Articles about Search Results image - Section 658

- You may be interested
- The Bitcoin roller coaster started a ba...
- The central bank's digital currenc...
- The integration of blockchain and AI is...
- Deloitte uses zero-knowledge proof tech...
- Global assets seek anchor under the cri...
- Zhongan Technology Wu Xiaochuan: Blockc...
- A number of state-owned banks disclosed...
- Diar report: 2019 Q1 smart contract cre...
- Innovation workshop talks about blockch...
- Twitter Featured: Facebook Encryption P...
- Blockchain + Supply Chain Finance: Mark...
- Babbitt column | How is full homomorphi...
- Unraveling the Mysterious Hijacking of ...
- BTC computing power continues to rise, ...
- Anchor determines success or failure? ...
Ethereum price analysis on April 8
Key points After Ethereum formed support near $165, the upward momentum was good. Ethereum broke through the $175 and $180 resistance levels and formed…
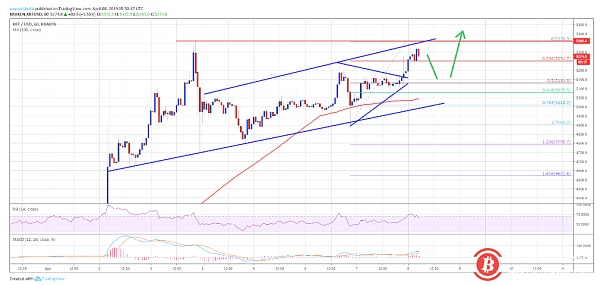
Bitcoin price analysis on April 8
Key points Bitcoin retested the support of $5,360 and is likely to rise further in the short term. On the hourly price chart, Bitcoin…
GTI Global Intensity Indicator: BTC may overbought after recent jumps, and price adjustment is a foregone conclusion?
The sudden rebound in prices has kept investors optimistic about a bearish market for more than a year. However, given that the Bitcoin GS…
The criminal's fingerprint can also be chained. Can the judicial alliance chain still tell you the truth?
Following the invoice chain, the judicial chain is about to enter the public life. On March 30th, the National Internet Information Office released the…
After the blockchain finance, the blockchain game is about to usher in the outbreak
Since the blockchain encryption market has taken the bear, the voice of rationally dealing with disruptive new technologies has dominated. Industry insiders have said…
Million yuan! Lightning network logo global collection order, I can get closer to Bitcoin!
In 2018, the blockchain market fell from the peak to the bottom, and the crazy investors continued to calm down. Entrepreneurs and investors became…
Learn more about IPFS (2/6): What is Interstellar Linked Data (IPLD)?
This article is a sequel to the "In-depth Understanding of IPFS" series (Part 2), which will help understand the basic concepts of IPFS. If…
The Samsung Galaxy S10 mobile phone is at risk of being hacked, and the security of the encrypted wallet is questioned.
According to Dailyhodl's April 7 report, Samsung's new Galaxy S10 phone is at risk of being hacked. Image source: visualhunt Since the Samsung Galaxy…
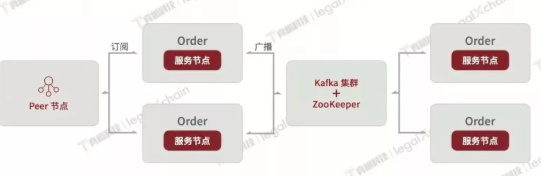
How does the enterprise blockchain + identity design design an identity model for the licensing chain?
Adopting license chain technology in the enterprise is a challenging road. Fundamentally, the so-called Web3 stack based on distributed ledgers is not mature for…
Science | What is Merkle Pollard?
In the field of cryptographic currency, the Merkel tree is a very efficient method for proving that a particular value exists in a large…
Find the right Blockchain Investment for you
Web 3.0 is coming, whether buy Coins, NFTs or just Coding, everyone can participate.