538 million Weibo user information is not worth 0.2 Bitcoin! How do I protect my data?
Author: Vanguard
Source: Blockchain Outpost
The data breach was due to Weibo being "snapped away some data" through the interface in 2019, rather than the so-called "data drag library".
Recently, some users found that 538 million pieces of Weibo user information were sold on the dark web, of which 172 million had basic account information. All data is priced at 0.177 bitcoin, which is about 7350 yuan. It is reported that the account information involved includes user ID, number of Weibos, number of fans, number of followers, gender, geographic location, etc.
- Electronic money issuer Billon Group completes $ 6 million Series A financing, mainly to expand existing use cases
- Panda miner Yang Xiao and fossil-level female miner Mint talk about BTC price and production halving together. What should the miners do? | Node AMA
- QKL123 market analysis | The master is also planted in the middle of the mountainside, not to underestimate the crisis (0320)
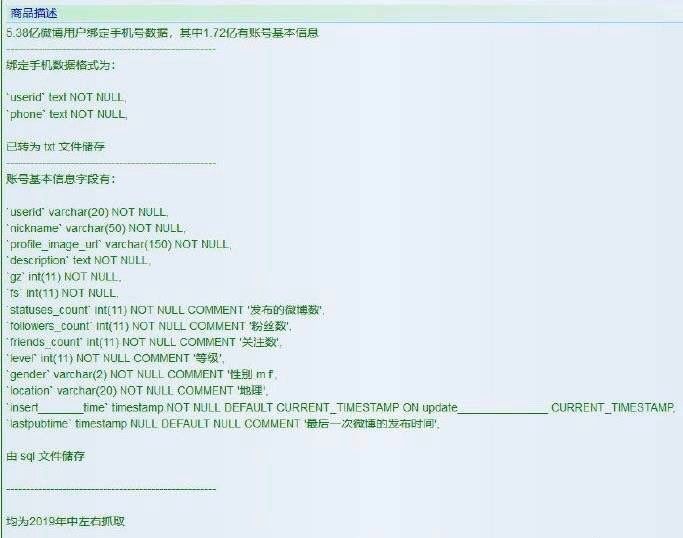
On March 19th, when a Weibo user named "Security_ 云舒" reposted Weibo, he said: "Many people's mobile phone numbers have been leaked. According to Weibo account numbers, mobile phone numbers can be found … Someone has passed Weibo leaked and found my mobile phone number to add me to WeChat. "
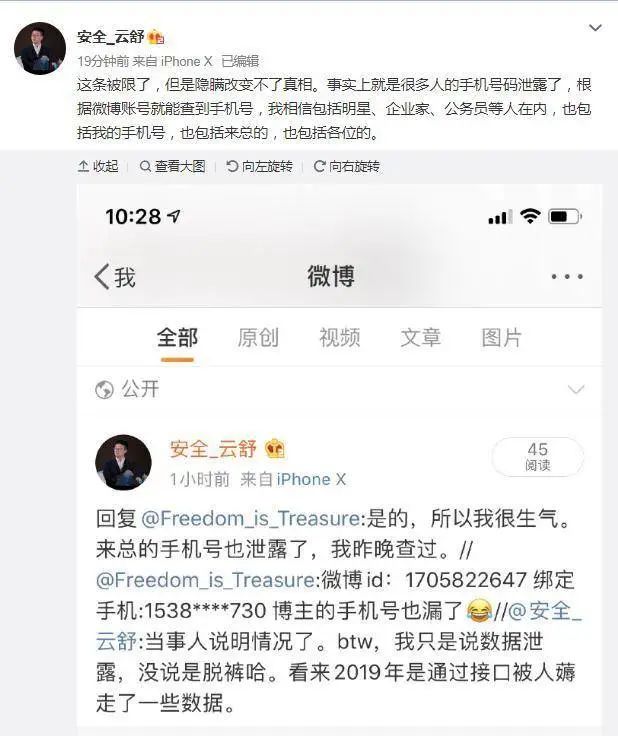
In their Weibo messages, several Weibo netizens confirmed that their mobile phone numbers were leaked. A netizen left a message, "I just checked it and it was leaked. The phone number, ID card and physical address are all correct."
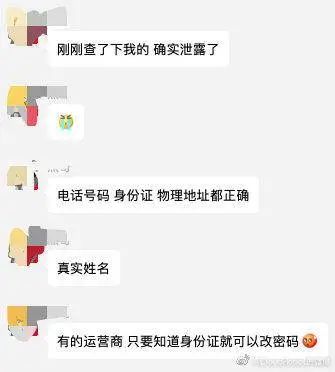
In addition to the mobile phone numbers of netizens, mobile phone numbers of "including celebrities, entrepreneurs, civil servants, etc." have been leaked.
It is reported that "Security_ Yunshu" Weibo's personal homepage shows that he is the founder and CTO of Mo An Technology, and former director of the security research laboratory of Ali Group. According to 36 氪 's verification, the netizen was Wei Xingguo, CTO of Mo An Technology.
At the time of writing, the 2 related Weibos posted by “Security_ 云舒” have been deleted.
1 Weibo response
In response to this data breach, Luo Shiyao, a netizen certified by Weibo as the “Director of Weibo Security,” replied on Weibo: Thank you for your concern. Everyone will sell (data) on the Internet every time. Every time, it will cause a wave of public opinion. I didn't want to respond, this Weibo will be used in the future.
As for the reasons for this data breach, security_ Yunshu said that this data breach was due to Weibo being “snapped away some data” through the interface in 2019, rather than the so-called “data dragging library”.
Luo Shiyao responded, "The leaked mobile phone number was violently matched through the address book upload interface in 19 years, and the rest of the public information was captured online."
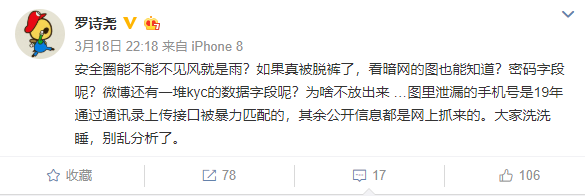
He also stated, "Some of the data that was brushed in 19 years later blocked the mouth immediately when an internal abnormality was found. We immediately reported to the police and passed the relevant information to the police after obtaining the evidence. At the same time, we have been tracing online sales information. Black and gray. User privacy is very important, especially when it comes to mobile phone numbers. "
According to Weibo, Weibo has always provided the service of querying the nicknames of Weibo friends based on the phone number of the address book. Users can use the service after authorization, but Weibo does not provide information such as user gender and ID number, and there is no Check your phone number "service. At the end of 2018, some users used Weibo-related interfaces to upload contacts in batches through batch mobile phones, matching millions of account nicknames, and selling them through information obtained through other channels. The information matched by the illegal call of the Weibo interface is the Weibo account nickname, which does not involve the identity card and password, and has no impact on the Weibo service. "After anomalies were discovered, we strengthened our security policies in a timely manner and will continue to strengthen them in the future."
Regarding this data breach, an industry security expert told the author, "For the data breach of Weibo, the first one should not be taken lightly, and the second one should not be overstated, because this is one of our many data breaches every year. Now As all Internet companies are undergoing digital transformation, in fact every enterprise has a lot of customer information. If this information is not protected, data leakage will occur. "
"Whether it is in the physical world or the digital world, it is not 100% secure, and there are bound to be various risks. Data leakage is actually one of the most common security risks in the digital world that needs attention."
2 Cause analysis
Data leaks are happening on the Internet today. In the "Annual inventory of data breaches in 2019", the author counted 43 data breach incidents from public channels, involving various industries.
The left ear mouse in Geek Time's "Data Security from Equifax Information Leakage" pointed out the reasons for the data breach:
- Exploiting known vulnerabilities in program frameworks or libraries. For example, the 145 million user data breach at Equifax, a U.S. credit reporting agency, is using a known vulnerability in Apache Struts;
- Brute force password cracking. Attackers use password dictionary libraries or leaked passwords to "bump the library";
- Code injection. Obtaining user permissions through programmer code security issues, such as SQL injection, XSS attacks, CSRF attacks, etc .;
- Use of program logs to accidentally leak information;
- Social engineering
In addition, he also explained the data leakage due to data management issues, such as only one layer of security, weak passwords, exposure of internal systems to the public network, security logs were exposed, unnecessary data and passwords were not properly stored Ground hashing, etc.
Specific to this Weibo data breach, the senior security person pointed out that according to some information currently disclosed, on many social platforms, it has the function of finding friends based on user contacts. Taking Weibo as an example, after a user signs in, it will ask you if you want to match a friend in your address book. "Apart from Weibo, Pinduoduo, JD.com, and Douyin all have similar functions."
The senior security person said, "The data leakage of Weibo is very likely that the black and gray attackers used the interface's business functions to consider incomplete or defective situations, and generated them in large quantities through scripts or automated tools locally. "
Black or gray production will use the tools in hand to generate a large number of consecutive mobile phone numbers locally, and use the Weibo interface to match the account on Weibo. In this way, it can generate a binding between your Weibo and mobile information, and use this binding to accurately locate your Weibo. "After you have your mobile phone number, you can match some other information, find your QQ number, ID number, etc. After matching some information, it may also get your account password, and then hit the library to find other information." He says.
In short, use Weibo to target individuals, mobile numbers, Weibo IDs, and QQ numbers. After getting the mobile phone number and QQ, go to get ID information, password information, etc.
32 tips to make your data more secure
For netizens, although we are the owners of personal information data, we are not the controllers of the data. "When we entrust information to a certain platform, then we actually give the initiative to the other party."
As an ordinary person, there are several steps we can take to effectively protect personal data:
- Set different passwords on different platforms, and change all passwords at a fixed time. Although this is more troublesome, the advantage is that once the data is leaked, the impact is relatively small. Moreover, after frequent password changes, even if a leak occurs, the time for which the information is valid will be shorter;
- Use of important information. When obtaining services, mobile phones must bind personal information and pay more attention to the information being bound.
Undoubtedly, the data leak of Weibo has sounded the alarm for the majority of enterprises. When data becomes the "oil" of this era, it becomes the object of many people's contention.
For enterprises or organizations, they should take a proactive approach to data leakage to avoid data leakage incidents.
There are 3 suggestions from security experts:
1. Improve data security protection methods
At present, enterprises mainly adopt network border protection and terminal management and control methods to prevent computer viruses, network attacks, and network intrusions for data security. They lack in-depth identification or perception technology for content, and lack comprehensive management and security management methods for sensitive data.
What are the sensitive data, where are they stored, which nodes are flowed through, and how can the source be held accountable after a data breach? Enterprises should adopt corresponding data security products and technical means to solve these problems.
2. Establishing industry-specific data security specifications and enterprise data security management systems
In recent years, data security has been gradually incorporated into national regulations and industry norms, including the "Network Security Law", "Basic Requirements for Cyber Security Level Protection 2.0", "Personal Information Security Regulations", and the EU "GDPR". Data security has become the basic content of a new generation of information security standards.
Although these promulgated laws and regulations have made clear legislative provisions on data security and personal information protection, they have clearly required data security guarantee obligations and responsibilities undertaken by various organizations, and ensure that individuals have the security and control over their personal information.
The expert said, "If the above-mentioned regulations are to guide enterprises to implement specific data security protection methods, they still need to combine specific industry characteristics to make clear requirements for the technical methods of data security protection to enhance their enforceability and enforceability."
3. Improve security awareness and increase protection against internal data leakage risks
At present, enterprises' investment in data security is mainly aimed at the protection of external attacks, such as firewalls, IDS, antivirus software, etc., and these technical means are difficult to identify and protect internal personnel ’s intentional or unintentional leakage.
The survey results show that the vast majority of the leakage risks come from within the enterprise. Outgoing emails and Internet uploads are the two most convenient means of data transmission, and the two channels with the highest probability of leaks.
Therefore, enterprises should strengthen the safety awareness management of internal employees or operation and maintenance personnel, increase investment in data leakage prevention products, implement the detection and control of internal personnel leakage behaviors, and reduce internal personnel's intentional or unintentional copying, outgoing and uploading, etc. Risk of data leakage from operations.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Steem forks Hive coming today, but not everyone has an airdrop
- The economic crisis is imminent. Should I sell bitcoin to save my life?
- Perspective | Bitcoin is a Really Interesting Asset: Talking about Bitcoin's Deflation Model and Its Impact on Price
- Analysts who had successfully predicted the cryptocurrency slump again predicted that Bitcoin will rebound sharply
- 2020 China Blockchain Talent Development Report: The global market size will reach $ 13.96 billion, with SMEs as the main force for recruitment
- Blockchain game The Sandbox secures $ 2.1 million in funding to build blockchain game world
- V God talks about Ethereum 2.0 again: Looking forward to the next 5 to 10 years, Ethereum will be better than Bitcoin






