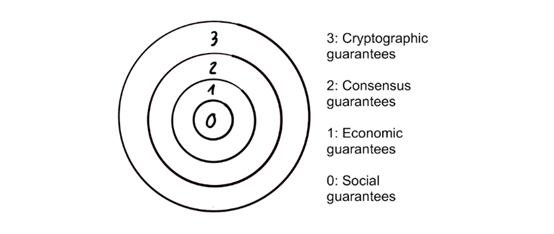
Onion model of blockchain security: additional security is added at each layer
Author: DeribitMarket Research
Translation: Zi Ming
Source: Crypto Valley
Editor's Note: The original title was "The Onion Model of Blockchain Security"
- A picture of the central bank's digital currency DCEP "Past Life and Life"
- Financial decentralization: Can DeFi replace traditional finance?
- See how this 80-year-old coffee brand has fun with blockchain
According to experience, public chains are safe. In most of their history, they have successfully achieved their design goals, that is, processing transactions without any errors. This is indeed the fact we observed, but it is more difficult to come up with a theory to explain why this is so.
Individuals generally use the things they know best and value most to explain the safety of their favorite projects. It is believed that a public chain guarantees its security through economic incentives, globally distributed hash power, global nodes, or fanatical communities (maintaining a set of consensus). This view can be understood, according to the law of the instrument (The law of the instrument), we rely too much on the tools we are already familiar with. In other words, if your only tool is a hammer, then you tend to treat everything as a nail.
I don't think that any of the above factors can explain this phenomenon alone (ie processing transactions without making any mistakes). Although there are perfect protection measures in a particular field, it is not difficult to attack them. For example, in a network where all users run a complete node, the miner can still replace the entire blockchain with a spare blockchain (he controls all coins on this blockchain). Therefore, it must be the interaction of different combinations to maintain a license-free digital currency system at a relatively safe level.
Onion model of blockchain security
The model I proposed hopes to form a coherent combination of various elements of security. The goal is to be able to look at the public chain more comprehensively to discover its strengths and weaknesses, and allow comparisons between different blockchains.
The security of the public chain is similar to onions, and each layer adds additional security:
To permanently destroy a public chain, it is necessary to destroy the user's trust in its ledger state (ownership list) and the ability to reliably update that state in the future. All higher-level services are designed to prevent this from happening.
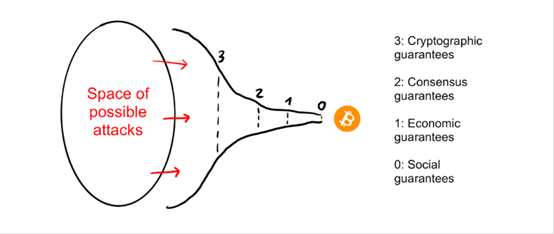
Attacks have to pass through these “funnels” of defense layers to reach the core. Now let's discuss these layers one by one.
Cryptographic guarantees
The outermost defense is guaranteed by cryptography. Cryptography gives the most reliable form of protection, so we hope it can take on the heavy lifting and prevent most attacks from the start. In addition, the following points need to be guaranteed:
- Do not create digital currency out of thin air. All blocks (and therefore all block rewards) must have sufficient work permits attached to it.
- Don't spend other people's digital currency. The digital signature must ensure that the effective owner of the digital currency can spend it.
- The content of the old block cannot be changed retroactively. The hash pointer ensures that the attacker must change all blocks built after any old blocks he wants to change.
All attacks against the above points will be blocked by the first layer of the "funnel".
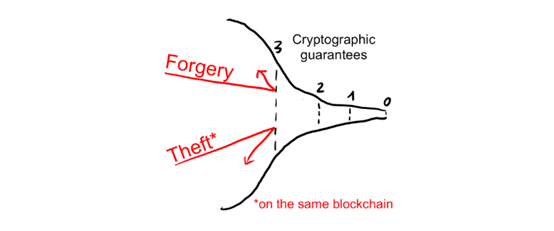
Although cryptography is very powerful, it also has some other guarantees that it cannot provide. For example, it cannot decide which of two equally long blockchains is the "correct" blockchain (this requires a certain understanding of the real world, such as "which blockchain other people will go to" , "Which blockchain has a higher long-term market value"). It also does not force miners to mine on specific blocks, nor does it allow them to publish blocks once they are discovered, or even ensure that they contain specific transactions.
Consensus guarantees
Some attacks through the first layer will be blocked in the consensus guarantee. In the consensus set by Satoshi Nakamoto, nodes will constantly observe the network and automatically switch to the longest (most expensive) chain. Miners will only get paid when their blocks eventually become part of that longest chain, so they need to converge with other miners. Therefore, for miners, they will be more inclined to mine at the top of the blockchain, because their blocks are most likely to be recognized by other miners there.
If a malicious miner wants to mine on the previous block, he will enter a competitive state with other miners who continue to mine on the top of the blockchain. Only when he finds several blocks faster than the sum of others can he catch up with the entire chain and pull the blocks he dug out and the chains afterwards to the longest. But according to his share of hash power, even a short fork is difficult for him to succeed.
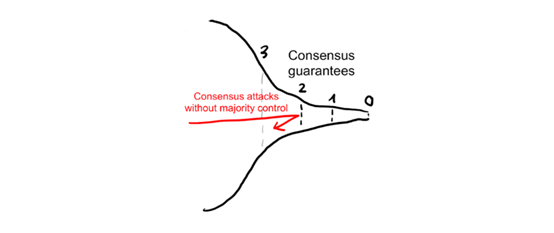
In order for the attack to function reliably, the attacker needs to gain control of the consensus layer first. This means controlling the hash rate of PoW greater than 50%, or controlling the equity greater than 33% in the proof of stake based on BFT, or controlling the equity greater than 50% in the PoS based on the longest chain.
The difficulty of operation is often underestimated. For example, large organizations are often considered the biggest threat to the public chain. However, if they want to purchase the necessary hardware in the primary market, they will soon find that there is a limit to the annual output of chip foundries in mainland China, Taiwan, and South Korea. Moreover, their production capacity is further limited by the rare earth mining in Australia, wafer production in Asia and Africa, that is, the annual production capacity is limited. This is true even for highly motivated buyers. It takes at least 2-3 years to obtain the necessary hardware in this way, and it is unlikely that it will not attract relevant attention during this period.
Economic guarantees
I think that because of the economic guarantee, even if a single entity controls the consensus layer, the blockchain will not immediately collapse. By setting the correct incentive mechanism, the blockchain can link real-world costs to wrong behavior. The main reason comes from the native token, which introduces the concept of digital scarcity (ie value), and can reward good behaviors (rewards and fees with blocks) and punish bad behaviors (by cutting safe deposits or seizing future rewards) .
The size of these incentives will vary with the level of actor control of the consensus layer. A miner who controls a large amount of hash power (even most of them) will increase the damage to the system proportionally. Therefore, the attacker would be discouraged by being financially punished.
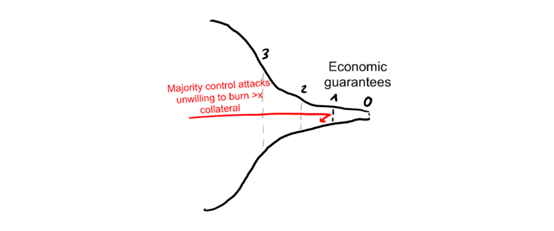
Not all economic incentives are created equal. Relative to the value of the network, the greater role of block rewards is to make the network more secure, because it forces miners to be more defensive in mining. This is why the decline in block rewards poses a risk to the security of BTC).
When Hash computing requires specialized hardware (that is, ASIC) and these hardware cannot be used in other fields, miners will be more defensive in the game. So far, all mining attacks have occurred on smaller networks, which is no coincidence, because these networks have accepted a wrong view called resisting ASICs, in which case attackers can easily prevail (for example By renting hash power).
Social guarantees
As we said before, to permanently destroy a public chain, it is necessary to destroy the user's trust in the state of the ledger (list of ownership) and the ability to reliably update the state in the future.
This is very necessary, because the blockchain is not the purpose itself, which means that there is no reason to deny the chain because some parts of the chain temporarily fail. Blockchain is just a means of automating the process of establishing social consensus among its participants, and is a tool for maintaining and updating shared databases. The state of the database is valuable to the participants. When the system fails, they have a strong incentive to restore the system.
For example, if there is a problem with the encrypted hash function, the social layer can reach an artificial consensus (under the guidance of technical experts) to replace the problematic part.
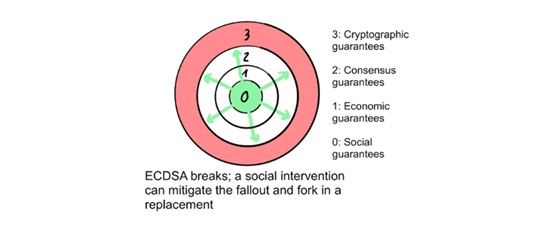
Similarly, if a consensus attack bypasses economic security, social security can still block it. If an attacker with the majority of Hash computing power fully accepts his own economic losses and starts to conduct a DOS attack on the network by hollowing out blocks, then miners can vote to change the PoW algorithm, thereby removing the mining Control.
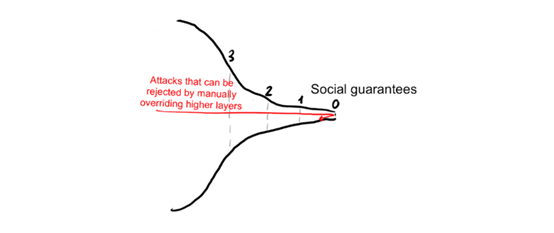
We can see that the only way to destroy a blockchain forever is to either let the user lose interest in the ledger state itself, or to destroy the system to an impossible repair level.
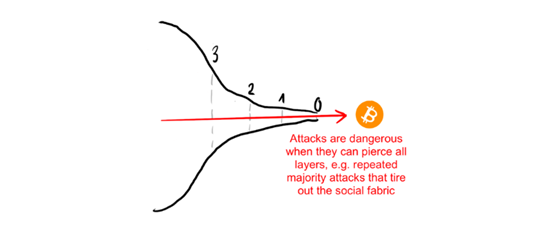
When an attack can penetrate all layers and eventually wipe out the social core of the system until it cannot cause deeper and incurable damage, then such an attack is quite dangerous.
In order for both self-healing and manual intervention to work, the community of each project needs to form a strong community consensus around the main attributes of the project. As far as BTC is concerned, these core attributes are the irreversibility of the transaction, the ability to resist censorship, changes that are not backward compatible, and the 21M token ceiling. When social intervention becomes necessary, they can serve as a blueprint for social intervention. These core attributes create Schelling points around what needs to be repaired and what does not.
These core attributes of a project will always be improved through repeated negotiation, and not all users will agree on all attributes. However, the stronger the consensus around a particular attribute, the more able to persist in difficult times. Considering the social layer as the bottom of any blockchain, we can recognize that it is a great threat to social layer attacks. If malicious developers can secretly make harmful code modifications without supervision (especially in projects with frequent hard forks), the higher layers will become more vulnerable.
to sum up
I think the onion model is useful, it can help us see how the various layers of the blockchain are combined to create a safe whole. In some ways, it builds on my previous article on Bitcoin ’s social contracts: any public chain starts with a core set of consensus, which is a blueprint that the system hopes to achieve.
This set of consensus must be translated into rules of interpersonal behavior, and then we automatically execute these rules to create different types of guarantees: economic guarantees, consensus guarantees, and encryption guarantees. By constraining the behavior of participants, the system becomes socially scalable, enabling cooperation in a low-trust environment and creating wealth together.

We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Popular Science | Use the overlay to change the format of the Ethereum state tree
- One article to understand the latest research and development progress of Ethereum, zero knowledge proof, sharding and other topics
- Topaz, the first testnet with Eth2.0 Phase 0 mainnet configuration, has been released
- The central bank's digital currency is ready: the wallet is undergoing internal testing, and related concept stocks have risen collectively
- The central bank's DC / EP beta is out, and we guessed about these functions …
- Observation | A picture to understand the Ministry of Industry and Information Technology's blockchain standard commission
- Agricultural Bank of China internally tested the outflow of "Central Bank digital currency": How far is it from us in the future?






