Opinion | The open source of hardware wallets does not represent a wallet upgrade, but a major security compromise
Source: Medium_Cobo official blog
Compilation: First Class (First.vip)
Editor's note: The original title was "View: Should Hardware Wallets Be Open Source? 》
As enthusiastic advocates of open source software, we have great respect for pioneer developers who share their work with the world. There is no doubt that we are in the cryptocurrency field and thank the founders of blockchain technology. It's because Satoshi Nakamoto and other great pioneers open-sourced their work that we were able to reap the benefits of amazing innovations such as Linux, Bitcoin, and the booming cryptocurrency market.
- Bakkt plans to launch a set of digital currency products in 2020, similar to Brent crude oil futures contracts
- Gospel for institutional investors, SEC approves first Bitcoin futures investment fund
- Li Lihui: China leads the way in the development of fiat digital currencies

But when it comes to whether making source code available is good for hardware wallet security, we enter a whole new discussion. This article explains why we believe that the nature of open source does not represent an upgrade of the hardware wallet, but a major security compromise.
Understand the benefits of open source
In traditional computing, open source proponents have been emphasizing the idea that open source is more secure because it enables the public to inspect source code and improve security by helping to fix potential vulnerabilities. Linus' law ("As long as there are enough eyes, all bugs are shallow"), statistics clearly show that zero-day attacks on closed-source Safari browsers take an average of 9 days to repair, while open source Zero-day attacks on the Firefox browser take an average of 1 day to fix.
However, Linus' law must be understood in a specific context, the traditional field of computers. When discussing the advantages of open source software in hardware wallets, we must keep in mind the fact that compared to hardware wallet development, the traditional computer development community is huge.
GitHub is the world's largest source code host, and it shows that the open source code of the largest hardware wallet brand, Trezor, has only about 180 contributors. This statistic is in stark contrast to the community of other hardware products such as Raspberry Pi (Raspberry Pi), which has about 9,500 open source firmware contributors.
No matter how big a project is, the potential dangers of exposing its code cannot be completely avoided. Take Linux Mint as an example. It was hacked in 2016. Although the backdoor issue was resolved in one day, its rapid response time was largely due to the size of the Linux open source community.
With our relatively small development community, we need to pay special attention to the fact that sharing source code is a double-edged sword. Unfortunately for hardware wallets, publishing source code makes it easier for hackers to detect vulnerabilities and launch attacks. Open source code can even open the door to cybercriminals and create fake hardware wallets that can deceive consumers-Trezor has become its victim.
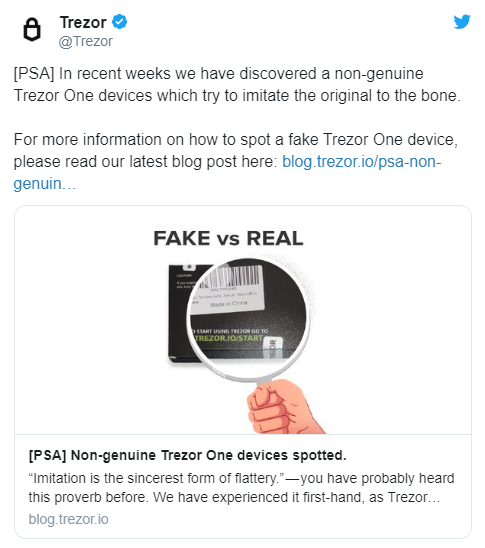
(First-class warehouse note: In 2018, Trezor's official tweet posted that "pirated" Trezor hardware devices appeared on the market, with a high degree of emulation, reminding users to carefully distinguish between true and false!)
Increased risk of zero-day attacks
One security issue that security hardware wallet owners need to be aware of is zero-day attacks. In a zero-day attack, the time period between the exposure or announcement of a previously unknown vulnerability and the repair of the vulnerability provides an excellent opportunity for hackers to attack. Because the vulnerabilities in hardware wallets are usually resolved through firmware upgrades, it usually takes a while, and users can really install and fix the problem after the official security patch is released. Some users do not open the hardware wallet for months or even years after setting it up, which greatly increases the risk of zero-day attacks. For those with experience in open source software development, it may seem counterintuitive that black boxes or devices with closed source code are more secure than white boxes with open source code.
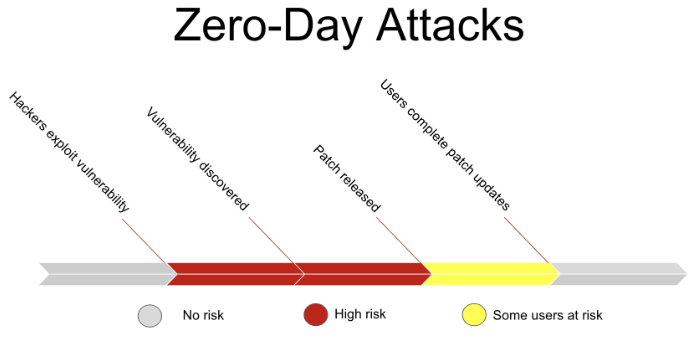
Hardware wallet users cannot be protected from zero-day attacks until the firmware is updated.
Psychological comfort or practical benefits?
Although it is easy to use Bitcoin as a major example of the security provided by open source code, it is reasonable to assume that all blockchain projects should follow suit and become open source code. Bitcoin's security from its open source development community is a direct result of its community-scale engagement. Regardless of source code or mining capabilities, the Bitcoin community is involved in the maintenance and protection of the project, involving many security functions. However, due to the relatively small number of developers currently involved in hardware wallet security, we cannot make any assumptions about the benefits of shared source code.
In addition to the large number of reviewers who check code, another benefit of open source code development in traditional computing is that anyone can download, install, burn, debug, and even delete certain aspects of the source code themselves.
The security provided by this degree of autonomy depends on the foundation of the particular technology. However, even with a solid technical foundation, security measures have the potential to be surpassed. Those working in the computer field should be familiar with how Ken Thompson Hack (KTH) creates backdoors in the C compiler, which can monitor or control any software program in the world. You must write your own compiler in binary code or use a tool that was compiled before installing KTH to overcome this security risk. KTH proves that any system compiled from source code is always vulnerable.
Professionals like Ken Thompson tell us that unless you are able to write your own compiler (only a few developers can do it), you will have to trust a third party. Other than having to compile their own compiler, most hardware wallet users don't even bother to burn or debug source code. For this type of users, knowing that their hardware wallets are open source is more of a psychological comfort than actually improving the security of their wallets significantly.
"Auditability" of QR code signature output
In the traditional field of computing, it helps to consider the security brought by open source software as a "censorship" of source code. Although this situation is not yet applicable to cold storage cryptocurrency security, what can replace hardware wallets as a reliable "audit" source?
Fortunately, signed transaction output is not as complicated as other types of software output. If providing source code is not the most secure option for auditing a hardware wallet, we may consider scrutinizing its transaction signature output.
People buy hardware wallets because they know that the most secure way to store private keys is to put them offline in cold storage. All hardware wallet services require a way to communicate between offline storage and online terminals. The cold end (offline storage) is responsible for storing the private key and signing the transaction, while the hot end (online terminal) needs to obtain data from the blockchain, build a signed transaction for the cold storage end, and broadcast the signed transaction to the blockchain
When transferring signature output, most cold storage hardware uses data cables, Bluetooth, or even NFC. Due to the opacity of their data transmission, these methods make the signature output extremely difficult to audit. One neglected method of cold storage hardware communication is the QR code, which is a "what you see is what you get" solution. We consider QR codes to be an ideal method for transferring data between the cold and hot ends, because the data output by QR codes is transparent. This makes it easy for users to ensure that every unsigned transaction transmitted to the cold storage device is valid, and that the signed output from the cold end does not leak private keys or sensitive information in any way.
in conclusion
We don't think open source is of much significance to enhancing the security of hardware wallets, but open source can enable users to see whether random numbers are generated by a TRNG or a pseudo-random number generator (PRNG).
Reprinted please retain copyright information.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Global debt, Ethereum, and the open financial system
- Focus on Hainan's blockchain boom: the talent dilemma behind the "gold rush"
- Bitcoin mining output halving effect hypothesis: every bitcoin that can be bought for every dollar will decrease in four years
- Long Baitao Recommended | Cash and Digital Currency in the Eyes of the Central Bank
- 340 million USD ETH collateral risks increase, MakerDAO may need urgent upgrade
- Ethereum upgrade travel map: a review of upgrade history and future planning
- Explore the Stratum V2 (Stratum V2), how to achieve the decentralization of Bitcoin mining?






