A Preliminary Study of Cryptography: The Art of Hidden Information——The Eleven of the Blockchain Technology
Guide
Cryptography is a discipline that encrypts and transmits information and analyzes encrypted information. According to the emergence of the public key encryption system represented by RSA, the development of cryptography can be divided into two parts: classical cryptography and modern cryptography. Classical cryptography is based on the "replacement method" and "replacement method", and is mostly used in the military and intelligence fields; modern cryptography is based on mathematics, computer and communication science, in addition to encrypted information, digital signatures, data Integrity, identity authentication, etc. are also research topics in modern cryptography.
Summary
The replacement method changes the order of the letters in the original information according to certain rules; the replacement method replaces the letters in the original information with other letters according to certain rules. The safety of the replacement method and the replacement method is poor. The ancient Arab scholars pioneered the science of deciphering encrypted information—cryptography, and solved the alternative encryption method by frequency analysis.
For more than a thousand years, classical cryptography has evolved on the basis of replacement and replacement. The multi-alphabet replacement cryptography represented by the Virginia password uses a plurality of different alternative cipher tables in turn to encrypt the letters in the plaintext in turn. The "Enigma" used by the Germans during the Second World War was a mechanical cipher based on the complex multi-table replacement encryption principle, but was eventually conquered by Turing's "bomb" due to the flaws of its own encryption algorithm. .
- BTC "blood sucking" is fierce, only 6 coins have won BTC in the past year
- Chief Technology Officer, Bitfury Group: Blockchain accelerates e-commerce and reduces trust costs
- Is the libra hearing really good? However, the rebound has not broken
The weakness of permutation and replacement cryptography is that it does not completely eliminate certain features of the ciphertext about plaintext, retaining some information in the plaintext. The Kirkhoff's Principle proposed by August Kirkhof in the 19th century summarizes the design principles that encryption algorithms should follow: even if all aspects of the encryption system are public knowledge. As long as the key is not leaked, the encryption system should be secure.
The essence of the security problem of the encryption algorithm is: how to reduce the possibility of the attacker guessing the correct key while understanding the encryption algorithm and having a long enough ciphertext fragment? In 1948, Shannon founded the theory of information and discussed the encryption system from a mathematical perspective in a paper the following year. People began to explore the mysteries of cryptography from a scientific perspective.
Risk Warning: Potential Threats of Quantum Computing Technology
table of Contents
1 hidden method
2 encryption
3 Quiet for thousands of years: encryption and decryption
4 Holy Grail of Classical Cryptography
5 Conquering Enigma
text
Cryptography is a discipline that encrypts and transmits information and analyzes encrypted information. The etymology of the term "cryptography" comes from the ancient Greek "Kryptós" and "Graphein", meaning "secret writing," whose history is almost as old as human civilization. The ancient Hebrew scholars mastered the "single alphabet replacement cryptography" around the sixth century BC. In the following two thousand and five hundred years, classical cryptography continued to evolve on the basis of alternative cryptography. Classical cryptography is used in military and intelligence fields, and the development of microcomputers and modern cryptography can protect ordinary people's daily communication from third-party snooping. Modern cryptography is based on mathematics, computer science and communication science. In addition to the encryption and decryption of information, digital signature, data integrity, identity authentication, etc. are also the research topics of modern cryptography. Today's online payment, e-commerce, and electronic money in people's daily life are all applications of cryptography, a crystallization of wisdom for more than two thousand years.
The concept of cryptography is not the same as the "password" that people usually use to log in to websites and use bank accounts. These "passwords" for identity authentication, more accurate translation is "password" or "password", which is one of the many applications of modern cryptography. Please pay attention to distinguish the difference between the two.
Due to space limitations, the content of cryptography and cryptography applied in the blockchain will be divided into two topics.
1
Hidden method
The history of concealment is very long and can be traced back to the war years of ancient Greece and the Persian Empire in the 5th century BC. In 480 BC, the Persian fleet was secretly assembled under the leadership of Xerxes I, the king of kings, preparing to attack Greece. However, this secret operation was carried out by a Greek Dima who was exiled and lived in Persia. Tulas found out. He wrote the news that the Persian army was preparing to attack Greece and wrote it on a wooden board with a layer of wax. He succeeded in defrauding the Persian guards on the road and passing the information back to Greece. The Greek city-states united to withstand the Persian surprise. After the defeat, the once-popular Persian Achaemenid Dynasty also began to decline.
Although simply “hiding information” is far from the cryptography we are familiar with today, the secret writing method known as “hidden law” marks the beginning of people exploring the way information is kept secret.
2
Encryption
The concealment method only hides information, and once the method of hiding is exposed, or the messenger responsible for conveying information is betraying, information security cannot be guaranteed. The encryption law focuses on hiding the meaning of the information itself. The sender of the information and the receiver agree in advance to translate the information according to certain rules. The receiver can restore the original information after receiving the agreed rules, even if the information Intercepted by a third party, if the translation rules are not known, the original information cannot be restored.
The emergence of encryption marks the beginning of classical cryptography . In the above example, the unencrypted original information is called plaintext, and the information obtained by translating the plaintext according to a specific rule is called ciphertext. This rule is called an encryption algorithm . The encryption algorithms of classical cryptography are mostly based on letters, words or phrases, and can be divided into two categories: Transposition ciphers and Substitution ciphers .
The replacement method changes the order of the letters in the original information according to certain rules. In the 5th century BC, the Spartan army used a tool called Scytale to encrypt information. The sender wraps the strip of parchment on a wooden stick, writes the information horizontally, and finally disassembles the parchment. The recipient can restore the information by wrapping the letter on a wooden rod of the same diameter. The text on the parchment seems to be meaningless, and the original information cannot be restored with wooden sticks of different sizes.
But as long as you understand the encryption of this password, you can easily interpret the ciphertext. Start with the first letter of the ciphertext and count the letter for each Nth letter after it. After recording to the end of the ciphertext, repeat the operation from the second letter, and so on, and you can quickly restore the plaintext information. N depends on the diameter of the wooden stick. After writing N letters, the tape is just around the stick, and a different N is selected. The same plaintext is also encrypted by the encrypted ciphertext. The sender and the recipient must agree on the same N in advance, and the recipient can restore the ciphertext. At the same time, N cannot be known by a third party to ensure the security of encrypted communication. Here, N is called a key and is a secret knowledge shared by the participants of the encrypted communication for encrypting and decrypting information.
The replacement method replaces the letters in the original information with other letters according to certain rules. It is rumored that Caesar was writing a letter using alternative encryption. Caesar the Emperor moved each letter in the message back three places, for example, A was replaced by D and Y was replaced by B. This encryption method is called Caesar cipher. In this example, the ciphertext is shifted back by 3 digits compared to the plaintext, and the key can be represented by 3. The possible value of the key ranges from 1 to 25 (when the key is 0, the ciphertext is the same as the original text), which is called the key space . The collection of all possible letters in the plaintext is called plaintext space . The set of letters that may appear in the ciphertext is called ciphertext space . The key in the replacement method can be represented as a mapping from plaintext space to ciphertext space. Also known as the password table . The ciphertext space can be the same as the plaintext space. For example, in the Caesar password, the ciphertext letters are still 26 Latin letters. The ciphertext space can also be a superset of the plaintext space, such as mixing some invalid characters in the ciphertext to interfere with the attempt to decipher the password. The ciphertext space can also be completely unrelated to the plaintext space. For example, in the "The Adventure of Dancing Men" by Conan Doyle, the criminals used 26 different kinds of dancing villains. Replace English letters.
In the 8th century AD, the second hereditary dynasty of the Arab caliphate, the Abbasid dynasty, was settled in Baghdad. The first hundred years of its establishment were the golden age of Islamic civilization. According to records, Abbasid officials used alternative encryption to protect confidential administrative affairs and tax data, which is believed to help them build a clean and efficient government. Al-Khalil, a linguist at Basra, wrote the Book of Cryptographic Messages, which uses an arrangement of combinations to analyze the cryptography of Arabic words. In addition, Arab scholars have also pioneered the science of deciphering encrypted information, Cryptanalysis.
3
A quiz for thousands of years: encryption and decryption
Classical cryptography is mostly used for the transmission of important information in the military, political, and diplomatic fields. It is natural that there are not many people who want to spy on these secrets. In the statistical linguistics, Arab scholars found that the frequency of occurrence of each letter is different in Arabic texts with large sample sizes . The letter a and the letter l appear most frequently in Arabic (here in Latin in Arabic), because "al" is the definite article in Arabic, equivalent to the English "the", in addition, the vowel The frequency of occurrence is also relatively high. These results were quickly applied to ciphertext analysis.
In the alternative encryption method introduced earlier, all the letters in the plaintext are replaced by the same set of rules (keys). This encryption method is called single alphabet replacement encryption . In the 9th century, Arab scientist Al-Kindi explained the interpretation of this encryption method in the book Manuscript for the Deciphering Cryptographic Messages. If you can determine the language used in the original text, first list all the letters (or characters) appearing in the ciphertext, count the frequency and order of their respective occurrences, and start the attempt to ciphertext against the frequency order in which the letters appear in the language. Analysis, this method is called frequency analysis . Frequency analysis can also count the frequency of occurrence of a specific combination of letters in a language, such as "ee" in English, and the frequency of occurrence of a specific letter before and after a letter. For example, the English letter "q" must follow "u". . It was not until hundreds of years later that medieval European scholars mastered this method and decided the fate of the two queens.
In 1586, the British government’s persecution of Catholicism increased, and Anthony Babington and several other parties conspired to rebel against the Queen of Scotland, the Queen Elizabeth’s cousin, and the Catholic Queen Mary, who were under house arrest by Queen Elizabeth. And assassinate Queen Elizabeth. Baptist passed a letter encrypted with alternative cryptography through a secret ambassador and discussed the assassination plan with Queen Mary. The more complex alternative encryption method designed by Bepinton uses 23 symbols to replace English letters except j, v, and w, and 4 ambiguous symbols that do not have any meaning, indicating that the next letter appears twice consecutively in "dowbleth". The symbol, as well as several symbols, replace commonly used words to minimize the possibility of being deciphered by frequency analysis.

But unfortunately, Baptiston’s trust is actually a double-faced spy. In the back, he handed over his secret letter with Queen Mary to the Queen Elizabeth’s Secretary of State, the spy head Walsingham, who opened the envelope first. Copy a ciphertext, re-falsify the seal, and hand the ciphertext to the cryptographer Thomas Phillips for analysis. Phillips deciphered the password by frequency analysis and attached a forged ciphertext to a letter sent by Queen Mary to induce Bapington to name the accomplices involved in the project. After the assassination plan was exposed, Queen Mary, Bepinton and her secret party were executed.
The above is an example of trusting the security of the encryption method, resulting in a tragic ending. How to measure the security of encrypted communication is an important issue. The process of encrypted communication can be divided into several steps of selecting encryption method, agreeing key, encrypting plaintext, transmitting encrypted information, and restoring plaintext . In classical cryptography, most encryption methods are substitution methods, replacement methods, or a combination of the two. Therefore, encryption is almost a secret. Those who try to analyze ciphertext can interpret by trying all possible keys . When a clear word appears in the plaintext returned by a key, it means that the correct key was found. Therefore, the larger the key space, the more keys the decipher needs to try and the more secure the password. Caesar's mobile cryptography has only 25 possible keys and is very poorly secured.
The Kirkhoff 's Principle proposed by August Kirkhof in the 19th century summarizes the design principles that encryption algorithms should follow: even if all aspects of the encryption system are public knowledge. As long as the key is not leaked, the encryption system should be secure. In another way, the security of the encryption system should depend on the security of the key, not the confidentiality of the encryption algorithm.
In addition, the encryption algorithm itself may also have security vulnerabilities. Although the key space is very large, the cracker can also narrow down the possible key range by analyzing some characteristics of the ciphertext. The purpose of plaintext is generally to convey certain information, so it is meaningful , there are some linguistic or statistical features, and ciphertext retains these features to a certain extent, such as single alphabet replacement encryption Frequency characteristics of different letters appearing. In order to eliminate these frequency characteristics, some enhanced alternative encryption methods have been invented, but the drawbacks of the alternative encryption method have not been solved. For example, homophonic substitution cipher ( Homophonic substitution cipher) will appear with higher frequency letters corresponding to multiple different ciphertexts, so that the frequency of each letter in the ciphertext is similar, but the frequency information of the letter combination is still not completely eliminated, and still exists. The possibility of being deciphered. The French King Louis XIV's " Grand Chiffre " used to encrypt confidential documents has been replaced by letter pairs and has not been deciphered for two centuries. At the end of the 19th century, it was found that the number of digits appearing in the ciphertext of a large password was close to 676, that is, the possible number of pairs of letters consisting of two letters, thus guessing the encryption method and deciphering it by frequency analysis.
Queen Mary’s example also shows that the way information is transmitted is not absolutely safe . Since both parties of the communication need to agree on the same key in advance, if the way of transferring the key is not secure, the entire encrypted communication system is also ineffective, and the information security defense war is a "key defense war."
As early as the beginning of the 15th century, the Renaissance Florentine artist Alberti had realized that the single-alphabet cryptography was vulnerable to frequency analysis. He proposed a new encryption method, that is, using multiple cipher tables in turn. Encrypt the letters in the plaintext in turn. This method was carried forward by the French diplomat Virginia and invented the "Virginia Encryption Law." The Virginia encryption method uses 26 sets of different password tables, corresponding to the Caesar mobile password table with keys from 0 to 25, and is represented by English letters from A to Z. The process of encryption is to select a key word (keyword), such as KEY, and then encrypt the plaintext letters according to the corresponding password table according to the alphabetical order in the key words. The first letter uses the password corresponding to “K”. Table replacement, the second letter uses "E", the third uses "Y", and the fourth returns to "K", which loops until the end of encryption. This type of encryption is called multi-alphabet replacement encryption . The same plaintext letters may be encrypted into different ciphertexts. The same ciphertext letters do not necessarily correspond to the same plaintext, which causes great interference to the decipherer. . The key space of Virginia's cryptography is almost infinite. It was once considered unbreakable and a major breakthrough in classical cryptography for a thousand years.
But British inventor Charles Babbage does not believe that deciphering the Virginia code is an impossible task. When people began to understand the encryption algorithm of the Virginia password, its Achilles heel also emerged. There are only 26 basic password tables used by Virginia passwords for encryption, and all are known Caesar password tables. The order in which the Virginia password is encrypted using plaintext is fixed, so there is only a limited possibility for the same plaintext word to be encrypted into a ciphertext. The number of possible ciphertext types depends on the length of the key word. And all the letters whose position difference key word length are replaced with the same password table. Babbage found that every part of the ciphertext of the Virginia code, there will be repeated letter combinations, which means two possibilities: First, different plaintext fragments are encrypted by the different parts of the key word into the same Ciphertext; Second, the same plaintext segment is just encrypted by the key word at the same starting position, forming the same ciphertext. If the repeated letter combinations are long enough, the likelihood of the first situation is much less than the second. The second case also reveals the fact that the length of the key word must be a factor of the difference in the position of the repeated letter combinations. Babbage records the difference between all repeated cipher letter combinations, and all their factors, where the most significant factor (and its own factor) is the possible length of the key word. The difference in position, and all of their factors, the most significant factor (and its own factor) is the possible length of the key word.
Knowing the important information of the key word length (denoted as N), Babbage divides the ciphertext into N groups of segments encrypted by N single alphabets. Although the plaintext corresponding to these scattered fragments is meaningless, as long as the fragment is derived from complete and meaningful information, its letter frequency distribution still follows the laws of the language in which the information is written. Using frequency analysis, the Virginia password can be deciphered. In order to facilitate memory, the cipher usually likes to select meaningful key words, but this also makes the password more insecure.
4
Holy Grail of Classical Cryptography
The Virginia cryptography seems to have a huge key space. If you use a combination of 26 English letters as a key word, there are more than 300 million key words with a length of 6 characters. Why can it be cracked? What? The shortcoming of the Virginia cryptography is to use a fixed cipher list to encrypt the plaintext. Once the loop length is analyzed by the cracker, the entire encryption algorithm becomes the same as the ciphertext table encryption. In order to enhance the security of the Virginia password, you can choose a very long key word, so the possibility of repeated letter combinations in the ciphertext is much reduced, and the number of letters encrypted using the same set of password tables is also With this reduction, guessing key word length and frequency analysis will be invalid.
To the fullest of this theory is the famous one-time pad cipher, which is widely used in situations where diplomacy, military, etc. need to guarantee communication secrets at no cost. "One time at a time", that is, each time a message is sent, a new key word is replaced. The length of the key word is equivalent to the length of the information to be sent, and is randomly generated and does not contain any meaningful words . Each party of the secret communication holds a code book, and each time a communication is made, the page of the code book is torn off, and the key of the next page is used. In theory, as long as the password book is not leaked, even if the cracker intercepts the plaintext and ciphertext of a certain communication, it is still impossible to decipher the ciphertext of the next communication. "One time and one secret" is a truly secure encryption method, which is known as The holy grail of classical cryptography.
In the Second World War, the Enigma (Greek "mystery") cipher used by the Germans was an encryption machine that was similar to "one time and one secret". Since the "one time one secret" encryption method needs to encrypt each piece of information with a random key of the length of the plaintext to ensure security, it is necessary to compile a code book in advance. After the modern era, the intelligence department had to deal with a huge amount of news every day during the war. Using this codebook, not only is it difficult to check the key, but the possibility of being intercepted by the enemy is also much higher.
In 1918, the German inventor Arthur Scherbius invented a cipher with a rotor disk and a mechanical structure, which was divided into commercial and military versions. Enigma uses the keyboard to input plaintext letters. The input signal is changed through a series of three encoders, and finally the light bulb on the corresponding ciphertext of another keyboard is illuminated. The encoder that receives the input signal first will rotate once for each letter input. When it rotates for one week, the next encoder will rotate once, and so on. The three installed encoders have a total of 26×26× There are 26 different states, each of which corresponds to a password table. When starting encryption, any state can be selected as the initial state, and the "key word" used to encrypt the plaintext also changes. In addition, the encoder positions can be interchanged. There is also a device called the terminal block between the input keyboard and the first encoder. It can exchange six pairs of letters and input signals. There are about 100 billion different kinds of signals. Interchange method. Enigma is one of the most reliable mechanical ciphers in history, but with the efforts of British legendary mathematicians Alan Turing and Bletchley Park's Allied cryptographers, Some of the Enigma ciphers used by the German army failed to be protected from the fate of being cracked. The Germans also paid a heavy price for the trust of Enigma’s safety. Enigma is the last of classical cryptography. brilliant. Unable to avoid the fate of being cracked, the Germans also paid a heavy price for the trust of Enigma's security. Enigma is the last glory of classical cryptography.


5
Conquering Enigma
Alan Turing, today named after him the highest honor in the field of computer science. Turing established the general model of the computer "Turing machine", proposed the concept of "algorithms", and was the first person to use the computer to crack the encryption algorithm.
The part of the Enigma cipher that can be set by the operator includes the position of the three encoders (6 possibilities), the starting position of the encoder (17,576 possibilities), and the letter arrangement of the interchangeable board (100 billion possibilities) ), the key space is more than 10^16. The German intelligence department will prepare a password book in advance and replace the key once a day. Since Enigma had a commercial version, the Allies had a certain understanding of its construction principles and encryption methods, and with several cryptographs seized by the Allies, Enigma’s encryption algorithm was nowhere to be found. But if you don't know the key, it will still be impossible to decipher the German encrypted intelligence.
In cryptanalysis, the behavior of the decipherer trying to crack the encryption system is called attack . According to the Kirkhof principle, it is assumed that everything except the key in the encryption system is public information, and the attack is actually the behavior of guessing the key . According to the amount of information the attacker has about the encryption system, there are the following types of attacks:
Ciphertext only attack: the attacker only has information about the ciphertext.
Known plaintext attack: The attacker has information about certain plaintext fragments and corresponding ciphertext fragments.
Choosing a plaintext attack: an attacker can obtain ciphertext information corresponding to any plaintext segment.
Chosen ciphertext attack: an attacker can obtain plaintext information corresponding to any ciphertext fragment.
If an encryption system is safe against known plaintext attacks, the new ciphertext cannot be interpreted even if the attacker intercepts some ciphertext and corresponding plaintext. Single alphabet and Virginia encryption are not safe for the latter three attacks. If the plaintext is a meaningful text, they are also insecure for ciphertext attacks and can be easily cracked by frequency analysis. "One time one secret", that is, multiple alphabet replacement encryption with a key length equal to the length of the plaintext is safe for all attacks. Shannon founded information theory 30 years after the emergence of the “one-time-one-density” method and proved its security from a mathematical perspective. While Enigma's security is between the one-time secret and the Virginia encryption method, the following is a brief description of Turing's method of cracking Enigma.

Enigma's patch panel can exchange signals for up to six pairs of letters. A swap process can be expressed as

The three encoders are recorded from left to right, and the position relative to the initial state is recorded as ,,, the interaction between the patch panel and the encoder on the original signal can be expressed as

Up to now, Enigma's design is still quite satisfactory. When the sender presses the button on the keyboard, the letter will be converted into a digital signal, which will be processed into a ciphertext to light the bulb at the corresponding position on the ciphertext keyboard. What if I want to decrypt it? The password light can only display cipher text and cannot be used as input. The party receiving the encrypted information needs to use the same keyboard input ciphertext decryption as the encryption, that is, to design a circuit capable of simultaneously encrypting and decrypting, satisfying any plaintext letter and corresponding ciphertext =():
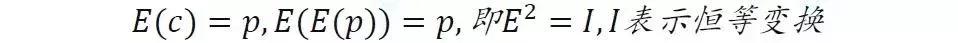
Snowby's method is to add a reflector after the three encoders. The function is to connect the output contacts of the leftmost encoder to each other and reflect the output signals back to the three encoders. Then pass through the terminal block and connect to the cipher bulb. The reflection plate is transformed into a combination of thirteen pairs of different letters, which is satisfied.

Enigma's encryption process in a particular encoder state can be expressed as

For the ciphertext attack, Enigma is almost unbreakable. The Germans change the keys every day, and the number of plaintexts encrypted per key is limited. The length of the key is 17576, which is longer than most plaintext lengths, so the frequency analysis method does not work for Enigma. However, for the known plaintext attack, the hazard of the reflector design is reflected. The Allies seized several of the German Enigma ciphers and compared some known plaintexts and ciphertexts. They found that the German official documents were more fixed in format and often appeared in fixed positions. For example, the word "wetter" (German, weather) appears in the weather forecast sent by the Germans every day. Turing also found that sometimes a special loop structure appears between plaintext and ciphertext, which helps to identify the state information of the encoder. Assume that the plaintext is known as a getter, and the corresponding ciphertext (in uppercase letters) is as follows:


It can be seen that such a cycle is produced under the influence of the wiring board setting. Using this, Turing can ignore the connection of the terminal block. He uses three identical Enigma cipher machines to set the position of the first encoder at random. Remember this position, set the second set to +1, the third set is +3, and the encoder settings of the three cipher machines are changed synchronously. Connect the output of the first cipher to the input of the second, the output of the second to the input of the third, and so on, simulating the same encryption process. If the encoder is set correctly, the same loop can be formed. Now that I don't know which letter the letter has been replaced by the patch panel, Turing thinks that connecting all the corresponding letter contacts of the two cipher machines, try the possible encoder positions one by one, as long as there is a loop connected, it means that there is a letter passing by. The three ciphers are encrypted into themselves. At this time, the encoder position is not necessarily correct, but as long as the filtered encoder position is used to restore the plaintext, the frequency board analysis can be used to test the patch panel settings one by one.
Turing's vision succeeded in simplifying the search key work by several orders of magnitude. The Tabulating Machinery Factory built a decryption machine "bomb" with twelve ciphers based on Turing's design, which can be analyzed. A cyclic structure of twelve lengths. By the end of 1942, Bletchley Park had a total of 49 "bombs", and it was possible to find out the German's key of the day in an hour, which greatly helped the Allies gain an intelligence advantage.

To crack Enigma, it is known that the corresponding segments of plaintext and ciphertext, and the internal lines of the three encoders are indispensable. During World War II, the Royal Air Force used the "gardening" to lure the German Navy to send ciphertext containing specific information. The British Air Force placed mines at specific locations, deliberately allowing the Germans to send intelligence about the coordinates of the location, intercepting the ciphertext and sending them to Bletchley Park, which is also a choice for plaintext attacks .
The weakness of the alternative encryption algorithm and encryption machine is that it does not completely eliminate certain features of the plaintext in the plaintext, and retains some information in the plaintext. For example, the single alphabet replacement encryption method retains the frequency information of the letters in the plaintext language. Some are design flaws, such as Enigma. In the late World War II, the Germans increased the number of encoders and the number of pairs of letters exchanged on the patch panels, but did not realize that the reflector was a fundamental defect. Some classical encryption algorithms have begun to eliminate the frequency information reflected in the ciphertext, just like the audio-replacement encryption method, but have never touched the essence of the encryption algorithm security problem: how to reduce the attacker's understanding of the encryption algorithm and have a long enough ciphertext fragment (or plaintext/ciphertext control fragment), guess the possibility of the correct key?
In 1948, Claude Shannon published the famous paper The Mathematical Theory of Communication, which opened up a new discipline: Information Theory. The following year, Shannon published the "Communication Theory of Secretary System", which first used mathematical tools to analyze the encryption system. Shannon's theory makes cryptography a true science and marks the beginning of modern cryptography.
references:
[1] The Code Book, Simon Singh (1999)
[2] The Code Breakers, David Kahn (1996)
Note:
For some reasons, some of the nouns in this article are not very accurate, such as: pass, digital pass, digital currency, currency, token, Crowdsale, etc. If you have any questions, you can call us to discuss.
This article is original for the General Research Institute (ID: TokenRoll). Unauthorized reproduction is prohibited.


General Education Institute × FENBUSHI DIGITAL
Text: Song Shuangjie, CFA; Sun Hanru
Special Advisor: Shen Bo; Rin; JX
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Compared with the original “one main multi-side” layered structure pioneered by Bystack, what are the pain points in the blockchain industry?
- If $13000 to $9000 is not a bear market, will the history of the bull market re-enactment repeat itself?
- Can "Leek" view the whale position information? Coinbase's new data tool is a bit 6
- Libra, can you surpass Utopia?
- Ping An and Zhong An lead: The Silver Insurance Regulatory Commission encourages the application of blockchain and the entry of nine insurance companies
- JP Morgan Chase CEO dilutes the effect of Libra coins: we will talk again after at least three years
- The top 5 “fraud coins” in the first half of the year, the lowest increase of 1400%





