifiable, self-governing, DID is independent of any centralized registry, identity provider or certification authority.
In terms of implementation, a standard DID is divided into three parts:
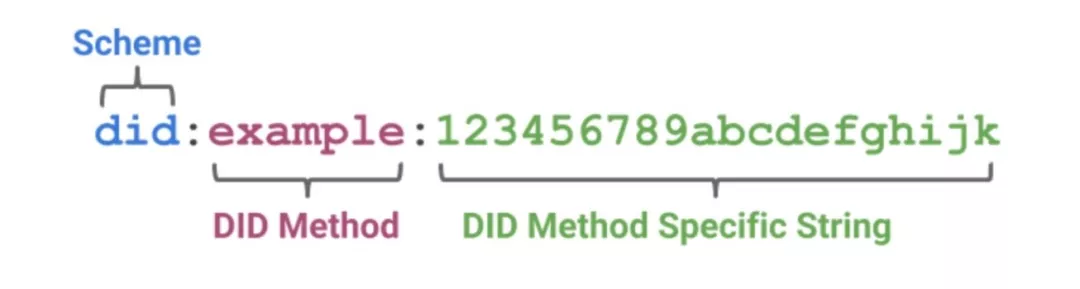
In the above example, "did" is the prefix, "example" is a DID method, and "123456789abcdefghi" is the specific DID identity.
What is the DID method? The DID method is a way of defining how to access a DID document and can be understood as an implementation of a DID. According to the latest documentation from the W3C Registry, there are currently 28 registered DID methods, including well-known ION, uPort, IPLD, and more. Most of the DID methods correspond to a blockchain network, such as ION corresponding to the bitcoin network.
The "did:example:123456789abcdefghi" in the above example refers to the identity provided through the example network or blockchain, and example is mainly used for example in W3C.
A DID can store data about this ID. The official name is the DID document .
02 How to use DID?
When it comes to DID, Verification Claim is usually indispensable. Currently, most DID sample scenarios are verifiable claims. For example, "Zhang San is a listed company employee" is a verifiable statement.
What scenario can the verification statement be used in? Below, the vernacular blockchain (ID: hellobtc) will be illustrated by two examples.
The building's access control system is a typical DID application. Visitors use their own DID to apply for authorization in advance. Any employee who is approved by the company can use their own DID to accept the application. Visitors can use their own DID to enter the building smoothly.
Or, if the user goes to the car rental car, the user is usually required to provide a deposit to reduce the operational risk, but for some qualified users, you can provide a deposit-free requirement, such as a listed company or a large state-owned enterprise employee.
How does the above function work in the DID network? Take the proof that the rental car needs to provide:
Method 1: The user provides the work card of a listed company or a large state-owned enterprise. This is the most direct method, but the user will expose a certain degree of privacy , which will provide the car rental party with unnecessary work information.
Method 2: Confirm by the DID verifiable statement that the DID document provided by the user declares that the user belongs to a listed company or a large state-owned enterprise employee, and the rental car can go to the issuing authority for verification, and the verification result will only return a “yes/no” As a result, there is no need to return the user's specific job information, so the user retains his or her privacy while meeting the business needs.
In the above example, the dealership needs to verify the results to the issuing authority (Issuer), which is generally a trusted third party, such as LinkedIn. When a user obtains a verifiable statement, they may need to provide their own work card certificate to the issuing authority, and the issuing authority may generate a verifiable statement for the user to use.
03 How is DID implemented?
As mentioned earlier, DID is implemented through different methods. The method provides a way to access the DID, taking the recent ION (Identity Overlay Network) released by Microsoft as an example.
ION accesses the Bitcoin network by implementing the Sidetree protocol. Since Bitcoin is a slow processing network, ION combines a large number of DID operations into one uplink operation by batch merging in the second layer of Bitcoin, and the modified data entity exists in IPFS, and the hash of the data entity. The existence of a bitcoin network to achieve trusted storage of DID data.
Like all Sidetree-based DID networks, ION includes three main features: a core set of Sidetree logic modules, a bitcoin-based read-write adapter, and a CAS protocol that replicates data between nodes (such as IPFS). These three systems together create a second-tier DID network over existing Bitcoins, and ION can support thousands or even tens of thousands of operations per second.
Since Bitcoin winding requires transaction fees, maintaining ION nodes also requires cost, but ION has not yet announced a complete economic operating mechanism. ION can charge users who perform DID data operations, but whether this charge can cover the ION network operating cost is still a problem. Of course, Microsoft can fully bear the operating costs of the ION network, but this is in line with the original intention of DID decentralized operation.
In use, Microsoft's DID and current Alipay scan code rental charging treasure process may be similar.
According to Microsoft, the Microsoft Authenticator App is used by millions of users every day for authentication. Microsoft plans to support decentralized identity and testing in the application, with the user's consent. This application manages user identity data and acts as an encryption key. In this case, only the ID is stored in the chain, and the identity data is encrypted with the key and stored in the ID Hub under the chain.
04 What is the difference between DID and a previously centralized system?
Simply put, the blockchain-based DID is the value of the user's digitalization on the Internet. From an implementation point of view, implementing the above-mentioned check-in or car rental scenario may require only a smart contract with very little code, and does not need to rely on any resources of the company. However, in accordance with the common practice of blockchains, the user's "authorization" query operation requires a small fee fee to support the miners behind the execution of smart contracts and data entry.
The DID is anonymous by default, a bit like a mobile phone SIM before the real name authentication. It is technically unique and unforgeable. Since the operator has controlled the issuance of the card, it takes a certain amount of work to prove that a group of accounts is controlled. Even if the SIM card does not have a real name, because it is unique and unforgeable, it is also a good real identity for each app.
Unlike a SIM card, users have full control over their anonymous identity. The user's data can be selectively encrypted and stored in the blockchain, such as the user's academic credentials, only the user and the corresponding authoritative DID can access the details of the data, and the querying party will only see the authoritative DID to the user's academic qualifications. The certificate is recognized by the certificate, thus ensuring the security of the data.
With DID, users can provide limited information to the systems they visit. For example, only the nickname Hellobtc is provided, which prevents users from repeatedly registering a system to repeatedly expose their own large amount of private data. Users can also choose to associate some of their physical identities, such as social accounts, with DIDs. If you associate your identity information with your DID, you can do things like swiping your face at a hotel.
In terms of privacy, DID can selectively disclose its own private data. For example, when taking a taxi, only announce your own taxi history and credit to the other party. Since the blockchain is essentially anonymous and some of the data is cryptifiable, this is technically not difficult to achieve, and all of this (disclosing only the information the other party needs) can be done automatically through smart contracts, without the need to install applications like Android. , prompting the user to make complex authorization choices.
05 summary
After DID becomes the infrastructure of the Internet, if it is associated with a smart contract and supports cross-chain applications, users can easily use the decentralized network to connect to a shared car in the same city, and the shared driver can also view the DID credit information of the order. Decide whether to take the order.
The user can perform a takeaway contract for the DID of a restaurant. After the restaurant receives the order, the smart contract will automatically trigger the delivery person's DID to execute the delivery contract. After that, all settlements will be carried out automatically, and there is no need for a centralized organization to coordinate.
Due to the non-tamperable nature of the blockchain, the user's credit history is naturally formed.
For workplace records like LinkedIn, a user needs to form their own work history through DID, and each experience needs to be certified and recognized by the relevant colleague (DID). Since the information cannot be tampered with, the colleague who undertakes the certificate will pay more attention to the authenticity of the information, which will form a very valuable data precipitation.
DID will be an important starting point for the transformation of the information Internet to the value Internet.
Issue 290: Do you want to have your own Decentralized Identity (DID)? why? Feel free to share your opinion in the message area.
——End——
Original: Tim Yang
Source: vernacular blockchain
『Declaration : This article is the author's independent point of view, does not represent the vernacular blockchain position, and does not constitute any investment advice or advice. 』
Editor's Note: The original title is: "The industry elite has long known that Microsoft's project is comparable to Facebook's currency. Many people still don't understand "Meng" in the drums."
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Hearing Preview: Circle CEO calls on Congress to treat cryptocurrency as a new asset class
- Encrypt the world gang, find out
- What is Plasma? Plasma Cash?
- EdenChain: The global platform for programmable economy
- Editor-in-Chief Interview | Liu Weiguang, Vice President of Ant Financial Services: Unmanned Areas Coming Out of Blockchain Business Exploration
- Hearing Prospects | Law Professor: The United States does not need cryptocurrency, only need to upgrade the system
- The world's first blockchain loan landed, Chengdu enterprises started with ant blockchain



