Blockchain Technology Criterion: Besieged, Troubled Privacy Defender
Guide
Since the birth of BTC, the encryption pass has gone through ten years. At present, countries have different attitudes toward encryption and certification, and some countries (regions) have relatively strict supervision. Among the various encryption certificates, the anonymous certificate designed to protect the privacy of users' transactions is the most regulated one. What is the current living environment of Anonymous Pass? How will the future develop?
Summary
The current common anonymity technologies (including privacy address technology, ring signature technology, Coinjoin, zk-SNARKs, RING-CT, and Mimblewimble) use different strategies to provide privacy protection for digital pass transactions. Coinjoin is the least cryptic and the only technology that requires third party participation; zk-SNARKs is the most occult; privacy address technology and ring signature technology are proposed in CryptoNote, but the transaction amount cannot be hidden. The subsequent RING-CT solved the problem; Mimblewimble is a newer anonymous technology that features no address at the time of the transaction.
- Faster and easier! Benxi's parent company Daimler completes the first transaction on the international trade blockchain network Marco Polo
- Thomas Lee: Bitcoin rebound? Waiting for the Standard & Poor's 500 to rise again
- The market is weak, and the bears continue to hang their longs
Since the birth of the digital certificate, the non-tamperable distributed ledger has brought a new trading model, which greatly reduces the cost of trust. However, unfortunately, the transaction mode in which the information is publicly available cannot be adapted to all transactions, one of which is privacy transactions. The emergence of the Anonymous Pass has solved this pain point, filled the gap in the demand for high privacy certificates, and met the needs of anonymous transactions.
Overall, the market value of anonymous passes that provide privacy protection is rising, which is in line with the public's growing emphasis on privacy. Today, Anonymous Pass has a high market value in the market. As of July 5, 2019, the total market value of Anonymous Pass was US$4.51 billion, accounting for 1.4% of the total market value of Encrypted Pass.
Anonymity is the most prominent feature of Anonymous Pass compared to other digital passes, but its untrackability is a double-edged sword. Anonymous certification faces severe regulatory pressures. It is difficult to achieve compliance with anonymous certificates. It may be difficult to obtain multi-party consensus in the short term. The auditable privacy agreement is an effective solution to this dilemma.
Anonymous Pass focuses on protecting the privacy of digital pass transactions, reaching the level of privacy protection that BTC has not yet achieved, and has won the first place in its share of the digital pass market.
But as more and more options are available to enhance the privacy of BTC transactions, BTC is likely to make up for its privacy shortcomings in the future. By then, the anonymous pass may be greatly affected.
table of Contents
1 Anonymous technical comparison
2 Privacy Defender: The Rise and Fall of Anonymous Pass
3 "There are tigers in front, there are wolves in the back" – Anonymous certificate of survival in the crack
3.1 “Before there is a tiger” – severe regulatory pressure
2.2 "There are evil wolves" – the challenge of the king of encryption BTC
text
In the previous article in this series, we delved into the current common anonymity techniques. This chapter continues the above, comparing common anonymous technologies and exploring the future of anonymous certificates.
1 anonymous technology comparison
Among the common anonymous technologies, Coinjoin is the least occult and is the only technology that requires third party participation; zk-SNARKs is the most occult; the privacy address technology and ring signature technology are all proposed in CryptoNote. , but can not hide the transaction amount, after the RING-CT solved the problem; Mimblewimble is a newer anonymous technology, which is characterized by no address when trading.
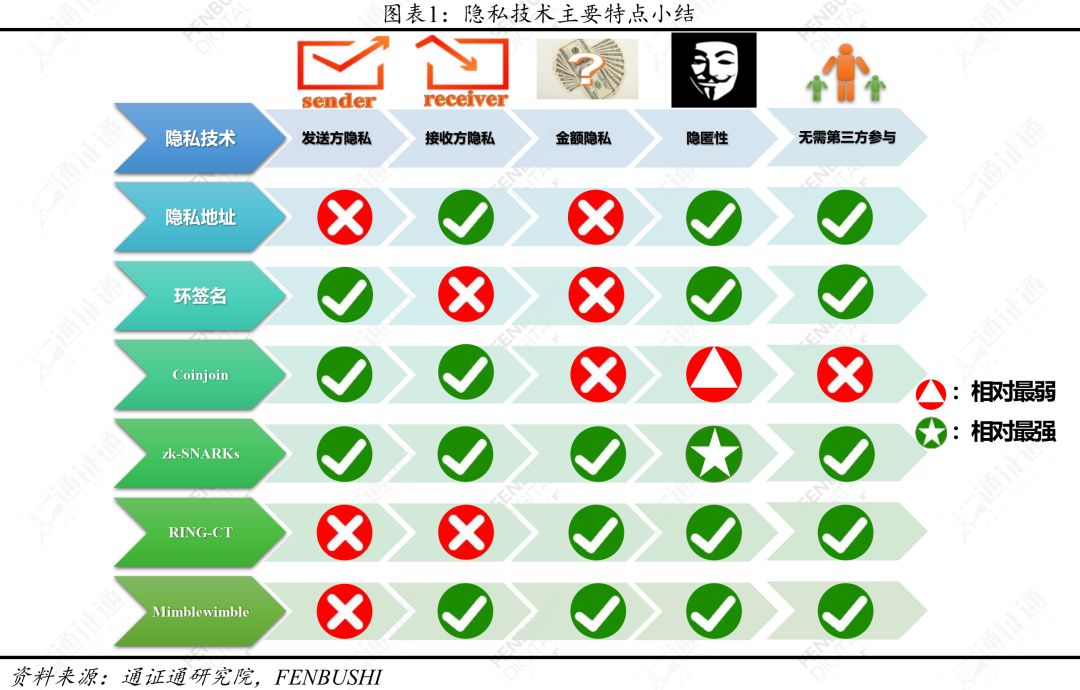
Privacy address technology and ring signature technology are technologies proposed in the CryptoNote protocol. The former provides privacy protection for data receivers, and the latter provides privacy protection for data senders. The two are generally used together, and the anonymity effect is strong and not Rely on any third party; the disadvantage is that you can't hide the transaction amount, and insufficient transaction volume can weaken the anonymity effect.
Coinjoin provides privacy protection for senders and receivers of data, helping to hide transaction amounts. Coinjoin is lightweight, relatively simple, easy to implement, and runs on most digital certificates without a specific consensus; but its shortcomings are more obvious, Coinjoin's anonymity is relatively weak, and early needs to be trusted. Third-party participation, the improved CoinShuffle++ does not need a trusted third party, but because the lack of transaction volume will affect the effect of the coin, this method still needs to participate in the relatively concentrated nodes of the pass-through resources to ensure the effect of the coin. In addition, users need to stay online to make a coin.
zk-SNARKs has the strongest anonymity and provides privacy protection throughout the transaction process, including privacy protection for data senders, data receivers and transaction amounts. The verification data is small, the storage space is small, and no third party is involved. However, zk-SNARKs relies on the trusted initial setting and the total amount of the circulation certificate cannot be checked. If there is a trust problem, the tamper can generate the digital certificate indefinitely. Detected. In addition, the use of zk-SNARKs for anonymous transactions requires complex mathematical calculations, and transaction generation time is relatively long (especially for poorly configured private computers).
RING-CT complements CryptoNote and has the ability to hide transaction amounts. RING-CT optimizes ring signature technology and improves the speed of digital pass transactions using ring signature technology. It has a strong anonymity and does not require any third party involvement. The disadvantage is that it takes up a lot of storage space and the lack of transaction volume will weaken the anonymity effect. In addition, the hidden amount of the transaction will result in the total amount of the circulation certificate not being checked, and it is impossible to detect whether there is a forgery certificate.
Mimblewimble is characterized by no transaction address and transaction amount, and is more anonymous. All transactions in Mimblewimble are private and do not involve any third party. In addition, the use of Mimblewimble can alleviate the pressure on miners' storage space; the disadvantage is that insufficient transaction volume can reduce the anonymity effect. Mimblewimble has no scripting language and it is difficult to implement smart contracts such as Lightning Networks. In addition, Mimblewimble is a relatively new technology, its effects and stability have yet to be further verified.
2 Privacy Defenders: The Rise and Fall of Anonymous Pass
Since the birth of the digital certificate, the non-tamperable distributed ledger has brought a new trading model, which greatly reduces the cost of trust. However, unfortunately, the transaction mode in which the information is publicly available cannot be adapted to all transactions, one of which is privacy transactions. The emergence of the Anonymous Pass has solved this pain point, filled the gap in the demand for high privacy certificates, and met the needs of anonymous transactions.
The total market value of Anonymous Pass has continued to rise since July 15, 2013. The total market value of Anonymous Pass and Digital Pass is highly correlated, and the two trends are very similar. In 2017, the Anonymous Pass was affected by the overall upward traction of the digital pass market, and its market value once fell below $2 billion. In 2019, the market value of Anonymous Pass entered a relatively stable rising phase. Overall, the market value of anonymous passes that provide privacy protection is rising, which is in line with the public's growing emphasis on privacy.
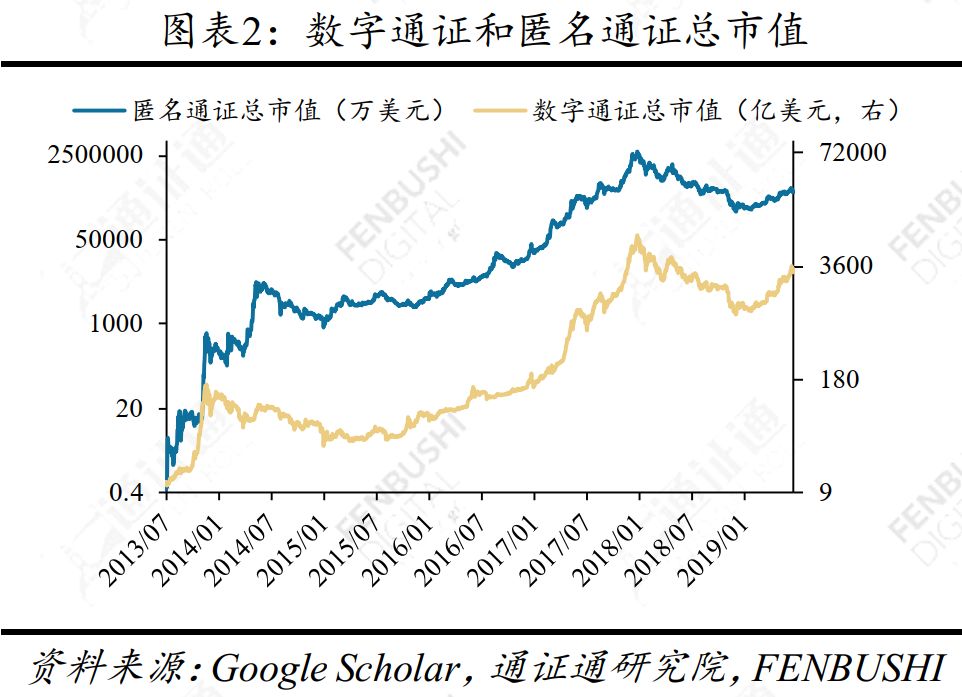
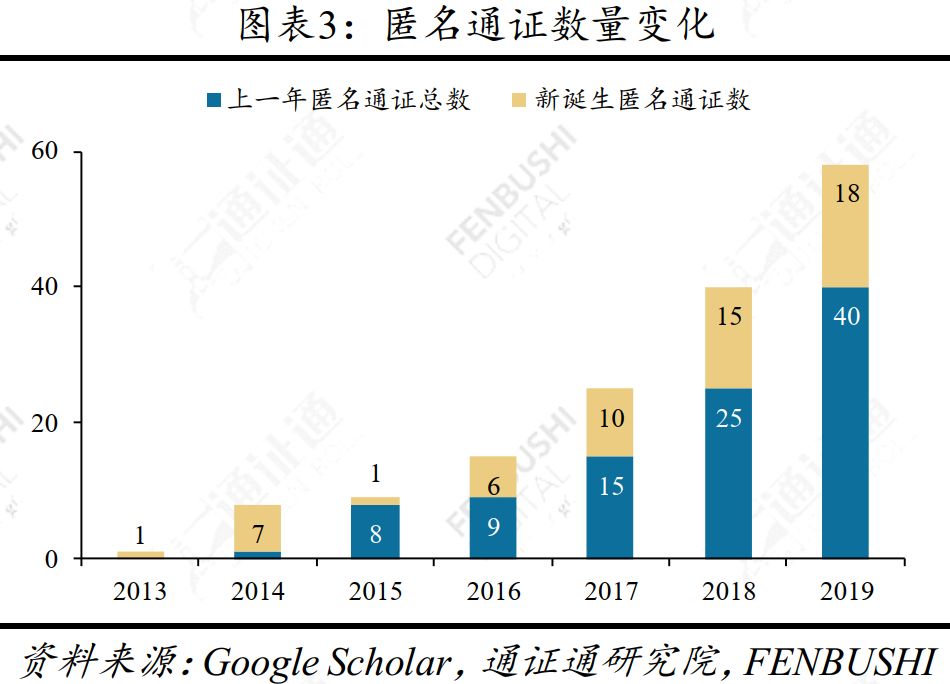
Note: The total market value of Anonymous Pass is calculated based on the 58 anonymous certificates currently on the market based on Cryptoslate statistics.
Bytecoin was the first anonymous certificate to appear, but it was initially run on a deep network and therefore lacked relevant data. On July 15, 2013, Anoncoin entered the market and became the only anonymous certificate that was officially circulated in the secondary market. In the following years, anonymous certificates such as Dash, Dreamcoin, Monero, Cloakcoin, and Bytecoin appeared one after another.
Dash was a representative certificate at that time. After the circulation in the secondary market, the market value of the market rose rapidly. At the peak, it reached 98.0%. Dash is still one of the three giants of the Anonymous Pass. However, at that time, the Anonymous Pass was very small regardless of the total market value or the number of certificates.
Since 2016, various anonymous certificates have emerged in the market (Zcash, one of the three giants of the current Anonymous Pass), was founded in October 2016. Monero, which was supported by AlphaBay (an online dark market) in August 2016, once occupied 66.7% of the total market value of Anonymous Pass, and is still in the Anonymous Pass market.
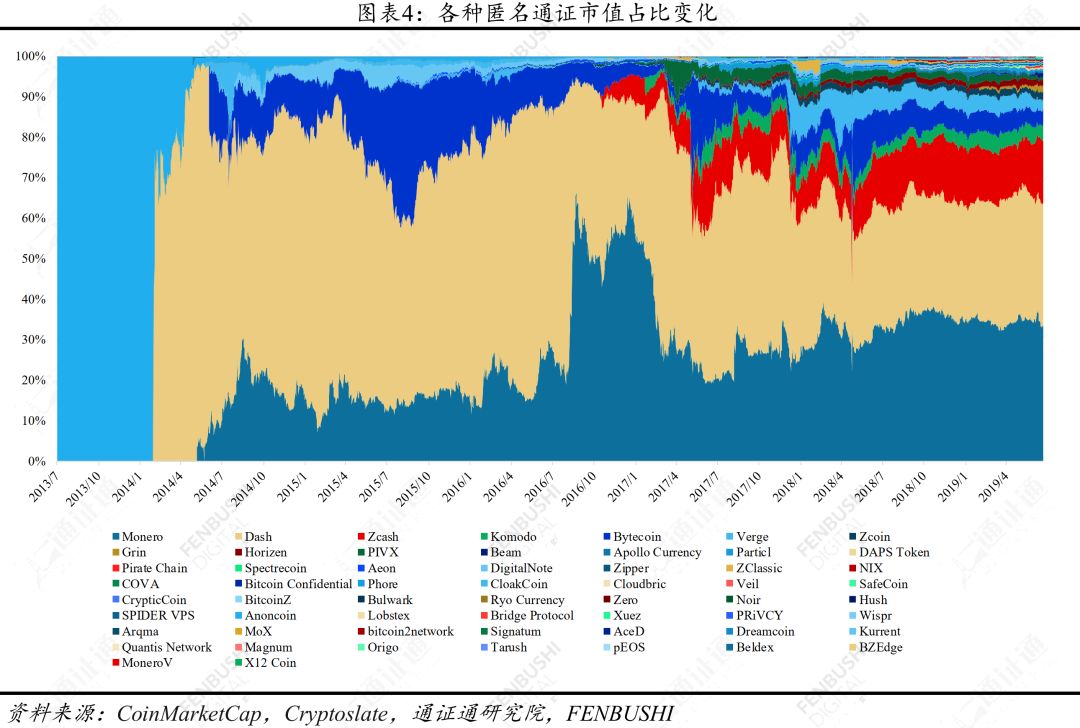
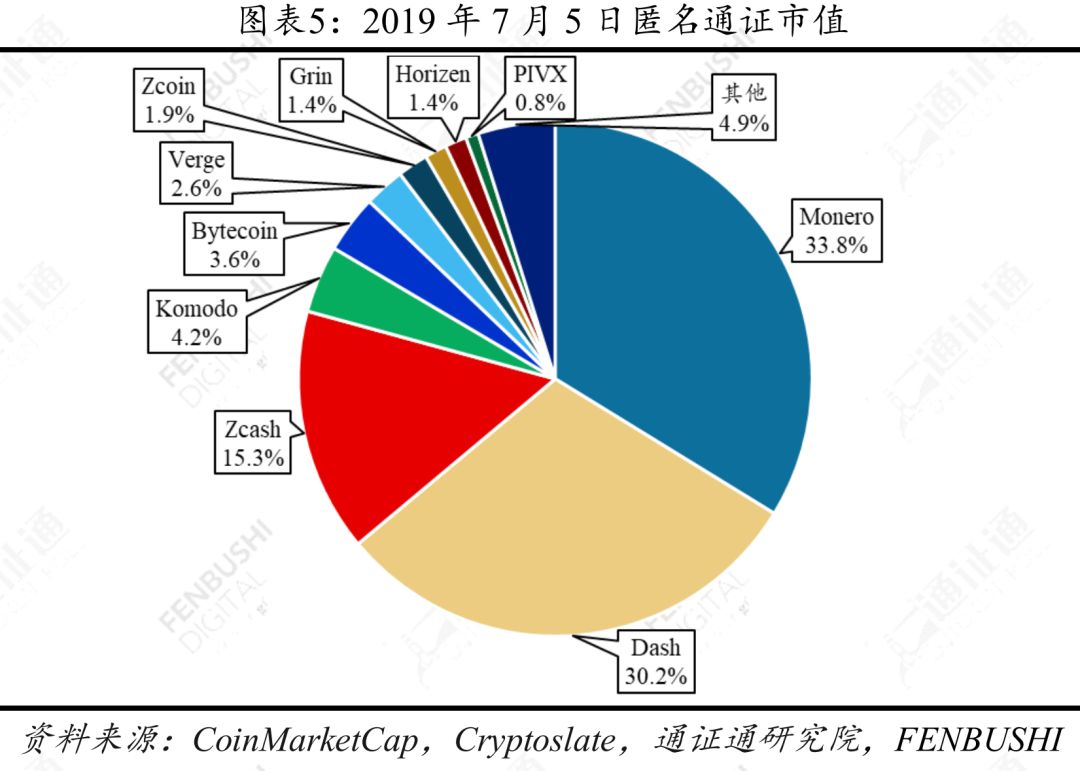
As of July 5, 2019, the total market value of Anonymous Pass has reached US$4.51 billion, accounting for 1.4% of the total market value of Encrypted Pass. At present, the common anonymous certificates on the market include old-fashioned certificates such as Monero, Dash, and Zcash, as well as emerging certificates such as Komodo, Grin, and Beam.
The market value of anonymous market value is obvious. From the market value point of view, Monero ranks first in the anonymous pass, followed by Dash. The sum of the market value of the two with Zcash accounts for 79.3% of the total market value of the anonymous pass, and the market value of the top ten of the anonymous pass market value. The proportion of the total market value of anonymous passes exceeds 95%. On July 5, 2019, Monero and Dash ranked 13th and 15th respectively in the market value of all passes.
3 "There are tigers in front, there are wolves in the back" – Anonymous certificate of survival in the crack
3.1 “Before there is a tiger” – severe regulatory pressure
Anonymity is the most prominent feature of Anonymous Pass compared to other digital passes, but its untrackability is a double-edged sword.
On the one hand, anonymous certificates can help solve many practical problems. For example, companies do not want their own transactions to be flown by competitors, and the input information of national security technology development is not suitable for disclosure. At the same time, anonymous technology ensures that personal privacy information is not abused. It is already a consensus that user data in the Internet age has great commercial value. It is often uncomfortable to accurately deliver advertisements or conduct telemarketing or even telecom fraud based on user habits. Anonymous technology can effectively solve these problems and re-own privacy rights to users themselves.
On the other hand, it cannot be denied that the emergence of an anonymous certificate also facilitates illegal transactions. BTC used to be the "official certificate" in the dark market, but its bureaucratic restrictions on its anonymity about its expansion in the dark network. Anonymous passes provide another option. Criminals can use anonymous certificates to conduct illegal activities such as money laundering and drug trafficking. This poses new challenges for regulators and law enforcement agencies.
Japan was one of the first countries to recognize the legality of digital passes, and was one of the first countries to incorporate encryption certificates into the regulatory authorities. However, CoinCheck announced that CoinCheck, a Japanese crypto-exchange exchange, had been hacked away with a cryptographic certificate worth about $530 million. On June 18, 2018, the encryption was sufficiently anonymized, including XMR, DASH and ZEC.
After this large-scale theft, the FSA (Japan Financial Services Agency) carried out a series of measures, including the revision of a more stringent exchange review system and assistance in establishing the Japan Virtual Stock Exchange Association (consisting of the Japan Digital Clearing Exchange). The industry self-discipline association, etc., and once expressed the attitude of prohibiting the transaction of anonymous pass, although there is no clear regulations or industry self-regulation regulations to restrict anonymous pass transactions, but there are strict requirements for the listing of transactions in Japan, and from the reality Look, Japan's major digital clearing exchanges do not support anonymous pass transactions.
In addition to Japan, some other countries (regions) have also proposed relevant regulations or recommendations for anonymous certificates. In January 2018, the Korean government introduced a law requiring all crypto-passters to provide identification; in May 2018, Korbit of the Korea Exchange removed five anonymous certificates; in March 2019, the head of the French National Assembly Finance Committee It is recommended to prohibit anonymous encryption of the pass.
There are difficulties in the compliance of anonymous certificates, and it may be difficult to obtain multiple consensus in the short term. At present, countries have different attitudes toward digital certification, and their attitude toward anonymous certificates is more cautious. The main reason is that anonymous certificates are far beyond the scope of supervision. If the Anonymous Pass is always closely related to criminal activities and cannot be effectively regulated, it will be quite difficult to move towards compliance.
Strict regulatory pressure is in the forefront. Anonymous certificates designed to protect the privacy of traders are still difficult to obtain official approval from all countries. This is an insurmountable slogan of anonymous pass to the public and a bottleneck restricting its development and expansion.
The privacy protocol layer may make the anonymous passer out of trouble. The privacy protocol layer can expand the interface for monitoring and auditing by the regulatory and auditing organizations at the protocol level, so that hierarchical privacy can be achieved, and the user can be completely private. The privacy agreement that provides auditing authority to a limited organization is to solve the regulatory problem. A better solution. The protocol layer includes the underlying technology for constructing the blockchain. In addition to the audit function, the protocol layer can be used to implement an anonymous transaction with an encrypted encrypted memo field containing the sender's identity and address, or the trader has the authority to delegate supervision. Ways to ensure compliance and compliance with the principles of anti-money laundering and counter-terrorism financing. At present, protocol layer expansion has become one of the important links in the research and development of blockchain technology.
Dr. Duncan S. Wong, the core technology developer of Monero, has said that the absolute privacy certificate will no longer be welcomed, and that the public and individual will be fully private and the encryption and certification of the regulatory and auditing institutions will be transparent. Gradually move to the mainstream. In September 2018, Dr. Wong proposed Abelian Coin (ABE), a privacy grading scheme. The solution is based on a verifiable encryption system. The user can choose either a full privacy mode or an accountable privacy mode, which allows user transaction data to be monitored by a particular third party. ABE combines a variety of privacy technologies. As a core developer of Monero, ABE is a natural integration of Monero's RING-CT privacy technology, with optional accountability.
3.2 "There are evil wolves" – the challenge of King of Encryption BTC
Digital certificates that have been widely accepted by the public, such as BTC and ET H, may add privacy protection features in the future. Coinjoin technology is already one of BTC's optional attributes. As of April 2019, the volume of Coinjoin used in BTC transactions was three times that of a year ago, accounting for 4.09% of all BTC transactions (data from Longhash), and the future Schnorr Technologies such as signatures, Dandelion++ or MimbleWimble may join BTC to enhance their privacy.
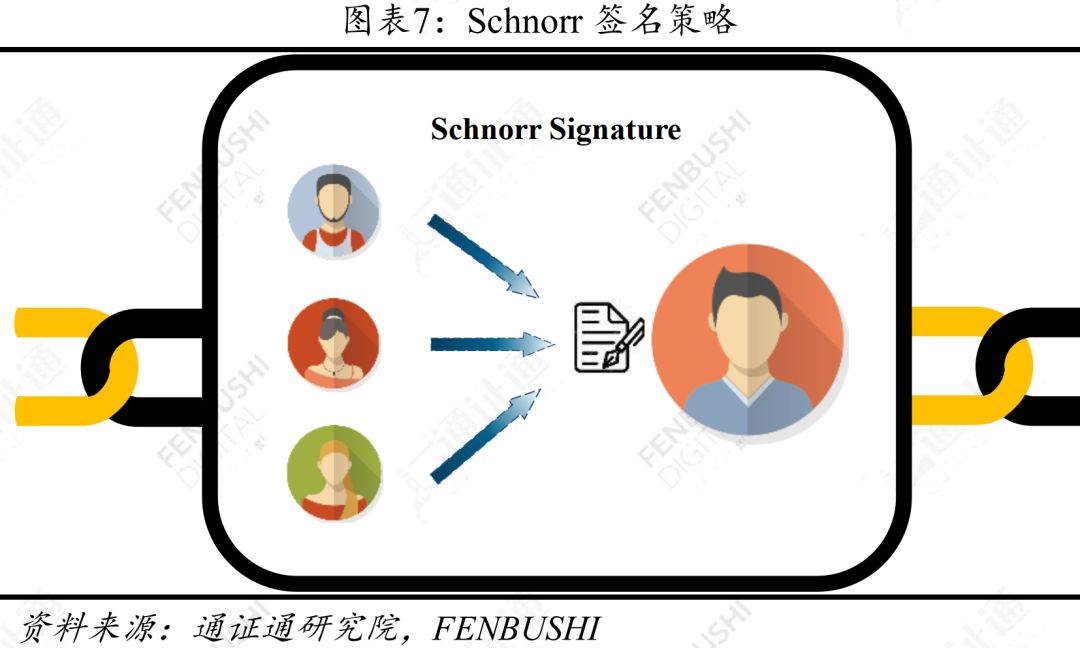
As one of the feasible solutions to improve the performance of the BTC blockchain, the Schnorr signature is compatible with the elliptic curve parameter secp256k1 already used by the BTC, and has the same safety assumptions as the ECDSA (Elliptic Curve Digital Signature Algorithm), which is a perfect alternative to ECDSA. The core use of Schnorr signatures is to aggregate multiple signatures into a single signature. Since the Schnorr signature has linear properties, two or more Schnorr signatures can be combined into a new Schnorr signature, and the new aggregate signature is still only the size of a regular signature. Such a design can make it impossible for viewers to distinguish between aggregated signatures and Regular signatures, which effectively enhance the privacy of digital passports (especially when using Schnorr-based Coinjoin technology), while increasing the transaction capacity of the block.
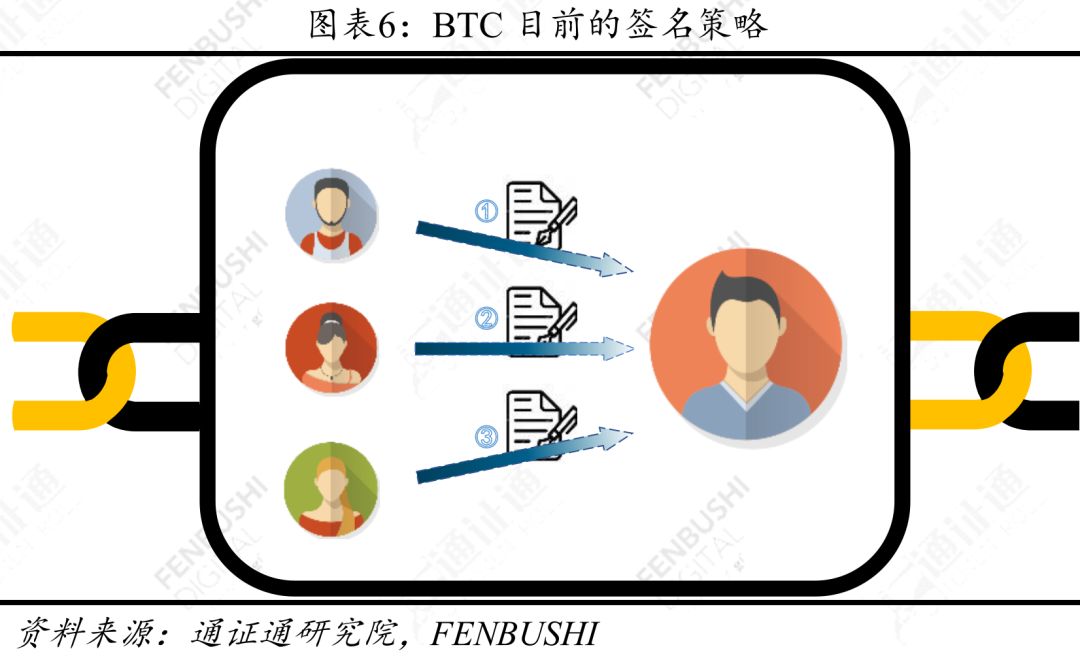
Taking a transaction with multiple inputs and one output as an example, each signature of each input party needs to be recorded on the chain. The current signature strategy makes the blockchain quite bloated.
Schnorr aggregate signature can effectively improve the anonymity of BTC transactions, and the newly generated aggregate signature is only the size of the regular signature. If each user uses Schnorr, the transaction capacity of the BTC block can be increased by 10-20%.
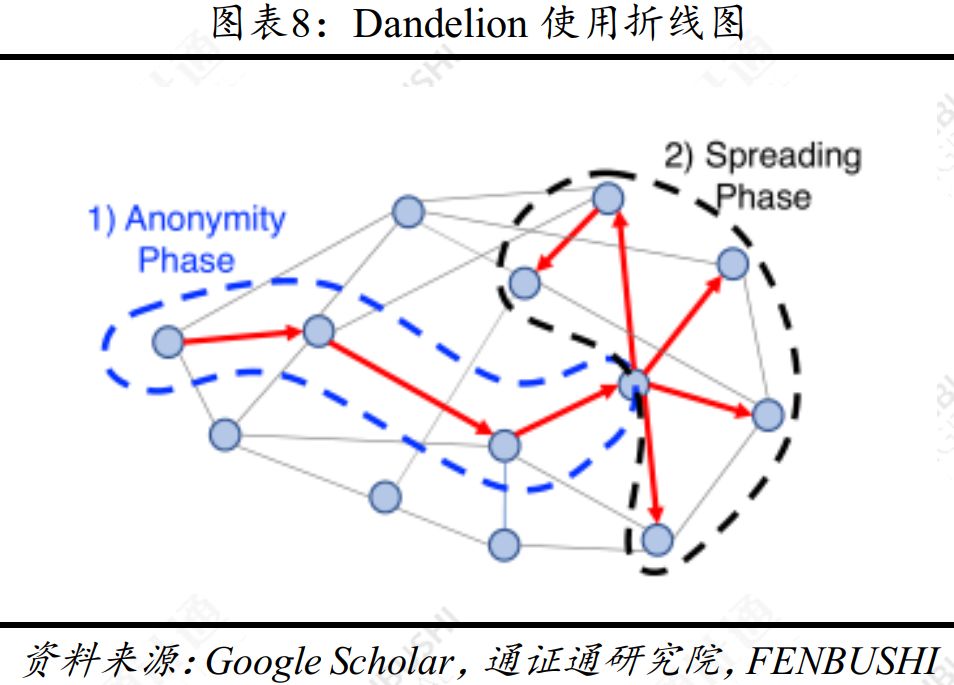
Dandelion is a simple and effective technique for increasing anonymity, which was proposed by Giulia Fanti et al in 2017. Dandelion modified the behavior of the communication node so that the original IP address of the transaction was hidden during the broadcast.
Dandelion divides the trading process into “trunk stage” and “fluff stage”: in the main stage, the transaction information is transmitted to another node instead of broadcasting to the whole network; after some information, the transaction information will enter the fluff stage and be changed to Broadcast transaction information to the entire network. The initial version of Dandelion's normal operation relies on three assumptions: all nodes are compliant with the protocol, each node generates only one transaction, and all BTC nodes run Dandelion.
If the above assumption is true, the node that broadcasts the transaction information to the entire network will no longer be the initial node that issues the transaction information, but the "relay node", and the attacker will have difficulty tracking the initial address of the transaction information. Unfortunately, the above three assumptions are not necessarily true in reality. To break through Dandelion's limitations, the researchers released Dandelion++ the following year, optimizing the algorithm and enhancing its anonymity, while also allowing nodes to generate multiple transactions.
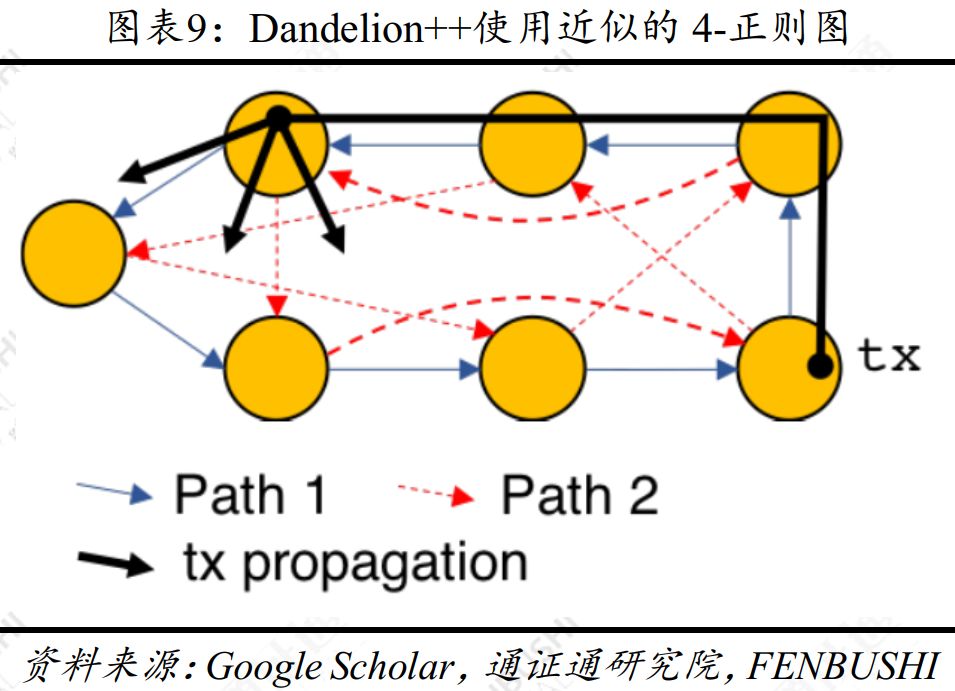
Anonymous diagrams designed by Dandelion are line charts that are easy to quantify but cannot effectively assess anonymity. Intuitively, changing the line graph frequently will not allow the attacker enough time to master the anonymous graph; in fact, it is very difficult to evaluate the attacker's heuristic learning of the anonymous graph, which makes it difficult to obtain the actual guarantee of the anonymity of the transaction. The line graph is a 2-regular graph, and Dandelion++ changes the line graph to an approximate 4-regular graph. The user will randomly forward the transaction information to one of the two surrounding nodes until it reaches the fluff stage.
Dandelion++ designed an anonymous graph that is difficult for attackers to learn, providing a guarantee for the privacy of the pass.
The Anonymous Pass is facing the challenge of the King of Encryption BTC. Since the emergence of the encryption pass, BTC has always been overwhelming the market value advantage to encrypt the pass market, is the veritable king of encryption pass. BTC, which has not fallen for ten years, has always been the vane of the encryption market, attracting more and more people to pay attention to the encryption market, and attracting more and more researchers to explore and research solutions to improve BTC. In the future, Schnorr Signatures, Dandelion++, and Mimblewimble are all likely to join BTC to enhance their anonymity, and more designs that can be used to optimize BTC anonymity may also be proposed and implemented. If BTC integrates enough powerful anonymity features, it will inevitably affect the anonymous pass-through that focuses on anonymity in the market.
Overall, the development of anonymous certificates faces serious difficulties. Severe regulatory pressures are in the forefront, auditable privacy agreements are a better solution; after the digital pass giants are catching up, there are several technologies that can be used to enhance the privacy of BTC. There are also many anonymous transaction solutions in Ethereum. The program was developed successively. For example, in May 2019, Ernst & Young Accounting Firm provided a zero-knowledge proof privacy solution for Ethereum. As the digital pass giant gradually improves its privacy capabilities, the anonymous pass that focuses on privacy in the market may be greatly affected.
Note:
For some reasons, some of the nouns in this article are not very accurate, such as: pass, digital pass, digital currency, currency, token, Crowdsale, etc. If you have any questions, you can call us to discuss.
General Information Institute × FENBUSHI DIGITAL
Text: Song Shuangjie, CFA; Tian Zhiyuan; Jin Jiahao
Special Advisor: Shen Bo; Rin Huang
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Can the Venezuelan oil company’s Bitcoin and Ethereum be placed in the central bank’s reserves?
- Market analysis: market sentiment weakened, BTC fell below 8,000 US dollars to strengthen risk
- China's blockchain patent applications exceeded 10,000: Alibaba ranked first
- Opinion | ETH is the best currency model in the world I have ever seen
- Want to join the blockchain industry? This developer's authoritative guide is worth reading
- Explaining what is a "zero knowledge proof" with Halloween candy may be a very popular explanation of cryptography…
- Ant Financial Service Jiang Guofei's latest speech: Within one year, there will be a batch of thousands of live applications in the blockchain.






