Bitcoin, Ethereum and Cosmos, Polkadot Wheel PK
Bitcoin and Ethereum will connect to the Cosmos and Polkadot ecosystems. This article will explain the security of Cosmos and Polkadot from a technical perspective. Is the two cross-chain projects more resistant to attack or bitcoin and Ethereum more resistant?
Bitcoin and Ethereum will connect to the Cosmos and Polkadot ecosystems. Most of Bitcoin and Ethereum's transaction costs will occur in both ecosystems because it takes a long time to wait for confirmation transactions on the Bitcoin and Ethereum blockchains. Transaction fees will be sent to Atom and Dot token holders and verification nodes in the form of rewards (as well as holders and verification nodes for pledge tokens in ecosystems such as Sentinel, IRISnet or Binance Chain)
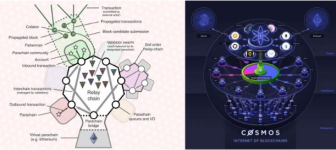
Cosmos Hub security
- Save 75% of bandwidth, make Bitcoin more secure, and core developers retreat for 1 year
- Opinion: Bitcoin is going through the blockchain is still winter
- Pantera Capital: The investment logic of DeFi products in my eyes
- 2/3 ranged attack: It is impossible to cancel during the 21-day lifting period because the new node and the current node without full uptime can be safely synchronized with the latest block (state) within 3 weeks (remote malicious fork in the release period) Will be slashed after double signature)
- Suppose you can buy 2/3 stakes in the market: 2/3 voting rights are very costly, and you can quickly detect double signatures. The chain consensus will reject malicious voting rights and the attacker loses 2/3 rights. .
- Assume that you can buy 1/3 of the equity in the market: the cost of purchasing 1/3 of the equity is also very high, the chain consensus will be solved in 1 or 2 hours of hard forks (hard fork must be done, because the network is attacked It is impossible to re-delegate or pledge more Atoms to re-determine offline voting rights. The attacker loses 1/3 of the equity.
- Assume that you can buy less than one-third of the equity in the market:
a) Instead of buying any Atom, the attacker creates a lot of small verification nodes with zero or low fees, and then persuades the principal to use the verification node until it gets 1/3 of the voting rights and starts attacking the network. However, the principal will be subject to slash, so the principal will do the due diligence and the attacker will have difficulty accumulating 1/3 of the voting rights.
b) Buy Atom and get the commission in parallel, but the cost of purchasing the token is very high, and the network only stops for 1 to 2 hours.
So the key is that the blocks in Cosmos have final certainty, and the blocks in Bitcoin or Ethereum are probabilistically determined. Therefore, it seems that Cosmos can't successfully achieve double-flowering. The worst case is that the network stops for 1 to 2 hours, but whether it is 1/3 or 2/3 malicious voting rights attack, the chain consensus will produce hard forks to adjust. In addition, if a zone is attacked, the Cosmos network may be affected. Users should pay attention to the verification node of a certain zone to confirm whether it is trusted. But in any case, in addition to the assets being attacked, the attacked area does not affect other areas or other assets on the hub, because each hub and area has independent verification nodes and governance.
Polkadot relay chain security
- More than 1/3 Byzantine verification nodes: The grandpa consensus stops determining blocks, and the longest chain consensus begins to run (Byzantine verification nodes may cover network errors, and malicious verification nodes are controlled by attackers). In this case, verifying that the node set changes, resulting in less than 1/3 of the Byzantine verification nodes, the grandpa consensus will restart the deterministic block.
- More than 1/2 Byzantine verification nodes: The babe (longest chain rule) consensus is built on the fork but does not stop. Some Byzantine verification nodes can be brought back online, and the number of Byzantine verification nodes is less than 1/3, so the grandpa consensus will restart the determination block.
- More than 2/3 malicious authentication nodes: The grandpa consensus identifies a malicious block that requires a hard fork with a chain of consensus, but this attack can be very costly and unlikely to be implemented.
In addition, the combination of these two parts of consensus means that the network communication of the block generated by the babe consensus is less than that required by the Byzantine protocol, and the certainty is achieved on the blockchain rather than on a single block, which makes Polkadot The verification nodes set on the trunk chain can be expanded to 1000 without deceleration in the pure Byzantine protocol.
Attack Bitcoin and Ethereum costs vs. cost of attacking Cosmos hub:
A 51% power attack on a PoW blockchain such as Bitcoin or Ethereum requires only enough computing power to be rented. If it is not enough, the ASIC miner can be purchased or produced, and the attacker cannot. Make "Atom or Dot". However, to attack the Cosmos hub, the attacker must acquire Atom. It is similar to an attacker who has to buy bitcoin or a large mine in Ethereum. Once he tries to double-flower or attack the network, the mine will be burned, and nothing will be done except for a short time to stop the network.
In addition, because Polkadot (the block has been finalized by the grandpa consensus) and the Cosmos block are finalized, the 51% double flower attack will not occur. ETC has recently experienced such an event (ETC has a probabilistic determination similar to Bitcoin and Ethereum). Note that there are 3 to 4 pools in Bitcoin that are close to 51%, so it's not very safe and decentralized: someone can call the pool and modify the history of the Bitcoin ledger (for example, Binance's $40 million) After being hacked by the hacker, the CEO decided to call the computing power to roll back. Then he changed his mind and thought that the better way is to keep the bitcoin blockchain "immutable".)
51% of the computing power attacked Bitcoin for 1 hour, costing about $650,000, while 51% of the computing power attacked Ethereum for $130,000 a hour. In contrast, the current Atom price is about 5 US dollars, the total pledge is 136 million Atom, and the cost of the 2/3 attack launched to the Cosmos Center will be close to 500 million US dollars, which may cost nothing more than the cost of the sky. Since the Cosmos hub stops for 1 to 2 hours, a hard fork will occur to adjust.
A 51% power attack on Bitcoin is difficult to rent enough computing power. But awesome attackers can buy or build enough ASIC miners (or create better ASIC miners, because bitcoin governance is very bad and slow, so hard forks have produced BCH, BCH changes the hash function to Preventing attacks, although not fast enough or effective, can't fight a powerful attacker) to continue to gain more than 51% of computing power. However, the attacker cannot "manufacture" Atom or Dot tokens, and the attacker can only purchase tokens or become a principal to obtain voting rights. This possibility is analyzed in the first part.
On the other hand, even if Bitcoin's algorithm changes (although management is slow) to counter the 51% power attack, malicious or good miners will be affected. The Cosmos hub is a PoS mechanism, and only a malicious vote will be slashed or forked.
Cosmos hub security vs Polkadot relay chain security
The Polkadot trunk chain has shared security, so it ensures that there are no error messages from other weak security blockchains (equivalent to zones in Cosmos). However, if 2/3 + 1 relay chain verification nodes in Polkadot are attacked and the fishman cannot report invalid transactions, then the entire Polkadot network (all chains) will be destroyed. In Cosmos, the attacked zone does not affect the rest of the network, only a single Cosmos hub will be destroyed (find the correct parameters or methods to quantify the security of the Cosmos zone or hub, or there is a way to do not need to multi-hop (multi -hop) can be directly connected between the two areas, similar to maintaining a series of area verification nodes often updated in the high security Cosmos hub to ensure connectivity to specific areas).
Despite this, destroying the Polkadot trunk chain is even more costly than attacking the Cosmos hub, because the attack relay chain is equivalent to attacking both the hub and all the zones connected to the Cosmos hub (but the Cosmos hub is about to provide shared security). Polkadot is investigating ways to avoid potential 2/3 + 1 relay chain attacks. This type of attack is that the parallel chain knows that the relay chain verification node confirms that it contains blocks that have not reached the Canon relay chain fisherman transactions. In addition, Polkadot erases all data on all verification nodes, solving data availability problems.
Another important point is that in addition to the Cosmos hub, there are more hubs, such as the Irisnet hub, the Sentinel hub, and so on. But these hub attacks cost differently, so security is different. In Polkadot, it takes the same cost for an attacker to destroy a chain or all chains (the Cosmos hub will also have shared security when the IBC is ready). In addition, an important issue is that it is difficult for users in the Cosmos ecosystem to know which authentication nodes in which regions are trustworthy to avoid receiving assets that may be attacked (zones have their own authentication nodes and security, not With shared security, users may not trust or trust the zone at all, but still have access to the Cosmos hub. By contrast, parallel chains that access Polkadot must share security. Therefore, verify trusted zones in other zones. The Cosmos hub verifies that the node will be a strong source of trust for interaction with the special area. Good decentralized token allocation is also important for the security of the Cosmos hub and zone and the Polkadot relay chain.
Source (translation): first class warehouse https://first.vip/shareNews?id=1666&uid=1
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Low-key Huawei: not only chips and 5G, but also blockchain
- Magic Cube: If you create a decentralized entertainment ecosystem, everyone is the protagonist
- Stable Currency 3.0 Report | New Historical Mission and Competitive Landscape
- I survived the collapse of Lehman and survived the financial crisis. See how he built the "Golden Surplus"
- Taiwan has included STO in regulatory scope | Standard Consensus
- 14 BTC, the highest donation in the history of Bitcoin.org
- Meet San Francisco in August, the second in 2019 than the original global developer contest