Blockchain Foundation: Misunderstanding of Decryption Mining and Consensus
As a "traditional software" developer, I feel that the learning curve is still steep during the development of the blockchain. For example, I often misunderstand some seemingly simple concepts. I suggest that beginners should read less articles like this one. There is no guarantee that your current understanding is completely accurate. The purpose of this article is to take your own notes and discuss them.
Beginners should try to read some related classic materials first: for example, white papers or official documents, related protocol documents, bip documents, or classics such as " Mastering Bitcoin ", capable of reading source code and release note, or even reading developers. Some email records or chat logs, such as bitcoincore dev log ;
With these foundations, take a look at other people's interpretations and related papers, which can reduce the probability of being misled by wrong opinions. It is fatal to misunderstand the basic concepts in the blockchain world, because they are all real gold. Silver, too many accidents are caused by a few lines of code introducing fatal vulnerabilities, or based on codebase or framework that is not fully understood;
Blockchain technology introduces a lot of new vocabulary, such as POW POS, distributed consensus, etc. This article first talks about the high-frequency POW/POS and consensus algorithms, first quote two paragraphs:
- Market Analysis: BTC trend is entangled, it is difficult to drive emotions
- During the wet season, the miners’ spring is back?
- Will BSV reproduce the BCC zero-zero operation?
1> What is the consensus:
Consensus is a form of automated governance that populates and publishes ledger entries every x period. The "blockchain" is proof that this automated governance structure actually works as designed, providing near ABSOLUTE assurance over the integrity of the ledger data. — https:/ /blog.goodaudience.com/1-assurances-in-crypto-14c55a1fd616
2> Emin Gün Sirer
POS/POW itself is not a consensus:
1. guessing game – mining mechanism solve the puzzle
POW POS is a different mining mechanism. In essence, they are different guessing games. The rules are similar. They are all constructed to make a block whose hash is smaller than a target target value, which is called the dynamically adjusted difficultyy difficulty value.
POW is to guess a nonce random value when constructing a block to meet the above conditions. When all nones are invalid, you can adjust the transaction contained in the block and fine-tune the timestamp. The more computing power, the greater the chance, this is Proof of workload
;
POS is to find a UTXO to construct a coinstake transaction, satisfying the kernel hash is less than the weight difficulty value corresponding to the UTXO, when the node is controlled
The more UTXO or the more accurate the Stake is, the greater the chance of finding it. This is the proof of equity;
It can be seen that the so-called POW POS is only a different requirement of the output block. The guessing game is one round, each round produces one block, and each round of the output block is broadcasted and released to the blockchain network, all The node will select this round of winning blocks based on the consensus algorithm and connect to the tip to connect to the current blockchain, so I refer to the POW POS as a consensus ticket or a ticket to be a candidate.
#POW小程序Example: https://github.com/bitcoinbook/bitcoinbook/blob/df1828b7205a5950a16a3182cf9b15421ee70658/ch10.asciidoc#pow_example_outputs
#POSv3Details:
Http://earlz.net/view/2017/07/27/1904/the-missing-explanation-of-proof-of-stake-version
2. Voting procedure – consensus algorithm trustless consensus
POW POS is only a ticket to be a candidate. In the end, which block is the winner of this round is determined by the majority of voters. The rule of voting is the consensus algorithm itself. The voters are the nodes in the network. Of course, I Here is the full node, the voting work probably includes (there is no detailed process here, it is a high-level overview):
1) validate and relay transaction: The process of verifying and relaying the received transaction can be regarded as one of the verification steps of voting. If a candidate block contains an illegal transaction, then the candidate area The block loses its legitimacy;
2) full validate block and activate best chain: more detailed verification of the received block (block level and transaction level verification) and find the longest chain, of course, the actual process is dynamic, the longest chain is not necessarily The longest chain,
There will be a continuous occurrence of soft fork, orphan block, and even reorg. Bitcoin is generally six confirmed (generally, as long as there is no large-scale long-term embarrassment in the world's network, there is no such thing as deep reorg, unless it is malicious. Long range attack);
In the blockchain network, here is mainly the public chain represented by Bitcoin. Each client, whether it is an ordinary mobile phone wallet or a mining machine node, has its own role in this network, for ordinary mobile wallet (hot wallet) ), his mission is mainly to broadcast and broadcast transaction information, and the purpose of the miner node is to earn coinbase rewards and fees, so miners try to generate candidate blocks, which may run different official versions, some are The modified unofficial version, and some even malicious hacker nodes, so the consensus algorithm is the basis for these good and bad nodes to cooperate in the case of mutual distrust, that is, to achieve the so-called trustless consensus;
The essence of consensus is to solve the problem of General Byzantine. The consensus algorithm is the Byzantine fault-tolerant algorithm (here, the general reference, not specifically BFT or PBFT). The purpose of POW POS is to increase the cost of bad nodes or traitor nodes. In fact, for POW It is said that the cost of doing evil is quite high, especially for the Bitcoin network, but there are many low-cost ways of doing things for POS, which will be mentioned in the next three;
The common consensus algorithm is nakamoto consensus, which is a series of consensus rules based on the longest chain principle of longest chain. The specific agreement is: https://github.com/bitcoinbook/bitcoinbook/blob/develop /ch10.asciidoc#decentralized-consensus
Other consensus algorithms are PBFT (ripple stellar hyperledger is used), see detailed explanation
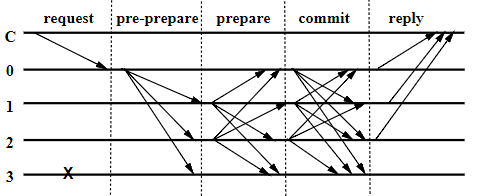
Simply put, when the client sends a transaction request, the primary node (the analogy representative) sends pre-prepare information to other nodes, and the node that receives the information responds to the prepare information. When each node receives the ack of the other node, All nodes send a commit message, and when they receive enough commit information, reply to the client;
Then I will mention the so-called DPOS algorithm here.
The DPS algorithm is divided into two parts: electing a group of block producers and scheduling production. The election process makes sure that stakeholders are ultimately in control because benefits lose the most when the network does not operate smoothly.
—
Https://steemit.com/dpos/@dantheman/dpos-consensus-algorithm-this-missing-white-paper As mentioned above, the DPOS algorithm has two parts, 'D': select the block producer, 'POS': generate the block, so DPOS itself is not a consensus, because the consensus is after the block is generated. Occurred between these producers;
Personal opinion DPOS and POS main difference is that POS is the ticket for most people to participate in the consensus, DPOS is a small number of selected people to participate in the consensus ticket, so for EOS is still based on the longest chain of longest chain The principle is to reach a consensus. The potential problem here is that the rich nodes with a large number of coins may do whatever they want, so EOS proposes to introduce the BFT consensus model. If you are interested, you can read this article " DPOS BFT – Pipelined Byzantine Fault Tolerance "
If you want to ask if some nodes don't follow the consensus or modify the consensus, the answer will be bifurcation, but if there is not enough node support and join your new consensus, your fork chain will have nothing. The meaning is, so the consensus is the consensus of the majority. The consensus of a few people only makes sense in the public chain based on DPOS or some alliance chain.
Attack vector attack vector
Understand this, you will have a relatively clear understanding of some complete problems or security incidents, such as
1) Certain attack techniques are economically viable for many POS public chains, but it is not economically viable for a POW public chain such as Bitcoin.
For example, long range attack and noting at stake attack , the main reason is that the cost of a block on the POW is very large, not to mention the deliberate choice of the wrong branch, the cost is greater, and POS does not have this problem, there is no block What cost, as long as there is a certain stake, or sometimes you can buy a stake, then construct an attack transaction, and then sell the stake, the cost is only a fee, nothing at the property attack does not understand the mistake is that you do not need to take, his Meanmin or it should be said that forger will mine on multiple branches at the same time, because the cost of the block is low, in multiple branches can increase the chance of getting rewards, nothing at stake will eventually lead to double-flower attack;
The solution is to improve on the consensus algorithm, such as setting checkpoints (bitcoin has also been adopted), penalize equivocation nodes to punish ambiguous nodes,
Specifically, there is the Slasher algorithm . If you are interested, you can take a closer look at Casper in Ethereum.
2) The same codebase, the same header-first node synchronization, resource exhausted attack will occur on the POS (that is, the attack method that runs out of memory and disk space), and POW can circumvent this problem.
This attack method simply uses the node to synchronize the fork branch block. If reorg does not occur, that is, the branch node is not the longest node, full validation will not be performed (full verification for double flower and signature, etc.) ), to consume memory (send header) or disk (send block)
— Resource Exhaustion Attacks on PoS
You can see qtum's response to this research:
Re: "Fake Stake" attacks on chain-based Proof-of-Stake cryptocurrencies
As can be seen from the above two examples, any small change in the consensus algorithm may introduce multiple attack vectors. We can learn a lot of ways of thinking. The following is a link to the vulnerability in Bitcoin history:
https://en.bitcoin.it/wiki/Common_Vulnerabilities_and_Exposures
https://en.bitcoin.it/wiki/Weaknesses
Can learn to analyze the report two lines of code caused by two vulnerabilities DOS and double spend
BitcoinCore CVE-2018-17144 Vulnerability Research and Analysis
4. More thinking
Although I am just a blockchain technology enthusiast and I don't have the opportunity to participate in the development of the public chain, but the deep understanding is also helpful to my own development ability. It is quite challenging to cultivate the decentralized global thinking, which may be familiar. Distributed development or multi-threaded development peers will be easier to get started than I am. Of course, in addition to technical thinking, many places also need to combine economic incentives. For example, this paper proposes a verification dilemma for miners:
If you do a full verification (including script execution verification) will take a certain amount of time, the advantage is to exclude illegal transactions, if you skip verification, you will get more time than other miners, but the danger may contain The legal transaction, which wastes the power to pay the price, is very interesting. It feels a bit like showing the contradiction between the 1 mining mechanism and the 2 consensus algorithm in front of me. It is completely driven by the interests of mining. Compliance with consensus rules or selective compliance, interested in understanding the solution proposed by the author " THE VERIFIER'S DILEMMA "
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Replace the SWIFT system? I understand the blockchain cross-border settlement system
- The game of the exchange after the BCHSV "belowed"
- Out of the 996 Dilemma: Property Rights, Pass and Productivity
- Hong Kong stock company "Ke Di Agriculture" terminates blockchain cooperation, and the partner "Ba Ping Tianxia" is suspected of pyramid schemes
- Polkadot innovates the Staking economy under the NPoS consensus
- Gu Yanxi: The near-term and long-term value of Bitcoin derivatives trading services
- Market Analysis: Short-term risk in BCH






