Puffer Finance Research Report LSD Track, a technology-driven seed player with dual staking and dual rewards.
Puffer Finance Research Report LSD Track, a tech-driven seed player with dual staking and rewards.Project Introduction
Puffer is an innovative technology-driven project that focuses on achieving low barriers, high returns, and decentralization in the field of cryptocurrency LSD tracks. As an emerging project, Puffer stands out with its unique technological advantages. Puffer is a liquidity staking protocol based on Eigenlayer, and its nodes also serve as active validation service (AVS) node operators on Eigenlayer.
Puffer’s staking mechanism allows participants to earn dual staking rewards, with a portion coming from the Ethereum network and another portion from the Eigenlayer network. At the same time, Puffer utilizes its self-developed Secure-Signer (remote signing tool) and RAV technology to address slashing issues in the Ethereum and Eigenlayer networks, providing participants with low-risk dual rewards.
Author
Elma Ruan, a senior research analyst at Shiliantou Investment Research, holds dual master’s degrees in marketing and finance from Ivy League schools. With 5 years of experience in WEB3, she specializes in DeFi, NFT, and other areas. Before entering the cryptocurrency industry, she worked as an investment manager at a large securities firm.
1. Research Focus
1.1 Core Investment Logic
Since Ethereum officially transitioned from Proof of Work (PoW) to Proof of Stake (PoS) in September 2022, more and more people have started to pay attention to its staking method. After the Shanghai upgrade, the Beacon Chain opened for withdrawals, and the ETH staking rate has increased significantly. Staking refers to locking a certain amount of Ether on the Ethereum network to gain the right to validate transactions and receive corresponding rewards. Currently, the requirement for an individual staking node on the POS Ethereum network is 32 ETH. As a result, many ETHs are being staked on centralized exchanges, large mining pools, and leading LSD protocols like Lido. According to Dune data, Lido’s ETH staking rate has reached 23.01%, significantly surpassing the initial staking cap threshold of 15% proposed by Vitalik, indicating a certain market monopolistic tendency. Obviously, due to the technical and economic barriers of staking, the validation nodes in the network are becoming more concentrated, affecting the decentralization and security of the network. Puffer is a new staking solution aimed at increasing the decentralization and security of the Ethereum network. At the same time, Puffer deepens its integration with EigenLayer to increase yield and maintain staking incentives. Puffer is an early-stage project but has already received support from some well-known investors, including the founder of Eigenlayer, the head of Coinbase’s staking business, and Ethereum core researcher Justin, among others. In addition, the Ethereum Foundation has also funded Puffer’s Secure-Signer technology to reduce slashing risks and maximize the number of independent operators, thus achieving network decentralization.
- The security model of Bitcoin withstands the test of halving block rewards; both the market and technology prove that defending against 51% attacks does not require breaking the upper limit of 21 million.
- Inspiration from the (3,3) and ve(3,3) flywheel models How to create a Ponzi scheme on friend.tech?
- Revolutionary Progress of Zero-Knowledge Proof Technology In-depth Exploration of the Nova Algorithm
Puffer is an advanced staking solution for an earlier project aimed at increasing the decentralization and security of the Ethereum network. It adopts a series of technical means, including anti-slashing technology, re-staking services, and remote signing, to minimize slashing incidents and highlight the advantages of individual stakers. In simple terms, participating in Puffer’s staking allows for dual rewards from ETH and Eigenlayer, and then solves the slashing issue in the Ethereum and Eigenlayer networks through the original Secure-Signer and RAV technology, providing stakers with the lowest-risk dual rewards. Through Puffer’s innovative mechanism, participants can achieve lower risk with less capital and enjoy stable returns from both networks. This solution maximizes the returns for stakers.
The core logic of Puffer is to improve the security and yield of staking through technical means, thereby attracting more individual nodes to participate in staking. Puffer Finance is built on the Eigenlayer protocol. As a node of Puffer, it serves as both an Ethereum validation node and a native node on Eigenlayer, running AVS (Validation Node Service). The first cooperative AVS of Puffer is EigenDA. Therefore, this node can obtain rewards from Ethereum and re-staking rewards from Eigenlayer, and as a node on Eigenlayer, there is no need to increase additional collateral. The security and anti-seizure issues of the node’s private key are supported by Secure-signer, RAV software, and TEE hardware, similar to a cold wallet for private keys. The hardware efficiency improvement is because the node’s hardware provides dual verification services, namely Ethereum PoS and Eigenlayer AVS, thereby improving efficiency. Both Ethereum and Eigenlayer have penalty mechanisms, with Eigenlayer having programmable penalties, and Secure-signer can effectively reduce this penalty risk. Puffer nodes perform dual verification and, with the help of Secure-signer technology, effectively reduce the risk of LSD and LSDFI assets. Compared to existing LSD tokens and liquidity staking tokens, this method is safer and more reliable.
In simple terms, first, Puffer adopts anti-Slashing technology, which means that during the staking process, the staked Ether is stored in multiple addresses to reduce the risk of being attacked. At the same time, Puffer also adopts re-staking mechanism, which means that the staked Ether is staked again to other validation nodes to increase yield and reduce risk. Secondly, Puffer also uses remote signing technology, which means that the signing process is transferred from the local node to a remote node to increase security and reduce risk.
In addition, as a technology-driven emerging project, the significance of Puffer lies in innovatively solving some core issues in Ethereum staking. In terms of the staking threshold issue, Puffer attracts more people to participate by reducing the amount of ETH required for staking. In addition, simplifying operations is also a key challenge for Puffer. In the Ethereum network, the construction and proposal of blocks are carried out by randomly selecting validators, and a validator committee is needed to prove the validity of these blocks. In order to avoid duplicate signatures and prevent seizures, ordinary stakers need to spend a lot of time and effort, which is not easy to achieve in reality. To solve this problem, Puffer lowers the staking threshold and provides tools to automatically prevent seizures, making it more convenient for ordinary users to set up validation nodes. In addition, the Ethereum Foundation attaches great importance to and funds the development of such technologies. Among them, Secure_Signer technology is one solution, which executes the final signing operation in a secure and isolated environment, minimizing the risk of seizure. Therefore, Secure_Signer technology is effective in solving the issue of seizure caused by poor key management.
Since the explosion of the LSD track, numerous projects have emerged, all focusing on three main directions of development: lowering the threshold, increasing yield, and enhancing decentralization. Lowering the threshold and increasing yield are key factors that users can directly perceive and benefit from, so these projects are striving to increase yield, even surpassing Ethereum’s benchmark APR (increasing yield). Puffer is currently in complete alignment with the current goals of the LSD track. In addition to lowering the staking threshold, Puffer also increases the number of independent operators as much as possible through the secure signing technology funded by the Ethereum Foundation, further enhancing the decentralization of the network. At the same time, Puffer achieves re-staking and MEV-Smoothing by reducing protocol fees and deep integration with Eigenlayer, thereby increasing yield. These improvements are aimed at providing a better user experience and higher system security while attracting more individual nodes to participate in staking. Because only when the network is sufficiently decentralized and secure, can it attract more users and applications, thereby achieving the sustainable development and maximization of value of the Ethereum network.
In summary, Puffer is an emerging staking solution aimed at improving the decentralization and security of the Ethereum network. The emergence of Puffer is of great significance to the Ethereum network as it helps achieve a higher level of decentralization and network security, laying a solid foundation for the long-term development of the network. However, Puffer also faces challenges and risks such as the complexity of technical implementation and intense market competition. Nevertheless, as the Ethereum network continues to grow and develop, Puffer is expected to become an important staking solution contributing to the long-term development of the network.
Currently, the Puffer testnet has not yet been launched, so it is unclear whether it can become a dark horse in the LSD track, break Lido’s monopoly position after all the technology is implemented, and further enhance the decentralization of Ethereum. Finally, it is worth noting that Puffer is an early-stage project, and investors should pay attention to the implementation of the project’s technology and its operation after launch before making investment decisions. Currently, Puffer can be regarded as a mid-term observation project, and its development progress should be closely monitored.
1.2 Valuation
Due to the fact that the testnet of this project has not yet been launched and the valuation of the seed round of financing has not been made public, it is not possible to make an accurate valuation.
2. Project Overview
2.1 Project Scope
The business scope of Puffer.fi is to provide a trust-minimized liquidity staking protocol, optimize staker reward mechanisms, and improve the accessibility of liquidity staking by reducing margin requirements and using an anti-confiscation environment. These measures aim to promote the decentralization of the Ethereum network and provide a more competitive liquidity solution. Through these measures, Puffer.fi makes household staking a viable option.
2.2 Past Development and Roadmap
Date Event
2022-12-24 Developing a liquidity staking protocol that uses SGX technology as a practical hedge against zk-rollup SNARK vulnerabilities.
2023-03-23 Both founders of Puffer co-authored an article proposing a permissionless liquidity staking protocol that allows the staking requirement to be lowered to below 16 ETH without the need for internal modifications or additional trust conditions.
2023-05-04 Building a trust-minimized and permissionless liquidity staking protocol and exploring integration with Secure-Signer technology.
2023-05-06 The first public product, Secure-Signer, has officially received funding support from the Ethereum Foundation; expanding anti-confiscation technology to implement ZK-2FA (multi-proof system).
2023-05-10 Taking a step towards trustless liquidity staking tokens; developing a highly capital-efficient and fully permissionless liquidity staking protocol (LSP).
2023-05-18 Secure-Signer was released as a public product, encouraging the community to fork and develop their own versions. Secure-Signer is supported by Intel SGX.
2023-08-30 Release update documentation about Puffer.fi.
Future Roadmap:
Puffer is currently in the early stages of development, with plans to release Puffer on the testnet in the second half of 2023 and launch the mainnet in 2024. Additionally, the project’s official website and Discord community mention that Puffer Fi is planning to optimize the LSD protocol with technologies such as pDVT and privacy-focused ZK-2FA.
2.3 Team Information
2.3.1 Overall Situation
According to LinkedIn, the team consists of five core members with expertise in Python, C language, Java, SolidWorks, JavaScript, blockchain, and other fields. Their professional backgrounds include computer science, electrical engineering, marketing, etc. The team members have extensive knowledge and skills to provide comprehensive support and solutions for the company. It is reported that the team is currently hiring technical personnel with years of experience in Solidity smart contract development.
2.3.2 Founders

Amir Forouzani Co-Founder & CEO
Amir Forouzani is the co-founder and CEO of Puffer. He graduated from the University of Southern California with a background in data science and NASA. He holds a master’s degree in electrical and electronic engineering from the University of Southern California and has served as a research assistant.

Jason Vranek Co-Founder & CTO
Jason Vranek holds a master’s degree in computer science and engineering and has experience in market design and blockchain front-running transactions. He uses Chisel to build hardware accelerators and is interested in areas such as teaching and automated theorem provers, deep reinforcement learning, etc. He is currently pursuing a Ph.D. in the field of verifiable computation.
2.3.3 Core Members

Christina Chen Marketing Operations
Christina is a professional with years of experience in marketing, public relations, brand promotion, and business development in the Silicon Valley tech industry. She has rich experience in the Web3 and blockchain fields. Christina specializes in DeFi, NFT, metaverse, P2E, DAO, and DAO funds, among other areas.

Jeff Zhao Developer and Software Engineer
He holds a Bachelor’s degree in Computer Science from the University of Toronto in Canada, and has worked as a full-time software engineer at companies such as Puffer, Alder Labs, Alice, and Circle, participating in projects such as cryptocurrency exchange products, smart contracts, and L2 MATIC integration. He also developed and maintained Java Virtual Machine during his internship at IBM.
2.4 Financing Situation
1) Initial Financing:
A. The initial funding for team expansion was obtained through Pre-Seed financing led by Jump Crypto, with a financing amount of $650,000.
B. The Ethereum Foundation provided a total of $138,000 in funding for the development launch of the Secure-Signer technology.
2) Seed Financing:
Raised $5.5 million, led by Lemniscap and Lightspeed Faction, with other participants including Brevan Howard Digital, Bankless Ventures, Animoca Ventures, DACM, as well as community funds such as 33DAO, WAGMI33, and others. In addition, support was also received from institutions and individuals such as Eigenlayer, Curve, Coinbase Instituteal, Canonical Ventures, and Obol Labs.

3. Business Analysis
3.1 Service Objects
The service objects of this project mainly include the following categories:
1) Individual users: Individual users can use the liquidity staking protocol provided by this project to stake their tokens in the staking pool to receive corresponding rewards. By participating in staking, users can increase the liquidity of the Ethereum network and earn profits from it.
2) Validators: This project targets individual users who want to become Ethereum validators. Validators can lower the staking threshold and stake their tokens in the staking pool by using the services provided by Puffer.fi. In this way, they can participate in the validation process of the Ethereum network and receive corresponding rewards.
3.2 Business Categories
1) Staking service: This project provides a staking pool (Puffer pool) that allows users to stake their tokens in it and participate in the validation process of Ethereum.
2) Technological innovation: This project adopts some unique technologies and strategies, such as reducing margin requirements and providing re-staking services, to improve the capital efficiency and economic potential of nodes, and provide better hardware efficiency and risk management measures.
3) Decentralization promotion: By increasing the feasibility and participation of home validators, this project is committed to promoting the decentralization of Ethereum, increasing the number and distribution of nodes, thereby improving the security and stability of the entire network.
In summary, the business categories of this project can include staking services, technological innovation, and decentralization promotion.
3.3 Business Details
1. Puffer Protocol
Puffer Protocol is built on top of Eigenlayer, and its rules can be referred to as Active Verification Service (AVS) or middleware. AVS is a service or middleware that validators choose to join and can programmatically penalize validators’ 32 ETH deposits. For example, if fraudulent behavior occurs during the re-staking process of Optimistic Rollup, validators’ 32 ETH deposits can be programmatically confiscated. If a validator violates the AVS rules of the Puffer Protocol, their ETH will be confiscated programmatically and returned to the pool.
1) In order to protect Puffers’ ETH from inactive penalties, the current balance of each validator must be maintained above the threshold set by Puffer DAO. The minimum threshold should be low enough to allow reasonable downtime, and the maximum value should be high enough to incentivize good performance. In other words, the threshold should be a compromise that can incentivize validators to stay active and give them a certain flexibility to adapt to possible downtime situations.
2) MEV-Smoothing is crucial for curbing centralization within the protocol. It allows individual nodes distributed at home to earn more income than independent operations and reduces the scale economy of centralized staking operations. Block proposers need to share execution rewards with the pool. If theft is proven on-chain, violating validators will be punished.
Puffers
Puffers refer to individuals who stake ETH on the Puffer Protocol to obtain pufETH tokens. When the ETH staked by Puffers reaches 0.01 or more, it will be added to an ETH fund pool. Part of this pool will be provided to nodes to meet the 32 ETH requirement for activating Ethereum validators, while the remaining part will be used to provide liquidity to Puffers when they want to redeem their pufETH tokens for ETH.
Nodes
In the Puffer Protocol, protecting the staked ETH is one of the primary concerns of the protocol, which is crucial for maintaining protocol stability. To achieve this goal, the protocol requires all nodes to have economic bonding to provide appropriate incentives. In the event of any misconduct, the corresponding penalty will first be deducted from the node’s economic bonding. To minimize the potential risk of penalties, Puffer Protocol adopts strategies supported by stealth zones and Guardianship to reduce the likelihood of node penalties and effectively deal with node inactivity. In this way, the protocol can provide a safer and more stable environment, protecting users’ staked assets from potential risks.
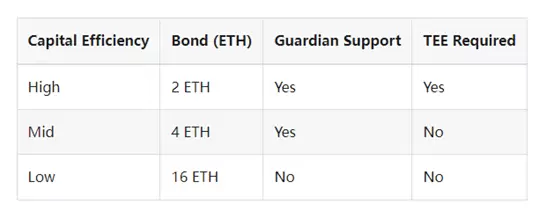
To accommodate different risk preferences and ETH requirements, nodes can choose from three different operating modes. These operating modes correspond to different capital efficiency and corresponding requirements. Nodes with Secure-Signers have higher capital efficiency and can access a set of validation nodes specific to stealth zones. Currently, for nodes with less than 16 ETH in collateral, Guardian support is required to prevent them from being penalized until EIP-7002 removes this requirement. Before that, nodes with 16 ETH bonding can join without Guardian support.
- Rewards
pufETH is a cToken reward token similar to Compound, with good compatibility in the DeFi field. As the protocol generates rewards, the amount of ETH supported by pufETH increases, thereby improving the exchange rate between the two. This allows holders of liquid pufETH to gradually receive rewards for staking and restaking while still participating in DeFi activities.
- Puffer Rewards
Puffers deposit ETH into the PufferPool contract to mint pufETH. At the beginning of the protocol, the exchange rate is one-to-one. However, if the protocol performs well and the accumulated rewards exceed the penalties, the exchange rate will make the value of pufETH higher than ETH. Therefore, Puffers holding pufETH can expect its value to increase over time.
- Node Rewards
After registering as a validator, Puffer nodes will mint pufETH equivalent to their collateral and lock it until they exit the protocol. Due to the rewards for node consensus, execution, and restaking, they will receive liquid ETH rewards based on the commission rate set by Puffer DAO, with the remaining portion sent to the PufferPool and the financial coordination account. Since nodes hold locked pufETH, they will also share rewards generated by other nodes in the protocol. This helps achieve efficient MEV and maintain consistency in node incentive mechanisms.
- Slashing Mechanism
The consensus mechanism is a set of rules that support the operation of a given blockchain. It determines how the blockchain operates, manages the operational rules of the blockchain, the way users interact with it, and how to prevent manipulation of the network, which could have catastrophic consequences for the entire blockchain. Typically, this can be achieved by ensuring that network nodes have a “stake”. This means that in order to achieve the best results at an individual level, network nodes must also align with the interests of the network to maintain their incentive consistency. Slashing is a part of the proof-of-stake consensus mechanism used to punish validators with malicious intent. In many proof-of-stake networks, validator nodes must “enter” by initially locking a certain amount of tokens on the blockchain, which is called staking. Simply put, by making personal investments on the blockchain, the consensus mechanism of the blockchain can prevent malicious or inefficient behavior through punishment, which is slashing.
Overall, slashing often punishes the following key behaviors:
1. Downtime
Downtime refers to validator nodes being offline at any given time period and therefore unable to participate in the network’s consensus process. This unreliability is harmful to the normal operation of the network and is typically deemed punishable behavior.
2. Double-Signing
In order to avoid downtime, many validator nodes have established backup devices. However, this also brings its own slashing risk: if the network detects the same validator key running on two different servers, it may consider this as a risk (because this behavior is not expected and may even cause conflicts in the information provided by the nodes). Therefore, this is also a behavior that may be subject to slashing penalties.
3. Manipulating the Network
Finally, any behavior that attempts to manipulate the consensus process, such as signing two different blocks for the same slot, will also face
The slashing mechanism is designed to ensure that validators in the proof-of-stake protocol not only need to actively participate in the consensus, but also actively avoid any behavior that is detrimental to or delays the network consensus process.
- Guardians
Guardians are a group of licensed nodes whose task is to ensure the smooth operation of the protocol. They currently have two responsibilities, but they will gradually be replaced by EIP-4788 and EIP-7002 in future hard forks:
1. Reporting the amount of ETH supporting pufETH: In order to calculate the conversion ratio between ETH and pufETH, the main contract needs to explicitly state the current amount of ETH supporting the protocol. This involves adding up the balances of all active validators on the chain with the balances on the beacon chain. Currently, Guardians are responsible for performing this calculation, but after EIP-4788, it will be replaced by a trustless zero-knowledge proof instead of Guardians’ calculation.
2. Exiting nodes that violate the Puffer Protocol AVS: The first rule of the Puffer Protocol AVS is designed to protect offline nodes from harm. However, since EIP-7002 has not been implemented yet, validators cannot complete the exit operation on the chain and need to sign an exit message with their validator key. In order to maintain decentralization before the implementation of EIP-7002, the Puffer Protocol requires nodes with a deposit less than 16 ETH to encrypt their validator key shards into the secure execution environment of the Guardians. These secure execution environments are designed to only be able to sign exit messages with the validator key shards. After the implementation of EIP-7002, the role of Guardians will no longer be needed.
To reduce counterparty risk, Guardians have taken many preventive measures. Guardians are composed of public community members who have a high degree of consensus on Ethereum’s ideas and reputation. Guardians must use secure execution environments to increase the security of their actions, and require a high proportion of Guardians (e.g., 8/9 signatures) to agree to perform certain operations.
- Withdrawals
Puffer Withdrawals
Puffer provides a withdrawal feature, where Puffer holders can destroy their pufETH to redeem the original ETH and accumulated rewards when there is sufficient liquidity in the withdrawal pool of the protocol. In order to ensure withdrawal liquidity, a portion of all Puffer deposits, rewards, and node withdrawals will be added to the withdrawal pool.
- Node Withdrawals
After participating in the Puffer protocol, nodes can fully exit by proving that they have exited the beacon chain. After fully exiting the Puffer protocol, the locked pufETH of the nodes will be destroyed, and they will be redeemed with liquid ETH equal to their original deposit plus accumulated rewards minus penalty amount. For example, if a node with a 2 ETH deposit exits, and its validator balance is 32 ETH, if the pufETH:ETH ratio doubles since registration, the validator will receive 4 ETH, while 28 ETH will be returned to the withdrawal pool.
- Governance
Puffer is committed to establishing an unobstructed decentralized protocol that can continue to grow and operate without relying on the Puffer core team. To achieve this goal, Puffer strives to minimize the governance role in the protocol. The PUFI token is primarily used for the following purposes: pausing and upgrading contracts to address vulnerabilities and Ethereum hard forks, voting to determine protocol parameters such as commission rates, managing the Puffer protocol’s financial fund, including grants and AVS whitelist that comply with the Ethereum concept.
- Restaking Service
Puffer is built on Eigenlayer, and all Puffer nodes can become local restakers to increase their rewards. Restaking work covers a wide range of important middleware, such as bridges and oracles, as well as services such as data availability layers and L2 sequencers. In addition, nodes that support secure execution environments can also participate in Puffer’s unique AVS activities, such as privacy-protected L2 and ZK-2FA. Puffer is committed to supporting AVS that have no adverse impact on Ethereum.
Distributed Validator Technology (DVT) in Puffer
The Puffer protocol is compatible with DVT. When used in conjunction with the Secure-Signer component, this combination provides optimal decentralized validation protection. At the same time, Puffer introduces an extension mechanism called DVT fractalization, which can only be achieved in a secure execution environment. Through DVT fractalization, the scale of the DVT cluster can be expanded beyond the standard DVT range, enabling larger-scale decentralized operations and reducing collateral requirements. This extension capability allows the Puffer protocol to flexibly adapt to different scale validation needs while maintaining high security and reliability, providing users with a better user experience.
- Burst Threshold
The burst threshold is set to ensure that the size of the Puffer pool remains within a reasonable range to maintain the decentralization of Ethereum. The threshold is set at 22% of the maximum capacity. Once the Puffer pool reaches 22% of the validator set, the minting of pufETH and the joining of nodes will be paused. It ensures that the Puffer pool never exceeds the dangerous consensus threshold of 33%, thereby protecting the stability of Ethereum.
2. Secure-Signer
• Definition and principle
Secure-Signer is a remote signing tool funded by the Ethereum Foundation to prevent Slashing attacks using Intel SGX.
Secure-Signer is a remote signing tool launched by Puffer. It utilizes the technology of trusted execution environment (TEE), currently implemented in the form of Intel SGX enclave. To reduce single points of failure, Puffer plans to implement Secure-Signer on devices from different vendors, including AMD’s SEV TEE and future new hardware.
Using TEE can provide guarantees for confidentiality and integrity. In the SGX environment, an enclave is a protected memory area used to store code and data. This ensures that the code is not tampered with during execution and protects the encryption and security of the data. The characteristics of the physical hardware also ensure that these properties are maintained. By combining these technologies, Secure-Signer can provide secure and reliable remote signing functionality.
• Operation Process
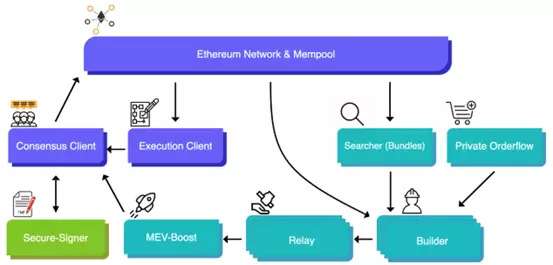
Secure-Signer is a remote signing tool that can manage validator keys on behalf of consensus clients. It can run locally on the consensus client or on a remote server. From the perspective of node operators, there is almost no difference in setting up their validators. If they have hardware that supports SGX, they can install and run Secure-Signer and instruct their chosen consensus client to use Secure-Signer as a remote signer.
How to Prevent Slashing
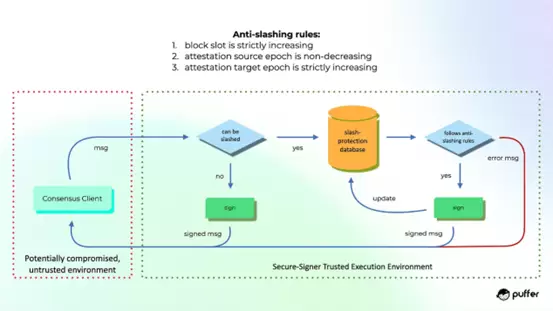
To prevent potential double-signing attacks, Secure-Signer generates and protects all BLS validator keys in its encrypted and tamper-proof memory. These keys can only be accessed at runtime and remain encrypted in a static state unless used to sign unslashable block proposals or proofs.
This binding and encryption method ensures that keys are not used across multiple consensus clients, protecting nodes from accidental slashing due to double-signing. Additionally, even if the system is compromised, these keys remain effectively protected.
In addition to protecting validator keys, Secure-Signer maintains an integrity-protected database that follows EIP-3076, storing previously signed contents. Through this database, Secure-Signer prevents double-signing attacks. When a consensus client passes a block or proof to Secure-Signer, the signatures of all validator keys need to meet specific requirements and assertions.
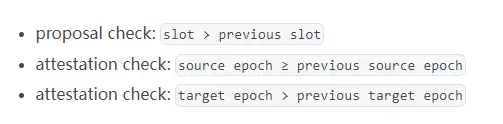
By eliminating the risk of slashing caused by accidents or consensus client errors, Secure-Signer significantly reduces the risk for nodes and allows Puffer Pool to safely lower the staking requirements. This not only ensures that nodes can continue to operate even if the operating system is compromised but also protects nodes from catastrophic consensus client errors. This is because Secure-Signer runs in a separate environment and maintains its integrity-protected slash protection database.
Significance
Secure-Signer is a public good that reduces the risk of individual validators losing funds due to slashing by protecting validators using a trusted execution environment (TEE). Compared to distributed validator technology (DVT), Secure-Signer offers a more cost-effective option to enhance validators’ ability to withstand slashing. Secure-Signer and DVT are complementary technologies, and using Secure-Signer can protect its security when the keys are at rest and provide stronger slashing protection at runtime, similar to the security of a cold wallet.
By protecting validators with TEE, Secure-Signer ensures the security of individual validator keys and reduces the risk of highly correlated slashing events for the entire set of validators. Therefore, Secure-Signer provides a secure and reliable way for the entire set of validators to benefit from it.
3. RAVe (Remote Attestation Verification)
RAVe is the second component of Puffer’s Ethereum fund, granted by the Ethereum Foundation. It stands for Remote Attestation Verification. This important smart contract collection allows secure interaction between the protected environment and the blockchain, and helps Puffer Pool achieve permissionless features. Through RAVe, new application scenarios that were previously impossible can be realized.
Remote Attestation
Remote Attestation is a process that allows an untrusted party to prove that it is running a specific SGX (Software Guard Extensions) isolated execution environment. The SGX isolated execution environment only allows the execution of its initialized code, so remote attestation enables one to prove to others that only specific programs can be run. In communication applications (such as Signal) that use SGX, remote attestation allows these applications to prove to user devices that they are running privacy-protecting software.
The goal of RAVe (Remote Attestation Verification) is to enable anyone to prove to a smart contract that they are running an isolated execution environment. This is highly useful in the blockchain environment, as it can provide highly trusted off-chain confidential computing. RAVe allows smart contracts to verify the running environment of participants, ensuring that they meet specific security requirements, thereby enhancing the protection mechanisms and computational privacy of the blockchain system.
RAVe v1
RAVe v1 uses remote attestation verification based on Enhanced Privacy ID (EPID) and interacts with Intel Attestation Service (IAS). At a high level, the isolated execution environment can submit 64 bytes of user data, including it in its remote attestation report. The report also includes security-relevant information about the device, as well as the MRENCLAVE and MRSIGNER fields. MRENCLAVE is the measurement of the isolated execution environment, uniquely identifying the program to be run, while MRSIGNER identifies the entity that built the isolated execution environment.
After a successful remote attestation verification, IAS returns the remote attestation evidence to the attested SGX device. The remote attestation evidence includes the remote attestation report, the remote attestation report signed by IAS, the IAS root CA certificate, and the x.509 signing certificate used to sign the report. The RAVe smart contract verifies the origin of these reports, the validity of various report fields, and then extracts the 64-byte payload.
RAVe in Puffer Pool
RAVe in Puffer Pool is a way to verify if a node is running Secure-Signer. The RAVe smart contract verifies the remote attestation evidence to allow nodes to enter the pool. When generating a validator key, the Secure-Signer isolated execution environment commits its validator public key in the USERDATA field of the remote attestation report. RAVe verifies the remote attestation evidence of the node, extracts its validator public key, and registers it on the blockchain. This way, the node can prove to the pool that they are running the Secure-Signer isolated execution environment and generate a new validator key within it. Anyone can verify the fact that the Secure-Signer program never leaks the key by inspecting the source code.
RAVe in Restaking
In re-staking, zero-knowledge proofs (ZKP) can be used to prove the correct execution of a program. However, isolated execution environments can prevent users from running anything other than the correct execution of the program. This is particularly attractive for middleware on Eigenlayer, especially considering that isolated execution environments have lower overhead compared to ZKP. By using isolated execution environments and RAVe, the problem of “potential re-staking” can be solved.
3.4 Industry Space and Potential
3.4.1 Background and Classification
The Liquid Staking (LSD) track refers to the mechanism of staking PoS tokens into a staking pool and simultaneously receiving liquidity proof assets representing these staked tokens. On Ethereum, the “three narratives” formed around liquidity staking have gradually formed a complete ecosystem.
The first narrative is the LS protocol and LSD. They provide liquidity staking services and create liquidity and returns for staked assets through LSD. Currently, mainstream protocols include Lido’s stETH/wstETH, Frax’s sfrxETH, Rocket’s rETH, Swell’s swETH, etc.
The second narrative is the LSD use case LSDFi. LSD is a strong consensus-bearing asset with programmability, composability, and free liquidity. It can be applied to various DeFi scenarios, meeting investors’ different needs for capital liquidity, capital efficiency, yield strategies, and risk management, forming various forms of LSDFi businesses. For example, in Pendle, depositing stETH can earn PT (principal tokens) and YT (yield tokens), providing different yield and risk strategies.
The third narrative is decentralized solutions. There are currently two mainstream decentralized solutions in the decentralized space to ensure the security and decentralization of blockchain networks. One is DVT technology, with related implementation protocols such as SSV.Network, Obol Labs, etc. The other is Re-staking, such as EigenLayer. These solutions mainly address the “centralization” trend and risks brought about by the rapid development of liquidity staking protocols.
The development of the LSD track has formed a preliminary pattern. In terms of hierarchy, DVT technology service providers such as SSV Network, Obol Labs, etc., can be considered L0. Lido, Ankr, Coinbase, and other Liquid Staking Token (LST) issuers can be considered L1. These L1 projects allow users to earn POS rewards through a commission model and occupy the majority of the market share, with Lido accounting for 74.45% of the liquidity staking share. In addition, there are other LST issuers in the liquidity staking market, but their market share is relatively small.
Furthermore, Ethereum’s PoS mechanism requires 32 ETH to become a validator, which increases the threshold for participation compared to the previous PoW mechanism and reduces the possibility of a centralized entity acquiring more than two-thirds of the validator set. At the same time, this also helps reduce Ethereum’s energy footprint.
The PoS mechanism incentivizes validators to participate through consensus and execution rewards, and implements penalties to ensure that validators perform their tasks honestly and diligently. These mechanisms will also be important factors in the development of the LSD track in the field of liquidity staking.
In addition, updates and upgrades to the Ethereum PoS mechanism, such as the Shanghai/Capella update, will further enhance the liquidity of validators and improve user experience. Validators can now fully withdraw their ETH when needed, and consensus rewards exceeding 32 ETH will no longer be paid all at once, but will be paid in batches to the execution layer address approximately every week. This will increase liquidity and make liquidity staking more flexible and efficient.
Based on the given classification, the Ethereum LSD track can be divided into the following categories, with detailed explanations for each category:
1) Liquid Staking: This category refers to the use of liquid proof-of-stake tokens issued by staked tokens for trading and providing liquidity after Ethereum tokens are staked. The main advantage of liquid staking is that it allows stakers to enjoy the liquidity of their funds while staking, enabling them to make other investments or engage in trading.
2) Unidentified: This category refers to stakers who have not been clearly defined or classified. This may be due to a lack of data or the inability to determine to which specific category they belong.
3) Centralized Exchanges (CEX): This category refers to users who stake on centralized exchanges. These exchanges typically provide staking services, allowing users to stake their Ethereum tokens in the exchange’s wallet without having to manage the staking process themselves.
4) Staking Pools: This category refers to staking pools in which multiple stakers participate together. Stakers deposit their Ethereum tokens into the staking pool to pool resources and increase their chances of receiving staking rewards.
5) Independent Stakers: This category refers to individuals or entities who choose to stake independently. Independent stakers manage and operate their staked tokens on their own and directly participate in the Ethereum network’s consensus process.
6) Others: This category refers to stakers who cannot be classified into the above categories, possibly due to special circumstances or uncommon staking methods.
3.4.2 Market Size
- Overall Situation
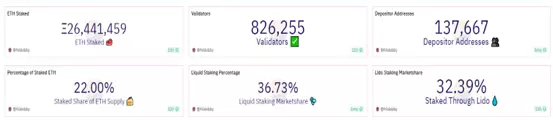
According to current data, the staked amount of Ethereum in the entire blockchain market has reached approximately 26.44 million ETH, accounting for 22% of the total supply. These staked Ethereum tokens are distributed among 826,000 stakers and 137,600 staking addresses. In the current market dominated by liquidity staking, the market share of liquidity staking is 36.73%, with staking through Lido accounting for 32.39% of the market share. Therefore, it can be seen that Lido is the leader in the current LSD track.
- Specific Data
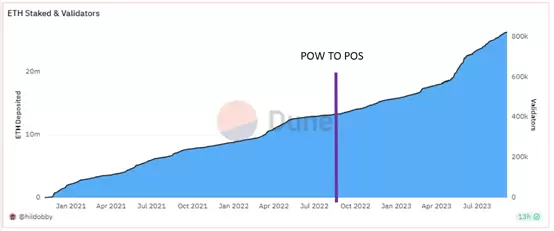
From the chart of Ethereum’s staking and validators, it can be observed that the amount of staking on Ethereum has continued to increase after Ethereum transitioned to a Proof of Stake consensus mechanism in October 2022. Especially starting from April 2023, possibly influenced by the Shanghai upgrade on Ethereum, the amount of staking has shown a sharp upward trend. As of now, the amount of staking has increased from about 400K ETH in August 2022 to about 800K ETH, approximately doubling. This indicates that Ethereum’s Proof of Stake mechanism is attracting more users to participate in staking, and the network security and decentralization of Ethereum are gradually improving.
According to data from DefiLlama as of September 7, 2023, the Total Value Locked (TVL) of Liquid Staking has reached $20.076 billion. In this field, there are approximately 117 Liquid Staking protocols. In comparison, in the Lending field, there are 296 protocols, but the TVL is only $13.332 billion, ranking second. In the Dexes field, there are 993 protocols, but the TVL is only $11.967 billion, ranking third. These data reflect the significant leading position of Liquid Staking in terms of TVL in the LSD track.
3.5 Business Data
• Operational Data
Since the project is currently waiting for the testnet to go live, there is currently no available operational data.
• Technical Data
Contributors
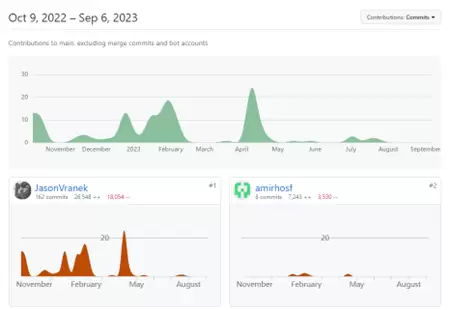
Since October 2022, the number of code contributors to the project on GitHub has gradually increased from a few dozen to a peak of 22 people. However, starting from May 2023, the number of contributors has remained at a low level, with less than 5 people, and the project’s activity has declined.
Commit
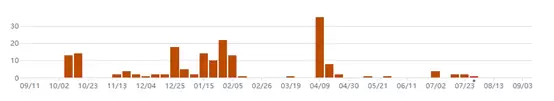
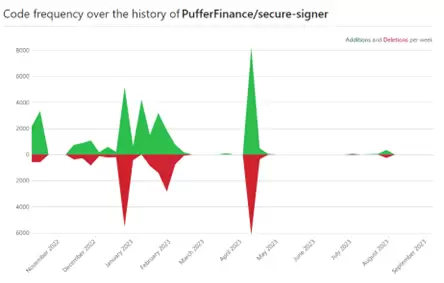
The frequency of code commits to the project is unstable. From November 2022 to June 2023, there were almost no code commit records. However, during the beginning of the project and in May 2023, code commits reached a peak, with the number of commits on the highest peak day exceeding 8,000. The average number of code commits in the early part of the year was around 4,000. Additionally, the frequency of code commits is similar to the level of involvement of project contributors.
• Social Media Data:
Twitter Data: 4,949 members
Discord Data: 2,517 members, 294 online
3.6 Project Competition Landscape
3.6.1 Project Introduction
- Lido
Lido is a leading liquid staking solution that provides a simple way for users holding digital tokens to stake and earn rewards. By using Lido for staking, users can maintain the liquidity of their tokens and be able to use them in various DeFi applications to earn additional rewards.
Lido manages secure and stable infrastructure to operate validator clients, ensuring the safety of protocol users’ funds and the correctness of validator operations. With Lido staking, users don’t need to own 32 ETH tokens, but the Ethereum assets staked by users still remain liquid and can be traded at any time. Additionally, the benefits of Lido are not limited to Ethereum, users can also enjoy similar benefits on PoS chains such as Kusama, Polygon, Solana, etc.

- Rocketpool
Rocket Pool is an Ethereum proof-of-stake protocol that aims to achieve community ownership, decentralization, and trustlessness while being compatible with Ethereum’s proof-of-stake. The project was conceived in 2016 and launched in October 2021.
Considering that most participants lack the technical capability to run nodes or don’t have enough funds to own 32 ETH, Rocket Pool aims to cater to the needs of two main user groups. Firstly, it provides a low barrier tokenized staking solution that allows users with as little as 0.01 ETH to participate in staking. Secondly, it offers an opportunity for users who want to stake ETH and run nodes to earn higher investment returns through commission earnings. The core idea of the protocol is to ensure that the network is not controlled by any single party, aligning with the core principles of Ethereum and ETH.

3.6.2 Project Comparison
1) Target Users
– Lido: Targeting users who want to delegate their digital assets to professional node operators for validation to earn stable returns.
– Rocket Pool: Targeting users who want to become Ethereum validators but are unable to independently run nodes due to technical or financial limitations.
– Puffer: Targeting users who want to run nodes at home and earn income.
2) Minimum Staking Amount
– Lido: There is no minimum staking amount, users can delegate any amount of digital assets to Lido nodes, and Lido charges a 10% protocol fee.
– Rocket Pool: The minimum staking amount is 0.01 ETH, and Rocket Pool charges a 15% protocol fee.
– Puffer: The minimum staking amount is 2 ETH, and it charges a 2.5% protocol fee.
3) Number of Nodes
– Lido: Lido has only one group of nodes operated by professional node operators.
– Rocket Pool: Rocket Pool consists of multiple nodes operated by different node operators.
– Puffer: Puffer consists of multiple nodes operated by different node operators.
4) Node Rewards
– Lido: Lido node rewards are paid in the form of ETH and LDO tokens.
– Rocket Pool: Rocket Pool node rewards are paid in the form of ETH and rETH tokens.
– Puffer: Puffer node rewards are paid in the form of ETH and PUFF tokens.
5) Node Security
– Lido: Lido nodes use multi-signature technology and decentralized storage for security.
– Rocket Pool: Rocket Pool nodes use smart contracts and decentralized storage for security.
– Puffer: Puffer nodes use TEE environment and decentralized storage (DVT) for security.
6) Profit Distribution
– Lido: Lido uses a portion of the node rewards for buyback and burn of LDO tokens to reduce supply and increase token value. Another portion is used to pay node operators and DAO financial expenses.
– Rocket Pool: Rocket Pool uses a portion of the node rewards for buyback and burn of rETH tokens to reduce supply and increase token value. Another portion is used to pay node operators and Rocket Pool Foundation financial expenses.
– Puffer: Puffer uses a portion of the node rewards for buyback and burn of PUFF tokens to reduce supply and increase token value. Another portion is used to pay node operators and DAO financial expenses.
7) Political Governance
– Lido: Lido uses DAO for governance. DAO holds LDO tokens and represents the community to vote on the selection of node operators and changes to protocol parameters.
– Rocket Pool: Rocket Pool uses DAO for governance. DAO holds RPL tokens and represents the community to vote on the selection of node operators and changes to protocol parameters.
– Puffer: Puffer uses DAO for governance. DAO holds PUFF tokens and represents the community to vote on the selection of node operators and changes to protocol parameters.
8) Token Types
– Lido: Lido uses ERC20 LDO tokens.
– Rocket Pool: Rocket Pool uses ERC20 RPL tokens and ERC20 rETH tokens.
– Puffer: Puffer uses ERC20 PUFF tokens.
9) Comparison with Traditional LSD Track Decentralization Mechanisms
1. Ethereum Staking:
– Requires depositing 32 ETH to activate a Validator node.
– Requires maintaining the normal operation of the node, ensuring the security of the chain and correct block generation.
– In return, new ETH is released to the stakers.
2. SaaS Service Staking:
– Requires owning 32 ETH.
– Delegates DevOps work to a third party, while the staker keeps the withdraw key.
– There is a risk of delegation abusing the validator key and trust issues regarding their technical abilities.
3. Centralized Exchange Delegation Staking:
– The simplest way with no funding restrictions.
– There are opacity and exchange risks with collateralized funds.
The common problem with traditional collateralization methods is that the collateralized funds lack liquidity. However, this problem can be solved through Liquidity and Staking Derivatives (LSD), a derivative. By staking liquidity, the pledged ETH can circulate in the form of another token (such as sd token or LST), thus obtaining returns in the DeFi field. The role of LSD providers is to help stakers eliminate funding, technical, and maintenance barriers, and issue LSD tokens, enabling stakers to obtain liquidity and earn more returns in DeFi.
The Ethereum staking industry is becoming increasingly centralized, and low-profit operations of operating nodes are most easily filled by institutions. This sets up barriers for individual stakers who may not have funds or technical expertise to participate in staking. Compared to traditional LSD collateralization methods, Puffer achieves lower entry barriers and decentralization by reducing margin requirements and providing re-staking services.
Puffer solves this problem by lowering the margin requirement to only 2 ETH, which is much lower than the margin requirements of other staking solutions. This means that more people can participate in staking and help protect the Ethereum network, even if they don’t have a large amount of funds to invest. By lowering the entry barrier, Puffer can increase the number of nodes on the network, thereby contributing to greater decentralization.
Compared to Lido and Rocket Pool, Puffer’s entry barrier has not been significantly reduced. Although Puffer’s margin requirement has indeed been reduced to 2 ETH, Lido and Rocket Pool also have relatively low margin requirements of 0.01 ETH and 0.01 ETH, respectively. However, in addition to the low margin requirement, Puffer also provides re-staking services, allowing stakers to pool their resources and form DVT clusters. This helps to more evenly distribute the staking rights of the network and reduce centralization risks. By concentrating resources, stakeholders can also increase their chances of being selected as validators, which is important because validators are responsible for verifying transactions and maintaining network security.
However, Puffer’s approach to lowering entry barriers is not only focused on reducing margin requirements. Puffer also provides re-staking services, allowing stakers to pool their resources and form DVT clusters, which helps to more evenly distribute the staking rights of the network and reduce centralization risks. By concentrating resources, stakeholders can also increase their chances of being selected as validators, which is important because validators are responsible for verifying transactions and maintaining network security.
In addition, Puffer’s use of Anti-Penalty TEE environments and Secure-Signer tools helps to reduce the risk of penalties for malicious behavior or failure to fulfill responsibilities by validators. This helps to enhance the confidence of individual stakers, as they may hesitate to participate in staking due to the risk of losing funds.
Overall, Puffer’s approach to lowering the barrier to entry focuses on making it easier for individual stakers to participate and form DVT clusters. By doing so, Puffer is able to more evenly distribute the staking power of the network and reduce centralization risks. This is in stark contrast to traditional LSD staking methods, which often require a large amount of capital and technical expertise to participate.
Overall, Lido, Rocket Pool, and Puffer are all designed to increase the decentralization of Ethereum, but they differ in terms of their target users, number of nodes, minimum staking amount, node rewards, node security, profit distribution, political governance, and token types. Users can choose the platform that suits their needs and preferences.
3.7 Token Model Analysis
- Total Supply and Distribution of Tokens
According to official statements, tokens have not yet been issued, and the project team is awaiting the launch of the testnet. At the same time, the project team is actively building the token model.
According to an article on the official website, although the token model is still under construction, initial information about the tokens can still be found: Puffer Protocol has two tokens: pufETH and PUFI.
1. pufETH (Staking Certificate):
– pufETH can be minted by depositing ETH into the PufferPool contract.
– The exchange rate between pufETH and ETH is determined by the rewards generated by the protocol, and the value of pufETH may be higher than ETH as rewards accumulate.
– Users holding pufETH can gradually earn rewards from staking and restaking, and can still participate in DeFi activities.
– pufETH can be used in other DeFi protocols, including as liquidity provision and participation in mining activities, to achieve compound returns.
2. PUFI (Governance Token):
– PUFI is used for protocol governance and decision-making, and can be used to pause and upgrade contracts to address vulnerabilities and Ethereum hard forks.
– PUFI holders can vote to decide protocol parameters, such as the commission rate.
– PUFI is used to manage the financial fund of the Puffer protocol, including grants.
– PUFI can be used to whitelist AVS that align with the Ethereum philosophy.
In summary, pufETH is a staking certificate that allows holders to earn rewards through staking and restaking, and achieve compound returns in other DeFi protocols. PUFI is a governance token that allows holders to participate in protocol governance decisions and manage the financial fund.
4. Preliminary Valuation
4.1 Core Questions
Does the project have a reliable competitive advantage? Where does this competitive advantage come from?
Puffer’s competitive advantage comes from its unique liquid staking protocol approach. Puffer operates around the principles of improving capital efficiency, increasing economic opportunities, and maintaining decentralization among a wider group of validators. To achieve these principles, Puffer has implemented several key functionalities.
1) The margin requirement for Puffer has been reduced to 2 ETH, allowing individual validators to participate in staking and earn rewards without having to invest a large amount of capital. This improves capital efficiency and makes it easier for a wider range of participants to get involved in staking.
2) Puffer uses anti-penalty TEE (Trusted Execution Environment) and Secure-Signer to ensure peak hardware efficiency and reduce risks. By reducing the risk of penalties, Puffer is able to provide users with a more secure and reliable staking experience.
3) Puffer offers a unique re-staking service that allows nodes to run web3 infrastructure and services. This provides additional economic opportunities for home validators and helps to enhance the overall economic potential of the Ethereum ecosystem.
In summary, these features make Puffer an attractive choice for home validators and help to mitigate the risks of centralization in the Ethereum ecosystem. By improving capital efficiency, providing additional economic opportunities, and maintaining decentralization, Puffer is in a favorable position.
What are the main operational variables of the project? Are these variables easy to quantify and measure?
The main operational variables of the Puffer project include the number of nodes, the security of the nodes, and the protocol fee revenue, among others. These variables all have an impact on the operation and development of Puffer, and therefore need to be monitored and analyzed.
1) The number of nodes is one of the key factors in the operation of Puffer. The more nodes there are, the higher the decentralization, security, and reliability of Puffer. At the same time, an increase in the number of nodes can also enhance the revenue and demand for PUFF tokens, thereby increasing the token price. Therefore, Puffer needs to closely monitor the changes in the number of nodes and take measures to attract more nodes to participate.
2) The security of the nodes is also an important factor in the operation of Puffer. Puffer uses TEE technology to protect the security of the nodes, but there are still risks such as hardware failures and network attacks. Therefore, Puffer needs to continuously improve security and take measures to protect the security of the nodes.
3) The revenue from protocol fees is another important factor in the operation of Puffer. Protocol fees are another operational variable used to manage the staking process. These rates determine the amount of rewards allocated to validators and are set by the community through a voting process. This variable is also easy to quantify and measure as it is a fixed percentage set by the community.
Therefore, Puffer needs to take a comprehensive approach to monitor and analyze these variable factors, including regular data analysis, market research, and user feedback, among others. At the same time, Puffer also needs to be flexible in adjusting strategies and measures to adapt to the ever-changing market and technological environment.
4.2 Key Risks
1) Technical compatibility risk:
The Puffer protocol is compatible with DVT technology, but using DVT technology may result in a decrease in system efficiency, thereby reducing block generation opportunities, especially when the node scale expands. This technical compatibility risk may have a negative impact on the earnings of node operators.
2) Ethereum 2.0 Upgrade Risk:
According to Puffer’s whitepaper, one of the biggest risks the project faces is being incompatible with the Ethereum 2.0 upgrade. Puffer relies on Ethereum 2.0 as the foundation for validator nodes. If the upgrade to Ethereum 2.0 prevents Puffer from functioning properly, it could have a negative impact on the project’s stability and sustainability. It is important to closely monitor the progress of the Ethereum 2.0 upgrade to mitigate this risk.
3) Development Stage and Testnet Online Risk:
The Puffer protocol is currently in its early stage, and its testnet has not yet gone live. This means that the functionality and security of the protocol have not been fully validated. During the early development stage, the project may face unknown technical and security challenges, which could affect its long-term success.
5. References
1.https://www.Puffer.fi/ Puffer Official Website
2.https://twitter.com/Puffer_finance Official Twitter
3.https://github.com/PufferFinance Official Github
4.https://dune.com/jackjin/LSD Dune Data Dashboard
5.https://defillama.com/ Defillama Data Dashboard
6.https://medium.com/@Puffer.fi Puffer Medium
7.https://Lido.fi/ Lido Official Website
8.https://rocketpool.net/ Rocket Pool Official Website
9.https://www.bitget.com/zh-CN/news/detail/12560603799731 Three Major Narratives Leading Ethereum’s LSD Track
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Restaking King Is EigenLayer’s business model a great idea or a waste?
- IDO&IEO Inventory of 8 Hot Projects to Be Launched Soon (September First Wave)
- Financial History, Legal System, and Technological Cycle The Trillion Dollar Narrative of RWA Cannot Withstand Scrutiny
- Financial History, Legal System, and Technological Cycles The Trillion-dollar Narrative of RWA Cannot Withstand Scrutiny
- In-depth analysis of Flashbots’ investment logic, technical framework, market size, and major risks.
- Mantle Network 20,000-word research report From technical features to token models, in-depth understanding of modular Layer2 new stars
- Model interpretation SOL unlocking market pressure will not bring massive selling pressure. This is a difficult but healthy reset.
