Articles about Search Results Click here - Section 76

- You may be interested
- Huobi Ventures’ latest research r...
- Where are the criminal risks of crypto ...
- Research Report | Libra, Central Bank D...
- Introducing the Bitcoin Script Project:...
- Don't know lightning network? Zer...
- Do the sender and receiver need to be o...
- With the use of a single scene, the sou...
- Ethereum 2.0 reward and punishment mech...
- One article reads DeFi's fifth Uni...
- ZeroLiquid: Zero-Collateral, Zero-Inter...
- Icebreaking tour of the planet
- Is your digital asset protected on the ...
- Monthly News | SEC Deterrence: October ...
- Interview with Li Lin | Year after retu...
- Chinese central bank paper: Innovating ...
Market Analysis: The callback in the bull market is a good opportunity to get on the train
Today's interpretation has created a triple benefit, the BSV hotspot has not yet retired, first Abbott Cong registered BTC white paper, followed by the…
Not just EOS, they also want to debut in June C.
The June that the EOS community is looking forward to is finally here! Since the BM in March, the telegraph group and Twitter have…
Block Chain Female Yang Xia: Provide military-grade security testing for blockchain code 丨 Ant blockchain competition Chengdu registration hot registration
Smart contracts allow for trusted transactions without third parties, which are traceable and irreversible. So what are the security issues in the smart contract…
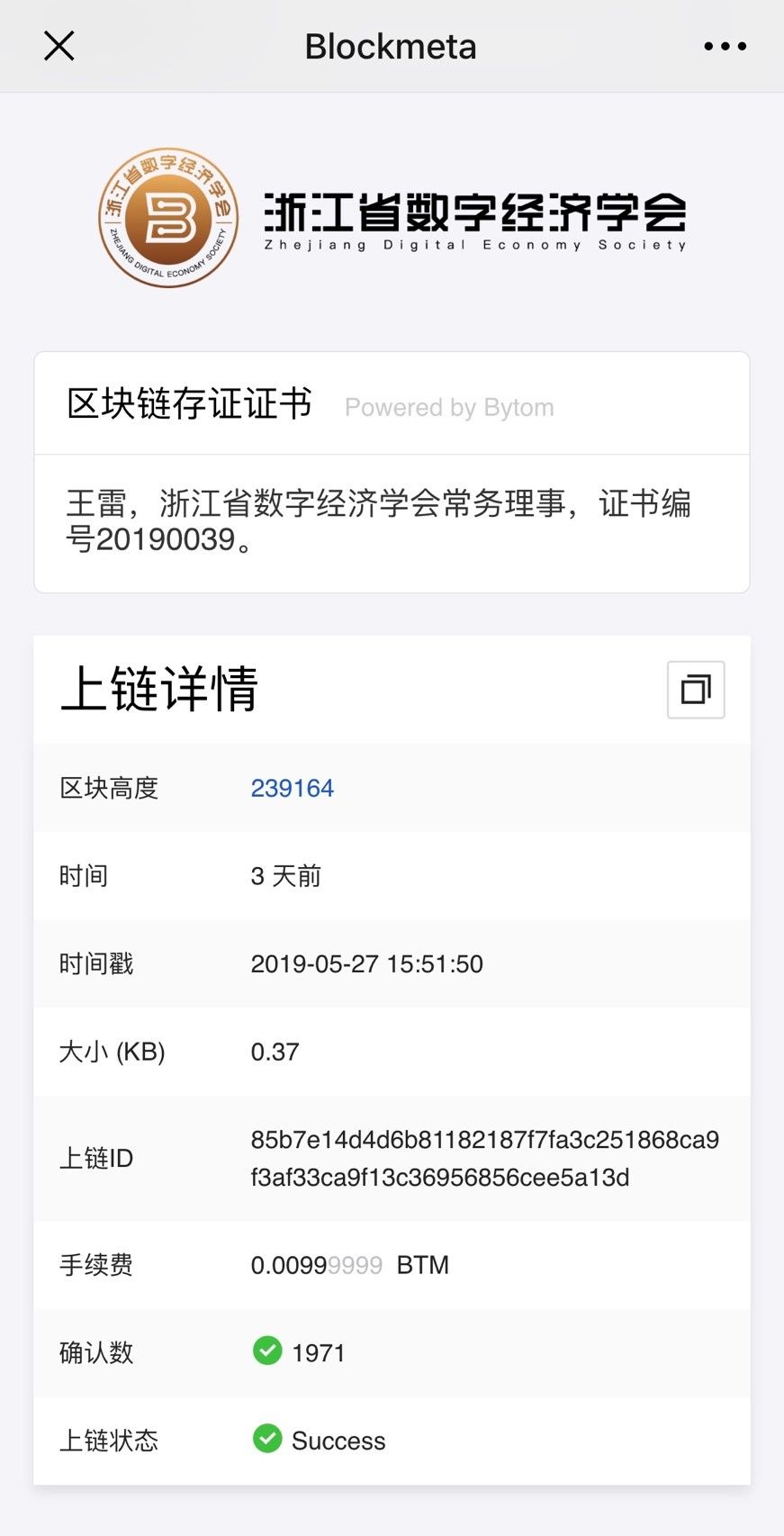
The first blockchain membership card issued in Hangzhou
The third national science and technology workers had just passed. On May 31, members of the Zhejiang Digital Economics Association received a unique "digital…
Magic Cube: If you create a decentralized entertainment ecosystem, everyone is the protagonist
Some people say that the post-90s is the first generation in China that has grown up in a peaceful era in the past 100…
Bystack Worldview (1): Three dimensions of assets
Teacher Xiao Feng defines assets as three states of existence: solid state, which represents the determination of assets and can be transferred as a…
The most stringent data security management methods in the history solicit opinions, PlatON cloud map to provide technical support
The National Internet Information Office and the relevant departments have researched and drafted the "Data Security Management Measures (Draft for Comment)" (hereinafter referred to…
Vote for new clothes, blockchain or subversion of traditional election mode
Blockchain has the characteristics of being non-tamperable, verifiable and transparent. Blockchain technology can be used to optimize and improve the efficiency of existing systems,…
Big households, small scattered food, how can hackers quietly slip your money?
On May 7th, the currency was hacked and more than 7,000 bitcoins were missing. The currency explained that the hacker used phishing, viruses and…
Blockchain Weekly | BSV and Ao Bencong's "Three Sins"
Guide Since the beginning of April 2019, BSV has experienced major events such as the demolition of the currency, the deep restructuring of the…
Find the right Blockchain Investment for you
Web 3.0 is coming, whether buy Coins, NFTs or just Coding, everyone can participate.