Articles about Search Results download - Section 68

- You may be interested
- The shackles of civilization: French cr...
- Market Analysis: Insufficient market ca...
- Smart Contract Series | Smart Contract ...
- The market temporarily stabilized and r...
- A road to smart hospitals: regulatory a...
- 5G+ blockchain, is it a gimmick, or is ...
- Blue Chip DeFi New Narrative Reviewing ...
- Babbitt original | Blockchain will deto...
- Global Blockchain Investment Statistics...
- Evening Read | Cosmos’ Threat to ...
- Libra Core releases roadmap # 2, define...
- 6 pictures tell you about the developme...
- Billionaire Michael Novogratz: The rece...
- LedgerX applies for a designated contra...
- Bitcoin’s market share reaches a ...
Parity CTO: Nearly half of the code specification for the initial phase of the Ethereum 2.0 upgrade
According to recent reports from foreign media, developers working on the next iteration of the Ethereum blockchain have developed some code designed to help…
The number of BTC nodes is even more than the number of active addresses of XRP.
Recently, an encrypted commentator observed that the number of Bitcoin nodes is even more than the active address of XRP, enough to highlight the…
Zhu Jiaming: The Digital Economy Fifty Years, From "Singularity" to "Big Bang"
This article is the third lecture of Mr. Zhu Jiaming in the third phase of the X-lab Open Class of Tsinghua University on April…
Storj: Amazon S3 Competitor | Babbitt Home Accelerator Technology Open Class Preview Interview
The Babbitt Accelerator Technology Open Course is a global online Geekhub Global Online program that includes in-depth dialogue and courses. We regularly invite experienced…
GitHub was attacked, hackers deleted hundreds of source libraries and asked for bitcoin
A large number of developers' Git source code libraries have been removed and asked to pay a ransom. The attack was first discovered on…
Security consultants anti-water hackers, an alternative legend for blockchain thieves
In Ethereum, guessing the private key is like guessing the lottery winning number, which is not statistically realistic. However, some users are clever and…
Security consultants turned into hackers, relying on swearing to steal $50 million in Ethereum, an alternative legend for blockchain thieves.
Source | WIRED Compilation | Guoxi Editor | Aholiab | Blockchain(blockchain_camp) In Ethereum, guessing the private key is like guessing the lottery winning number,…
The 100 trillion dollar road to encrypt the world
Foreword: Blockchain will store the wealth value of the world. This is a moving direction, but it is still too early, and the evolutionary…
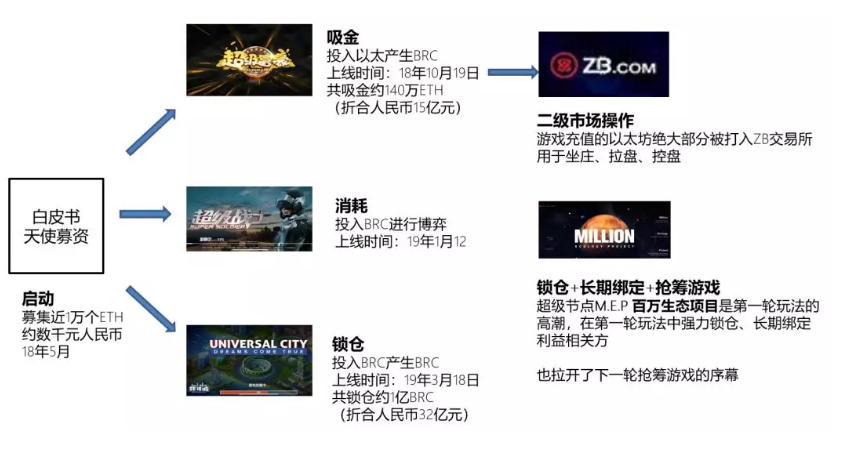
Half a year of gold 5.2 billion, the "black" of the Bell chain
The recent demon currency is the Bell chain. It has risen five times in just 10 days, with a market capitalization value of up…
Dry goods | Current main limitations of Lightning Network (Part-1)
introduction I launched a survey on Twitter and found that everyone seems to be interested in the limitations of the lightning network – what…
Find the right Blockchain Investment for you
Web 3.0 is coming, whether buy Coins, NFTs or just Coding, everyone can participate.