Chinese Computer Society Report: Research Progress on Key Technologies of Blockchain
Author: Block Chain Professional Committee
Source: Chinese Computer Society
Summary
Blockchain is a bookkeeping technology that is jointly maintained by multiple parties and uses cryptography to ensure transmission and access security. It can achieve consistent data storage, is difficult to tamper with, and prevents non-repudiation. In recent years, the development of blockchain technology has had an important impact on society. This article introduces the development status and research progress of key blockchain technologies in recent years. Firstly, the current status and challenges of blockchain technology are introduced from the aspects of consensus mechanism, interoperability, security, privacy protection and supervisability. Then analyze the current research status at home and abroad from cross-chain communication technology, blockchain smart contracts, blockchain security, blockchain supervision and privacy protection, blockchain technology applications, etc., and point out the development trends of related technologies And outlook. As an important technology of fintech and an important foundation of the digital economy, blockchain technology will play an important role in the future.
- Babbitt Original | Microsoft, Baidu successively layout, is DID an inevitable choice for the digital process?
- Yao Qian: What is the difference between the new financial market infrastructure based on blockchain and traditional FMI?
- South Korea is enacting a cryptocurrency bill, virtual currencies will be classified as digital assets
Keywords: blockchain, smart contract, digital currency, security, supervision
1 Introduction
In October 2008, Satoshi Nakamoto described a method based on blockchain technology in his paper "Bitcoin: A Peer-to-Peer Electronic Cash System" An electronic cash system called Bitcoin. In January 2009, the Bitcoin system was officially operated and the first Bitcoin was produced. For a decade, Bitcoin has had a huge impact on society as a whole. At the same time, blockchain technology has also been used in many fields from the issuance of Bitcoin to society, providing a new option for solving real-world problems. It is called "the machine that creates trust" and "new technology that will disrupt the Internet." ". In June 2019, the Facebook white paper of the cryptocurrency project Libra was officially announced, which has drawn great attention from countries around the world, once again pushing digital currency and blockchain technology to a new stage.
Blockchain is a bookkeeping technology that is jointly maintained by multiple parties and uses cryptography to ensure transmission and access security. It can achieve consistent data storage, is difficult to tamper with, and prevents non-repudiation. It is also called distributed ledger technology. Blockchain technology provides new solutions to further solve the problems of trust, security and efficiency in the Internet, and also brings new opportunities and challenges to the development of industries such as finance. In order to cope with the opportunities and challenges brought by blockchain technology, the industry and academia have carried out exploration and theoretical research of blockchain technology, which has provided a strong impetus for the in-depth promotion of the integration of blockchain technology and actual business. At the same time, in recent years, the trend of the development of blockchain technology and policy supervision has become increasingly apparent, which has also provided an important driving force for the in-depth integration of blockchain technology and finance and other industries.
This article introduces the development status and research progress of key blockchain technologies in recent years. It focuses on the analysis of current research status at home and abroad from the aspects of scalability, cross-chain communication technology, blockchain smart contracts, blockchain security, blockchain supervision and privacy protection, and blockchain technology applications, and points out related technologies Development trends and prospects.
2.Blockchain key technologies and the challenges they face
At this stage, although the industry ecology of the blockchain has taken shape, blockchain technology still faces many technical bottlenecks, which are manifested in many aspects such as architecture, consensus mechanism, interoperability, and system security. Therefore, it is necessary to attach great importance to the key technologies of the blockchain, and to gather multiple forces to break through the technical bottleneck, so as to clear the obstacles for all aspects of the application of the blockchain.
2.1 Consensus Mechanism
The consensus mechanism is the core and key technology for the stable and reliable operation of the blockchain system. Unlike traditional centralized systems, all network nodes in a blockchain system are free to participate and maintain independently. There is no trusted central node to undertake tasks such as network maintenance and data storage. Therefore, how to make a lot of geographically dispersed and weakly trusted blockchain nodes maintain consistent copies of trusted data and achieve stable system operation is a problem that the blockchain consensus mechanism must solve.
The main function of the consensus mechanism is to solve two basic problems:
(1) Who has the right to write data. In a blockchain system, each backbone network node will independently maintain a blockchain ledger (that is, a database in the blockchain system). In order to avoid the problem of data chaos in different blockchain ledgers, a fair selection mechanism must be designed, and only one network node is selected to write data at a time;
(2) How others synchronize data. After the selected network node writes data, other network nodes must be able to synchronize the data accurately and in time. In order to avoid falsification and tampering of new data in the network, a reliable verification mechanism must be designed to enable all network nodes to quickly verify that the received data is data written by the selected network node.
Once these two issues are resolved, the nodes in the blockchain distributed network can spontaneously establish a consistent and trusted copy of the data. First, every certain time, the nodes selected by the consensus mechanism will select the transactions to be stored in the warehouse, construct the smallest "block" of the blockchain data storage structure, and then broadcast the block data to the blockchain network. Second, all nodes on the entire network will detect the received block data, and determine whether the block data is issued by a legitimate authorized node according to the consensus mechanism. If the block data meets the requirements of the consensus mechanism and other formats, the nodes will be added to the blockchain ledger maintained by them to complete the data synchronization. By repeating these two processes, the blockchain ledger can stably and reliably update and synchronize, avoiding problems such as data confusion and data falsification.
The consensus mechanism is the core technology of the blockchain and is closely related to the security, scalability, performance efficiency, and resource consumption of the blockchain system. So far, researchers have done a lot of research work in consensus-related fields, and proposed many different consensus mechanisms. From the perspective of how to select bookkeeping nodes, the existing blockchain consensus mechanisms can be divided into five types: election, proof, random, alliance, and hybrid:
- Election consensus means that the miner node selects the bookkeeping node of the current round by "voting election" in each round of consensus process. The miner node that first obtains more than half of the votes will get the bookkeeping right. For example PBFT, Paxos and Raft. The PBFT consensus mechanism is highly efficient, supports block-second generation, and supports the participation of strong supervisory nodes. It has the ability to classify permissions and has strong advantages in terms of security, consistency, and availability. However, in the PBFT system, once one-third or more of the bookkeepers stop working, the system will not be able to provide services. When one-third or more of the bookkeepers cooperate, and all other bookkeepers are split into two When the network is isolated, malicious bookkeepers can cause the system to fork.
- Proof-of-consensus is called "Proof of X" consensus, that is, the miner node must prove that it has a certain ability in each round of consensus process, and the proof method is usually to complete a difficult but difficult to verify competitively For the task, the winning miner node will get the right to book. For example, PoW and PoS consensus algorithms. The core idea of PoW (Proof-of-Work Mechanism) is to ensure the consistency of data and the security of consensus through the competition of computing power of distributed nodes. The purpose of PoS (Proof of Stake) is to solve the problem of wasting resources in PoW. PoS is the node that has the highest equity to obtain the bookkeeping rights and revenue rewards for the new block, and does not require a large amount of computing power competition. PoS solves the problem of wasted PoW computing power to a certain extent, but the PoS consensus mechanism causes participants with equity to obtain interest by holding currency, which is prone to monopoly.
- Random consensus means that the miner node directly determines the accounting node of each round according to a random method, such as the Algorand and POET consensus algorithms. The Algorand consensus is to solve the problems of waste of computing power, weak scalability, easy fork, and long confirmation time in the PoW consensus protocol. The advantages of Algorand consensus include: low energy consumption, no matter how many users are in the system, only 1 out of every 1500 users will be randomly selected by the system to perform calculations for up to several seconds; democratization, there will be no similar Bitcoin The group of "miners" of the blockchain system; the probability of a fork is less than 10-18.
- Coalition consensus means that a miner node first elects a group of representative nodes based on a certain method, and then the representative nodes obtain the right to book in turn in turn or by election. This is a consensus algorithm characterized by "representative system", such as DPoS. DPoS can not only well solve the problem that PoW wastes energy and joint mining poses a threat to the decentralization of the system, but also can make up for the shortcomings that participants with accounting rights in PoS may not want to participate in accounting.
- Mixed consensus refers to the fact that miner nodes use a mixture of multiple consensus algorithms to select accounting nodes, such as PoW + PoS hybrid consensus, DPoS + BFT consensus, and so on. By combining multiple consensus algorithms, we can learn from each other and solve the energy consumption and security risks of a single consensus mechanism.
The current consensus mechanism is difficult to achieve a balance between performance and scalability. Although consensus mechanisms (such as PoW, PoS, etc.) used by public chains such as Bitcoin and Ethereum support large-scale node networks, the consensus performance is low. For example, Bitcoin's TPS (transactions processed per second) is only about 7. Although the consensus mechanism of the alliance chain led by Fabric (such as PBFT) has a high TPS, such as PBFT's TPS can reach 1,000, these consensus algorithms have poor scalability and only support small-scale networks. The consensus mechanism will collapse in a long time, and many consensus nodes of the alliance chain consensus algorithm are preset, and do not support the dynamic joining and withdrawal of nodes. At present, the consensus efficiency of the blockchain system is still one of the bottlenecks of the blockchain technology, which limits the development of the blockchain technology and the implementation of related applications to a certain extent. The research direction of the future blockchain consensus algorithm will mainly focus on the performance improvement, scalability improvement, security improvement of the consensus mechanism and consensus innovation under the new blockchain architecture.
2.2 Interoperability
Blockchain technology has penetrated into different industries and scenarios such as finance and supply chain, effectively breaking the value silos between different parties in the same scenario. But at this stage, value is difficult to flow between different industries and different scenarios. This makes the participants of different blockchains into closed small groups, which is obviously not conducive to the social circulation of value. Therefore, it is imperative to realize the interoperability of the blockchain. At present, the interoperability of blockchain is mainly achieved through cross-chain technology. According to the specific technical route, cross-chain technology can be divided into four categories: notary technology, side chain technology, atomic exchange technology and distributed private key control technology.
(1) Notary technology
In notary technology, transaction participants select a set of credible notaries in advance to ensure the effective execution of the transaction. The InterLedger protocol proposed by Ripple is a typical case of notary technology. InterLedger implements cross-blockchain transfers. Before the sender of A chain needs to transfer money to the receiver of B chain, he needs to find a set of connectors, and the linker sends funds to the receiver hop by hop. Each linker needs to appoint a set of notaries, who will monitor the validity of this set of transactions.
The main problem of the notary technology is the need to trust a specific notary group, which violates the original intention of the decentralized design of the blockchain and introduces certain security risks.
(2) Side chain technology
With the help of sidechain technology, one blockchain can read and verify the events and status of other blockchains. At present, the side chain technology can be divided into two major types: a pair of side chains and star side chains. A pair of side chain technologies includes a new type of blockchain represented by BTC Relay and RSK. This type of blockchain can interact with an existing blockchain (such as Bitcoin), and the main purpose is to achieve the function expansion of the existing blockchain. The star side chain technology mainly includes cross-chain infrastructure represented by Polkadot and Cosmos.It constructs a new blockchain to connect multiple other blockchains, and then forms a star topology to realize the inter-chain topology. Value and information flow.
(3) Atomic exchange
The basic idea of atomic exchange is that when two parties on two chains exchange assets, the two parties of the transaction maintain a mutually-triggering trigger through smart contracts and other technologies to ensure the atomicity of asset exchange. That is, the asset exchange between A and B occurs at the same time, or does not occur at the same time, and there is no case where A transfers to B are completed and B does not transfer to A.
A typical example of this type of cross-chain solution is Blocknet. On the basis of atomic swaps, Blocknet adds functions such as order matching and transaction matching to achieve decentralized cross-chain currency exchange. However, the application scope of atomic swap technology is relatively narrow, it is limited to the field of cross-chain transfers, and cannot meet other cross-chain needs.
(4) Distributed private key control technology
The distributed private key control technology aims to map various digital assets to a new blockchain through distributed private key generation and control technology, thereby achieving the free exchange of different digital assets on the same blockchain.
Fusion is a representative project of distributed private key control technology. Its core idea is to map the digital assets on each blockchain to the public blockchain built by Fusion. To put it simply, just as different blockchain users deposit digital assets into "banks", digital assets in banks can be freely circulated and exchanged, and user account balances can be updated in real time. Account balance shall prevail.
Distributed private key control technology is similar to atomic swap technology.It can only complete cross-chain asset transfers, and cannot perform more complex cross-chain interoperation. If it is impossible to further expand its functions in the future, the application scope of distributed private key control technology will be far from the expected effect.
It can be seen that the existing blockchain interoperability solutions have obvious shortcomings. First, the application range is narrow. For example, BTC Relay can only perform one-way operations from Bitcoin to Ethereum, while InterLedger and Fusion can only complete cross-chain transfers, and cannot perform other types of operations. Second, compatibility is poor. For example, systems such as Cosmos only support interconnection and interconnection of the same structured blockchain. In short, the existing cross-chain and interoperability solutions are still in their infancy, and there is still a long way to go for practical applications. Optimizing for such problems is also the future evolution direction of blockchain interoperability. In addition, the research on the interoperability of blockchain is directly related to the interface standard of blockchain communication. However, the most influential cross-chain solutions are currently proposed by foreign companies and research institutions. When designing cross-chain solutions for related entities, the first consideration will be their own economic interests. Therefore, China should promote the research on blockchain interoperability as soon as possible, and actively participate in the formulation of cross-chain standards, so as to fight for the right to speak for the domestic blockchain industry.
2.3 Security
At present, blockchain technology has obtained preliminary applications in the fields of finance, government affairs and even defense. These scenarios have extremely high security requirements, however, many blockchains have experienced serious security issues. As of April 2018, there have been more than 200 major security incidents in the blockchain, and the economic losses caused have exceeded $ 3.6 billion. Therefore, research on the security of blockchain is imperative.
At this stage, the industry focuses on proposing offensive and defensive measures against the blockchain system from different angles, and then exploring the security of the blockchain in all directions. Research shows that any violation of the security of the blockchain can be attributed to the destruction, modification, and leakage from five levels: algorithm security, protocol security, implementation security, use security, and system security.
(1) Algorithm security
Algorithmic security usually refers to cryptographic algorithm security, including both hash algorithms and signature algorithms used to verify transactions, and complex cryptographic algorithms used in some smart contracts.
Generally speaking, the common standard cryptographic algorithms used in most blockchains are currently safe, but these algorithms also have hidden dangers from an indirect and future perspective. First of all, from an indirect perspective, the emergence of ASIC mining machines and mining pools corresponding to the SHA256 algorithm broke the original "one CPU, one vote" concept, reducing the number of nodes on the entire network, increasing power concentration, and reducing the difficulty of 51% attacks. The blockchain system is threatened by security. Secondly, from the perspective of future development, with the rise of quantum computing, practical cryptosystems are threatened with breach.
In addition, the new type of password is more likely to become a shortcoming in practical applications because it has not undergone sufficient time and sufficient offensive and defensive tests. For example, the Massachusetts Institute of Technology found a fatal loophole in the hash algorithm of the emerging blockchain IOTA, causing the IOTA team to urgently replace the algorithm. Some untested random number generators may also have vulnerabilities. Using birthday attacks will generate the same random numbers, thereby threatening the security of the blockchain.
In order to prevent the centralization of the blockchain caused by the excessive use of ASIC, it is imperative to design a hash algorithm that is not conducive to parallel computing. At present, Litecoin's scrypt algorithm and Diablo X11 algorithm both increase the difficulty of ASIC development in terms of increasing memory consumption. In order to prevent the threat of quantum computing, traditional cryptographic algorithms need to be replaced with anti-quantum cryptographic algorithms as soon as possible. At present, the industry has proposed cryptographic algorithms based on lattice difficulties and cryptographic algorithms based on error correction codes. In order to prevent security holes caused by immature passwords, you must use caution with unverified password algorithms. In addition, the random number generator must also transition from pseudo-random to true random, such as using a chaotic-based random number generator 129J and a quantum-based random number generator.
(2) Protocol security
A protocol is a convention or call rule designed by the two communicating parties to achieve communication, including a communication protocol at the network level and a blockchain consensus protocol at the upper level.
Protocol security manifests itself as P2P protocol design security at the network level. Attackers can exploit network protocol vulnerabilities to perform Eclipse Attacks and Routing Attacks. Attackers can limit the number of network nodes by using eclipse attacks to isolate nodes from the main network, while routing attacks are attacks that control the routing infrastructure to partition the blockchain network. Attackers can also launch DDoS attacks. At present, DDoS attacks can only be controlled by collecting transaction fees and wasting computing power.
Protocol security manifests itself as consensus protocol security at the blockchain consensus level. First of all, various types of consensus protocols have fault tolerance limitations. For example, PoW has a 51% hash power attack, PoS has a 51% currency-day attack, and DPoS also has centralization risks. Second, consensus protocols are vulnerable to external attacks. For example, various attacks such as Selfish Mining and Stubborn Minging have appeared against the PoW consensus. Selfish mining can make the attacker gain more than the proportion of his own computing power; stubborn mining is an extension of selfish mining, which can increase the attacker's profit rate by 13.94% compared to selfish mining. The PoS consensus has a "Nothing at Stake" problem, that is, when a blockchain forks, miners may bet on multiple forks at the same time to seek improper benefits.
Aiming at the security of the protocol, in order to prevent network-level attacks, developers need to carefully choose the network protocol of the blockchain. In order to prevent attacks on the consensus level of the blockchain, it is necessary to design appropriate incentives and punishment measures to reduce the gains obtained by attackers.
(3) Achieve security
During the implementation of the blockchain system, programmers may intentionally or unintentionally leave loopholes, which will cause the security of the blockchain to be compromised. It is manifested in the following two aspects.
First, many blockchains have introduced Turing's complete smart contract mechanism. Users can use smart contracts to write automated programs to complete operations such as asset allocation. However, security vulnerabilities are likely to be introduced when writing smart contracts. For example, some contracts may send assets to an uncontrolled address by mistake, or the assets are locked indefinitely, resulting in a decrease in available tokens across the network.
Second, the underlying source code of the blockchain may also have various vulnerabilities such as integer overflow vulnerabilities, short address vulnerabilities, and open function vulnerabilities. For example, versions prior to Bitcoin 0.3.11 can generate a large number of bitcoin in violation, while the short address vulnerability of Ethereum can allow traders to obtain 256 times or more benefits from exchange violations.
Aiming at the security issues of the implementation of programs such as smart contracts, the industry has proposed a series of formal verification and security testing technologies, so that potential vulnerabilities may be discovered before the product goes online. In addition, many blockchain product developers have begun regular code audits, including transaction security reviews and access control reviews, in an effort to fix security issues before attackers discover vulnerabilities.
(4) Use safety
In the blockchain, "use security" specifically refers to the security of the user's private key. The private key represents the user's asset ownership and is a prerequisite for asset security. However, in the traditional blockchain, the private key is produced and kept by the user without the participation of a third party, so once the private key is lost or stolen, the user will suffer asset loss.
In actual use, some trading platforms will manage the private key instead of the user, but many platforms often use a networked "hot wallet" to manage the private key. Once the "hot wallet" is hacked, the user's assets will be stolen. In addition, due to the absence of perfect risk isolation measures and personnel supervision mechanisms, some employees with authority have taken advantage of regulatory opportunities to steal information or tokens.
To address the issue of security, users need to be more careful in keeping private keys, and try to use cold wallets that are isolated from the network to store private keys. The trading platform needs to strictly manage permissions, carefully open server ports, conduct regular security monitoring, and establish comprehensive emergency response measures.
(5) System security
System security is a holistic concept that is affected by security factors at all levels. Attackers can comprehensively use network attack methods to comprehensively utilize algorithm vulnerabilities, protocol vulnerabilities, use vulnerabilities, implementation vulnerabilities, system vulnerabilities and other aspects to achieve the purpose of attack. In addition, the introduction of social engineering attacks has also made the blockchain more vulnerable. To this end, the industry also needs to pay attention to the security of users' own systems, including regularly updating patches, enabling device firewalls, and disabling unnecessary components in routers.
Blockchain technology has begun to be widely used. However, the security issues of the existing blockchain have been endless, so we must pay great attention to security issues. At present, the research on the security of blockchain is mainly carried out from two perspectives: "attack" and "defense". The industry has discovered security risks from five levels: algorithms, protocols, implementations, usage, and systems, and put forward remedial measures. However, at this stage, security issues are fundamentally addressed. Therefore, in the future, we must innovate from the blockchain system architecture, essentially find the reason why a single vulnerability affects the system security, and get an effective mechanism to deal with the blockchain security problem.
2.4 Privacy protection
With the continuous development and wide application of blockchain technology, the privacy leakage problems it faces are becoming more and more prominent, and must be paid full attention by researchers and industrial developers. Compared with the traditional centralized storage architecture, the blockchain mechanism does not rely on specific central nodes to process and store data, so it can avoid the risk of a single point of centralized server crash and data leakage. However, in order to reach a consensus among the nodes in the distributed system, all transaction records in the blockchain must be disclosed to all nodes, which will significantly increase the risk of privacy leakage.
However, the distributed nature of the blockchain itself is significantly different from the traditional IT architecture. Many traditional privacy protection schemes are not applicable in blockchain applications. Therefore, the analysis of blockchain privacy leakage defects and the research on targeted privacy protection methods have important meaning.
According to the classification of privacy protection objects, it can be divided into three categories: network layer privacy protection, transaction layer privacy protection and application layer privacy protection. The privacy protection of the network layer covers the process of data transmission in the network, including the blockchain node setting mode, the node communication mechanism, and the protocol mechanism for data transmission. The privacy protection of the transaction layer includes the data generation, verification, In the entire process of storage and use, the focus of privacy protection at the transaction layer is to meet the basic consensus mechanism of the blockchain and the constant storage of data, to hide the data information and the knowledge behind the data as much as possible to prevent attackers from analyzing the block data. Extract user portraits; privacy protection scenarios at the application layer, including the process of blockchain data being used by external applications, etc. The process of blockchain being used externally threatens to leak transaction privacy and identity privacy. Therefore, the application layer privacy protection side The emphasis includes improving the security awareness of users and improving the security protection level of blockchain service providers, such as reasonable public and private key preservation, and building a vulnerability-free blockchain service.
In the current public chain project, all participants can obtain complete data backup. All data is transparent to the participants, and anyone can query the on-chain data on the chain. The Bitcoin project only achieves the anonymity effect by separating the association between the transaction address and the real identity of the address holder. The attacker can see the address of the sender and receiver of each transfer record, but it cannot correspond to the specific in the real world. someone. Nevertheless, an attacker can still steal privacy through multiple levels of attacks, such as launching different forms of attacks at the network, transaction, and application layers. For the alliance chain, although the regulatory role with CA nature can ensure the credibility of access nodes, if the blockchain is to carry more business, such as registering real-name assets in actual scenarios, and implementing specific loan contracts through smart contracts At the same time, it will ensure how the verification node executes the contract without knowing the specific contract information. Research on technologies such as cryptography and zero-knowledge proofs is continuously being promoted. Only the multi-level privacy protection mechanism of the blockchain technology itself is continuously improved. Only in this way can the blockchain actually empower traditional industries and give play to their established advantages.
2.5 Supervisability
At present, various types of blockchain applications led by digital currencies are developing rapidly. At the same time, potential regulatory issues in the blockchain are gradually emerging. On the one hand, the blockchain digital currency provides a safe and stable funding channel for criminal activities such as money laundering and ransomware, and promotes the operation of the underground black market. Take Bitcoin as an example. WannaCry, a well-known ransomware virus, uses Bitcoin to realize the ransom of user assets. The underground black market website "Silk Road" uses Bitcoin to illegally buy and sell. On the other hand, blockchain digital currency makes it easier to transfer funds across borders, which may damage the financial sovereignty of countries and affect the stability of financial markets. At the same time, due to the decentralization and immutability of the blockchain, the blockchain is often used to store and disseminate sensitive information. Some people store sensitive and harmful information in the Bitcoin and Ethereum blockchain transactions, and this information cannot be deleted from the blockchain. At the same time, due to the anonymity of the blockchain, the regulator cannot find the true identity of the sender through these sensitive information and the sender address of transactions involving illegal crimes. Such incidents seriously endanger national security and stability, and bring great challenges and threats to network regulators.
The current supervision of the public chain is just in its infancy, the research direction is not comprehensive, and the research technology is not mature. However, the need for public chain supervision is necessary and urgent. Therefore, supervision has become a problem that needs to be urgently solved in the field of public chain, and it has also become the biggest challenge for the current implementation of public chain projects. Due to its own characteristics, the alliance chain enables the alliance chain to support the supervision of nodes and on-chain data. Therefore, how to design a regulatory-friendly alliance chain infrastructure and realize the supervision function under the premise of protecting privacy is the main issue that needs to be studied in the supervision of the alliance chain. The development of any technology is inseparable from the supervision of the technology itself. We need to strengthen the research on blockchain supervision. Only in this way can we ensure the healthy and sustainable development of the blockchain industry.
3. Core Technology Research Progress
In view of the problems facing the current development of blockchain technology, this section covers scalability, cross-chain communication technology, blockchain smart contract optimization, blockchain security, blockchain supervision and privacy protection, and blockchain technology applications. Six aspects analyze the current research progress at home and abroad.
3.1 scalability
Scalability [ 1 ] refers to the ability of the blockchain system to process transactions and expand to accommodate transaction growth. Existing methods to improve the scalability of the blockchain can be divided into: efficient consensus algorithms, sharding technology, on-chain capacity expansion, off-chain capacity expansion, and so on. Among them, the efficient consensus mechanism has been introduced in section 2.1. Here we focus on the progress of blockchain scalability research from sharding technology, on-chain capacity expansion, and off-chain capacity expansion.
3.1.1 Sharding Technology
In 2016, Luu et al. [ 2 ] first introduced the sharding technology in the database to the blockchain, and proposed a secure sharding protocol for the public chain, Elastico, which can provide approximately linear scalability while tolerating 1/4 maliciousness. node. Specifically, Elastico first uses PoW to generate node identities, and then divides the blockchain nodes into different shards according to the last few bits in the node identities. The last few bits of the node identities in the same shard are the same. In order to ensure that at least a certain number of nodes in each shard reduce the number of broadcast messages at the same time, Elastico establishes a shard directory and manages each shard; if the number of each shard node meets the requirements, the node identity is broadcast to the nodes on the entire network. . Finally, each shard runs the BFT consensus algorithm independently, and sends the respective block headers to the ruling shard, which verifies all signatures and generates a global block broadcast to each shard. It can be seen that with the increasing number of network nodes, Elastico can achieve an approximately linear increase in blockchain throughput.
In 2017, the public chain Zilliqa based on sharding technology was proposed [ 4 ] . First of all, Zilliqa uses the method of sharding verification nodes in Elastico, which also uses PoW to select the verification nodes and performs sharding based on the bits after the hash. In order to determine the number of each shard node, experiments found that when the number of each shard node is greater than 600, the probability of a 1/3 bad node against one millionth. To this end, Zilliqa assigns verification nodes to each shard in groups of 600. Then, BFT consensus is performed on-chip. Considering that PBFT performs poorly when there are a large number of nodes, Zilliqa uses a multi-signature algorithm to optimize the PBFT consensus algorithm, thereby reducing the communication complexity.
In 2018, Kokoris-Kogias et al. [ 5 ] pointed out that Elastico's shards with a small number of nodes have a high probability of damage, and the shard partitioning does not have strong anti-prediction, cannot guarantee the atomicity of cross-shard transactions, and verifies that nodes frequently switch between Tablets cause problems such as performance degradation. To this end, the first blockchain OmniLedger that can compete with centralized payment systems (such as Visa) and has horizontally extended transaction processing capabilities has been proposed using sharding technology. Specifically, OmniLedger distributes the generated verifier identity to different shards through an identity chain. To ensure that the verifier selection process is scalable and highly predictable, OmniLedger uses public random protocols or cryptographic lottery protocols to select verifier groups, and uses the RandHound protocol to securely assign verifier groups to different shards. Secondly, in order to guarantee the atomicity of cross-shard transactions, OmniLedger proposed a Atomix, a Byzantine shard atomic submission protocol, to ensure that each transaction is fully committed or eventually cancelled, to achieve consistency across cross-shard transactions, thereby preventing double payments or funds Issue with permanent lock. Finally, OmniLedger uses the status block to summarize the status of all shards in a cycle, which reduces the storage and startup overhead for the verifier, and uses the trusted but checked method to realize the real-time nature of small payments.
Subsequently, Zamani et al. [ 6 ] pointed out that OmniLedger, like Elastico, can only tolerate 1/4 malicious nodes, and only when the number of malicious nodes is less than 1/8, can it reach a delay of less than 10 seconds. Secondly, the communication between nodes is complicated in the consensus process, and a trusted initialization process is needed to generate random parameters. In addition, it is vulnerable to DoS attacks that use Atomix to lock malicious users of arbitrary transactions. To this end, a public chain RapidChain that resists Byzantium is proposed to improve the security and scalability of blockchains such as Elastico and OmniLedger. Specifically, RapidChain includes startup, consensus, and reconfiguration phases. The startup phase mainly uses the election protocol to select the root group from the network nodes to generate random bits for establishing fragments. The consensus phase mainly adopts a practical synchronous Byzantine consensus algorithm [ 14 ] , which realizes that the content of the slice can tolerate 1/2 malicious nodes, and the overall tolerance of 1/3 malicious nodes. The reconfiguration phase mainly uses the Cuckoo rule [ 15 ] to ensure that the new node does not affect the 1/2 Byzantine tolerance of all the shards after joining.
In 2018, Vitalik proposed an Ethereum sharding scheme based on a two-layer design [ 3 ] . Specifically, the Ethereum blockchain is divided into a main chain and a shard chain. The main chain manages the shard chain through a Validator Manager Contract (VMC). The shard chain uses PoS consensus mechanism to package transaction data to generate verification Blocks, through these verification blocks, eventually generate blocks on the main chain. Each transaction runs independently on one of the shards, and the verification node only verifies the transactions of the shards. In order to ensure that the verification selection process is highly anti-predictive, VMC uses random sampling to assign verification nodes to the shard chain, and simultaneously verify the verification block headers submitted by all shards, and records the verification block headers that pass the verification to the chain. on. In addition, VMC uses UTXO model and receipt tree to achieve cross-chip communication.
3.1.2 Capacity Expansion
Capacity expansion on the chain improves the scalability of the blockchain by changing the underlying structure of the blockchain, such as increasing the block size and shortening the block production time. Part of the existing research studies high-efficiency consensus mechanisms, such as Bitcoin-NG, PBFT, etc., to improve the scalability of the blockchain by shortening the block generation time. Part of the research involves increasing the block capacity, involving BIP-102, BIP-103, BIP-104, BIP-106, BIP-107. The Hong Kong consensus reached in February 2016 states that the Bitcoin core will pass a hard score after Segregated Witness The fork expands the block to 2M. However, this consensus was not implemented. In October 2016, ViaBTC, a new mining pool invested by Bitmain, proposed that in Bitcoin Unlimited, the upper limit of block capacity is no longer a fixed value, but can be changed by miners' votes. However, due to technical reasons, Bitcoin Unlimited ended in failure. The New York Consensus reached in May 2017 states that it will be ready to implement the SegWit2X capacity expansion solution, namely the SegWit soft fork and the 2M capacity expansion hard fork. However, the consensus ended in failure. In August 2017, BCH performed a hard fork at the Bitcoin block height of 478558, removed the Segregated Witness, and expanded the block to 8M. It is expected to solve the problems of block congestion and high fees in the Bitcoin system through the on-chain expansion. Since then, BCH has been upgraded 4 times by means of a hard fork.
3.1.3 Off-chain Expansion
Off-chain expansion is to transfer transactions to the off-chain for completion, and the on-chain is only used as a transaction record or arbitration platform. By changing the blockchain from a settlement platform to a clearing platform, the number of transactions on the blockchain can be reduced, and the transaction capabilities of the blockchain can be enhanced, including schemes such as segregated witness, state channels, and sidechains.
In 2015, Poon et al. [ 16 ] first proposed the concept of the Lightning Network, which took away small transactions in the Bitcoin network by establishing a micro-payment channel for transactions off-chain. In the Lightning Network, it mainly includes two protocols: Revocable Sequence Maturity Contract (RSMC) and Hashed Timelock Contract (HTLC). The RSMC mechanism implements two-way payment of payment channels by setting time locks and introducing penalties, while HTLC uses the conditional payment method to achieve the problem of cross-channel payment of different nodes. The specific process of Lightning Network is roughly divided into the initial phase, the transaction phase and the end phase. In the initial stage, the two parties to the transaction create a trading channel and place their deposits in the created capital pool to broadcast each other's initial status; the transaction stage updates the commitments of each round to conduct transactions; after the transaction is completed, the two parties broadcast the commitments, The channel is closed. In order to ensure two-way payment in the payment channel, RSMC uses the time lock mechanism to delay the time for the party in the channel to retrieve the asset, and at the same time, the penalty mechanism is used to ensure that the commitments of the two sides of the channel are up to date. If there is a false transaction on one side of the transaction, the other party can find out within the delay of the time lock and recover the assets in the channel to punish the false transaction.
However, in order to solve the problems of the efficiency and availability of the Lightning Network, the penalty transaction in the payment channel of the Raiden network [ 17 ] is based on the signatures of the two parties to the transaction round, which makes the payment channel no longer limited to the script of the Bitcoin system. Limitations effectively avoid the problem of increasing transaction costs caused by the continuous occurrence of high-frequency transactions. Miller et al. [ 18 ] defined a new payment channel Sprites, which solves the problem that if the user fails to cross-chain, it will consume too much time. Sprites uses smart contracts in the Ethereum platform to design management contracts based on hash primitives, so that users can obtain information about whether the transaction was successful by calling the status of the contract, thereby reducing time costs. In order to ensure the sustainability of the transaction channel, Duplex proposed by Decker et al. [ 19 ] used the time lock mechanism in the Bitcoin system to design the structure of an invalid tree to ensure the channel's durability, while ensuring secure and timely transactions between customers. Revive, proposed by Khalil et al. [ 20 ] , allows any group of users in a transaction channel to safely rebalance their transaction channels through the preferences of the transaction channel owner to ensure the sustainability of the payment network.
The Plasma proposed by Poon et al. [2 1 ] is a side chain technology based on the Ethereum network by reducing the amount of transactions on the root chain as much as possible by establishing a side chain mechanism, thereby reducing the transaction load on the root chain. The Plasma blockchain is a tree structure with multiple branches, each branch is a sub-chain. The hash value of the block header of a general sub-block is stored in the root chain. verification. In order to prevent fraud in communication between the sub-chain and the root chain, Plasma has designed a Fraud proofs mechanism. The root chain is mainly responsible for ensuring the security of the network environment and the handling of fraud. Each sub-chain can have its own fraud proof, which can be built on different consensus algorithms. When fraud occurs, users can submit fraud certificates to the root chain to ensure that their rights are not harmed. MapReduce is used in Plasma as a distributed computing rule that organizes and calculates data across multiple databases. In the MapReduce mechanism, each sub-chain is regarded as a database, and fast data processing is realized. Finally, Plasma reduces the work of the main chain by creating multiple sub-chains through a tree structure, so that the main chain can process more transactions per second and improve the overall performance of the Ethereum network.
3.2 Cross-chain communication technology
The research on blockchain cross-chain technology can be traced back to 2012. Ripple released the Interledger Protocol (ILP) for the first time to propose an inter-blockchain interoperability solution. In 2014, Blockstream launched Sidechain and proposed a two-way anchoring side chain technology solution. This technical solution has been the focus of research until today. In 2015, the design idea of Lightning Network was proposed, and the technical route of cross-chain using hash lock technology was created. In 2017, Fusion was officially launched, and a distributed private key control technology solution was proposed. After continuous development and innovation of blockchain cross-chain technology, it can be roughly divided into four categories: notary technology, side chain technology, hash lock technology, and distributed private key control technology.
3.2.1 Notary Technology
Notary technology refers to the technology that uses a trusted notary to ensure the atomicity of transaction execution to complete cross-chain transactions. The main representative of this technology is the Interledger protocol (ILP) proposed by Ripple Labs.
(1) Ripple
Ripple is the world's first open payment system and the first technology to realize cross-system transfer using blockchain technology. Its essence is an open source, distributed payment protocol, and its main application area is cross-border transfer. Now banks' cross-border transfers, clearing and other operations rely on the SWIFT network, which has problems such as high fees and low efficiency. Realizing cross-border transfers through the Ripple protocol will greatly reduce the required processing fees, and statistical Ripple network fact settlement will greatly improve transaction processing efficiency. Ripple designed the Interledger Protocol (ILP) to implement cross-chain transactions: using multi-hop connectors to connect senders and receivers of cross-chain transactions, and to achieve the purpose of transaction needs through a set of transactions between senders, multi-hop connectors and receivers The effect achieved, while guaranteeing the atomicity of the execution of this group of transactions through a notary.
Ripple was established as early as 2012. It provides three solutions: xCurrent to assist banks in processing global payments, xRapid to provide liquidity for payment service providers, and xVia to assist ordinary companies to access the Ripple network for payments. Since 2014, financial institutions such as Fidor Bank, Cross River Bank, and CBW Bank have accessed the Ripple agreement. Now that the Ripple ecosystem is relatively mature, more and more financial institutions maintain cooperative relationships with Ripple, but since Ripple mainly solves the problem of cross-border transfers and ILP requires a notary, Ripple has made no more progress in cross-chain communication.
(2) PalletOne
PalletOne is a blockchain cross-chain platform.The goal of PalletOne is not only to design cross-chain protocols and realize value circulation of public chain cross-chain carriers, but also to achieve high concurrency, build high-performance "super public chains", and implement blocks Maximize the value of the chain network. The PalletOne architecture includes: an adapter to the underlying blockchain, distributed storage using DAG, a jury and mediation agency responsible for network security, a token abstraction layer, a virtual machine layer that guarantees the safe and stable operation of the contract, and provides software developers SDK, what PalletOne wants to achieve is a complete cross-chain ecology. PaalletOne cross-chain is implemented through a lightweight, high-level contract execution layer that is separated from the blockchain. The specific transaction is executed by the multi-signature of the jury, which is equivalent to the notary of the cross-chain transaction.
The PalletOne project concept was born in September 2017, and the project white paper and yellow book were released in May 2018. According to the team's Git update and announced development progress, at the end of September 2018, PalletOne completed the development of BTC and ETH adapters, and realized the cross-chain exchange of BTC and ETH based on PalletOne. Currently, the adapter is constantly being updated and improved. According to the development team's plan displayed on the official website, the test network will be launched in the fourth quarter of 2018, and the main network will be launched in the second quarter of 2019.
3.2.2 Sidechain Technology
Sidechain technology can be divided into narrow and broad categories according to its implementation and main uses. In the narrow sense, side chain technology refers to a new type of blockchain represented by BTC Relay, Sidechain, Drivechain, and RSK, which is based on anchoring some kind of original chain (mainly the Bitcoin blockchain). In a broad sense, the side chain technology also includes cross-chain infrastructure represented by Polkadot and Cosmos. Its main purpose is to solve the scalability problems, extensibility problems, and interoperability problems of the existing blockchain.
(1) BTC Relay
In 2016, the BTC Relay launched by the ConsenSys team used Ethereum smart contracts to connect the two most widely used blockchains-the Bitcoin blockchain and the Ethereum blockchain-in a decentralized manner to achieve Ether. Users verify Bitcoin transactions on the Ethereum blockchain. BTC Relay uses the Bitcoin block header provided by Relayers to build a lightweight version of the Bitcoin “blockchain” to verify the Bitcoin network activity.
BTC Relay has been widely recognized since its launch, and is considered to be the first cross-blockchain communication product. At the same time, it is entrusted with the desire to help improve the Ethereum infrastructure and help Ethereum complete greater innovation. In 2017, a decentralized platform EtherEx built on Ethereum cooperated with BTC Relay to introduce BTC transactions to EtherEx and explore the processing of cryptocurrencies not on Ethereum.
Because this project only implements a unidirectional cross-chain operation between the Ethereum blockchain and the Bitcoin blockchain, the application scope is relatively narrow. At the same time, Relayer needs to pay a certain fee for submitting the block header. Relayer is not active enough. The project was not widely accepted. According to the information on BTC Relay's official website, there is no active Relayer working now. The height of the last Bitcoin block that was synchronized was 501329. The block was packaged in December 2017, which means that the BTC Relay main network has Almost a year without work. There are currently no other valuable news updates for this project.
(2) Liquid
Liquid is a side chain anchored on the Bitcoin blockchain launched by Blockstream.Its goal is to help exchanges, brokers, and financial institutions and other organizations quickly and securely transfer large amounts of bitcoin, improve the efficiency of fund use and market liquidity. . Liquid, as the side chain of the Bitcoin blockchain, is anchored on the Bitcoin blockchain through the Sidechain two-way anchoring technology to achieve interoperability with the Bitcoin blockchain. The bottom layer of the liquid blockchain adopts a blockchain that is improved by using a strong alliance, and uses a strong alliance as the protocol adaptor between the main chain and the side chain to provide a more efficient cross-chain.
People have different views on Liquid: People who are not optimistic about Liquid believe that a strong alliance blockchain is a kind of damage to the Bitcoin blockchain. The flaws in the multi-signature technology will bring security risks. At the same time, they also believe that two-way anchoring technology It will affect the independent security of the blockchain; people who trust Liquid believe that the alliance of 23 exchanges is trustworthy, and efficient transactions can minimize spreads and increase liquidity.
Blockstream announced Liquid in 2016. After nearly two years of development research and internal testing, Blockstream demonstrated at the Consensus 2017 conference held in May 2017, and the Liquid blockchain entered the public beta phase. On September 27, 2018, the Liquid blockchain was officially launched, and the members participating in the listing were the 23 largest companies in the digital currency industry.
(3) RSK
RSK is an open source smart contract platform anchored on the Bitcoin blockchain through two-way anchoring technology. Its goal is to bring smart contracts into the Bitcoin system in an operable form, to achieve instant payment and high scalability, so that Add value and functionality to the Bitcoin ecosystem. Because the Bitcoin system currently does not support verification of external SPVs, the Bitcoin blockchain and root chain cannot achieve full trust and two-way anchoring without a third party, so RSK has introduced a federation consisting of multiple semi-trusted third parties. Federal members jointly determine the locking and release of Bitcoin. The specific anchoring scheme is: the sidechain side uses the sidechain anchoring scheme, and the bitcoin blockchain side uses the Drivichain anchoring combined with the federal voting scheme. RSK guarantees the network computing power through joint mining to ensure the security of the system.
Because RSK is not the competition chain of the Bitcoin blockchain, but the side chain anchored on the Bitcoin blockchain to improve the Bitcoin blockchain ecosystem, it has won the support of the Bitcoin community and miners. According to statistics, the RSK test network release is that 50% of Bitcoin miners have expressed willingness to carry out joint mining to support RSK, but at present the number of miners who maintain on the RSK mainnet is far below this percentage. For ordinary users, RSK's proposal will enable fast payment and add new features to Bitcoin, improving the user experience.
RSK Lab proposed RSK as early as 2015. In 2016, the RSK smart contract test network Turmeric was officially launched. At this time, most miners expressed support for RSK's joint mining. The RSK mainnet was officially launched at the end of 2017. On January 4, 2018, RSK dug up the initial block. At present, there are more than 880,000 blocks on the RSK mainnet, with a total of 16 nodes for mining and network maintenance, with an average of 33 blocks per block. Although there are fewer RSK mainnet nodes and fewer packaged transactions, it can be said that it is a relatively successful attempt at sidechain technology. The company is also actively developing supporting wallet tools.
(4) Cosmos
Unlike other cross-chain projects, Cosmos is not a side chain of a blockchain, but a network architecture that supports cross-chain transactions.The goal is not to solve the problems of a blockchain, but to solve the problem of digital currency in the zone. Blockchain systems have long had interoperability, scalability, and scalability issues. The Cosmos network includes multiple independent blockchains running on Tendermint Core. These independent blockchains are called "Zone". The first space on Cosmos is called "Cosmos Hub". The Cosmos Hub and each zone can communicate through the Inter-Blockchain Communication (IBC) protocol. It can be said that Cosmos uses the IBC protocol to implement the blockchain relay function. Specifically, the IBC protocol allows the blockchain to read and verify other blocks. Transactions in the chain.
Cosmos has a long-term goal and a huge vision. In order to ensure that the network constructed is sufficiently secure and the services provided are high enough, the development team has conducted thorough iterative tests during the software iteration. The Cosmos public test network gaia-1 was released in October 2017, and users can send and receive tokens on the Hub on this test network. In January 2018, gaia-2 was released, and the test network realized the dynamic node discovery function; 2018 4 Every month from August to August, some updates were made to continuously improve the test network functions, and at the same time, the corresponding new test network was launched. The current test network version is gaia-8001 and the SDK version is v0.24.1, as shown in Figure 1.
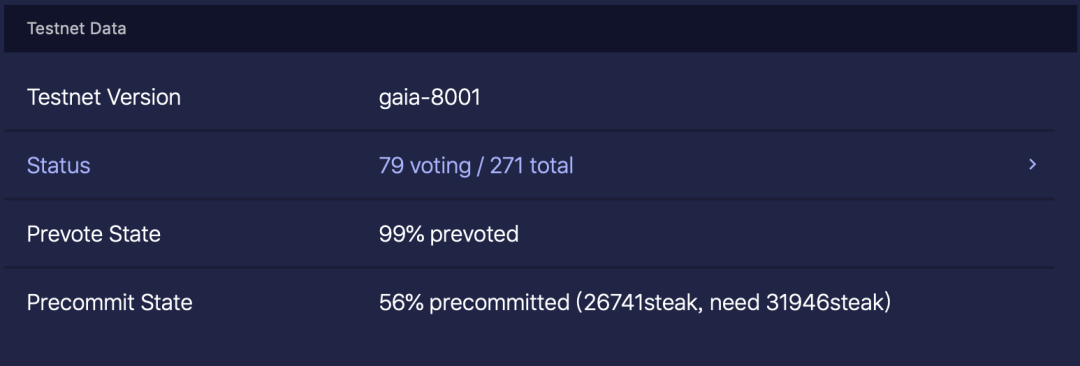
Figure 1 Cosmos test network information
It is understood that there are 7 main functions that need to be implemented before the launch of the Cosmos main network: handling fees, forfeiture of equity in the agreement, multi-signature function, ABC (Application Blockchain Interface) update, Gas pricing, and governance v2. The exact online time of the Internet is still uncertain.
(5) Polkadot
Polkadot is also a network structure that supports cross-chain transactions.The goal is to reconstruct the blockchain architecture, separate the normativeness and effectiveness of the blockchain consensus, and fundamentally solve the scalability and scalability of the blockchain system. problem. The difference between Polkadot and Cosmos is that the Cosmos network is a homogeneous system that must be given to Tendermint, while Polkadot is expected to build a heterogeneous multi-chain system. Polkadot is made up of a relay chain and several parallel chains. At the same time, the network nodes are divided into four roles according to the functions that the nodes perform in the network: collectors, fishermen, nominators, and validators. Among them, the verifier is responsible for the main work of network maintenance, and other roles assist and supervise the work of the verifier. The specific relationship is shown in Figure 2. The four roles work together to maintain the network, enabling secure and effective cross-chain transactions.
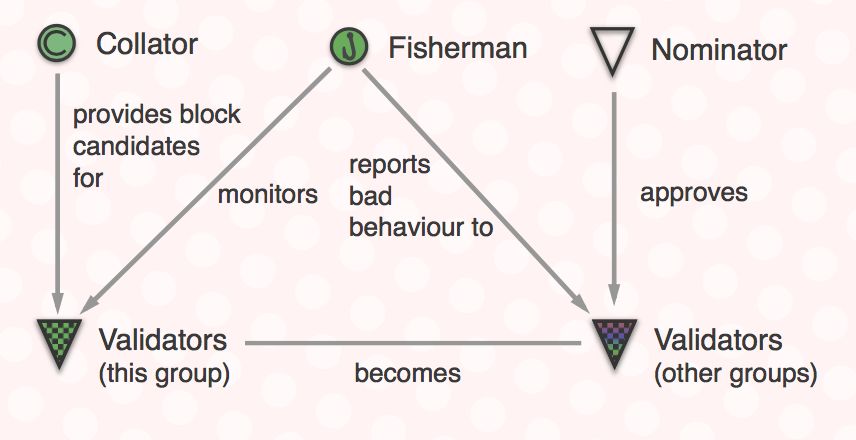
Figure 2 Polkadot character interaction
In order to better build the Polkadot ecosystem, the development team abstracted the Substrate framework during the development process. Using this framework can easily build a parallel chain that can directly access Polkadot. Of course, the framework can also be used for independent blockchains. Development. The Substrate framework has implemented functions such as consensus mechanism, block voting logic, P2P network, Wasm virtual machine, and native execution of smart contracts. At present, other teams have built blockchains based on Substrate, such as ChinaX in China.
Polkadot's progress is a little slower than Cosmos, and it is currently in the PoC-3 stage. Its first proof of concept has been able to verify the block and implement state transitions. It also implements functions such as sending Dot tokens through the test network. The Polkadot team plans to launch the mainnet in the third quarter of 2019.
3.2.3 hash lock technology
The basic idea of hash lock technology is that the two parties to the transaction maintain a trigger that sets an interoperation to ensure the atomicity of the two parties' operations. The typical representatives are the Lightning network and the Raiden Network. Both are typical applications of state channel technology.
(1) Lightning Network
Lightning Network is a typical application of state channels. It is a distributed network that realizes instant, high-capacity payments through smart contracts. Its purpose is to achieve secure off-chain transactions, but its core technology, hash lock technology, enables it to perform atomic cross-chain exchanges. However, in order to run atomic cross-chain exchanges, both blockchains that require cross-chain exchanges support Lightning Network. The two parties to the exchange have opened lightning payment channels on both blockchains to form a loop channel; the two parties to the exchange use the Hash Time Locking Contract (HTLC) to implement atomic swaps, specifically, the two parties to the exchange temporarily store the exchange assets in a temporary account, Through the same hash primitive and the set time difference, two "payment" transactions can be achieved at the same time or neither. Of course, not all cross-chain exchanges need to establish new channels, and they can also be achieved through existing middleman channels.
The Lightning Network was not originally used for cross-chain communication, but due to its technical characteristics, it can be well applied to cross-chain transactions. In November 2017, Lightning Network Lab completed the cross-chain exchange of Bitcoin to Litecoin, confirming the ability of Lightning Network's atomic-level cross-chain transactions. In early 2018, BitUN was officially launched. It defined Lightning Network 2.0 and built a digital currency clearing network in an attempt to achieve more efficient and secure cross-chain asset management.
(2) Lightning Network
Like the Lightning Network, the Lightning Network is also an application of the state channel, except that the Lightning Network is for Bitcoin, and the Lightning Network is an off-chain capacity expansion solution on Ethereum. The purpose is to use the off-chain state network to expand Ethereum's transaction capabilities. The basic principle is similar to Lightning Network, but the implementation is different: the payment channel of Thunderbolt Network is controlled by smart contracts instead of multi-signature addresses. Thunderbolt Networks can use smart contracts to achieve more complex exchange conditions.
In 2017, the Thunderbolt Networks team released an early version of the Raiden test version after the release of an earlier version on the Ethereum testnet. At the end of November 2017, µRaiden was officially launched on the Ethereum main chain and can support 1 million transactions per second. In March 2018, Liquidity.Network officially joined the Thunderbolt Network, as the latest Ethereum project, trying to transfer transactions from the world's second largest and most valuable blockchain to payment channels, thereby allowing the network to support being More adoption and use. In addition, Thunderbolt Networks has established cooperative relationships with Share & Change, Smart Mesh, Grid +, Tobalaba and other companies, and will explore applications in multiple fields.
(3) Blocknet
Blocknet is an inter-chain infrastructure that provides distributed applications and smart contracts, and its purpose is to achieve communication between different blockchains, making interoperation between different blockchain users and corresponding services possible. In simple terms, Blocknet is committed to building a "Blockchain Internet." In order to achieve this goal, Blocknet designed the corresponding distributed network architecture and protocol. Blocknet contains three core components: Xbridge-the inter-chain network overlay, Xname-the block chain, and Xchat-the P2P data transmission; implementation Monetized inter-chain services require three core infrastructure services: service discovery, inter-chain message transmission, and decentralized exchange. Infrastructure services are the orchestration of core components, as shown in the following figure.
Blocknet was introduced as early as 2014. What it wanted to achieve at the time was to provide a virtual currency to serve another virtual currency. On the basis of atomic exchange, it added functions such as order matching and transaction matching to achieve decentralization. Cross-chain currency exchange. After function expansion, it can be used to purchase services across chains. But progress has been slow, and less information has been revealed recently.
3.2.4 Distributed Private Key Control Technology
The distributed private key control technology aims to map various digital assets to a new blockchain through distributed private key generation and control technology, so as to achieve the free exchange of different digital assets on the same blockchain. Representatives include Fusion and Wanwei Chain.
(1) Fusion
Fusion is a crypto-financial application.The purpose is to build a set of blockchain infrastructure platforms to run crypto-finance applications. On this platform, value interoperability will be achieved through the free interaction of smart contracts, thereby achieving the "bank" effect. . Its core technology is distributed signature technology, through which users can map various digital assets it owns to the public blockchain built by Fusion, and the Fusion public blockchain that has mapped many digital assets can freely carry out different digital Exchange of assets and provide corresponding support when users apply for withdrawal. To put it simply, just as different blockchain users deposit different digital assets into the "bank", the free circulation of digital assets in the "bank" affects the user account balance, and the user's withdrawal from the "bank" is subject to the final account balance .
The Fusion project started in 2017, and the construction of the platform is expected to be completed in 2019. According to the planning of the development team, the first three quarters of 2018 should complete the joint planning work, core team building, core protocol development, smart browser, and core wallet development, and continue to improve the security and efficiency of the protocol. According to the plan, the team should have launched the test chain and the main chain in the second quarter of 2018, but now they can't check more related content and need to continue to track.
(2) Wanwei chain
The digital asset infrastructure platform that combines the three major features of asset cross-chain, privacy protection, and smart contracts of Wanwei Chain is similar to Fusion: to complete the link and value exchange of different blockchain networks in a decentralized manner, and to establish a A distributed future "bank". Its ultimate goal is to build a distributed digital asset financial infrastructure. Wanweichain completes the linking and value exchange of different blockchain ledgers in a distributed manner. It proposes a universal cross-chain protocol and a distributed ledger that records cross-chain transactions and intra-chain transactions. The public chain, private chain, and alliance chain can all access Wanwei Chain at low cost to realize the connection of different blockchain ledger and asset cross-ledger transfer. Any institution or individual can open its own business window in Wanwei Chain and provide digital asset-based deposit and loan, exchange, payment, settlement and other services. Through the guarantee of the blockchain-based infrastructure provided by Wanwei Chain, more people can enjoy more abundant financial services based on digital assets
The Wanweichain project was launched in 2016, and a proof of concept was carried out in the same year. In 2017, the balance completed the ICO. In November 2017, Wanwei Chain released the Alpha testnet and publicly convened volunteers to participate in the test in the community. At this time, the core development work of transaction privacy protection was completed, and some consensus algorithms and wallets were also developed. In December of the same year, Released Wanweichain Bate test network. In January 2018, the main chain of Wanwei Chain 1.0 was officially launched. This version of Wanwei Chain includes Ethereum's smart contract mechanism and Monero-style privacy transaction function. In July 2018, Wanwei Chain 2.0 docked with Ethereum. Officially launched, this version of Wanwei Chain has realized cross-chain functions, and the development team will further improve to achieve a good cross-chain ecology. The Wanlochain 3.0 Aloha test network was released in September 2018, and the Wanlochain 3.0 beta test network was released in October of the same year. The development team stated that the final realization of Wanlochain 3.0 will break the barriers between the Ethereum series of projects and the Bitcoin network project. The specific situation needs to continue to follow up.
3.2.5 Cross-chain technology comparison
The main problem of notary technology is the need to trust a specific group of notaries, which is contrary to the original intention of the blockchain design, and the trust issue will also bring a series of security issues. This may be the reason why there are fewer cross-chain projects other than using notary technology alone. However, the notary technology is used as a technical point in various cross-chain transaction schemes.For example, in the Rootstock (RSK) project, which is a side chain technology, due to the use of joint mining, the computing power of the previous RSK blockchain is likely to Less than half of Bitcoin's entire network computing power, in order to prevent other computing power from 51% attacks on the RSK blockchain, the block packaging of the RSK blockchain uses notary technology.
The side chain technology that anchors a specific blockchain is verified by SPV to verify the validity of cross-chain transactions. In theory, it supports cross-chain exchange and asset transfer of all blockchains. However, for each main chain, The combined design of the side chain implements relaying, which is complex and difficult to implement, and has poor scalability. The side chain technology that does not anchor a specific blockchain is based on the concept of side chain technology to establish a cross-chain infrastructure, which can solve many problems in the narrow side chain technology, but the implementation is complicated, and there are currently no real online projects to refer to.
The hash lock technology is an ideal solution to ensure the atomicity of cross-chain transactions. However, the application scope of the cross-chain solution using only the hash lock technology is relatively narrow and is limited to the field of cross-chain transfers. It cannot meet other cross-chain requirements. Like notary technology, hash lock technology can also be used in other cross-chain schemes to ensure the atomicity of cross-chain transactions.
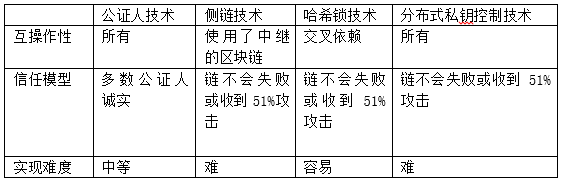
The multi-currency smart contract implemented by the distributed private key control technology that maps the assets of different blockchains to the same blockchain is currently implemented just like the hash lock technology, and it is only a simple asset exchange. Starting from the transaction, more complex cross-chain interoperation cannot be completed yet. If the design of multi-currency smart contracts cannot be further enhanced in the future, the application scope of distributed private key control technology will be far from the expected effect. Table 1 is a comparison of the current major cross-chain technologies.
Table 1 Comparison of cross-chain technologies
3.3 Blockchain Smart Contract
Smart contracts are programs that run on the blockchain and trigger execution through transactions. Smart contract research mainly includes contract coding, contract performance, contract security, and contract privacy issues.
3.3.1 Smart Contract Performance and Security
Loi Luu [ 32 ] et al. Studied the security issues of running Ethereum-based smart contracts in a cryptocurrency-like distributed network. By understanding the distributed semantics of the underlying architecture platform, there is a slight gap. Method, enumerating the possible vulnerabilities in the operation of the Ethereum smart contract, and building an execution tool called Oyente to discover potential security vulnerabilities. Stefano Bistarelli [ 33 ] and others have collected a large number of verified smart contracts written in Solidity language and analyzed their code; similar research has been done on the Solidity compiler to determine the important role that opcodes play in practice. Atzei, Bartoletti, and Cimoli provided an investigation of attacks on Ethereum smart contracts [ 34 ] , and they defined and classified common programming errors that could lead to different vulnerabilities. This research work provides useful guidance for programmers to avoid security issues caused by programmers' lack of knowledge of the blockchain. Delmolino et al. Proposed a step-by-step procedure for writing smart contracts [35 ] . Anderson [36] and others provided quantitative analysis of Ethereum blockchain transactions from August 2015 to April 2016. Their investigation focused on smart contracts, with a particular focus on zombie contracts. They performed a security analysis of the contract to check the use of unprotected commands (such as SUICIDE). They also checked the similarities in the protocol code and analyzed the reasons for the similarity in the smart contract code section. Maurice Herlihy [ 37 ] discussed the issue of smart contracts due to factors such as concurrency control. Bhargavan et al. [38 ] used formal methods to analyze and verify the correctness of smart contracts, while Bigi et al. [ 39 ] went further. Combining formal methods with game theory technology to verify smart contracts. In the article [ 40 ] , the author made a systematic mapping study; collected all research related to smart contracts from a technical perspective, and derived future research directions. Due to the immutability of the blockchain, smart contracts cannot be changed or terminated after deployment to the blockchain. In order to solve this problem, Marino et al. [41] proposed a set of standards that allow changes or termination of smart contracts. Current smart contracts are based on programming languages such as Solidity. In procedural languages, code is executed as a series of steps, so the programmer must specify what should be done and how. This makes the task of writing smart contracts in these languages both cumbersome and error-prone. To solve this problem, Idelberger et al. [ 42 ] suggested using a logic-based language instead of a procedural language. Some smart contracts require information from outside the blockchain. The problem is that the information provided by external sources cannot be trusted. To solve this problem, F. Zhang et al. [ 43 ] constructed a Town crier solution as a trusted third party between external and smart contracts, providing authenticated transmission data for smart contracts.
3.3.2 Optimization of smart contracts
Aiming at the problems of privacy, security, performance, and unified standards in smart contracts, with the advancement and breakthroughs in the research of blockchain technology, more and more scholars in China are also paying attention to the optimization research of smart contracts. For example, Wang Weiwei and others [ 44 ] analyzed and compared the implementation of existing smart contracts, proposed a formal definition method of contract-oriented smart contracts, and gave reference implementations. In the study of building smart contracts, [45 ] used domain-specific language (DSL) and blockchain technology to build a decentralized point-to-point distributed model to achieve the programmability of smart contracts and the credibility of the execution environment. In the application of blockchain technology, Literature [ 46 ] realized Fabric's cross-border remittance tracking platform, and detailed the smart contract's main structure and method-level authority control, which is a true combination of technology and application. In order to improve the robustness and resistance of smart contracts, Literature [ 47 ] clearly defined a smart contract framework based on secure multiparty computing (SMPC), a fair SMPC algorithm design for linear secret sharing, and a non-blocking information transfer interface technology. A smart contract model based on multi-party computing was introduced. By standardizing the SMPC-based smart contract execution process and language structure, the smart contract's secure execution was enhanced. Aiming at the unfriendly problem that most of the smart contracts on the market are oriented to developers and rely too much on development platforms and development technologies, [ 48 ] developed a smart contract platform that can access the contract network through the Android terminal. In order to facilitate the archival data recording and effective preservation, so that archival data cannot be tampered with, [ 49 ] realized the identity verification of digital archives and the determination of archival ownership through smart contracts and digital signature technology to achieve archival data based on blockchain. Protection and sharing methods. Reference [ 50 ] has defined a new operation code to represent byte compression, which can effectively save the storage space of smart contracts after deployment. In order to guarantee the privacy of smart contracts, in [5 1 ] , blind signature technology and improved PBFT algorithm are introduced to improve the privacy protection of smart contracts. For the management and search of smart contracts, article [52 ] introduced the idea of code classification to classify and manage smart contracts, and based on this, proposed a smart contract automatic classification system based on semantic embedded models and transaction information. Aiming at the study of the performance of the blockchain and the throughput of the blockchain, literature [53 ] proposed a trusted contract-based certification system based on smart contracts on the Ethereum platform, which improves the security and efficiency of data storage and guarantees data. Not to be tampered with and lost.
Overall, the research on smart contracts is still in its infancy, especially in terms of the optimization of smart contracts, and no effective method has yet been formed.
3.4 Blockchain Security Guarantee
Internationally, NEC European Laboratory, Cornell University, Romania, Barbis-Boyayi University, Münster University, Boston University, Hebrew University of Israel, Massachusetts Institute of Technology, National University of Singapore, Teams at the University of Newcastle in Australia, Princeton University in the United States, the Autonomous University of Barcelona in Spain, and the University of Edinburgh in the UK have conducted some research on blockchain security. These scholars mainly focus on the security and stability of blockchain technology from the perspectives of data security, network security, consensus security, and smart contract security. In China, the work of blockchain security is mainly reflected in the development of blockchain-related standards, and a series of related standards have been introduced. Blockchain standardization can open up application channels, prevent application risks, and improve application results. It plays an important role in solving the problem of blockchain security development and advancing blockchain security applications. Relevant standardization organizations, alliance associations, and research institutions in China have put blockchain standardization on the agenda, carried out a series of work such as organizational construction and standard pre-research, and have made certain progress.
3.4.1 Data security
The data storage structure of the blockchain determines the characteristics of the blockchain that are difficult to tamper with. It also objectively increases the risk of harmful information being chained, and the privacy protection of sensitive data after being chained.
(1) The problem of harmful information uploading
The difficult to tamper with the data of the blockchain makes it difficult to modify and delete the data on the blockchain through traditional methods, which increases the difficulty of supervising harmful information on the chain and presents new challenges for information management. Therefore, once harmful information such as violent terror and pornography is written into the blockchain, not only can it use its synchronization mechanism to spread rapidly, but it is also difficult to modify and delete it. Although it is theoretically possible to use attack methods to create hard forks, rollbacks, etc., the implementation is costly and difficult, which brings new challenges to information content management. In March 2018, German researchers found more than 274 links and pictures of child pornography websites in the Bitcoin blockchain. It was verified that malicious users could inject blocks by encoding harmful information into Bitcoin transaction information. Behavior in the chain.
For public chains, such as the Bitcoin blockchain, the response strategy is mainly to track the source of harmful information through the association relationship between Bitcoin addresses proposed by scholars such as Reid and Meiklejohn. For alliance chains or private chains, the response strategy is mainly to increase the audit mechanism and explore the balance between auditing illegal information on the chain and user privacy protection needs.
(2) Privacy data protection issues
The open source sharing protocol in the blockchain enables data to be recorded and stored simultaneously on all user sides. For attackers, they can obtain copies of data in more locations and analyze useful information such as blockchain applications, users, and network structures. For example, Bitcoin, one of the typical applications of the blockchain, every transaction will be publicly recorded on the blockchain ledger, and anyone can check it. Reid, Meiklejohn and other scholars have found that the association between input addresses, output addresses, and change addresses in historical transactions can infer the association between Bitcoin users. The application of blockchain, especially the financial industry, will pay more attention to privacy protection. Privacy issues have become one of the main guarantees for the implementation of blockchain applications.
Private data is stored off-chain, and part of the data that can be made public is stored on the distributed ledger. Data according to different privacy requirements are stored on different distributed ledgers. Private data is encrypted and protected, and only relevant parties can decrypt and view it. Use group signatures to anonymize identities and hide the identities of users on the blockchain.
3.4.2 Network Security
(1) P2P network security vulnerability
P2P networks provide a distributed, self-organizing connection mode for nodes in a peer-to-peer network environment, and lack mechanisms such as identity authentication, data verification, and network security management. Attackers can freely publish illegal content, spread worms, Trojans, viruses, and even implement distributed denial-of-service attacks (DDoS), routing attacks, etc., which are difficult to detect and spread quickly. Donet and other scholars have pointed out that weak connections and incorrect protocols will increase the propagation delay in IP networks and cause the blockchain to fork in some systems. Although the blockchain is a completely decentralized system, it is difficult to establish a uniform connection between nodes in practice. The research results of Gervais and other scholars show that attackers can prevent miners from mining by controlling multiple blockchain nodes, thereby gaining more profits.
P2P network security vulnerabilities are a system engineering, and network attacks such as DDoS are becoming more and more intelligent, which makes attacks caused by network security vulnerabilities difficult to cope with. You can increase the cost of an attacker by installing special security equipment such as DDoS firewalls to reduce the probability of such attacks.
(2) Network topology of nodes
The network topology of the nodes will create convenience for the attacker to find the attack target and carry out the attack. An attacker can monitor network topology by actively injecting packets or passively listening to data packets transmitted between routes. It is easy to obtain the routing information of the target node and control its neighbors to carry out the attack. Scholars such as Francisco have found that "eclipse attack" is a typical attack method in which attackers use the topology relationship between nodes to achieve network isolation. The basic idea is that the attacker controls the data transfer of the target node to and from the node through the network topology, restricts the target node's data interaction with the outside world, and even isolates the target node from the main blockchain network so that the target node can only receive the attacker. The transmitted message causes the block chain view saved by the target node to be inconsistent with the main network block chain view, which destroys local consistency. "Eclipse attacks" can be used as a basis for other attacks. When a phased blockchain fork race occurs in the network, the attacker uses a solar eclipse attack to force the target node to waste computing resources on an invalid blockchain. Attackers can also implement “eclipse attacks” on the nodes with superior computing power to achieve the separation of computing power, affect the distribution of mining rewards, reduce the effective computing power in the network, and further reduce the difficulty of attacks such as selfish mining and double payment.
By establishing a uniquely identifiable and verifiable digital identity, blockchain network users can reasonably set the number of peers, the connection time, the size of the address list, the update frequency, the update mechanism, the link selection mechanism, the anomaly detection mechanism, and so on. A platform providing blockchain services should have basic network boundary protection, network intrusion detection, and virus defense mechanisms.
3.4.3 Consensus Security
The consensus mechanism is an algorithm for blockchain transactions to reach a distributed consensus. It is used to make the blockchain reach a consistent state. It implements many copies that reside on each node of the network. The consensus mechanism should separate one state from the rest so that the state can be accepted by the entire network. The consensus mechanism is the key to ensuring the continuous operation and continuous development of the blockchain system. A good consensus mechanism helps improve the performance and efficiency of the blockchain system, provides strong security guarantees, supports complex application scenarios, promotes the expansion and extension of blockchain technology, and various typical blockchain consensus mechanisms For example, as shown in Table 2.
Table 2 Comparison of typical blockchain consensus mechanisms
(1) Double spend attack
In 2012, Ghassan and other scholars proposed a double-spend attack, which is a unique attack on the Bitcoin system. There are two types of attacks:
The first attack: the attacker uses a sum of money to transact with multiple objects at the same time. If these transaction objects complete the transaction without the transaction being recorded in the legal blockchain, the attacker achieves the purpose of double consumption or even multiple consumption. Although in the multiple transactions initiated by the attacker, only one transaction will eventually be considered legal and recorded in the blockchain, but the transaction object has completed the transaction (such as the goods purchased by the attacker have been sent to the attacker), and the attack Authors have benefited from this attack.
The second attack: the attacker uses his own computing power to launch a double-spend attack. The attacker uses the same amount to conduct transactions with two transaction objects at the same time, such as transaction A and transaction B. One transaction A was confirmed and recorded in the blockchain, so that transaction A was completed. Because the attacker has powerful computing power, he records transaction B in a private blockchain and digs out a chain longer than the legal link, prompting transaction B to be confirmed and to complete transaction B.
Of the double cost attacks, the second type of attack is more harmful. This is because, for the first type of attack, the trader only needs to confirm the transaction more than 6 times before completing the transaction to avoid it; for the second type of attack, because the attacker adds "illegal" transactions to the private blockchain, And in the end, this chain was deemed legal, which was equivalent to changing the transaction in the blockchain (changing transaction A to transaction B). This kind of tampering with blockchain data severely affected the blockchain. Completeness.
(2) 51% attack
In the PoW consensus algorithm, the system allows multiple fork chains at the same time. In the design concept of PoW, there is a longest valid principle: "No matter what time, the longest chain will be considered the main chain with the most work. Satoshi Nakamoto mentioned 51% attacks when he invented Bitcoin. A 51% attack means that if the attacker has more than half the capacity of the entire network, it has the ability to overthrow the original confirmed transaction, recalculate the confirmed block, cause the block to fork, complete the double spend, and obtain interest. The motivation for an attacker to carry out a 51% hashrate attack is to complete the double spend on their own transactions and to defraud the recipients of the transactions. Second, they can control the generation process of the longest chain to obtain block rewards. The 51% hashrate attack was once considered difficult to reach. However, with the emergence of mining pools, a mining pool called GHash.IO once had 51% of the computing power of the entire network in June 2014; therefore, the threat of 51% computing power attacks always exists and is likely to occur.
(3) Selfish mining attacks
Eyal and Sirer scholars believe that if a group of selfish miners (mining pools) exist and adopt a selfish mining strategy and succeed, it may invalidate the work of honest miners. This selfish mining attack manifests itself as follows: A malicious mining pool decides not to publish the blocks it finds, and then creates a fork, so there is a public chain maintained by honest miners and a private fork of the malicious mining pool in the network. Malicious mining The pool continues to mine under this private fork. When the private fork is longer than the public chain, the malicious mining pool will release the private fork. Since the fork is the longest chain in the current network, it will be honest. The miner determines that it is a legal chain, so the original public chain and the honest data contained in it will be discarded. The results of the study show that under normal circumstances, selfish mining strategies used by malicious mining pools will yield more benefits.
(4) Block attack
Courtois and Bahack scholars have analyzed actual examples and found that malicious miners can also profit from "block attack". In the block-holding attack, some malicious members who have joined the joint mining pool do not distribute any mined blocks, thereby reducing the revenue of the mining pool and wasting the computing power provided by other members. This kind of attack is also called "Sabotage" attack. Generally, malicious miners do not have any gain, but the main hazard of "block attack" is to waste computing power of the mining pool and reduce mining pool revenue.
From the above analysis, it can be seen that the “block attack” will cause both the miner and the mining pool to suffer different degrees of loss. Compared to the very low cost of the miner, the loss of the mining pool is relatively large. From the perspective of benefits, most of the "blocking attacks" are competing mining pools, and generally there are fewer miners. Although the "block attack" is theoretically true, it is actually difficult to implement the attack. This is because the cost of the “block attack” is very high, which is similar to the 51% attack of Bitcoin, that is, the necessary foundation for launching this attack is to have a huge computing power, so basically the “block attack” is in reality. Rarely.
(5) Bribery attack
Chepurnoy scholars propose that attackers can encourage miners to mine on transaction chains that include attackers through high rewards. First, the attacker purchases a certain product or service, and the merchant begins to wait for the network to confirm the transaction. If the attacker first declares on the network at this time, he will reward the relatively longest main chain that does not include the transaction. When the chain is long enough, the attacker starts to release larger rewards, rewarding the miners who are mining in the chain containing the transaction; when the six confirmations are reached, the reward is abandoned; and finally, when the reward is in hand, the attacker's choice is abandoned. Chain. Therefore, as long as the cost of the bribery attack is less than the reward or service fee, the attack is successful. It is worth noting that this attack is basically invalid for the PoW mechanism, because in the PoW mechanism, bribery attacks need to bribe most miners, so the cost is extremely high and difficult to achieve.
3.4.4 Smart Contract Security
The smart contract is the core of the contract layer. It is a digital protocol that can be executed automatically. It contains the relevant code and data sets and is deployed on the blockchain. It is also a computer program that can be automatically executed according to preset contract terms. Smart contracts were first proposed by scholar Nick Szabo, and later redefined by Ethereum, and a complete development architecture was established. Most of the objects operated by smart contracts are digital assets, so smart contracts are highly risky. This section deals with security issues and solutions from writing security and operational safety.
(1) Writing security
Focus on both text security and code security of smart contracts. Text security is the first step to the stable operation of smart contracts. Before writing a smart contract, smart contract developers need to design a complete contract text based on actual functions to avoid abnormal smart contract execution or even deadlocks caused by contract text errors. Code security requires smart contract developers to use a safe and mature language and write in strict accordance with the contract text to ensure that the contract code is consistent with the contract text, and there are no loopholes after the code is compiled.
(2) Operational safety
The security protection mechanism involved in the actual operation of smart contracts is an important goal for the safe operation of smart contracts in untrusted blockchain environments. Operational security means that once a smart contract has a loophole or even an attack during its execution, it will not affect the local system equipment of the node, nor will it cause other contracts or programs that call the contract to perform abnormally, including modularization and isolated operation. Modularity requires standardized management of smart contracts, has the characteristics of high cohesion and low coupling, is portable, and can realize the secure call of smart contracts through interfaces. The abnormal results after the attack will not continue to spread through the way of contract invocation, ensuring the availability of smart contracts. Isolation operation requires smart contracts to run in isolated environments such as virtual machines. It cannot run directly on the local systems of nodes participating in the blockchain to prevent attacks on local operating systems running smart contracts.
(3) Security holes in virtual machines
At present, most smart contract languages are virtual machine languages. The smart contracts implemented by them need to run in a specific language virtual machine. The security of the virtual machine itself can ensure the correctness of the smart contract operation results on the one hand, and it can also Prevent smart contracts running on it from being attacked by other malicious contracts. Considering that a large number of nodes in a blockchain system often deploy virtual machines of the same version or similar implementation, the impact of a single virtual machine vulnerability is likely to affect the entire system.
3.4.5 Safety related standards
In terms of cryptographic algorithms and signature standards, China has a good research foundation. According to statistics from the CCID Blockchain Research Institute, as of the end of June 2018, China has introduced SM2 elliptical cryptographic algorithms, SM3 hash algorithms, and SM9 identification cryptographic algorithms. 19 signature algorithms including 19 cryptographic algorithms and digital signature schemes, minimum interoperability specifications for PKI components, and specifications for electronic signature formats. In the development of the underlying framework technology standards, related work has been carried out in an orderly manner. At present, there are some preliminary results in the aspects of basic blockchain standards, credible and interoperable standards, process and method standards, such as May 2017, China Electronic Technology Standardization. The Institute released the blockchain standard "Blockchain and Distributed Ledger Technical Reference Architecture", which detailed the concept of the blockchain, its main players, and core functional components. In December 2017, the China Blockchain Ecology Alliance released the "China Blockchain Ecology Alliance Group Standard Management Measures (Trial)". In March 2018, the Ministry of Industry and Information Technology announced the establishment of the National Blockchain and Distributed Accounting Standardization Technical Committee. In April 2018, the China Blockchain Ecological Alliance announced the establishment of the Standard Drafting Working Group for "General Technical Requirements for Blockchain Platforms (tentative name)" and "General Requirements for Blockchain Enterprise Service Capabilities (tentative name)" to promote standards Development work, these standards all describe the security of the blockchain. In April 2018, the National Information Security Standardization Technical Committee conducted a review of the project "Research on Blockchain Security Technology Standards". According to the CCID Blockchain Research Institute, as of June 2018, there are more than 20 underlying platform evaluation standards in the research state.
3.5 Blockchain supervision and privacy protection
3.5.1 Blockchain supervision
At home and abroad, the research on the supervisability of blockchain is mainly based on the supervision of public chains, and it is mainly aimed at digital currencies such as Bitcoin and Ethereum. Digital currency, as the most typical application in the blockchain, has great market value and potential. Therefore, the regulation of digital currencies has attracted widespread attention from domestic and foreign government agencies and researchers. This section analyzes the current state of blockchain supervision from the policy and technical perspectives.
(1) Policy perspective
For anonymous digital currencies represented by Bitcoin, many countries have formulated stricter bans to prevent related illegal activities. In 2015, the US Commodity Futures Commission did not recognize the monetary status of digital cryptocurrencies such as Bitcoin, but defined them as commodities. Countries such as Japan and Canada have made some Bitcoin transactions illegal. In 2016, American blockchain company R3 launched a blockchain alliance of the same name, including more than 80 banks, financial institutions and regulators such as Goldman Sachs and HSBC. R3's latest research report points out that financial institutions need an autonomous and controllable system, which must be visible to supervision on the basis of ensuring transaction privacy. In 2018, the EU plans to release specific drafts such as blockchain technology standards and crowdfunding regulations to establish common standards for blockchain technology.
On January 10, 2019, the National Internet Information Office issued the “ Regulations on the Management of Blockchain Information Services '', requiring blockchain information service providers to set up a regulatory platform in advance; find out the source of problems in a timely manner, handle illegal information and control information Develop and eliminate adverse effects; trace back to the source of the violations in accordance with the regulatory system afterwards. Due to the self-organization and cross-border characteristics of public blockchains such as Bitcoin and Ethereum, it is difficult to regulate these public blockchains from a legal level.
(2) Technical perspective
Regarding blockchain technology, all countries focus on regulation and supervision. Foreign researchers have conducted research on the anonymity of digital currencies led by Bitcoin and privacy protection of the blockchain, and have achieved many research results. These studies provide some technical guidance and support for the realization of blockchain supervision. The anonymity of the public chain account allows everyone to generate a large number of account addresses, and the generation of these addresses does not need to provide content related to personal information. However, researchers from universities such as the University of Luxembourg pointed out that attackers can use publicly available background knowledge on the network, or monitor transaction propagation information on the Bitcoin network layer, to find the identity of the user behind the address and its corresponding IP address. Researchers at University College London have proposed a heuristic clustering method based on the anonymous digital currency Zcash, and taking Shadow Broker as an example, they introduced how to use the above-mentioned technology and combine public information on the Internet to achieve supervision of illegal and criminal acts in Zcash. . The United Kingdom, Singapore, Japan and Canada have promoted regulatory sandboxes to prevent and control blockchain risks to a certain extent.
3.5.2 Blockchain privacy protection
According to the classification of privacy protection objects, it can be divided into three categories: network layer privacy protection, transaction layer privacy protection and application layer privacy protection. The privacy protection of the network layer covers the process of data transmission in the network, including the blockchain node setting mode, the node communication mechanism, and the protocol mechanism for data transmission. The privacy protection of the transaction layer includes the data generation, verification, In the entire process of storage and use, the focus of privacy protection at the transaction layer is to meet the basic consensus mechanism of the blockchain and the constant storage of data, to hide the data information and the knowledge behind the data as much as possible to prevent attackers from analyzing the block data. Extract user portraits; privacy protection scenarios at the application layer, including the process of blockchain data being used by external applications, etc. The process of blockchain being used externally threatens to leak transaction privacy and identity privacy. Therefore, the application layer privacy protection side The emphasis includes improving the security awareness of users and improving the security protection level of blockchain service providers, such as reasonable public and private key preservation, and building a vulnerability-free blockchain service.
(1) Privacy protection mechanism at the network layer
By analyzing the packet data and attack methods at the network layer, it can be concluded that the attacker mainly collects transaction privacy and identity privacy by listening to network layer information. Therefore, the focus of the defense mechanism at the network layer is to increase the difficulty for the attacker to collect data at the network layer, so that the attacker cannot extract useful information from the network layer. The existing defense mechanisms can be divided into three categories:
1) Restrict network access. Authorize and control the nodes in the blockchain. Unauthorized nodes cannot access the network and cannot obtain transaction information and block information. This will fundamentally increase the difficulty of network layer attacks. However, this method needs to modify the operating mechanism of the blockchain itself. At present, it is mainly used in the architecture of private chains or alliance chains. For example, the architecture of the super ledger alliance chain is a node access mechanism that requires CA certification, while in the public chain, Well-known blockchain projects such as Ethereum and Bitcoin are not suitable for network restrictions in the form of identity authentication.
2) Detection and masking of malicious nodes. The method of restricting access is not suitable for public chain systems. In the public chain architecture, nodes cannot be directly restricted from accessing the network, but a detection and sampling mechanism can be adopted to detect malicious nodes and add them to the blacklist to prevent malicious nodes from continuing to collect sensitive information. information. Researchers have proposed a malicious node detection method based on behavior pattern clustering, which can quickly locate malicious nodes and eliminate the hidden danger of privacy leakage caused by malicious nodes.
3) Data confusion. In order to prevent attackers from obtaining identity and privacy information by discovering the network topology, some researchers have proposed that the blockchain can be run on a network with privacy protection features to ensure that it is difficult for the attacker to find the true IP of the sender and therefore cannot be analyzed at the network level. User behavior and geographic location.
(2) Privacy protection mechanism at transaction level
By analyzing the attack method of the transaction layer, it can be obtained that the attacker mainly obtains the private information by analyzing the public blockchain transaction data. Therefore, the focus of the transaction layer protection mechanism is to prevent malicious nodes from obtaining accurate transaction data, or to limit their inability to analyze and obtain valuable information in a small amount of data, on the basis of satisfying the normal operation of the blockchain. At present, academic researchers have proposed a variety of privacy protection schemes for the transaction layer. Here, we classify different protection mechanisms into three main categories according to the classification method for privacy protection of distributed databases:
1) Data storage is distorted. When data is stored, by obfuscating part of the data of the transaction content, the attacker cannot obtain accurate data, which increases the difficulty of analysis. Difficulties of this scheme obfuscate the efficiency of the method, and must ensure that the attacker cannot discover the transaction relationship between different addresses without damaging the transaction result.
2) Data encryption. By encrypting the transaction information, it is impossible for the attacker to obtain specific transaction information, and thus analysis cannot be performed. The difficulty of this solution is that at the same time as the encryption is implemented, the original verification mechanism must not be affected, such as how to ensure that the transaction information of both parties can be confirmed and verified by miners or other personnel when the encrypted data is stored on the chain.
3) Restricted distribution. By publishing small or no transaction data, the amount of information that an attacker can obtain is reduced, thereby increasing the difficulty of the attack. The difficulty of this method lies in how to ensure that the integrity and consistency of the data itself are not destroyed while limiting the distribution.
(3) Application-level privacy protection mechanism
By analyzing the attack methods at the application level, it can be seen that the attackers mainly use user irregular operations and loopholes of blockchain service providers to collect transaction privacy and identity privacy. Therefore, the focus of the application-layer defense mechanism is to improve protection capabilities from the user's perspective. There are two types of defense methods that users can use:
1) Introduce privacy protection schemes in blockchain applications. Bitcoin is the first application of blockchain technology in the digital currency field, and it has obvious defects in privacy protection. Attackers can analyze user identity from both the transaction and network levels. In this context, many currencies with better privacy protection have appeared, such as Zcash. Zcash is currently the best digital currency for privacy protection. By using zk-SNARKs (simple, non-interactive zero-knowledge proof) technology, it can hide the sender and receiver of blockchain transactions under the conditions of verification and consensus mechanisms. There are different levels of concealment schemes in the design of the party and even the transaction amount. The highest-level scheme can ensure that the identity of the recipient is not visible, and that the identity of the recipient is not trusted, while hiding the interactive amount. The new type of digital currency uses cryptography to protect transaction data. Compared with Bitcoin, it can better protect users' identity privacy and transaction privacy.
2) Use a blockchain program with a privacy protection mechanism. Different blockchain programs have different characteristics in terms of privacy protection, and need to adopt targeted protection methods. Taking Bitcoin as an example, cold wallets can effectively prevent hackers by keeping secret keys offline, but there may be security risks caused by the loss and theft of storage media. The key to privacy protection is to protect the security of storage media. Multi-backup, encrypted storage and other mechanisms are used to protect the security of storage media. At the same time, users need to be more aware of application-level security operations, such as involuntary authorization, offline storage, and inadvertent exposure of private keys. Applications should also not collect user privacy information.
3.6 Application of Blockchain Technology
The application of blockchain technology is mainly manifested in the financial industry, supply chain management, the Internet of Things, copyright protection, and the medical industry. The current state of international research on the application of blockchain technology shows a trend of mainly large traditional companies and supplemented by start-ups. Large companies lay out entire ecological chains and basic platforms. All are involved, and small companies focus on the specific application of an industry and cut into the blockchain field from different angles. Traditional enterprises and start-ups are working in both directions to continuously promote the widespread popularity and accelerated integration of blockchain in the industry.
3.6.1 Financial industry
In the financial field, blockchain has been applied to business models such as equity crowdfunding, P2P network lending, and Internet insurance. Securities and banking business are also important application areas of blockchain. Traditional securities transactions need to be coordinated by central institutions such as central settlement institutions, banks, securities companies, and exchanges. Blockchain is used to automate smart contracts and programmable features. It can greatly reduce costs and improve efficiency, avoid tedious centralized clearing and delivery processes, and realize convenient and efficient financial product transactions. In order to promote the development of blockchain technology and its applications, various types of blockchain industry alliances have emerged. The most influential of these is the R3 Blockchain Alliance, which brings together more than 40 of the world's leading financial institutions, including Bank of America, Citibank, Morgan Stanley Investment Corporation, Deutsche Bank and Barclays Bank [ 61 ] .
Barclays Bank and an Israeli company completed the world's first blockchain-based transaction, which guaranteed the export of approximately $ 100,000 worth of cheese and butter products from the Irish company Ornua to the Seychelles Trading Company. The transaction was completed on a platform set up by Barclays bank partner Wave. Using blockchain technology, the processing time of a transaction can be reduced from 7-10 days to 4 hours.
The United Bank of Switzerland (UBS) also plans to establish a trade finance system that uses distributed ledgers to simplify global import and export trade. In current large-scale transactions, when the product is still in transit, the buyer's bank can use credit to troubleshoot the seller's credit risk. Blockchain technology can program this process into smart contracts, reducing credit processing time and reducing operational risks.
3.6.2 Supply Chain Management
The supply chain consists of multiple nodes. During its operation, a large amount of information needs to be exchanged between different nodes. The data generated during the operation of the supply chain is scattered and stored in the private systems of each node, which cannot guarantee the openness and transparency of the data. This will lead to multiple problems: ① node information cannot be shared, causing upstream nodes to maintain excessive inventory to deal with downstream nodes Demand greatly increases production, inventory management and marketing risks, otherwise it may lead to increased supplier risks; ② Poor information flow causes nodes in the supply chain to be unable to grasp the relevant situation in the first place, which affects the efficiency of the supply chain; ③ When there are disputes in various nodes of the supply chain, the low traceability of production information will lead to a significant increase in the difficulties encountered in the investigation and accountability process; ④ financing difficulties faced by small and medium logistics companies.
The blockchain can keep the information in the supply chain interoperable, and each member node can grasp the relevant situation at the first time, thereby improving the overall efficiency of the supply chain management. At the same time, each node can obtain accurate transaction information. All member nodes are the owners of all information in the supply chain. On this basis, production activities can be conducted to reduce supplier risks and improve the stability of the supply chain. The traceability and non-tamperability of the blockchain can not only ensure the accuracy of the data, but also the traceability of the transaction. Blockchain can solve the problem of information asymmetry, improve the credit evaluation system, and help small and medium-sized logistics companies to get out of the difficult financing situation [ 57 ] .
With the promotion of governments and related companies in various countries, many blockchain applications in the field of logistics supply chain have been carried out. IBM uses blockchain technology to track the location of trucks and the origin of goods to increase the transparency of the process. It uses IBM blockchain technology and IBM Watson to track the origin and location of trucks and their goods. The IBM blockchain technology solution records Processing cargo transactions and information, IoT sensors will track the journey of the cargo, as well as the space available on the truck, and record this data on all relevant aspects of the block. This blockchain technology solution is integrated with the IBM Watson IoT system to check factors such as weather and temperature to estimate itinerary and estimated delivery time [ 59 ] .
Alibaba, IBM and other core R & D teams from 9 core countries around the world first proposed the concept and concept of Blockchain-As-A-Service. Its product VeChain is dedicated to tracking and management of freight assets. The solutions provided by the logistics industry use blockchain technology and IoT technology. In the key aspects of logistics, each participant collects key data and deposits it on VeChainThor Blockchain. This solution supports the accurate dimension of material management to each item, records the information and flow of each item, and provides the possibility for new logistics and business models. In addition, according to the certificate information on the blockchain, various digital value-added services can also be provided [ 73 ] .
Nestlé cooperates with the blockchain platform OpenSC to launch a new blockchain supply chain tracking pilot. Nestlé will cooperate with the blockchain platform OpenSC to jointly develop a distributed ledger system. The project will first track milk from New Zealand farms to Nestlé in the Middle East, and then expand to American palm oil production. Collecting data for each step in the value chain is recorded on an open platform, providing consumers with independently verifiable data and promoting market transparency. At the same time, this mechanism will improve food safety and improve quality control [ 75 ] .
3.6.3 Internet of Things
Many internationally renowned companies such as IBM have invested massive resources in the field of Internet of Things, and blockchain technology is used to solve some of these core problems. The traditional centralization mechanism is inefficient or unavailable for IoT devices with a potential number of tens of billions. In solving the problem of trust between nodes, a centralized solution is not realistic. Blockchain technology provides a solution for creating a consensus network without relying on a single node. Blockchain-based IoT applications, each IoT device can manage itself without manual maintenance. As long as the IoT device still exists, the life cycle of the entire network can be long, and the operating overhead can be significantly reduced. For example, in the smart home, all the connected devices of the smart home can automatically perform activities with other devices or the outside world. Only telegrams can control electricity charges by adjusting the amount of power used and the frequency of use [ 57 ] .
Many domestic enterprises have carried out industrial applications of the integration of the Internet of Things and the blockchain, such as in fisheries, food traceability, energy and other fields, indicating that the blockchain as a basic technology for the application of the Internet of Things has been widely recognized. For example, in the field of fisheries, Qingyutang Company uses the Internet of Things and blockchain technology to help farmers monitor water quality, reduce risks in the cultivation process, improve production efficiency, and realize agricultural science and technology credit loans, agricultural technology insurance, supply chain traceability, agricultural products. Traceability and brand marketing. In the field of food safety traceability, the Food Safety Blockchain Lab Akte is committed to creating a food anti-counterfeiting traceability ecology based on the Internet of Things and blockchain technology. By opening the information collection of the intelligent terminal of the Internet of Things and the data link of the blockchain, Food traceability and authentic information.
Based on the TBaaS basic platform, Tencent has taken the lead in proposing multiple application cases in the field of Internet of Things, such as smart manufacturing, smart grid and so on. In response to the pain points of the intelligent manufacturing industry, the combination of blockchain and the Internet of Things makes smart devices manage in a more secure and reliable form, and achieves the advanced goals of the Internet of Things, namely the settlement of payments and expenses, forming a network of value circulation.
3.6.4 Copyright protection
Internet copyright infringement events, mainly "Visual China", have aroused public concern, and Internet copyright protection has become the focus of everyone's attention. The amount of online media and self-media produced massive amounts of content every day. Then, how to protect the copyright of the creator, how to prove that the work is his own, and how to authorize others to use his work legally, these are difficult problems to solve [ 63 ] .
From the current point of view, the biggest difficulty in network copyright protection lies in the difficulty for users to obtain evidence, the high cost of evidence, and the long period of evidence collection, which is one of the pain points that hinder the development of network copyright protection. Based on these common problems in network rights protection, Huazhi Broadcom has designed and launched a self-developed network rights protection tool "Copyright Treasure". Based on the development of Biyuanchain, blockchain technology is used in the two business processes of self-certification of original news (original on-chain) and acquisition of infringement evidence (on-chain evidence) to ensure that users obtain evidence in a timely manner when network infringement occurs, Fix the evidence, and solve the difficult, expensive and long cycle of obtaining evidence.
Microsoft and Ernst & Young, a well-known international consulting firm, jointly launched a copyright-protected blockchain tool that uses blockchain technology to collect royalties for authors, software developers, and other creative producers. The project aims to simplify the current process of tracking and collecting royalties. The scale, complexity and number of digital rights and royalty transactions make this the perfect application scenario for blockchain technology. The blockchain can handle every special contract between the digital copyright holder and the licensor, and can provide participants with an auditing system in a scalable and efficient manner [71 ] .
3.6.5 Medical industry
At present, there is no uniform standard for data collection in the field of medical data, and a complete portrait of a patient cannot be formed. The pressure on network security is high, and the cost of obtaining information is reduced. Data classification is vague and lacks value data levels. The medical data industry is fully able to take advantage of the advantages of blockchain technology to bring inaccurate and differentially affected medical data records to the chain [ 78 ] .
Around April 2017, IBM launched its own blockchain-as-a-service BaaS, which focuses on medical and other aspects. In January 2019, IBM announced a new collaboration with Aetna, Anthem, HCSC (Health Care Service Corporation) and PNC Bank to use blockchain technology to design and build networks to increase transparency and interoperability in the healthcare industry [ 58 ] . The purpose of this collaboration is to create an inclusive blockchain network that enables most members of the medical ecosystem to benefit from a highly secure shared environment [ 80 ] .
On August 17, 2018, Alibaba Health and Changzhou cooperated with the "Medical Alliance + Blockchain" pilot project. This project is the first domestic application based on medical scenarios. It uses blockchain technology and is applied to the underlying technical architecture system of Changzhou Medical Consortium. It has achieved secure and controllable data interconnection between some local medical institutions. Use low-cost and high-security methods to solve the "information island" and data security problems that have long plagued medical institutions [ 84-85 ] . At present, the project has achieved certain results. Take grading diagnosis and medical treatment as an example. Residents take a physical examination at the nearest hospital. Through the analysis of the medical examination report on the blockchain, they are screened for patients with high risk of cardiovascular and cerebrovascular chronic diseases. Community doctors can use the blockchain to authorize and circulate cases to higher-level hospitals. Doctors at higher-level hospitals can quickly understand the patient's past medical history and physical examination information after being authorized, and patients do not need to perform unnecessary secondary basic checks. To improve efficiency and reduce costs.
4. Development Trends and Prospects
The blockchain has been applied to many fields at present to solve some practical problems and ensure that the data on the chain is tamper-proof and traceable. However, some problems in the blockchain itself still need to be considered, such as performance bottlenecks, data storage, and resource consumption. For different application scenarios, different blockchain architectures and business models need to be designed to meet the needs of the current scenario, helping the blockchain to play a role in various vertical industries.
4.1 Scalability
Although the current domestic and foreign research has made a lot of efforts in the scalability of the blockchain, the existing performance optimization schemes have certain limitations in improving the performance of the blockchain, which makes the large-scale commercial application of the blockchain relatively difficult. Great distance.
(1) The software-hardware integrated blockchain scalable architecture remains to be studied. Most of the existing researches have improved the scalability of the blockchain from the aspects of data structure, transmission protocol, consensus layer, and application layer. Building a software-hardware integrated system architecture and improving blockchain scalability from the perspective of software-hardware collaborative innovation remains to be studied.
(2) The actual large-scale application of fragmentation technology needs to be improved. The sharding technology makes it possible for the blockchain to process more and more transactions as the network grows in scale. In theory, sharding technology can realize the large-scale expansion of the processing capacity of the blockchain system, which is an important direction to improve the scalability of the blockchain. However, existing sharding technologies such as network sharding, transaction sharding, and state sharding are still in their infancy, and they have security, data validity, and availability issues. For example, network sharding makes the computing power of a single shard lower than that of the entire network, and is vulnerable to double payment or witch attacks. For UTXO data model, transaction sharding is likely to cause cross-slice communication. In extreme cases, all transactions in a single shard. All transactions are cross-slice, which makes the overall performance of the system lower than before sharding. State sharding can easily lead to data validity and availability problems because of verifying the state of some nodes. To solve these problems, existing research has proposed some solutions in these aspects, but there is still a certain distance from large-scale applications in terms of quantization of shard scale, complexity of on-chip communication, atomicity and performance of cross-segment communication, and further research is needed. the study.
(3) The collaboration between on-chain capacity expansion and off-chain capacity expansion needs to be deepened. On-chain expansion and off-chain expansion each have certain limitations. Capacity expansion on the chain enables more transactions per block of unit time by changing the underlying structure of the blockchain. However, it is easy to exacerbate risks such as blockchain centralization and security attacks; while the off-chain expansion does not require changes to the underlying structure of the blockchain. By isolating off-chain settlement from on-chain settlement, it guarantees security and a certain degree of decentralization At the same time, it effectively improves the scalability of the blockchain. However, they face problems such as channel routing, node offline, and margin lock. According to the transaction requirements of different quotas, the impact of on-chain capacity expansion and off-chain capacity expansion on the degree of decentralization, security, and scalability needs further research.
4.2 Cross-chain communication technology
The development of future cross-chain technology research has the following trends:
(1) Cross-chain will become an irresistible trend. This is analogous to the development of the Internet. The urgent need for information interaction connects each independent local area network into a global Internet, the Internet. Similarly, the urgent need for value interconnection will prompt the current "circulation within the value alliance" composed of different blockchains to transform into "social circulation".
(2) Isomorphic cross-chain appeals. Cross-chain communication between blockchains with consistent underlying architecture is relatively simple compared to heterogeneous cross-chain. At this stage, Cosmos is mainly concerned with isomorphic cross-chain communication. At present, the Cosmos Hub has begun preliminary public testing, and multiple Cosmos Zones are also in the development process. It is expected that in the near future, a preliminary available cross-chain system will be built. Although homogeneous cross-chain has great limitations in compatibility and other aspects, related work can also be regarded as an important progress in cross-chain technology.
(3) Heterogeneous cross-chain will be realized. Bitcoin and Ethereum are currently the two most influential blockchains. The former is the earliest and highest market value blockchain; the latter has integrated thousands of applications provided by developers around the world. If a cross-chain solution wishes to gain global recognition, it must be compatible with these two different types of blockchains. Therefore, it is believed that after the implementation of isomorphic cross-chain, more research will be invested in heterogeneous cross-chain, which will open up different value circulation systems and better serve the economy and society.
4.3 Blockchain Smart Contract
In terms of smart contracts, the following areas will be researched in the future:
(1) Optimization of smart contract performance
At present, the computing capacity of smart contracts is relatively limited and it is difficult to meet the requirements of large-scale and complex calculations. The second layer expansion solution (Layer2) shifts most of the "expensive" work off-chain, enabling blockchain developers to work in Turing. Make a trade-off between scalability, decentralization, and cost on a complete programmable blockchain, such as the state channel in its four main forms allows transactions, operations, and operations on the blockchain to be off-chain Manage and perform multi-signature based on the completion of off-chain operations, and bring the final state to the chain. Through continuous research and improvement of Layer2, it is an effective method to improve the performance of the blockchain and its smart contracts.
(2) Deploy cross-chain smart contracts
Cross-chain and its derived side chains are still an important link in the development of blockchain technology. Cross-chain can achieve mutual communication and value transfer between chains. In order to achieve better cross-chain communication, high-availability, high-performance, and scalable cross-chain contracts need to be formulated.
(3) Smart contract security
According to the statistics of blockchain security incidents compiled by Cheetah Technology, from 2011 to 2018, smart contract security incidents only accounted for 6.67%. This proportion is not too high compared to the blockchain security incident, but the economic loss caused by it is as high as $ 12.4. Among them are The DAO security vulnerabilities, parity multi-signature wallet two security vulnerabilities, and BEC theft incidents. Smart contracts should reduce vulnerabilities in security, and improve the security of contract making in terms of re-entry attacks, permission control, integer overflow, time stamp dependency, short address attacks, etc.
(4) Smart contract privacy
At present, each user on the smart contract is only theoretically anonymous. Although other identity information such as user names are transferred to the blockchain network by being converted into address identifiers, the real information cannot be known, but once the network user and the real world affairs When the association occurs, the address identifier becomes the network code, and any user-related information and behavior will be associated with this account. If the account is profiled, the user information will still be leaked. And the current privacy protection of smart contracts is based on the principle of asymmetric cryptography, and it is difficult for the existing technical means to directly overcome it through calculation. But with the development of quantum cryptography, it is possible to crack asymmetric cryptography. Attention should be paid to the research on the privacy of smart contracts and their risk response measures.
(5) Combination of smart contracts and application fields
The implementation of blockchain and smart contract technology has great commercial value. How to optimize smart contracts to integrate with emerging fields such as the Internet of Things is of great significance. The Internet of Things has characteristics such as multiple nodes and high concurrency, which will generate a large amount of data. It brings a serious burden to the traditional centralized network data storage, and combined with the blockchain technology helps reduce the burden on the centralized nodes. Smart contracts realize the automation of IoT processes in the combination of IoT and blockchain technology, ensuring efficiency and cost savings.
(6) Legal issues of smart contracts
In practical applications of smart contracts, legal problems such as difficulty in accountability may occur. Making smart contracts legally effective is also a prerequisite for smart contracts. In order to fully guarantee the legal efficiency of smart contracts, laws and regulations in the actual application process should be fully considered when formulating contracts.
(7) Smart contracts are more intelligent
At present, most people consider the smart characteristics of smart contracts. In the future, with the development of artificial intelligence technologies such as deep learning and semantic recognition, smarter smart contracts will need to be developed to enable smart contracts to have the capabilities of autonomous perception, autonomous learning, and autonomous reasoning. Smart contracts are truly intelligent.
4.4 Blockchain Security Guarantee
Research on blockchain security assurance is mainly reflected in the following three aspects:
(1) Decentralization, security and scalability
PoW is the earliest consensus mechanism applied to the blockchain. It has always had problems such as low efficiency and high energy consumption. PoS consensus solutions with low energy consumption face security problems that are easy to fork. The BFT protocol with a relatively complete certification system does not support large-scale node expansion, and the network overhead is large. The sharding technology improves the efficiency of the system and causes the problem of weak security. Using trusted hardware to achieve consensus has backdoor risks. How to balance decentralization, security, and scalability is an important issue to be resolved in the development of the blockchain consensus mechanism.
(2) Blockchain interconnection
In order to enrich the functions of the blockchain, improve the ecosystem of the blockchain, and maximize the value of the blockchain, the interconnection between the blockchain and the external digital world, the physical world, and the heterogeneous blockchain will become a future development trend. In the process of achieving blockchain interconnection, there will be many security issues, which will also become the research focus of the future blockchain security direction.
(3) System-level security system
The development of the blockchain also requires the establishment of a system-level security system to improve the security of the blockchain as a whole, promote the security standardization of the blockchain, and provide design, management, and use guidelines for the development and use of the blockchain. Accelerate the development of blockchain-related security specifications and standards, and enhance the blockchain security monitoring capabilities to ensure the healthy development and continuous innovation of the blockchain industry.
4.5 Blockchain supervision and privacy protection
The research focus of blockchain supervision is:
(1) Anonymous supervision technology of public blockchains needs to be deepened: Although many researchers are using account analysis methods on public blockchains such as Bitcoin and Ethereum, hoping to find the owner behind a public blockchain account, the current research still In its infancy, there is no good way to solve this problem.
(2) Coexistence technology of privacy protection and supervision of the alliance chain needs to be improved: the current alliance chain architecture has not been designed with a special supervision node, and it is impossible to meet the regulators' requirements on the premise of protecting the privacy of blockchain members and data. Regulatory needs. The balance between regulation and privacy requires further research.
(3) Content supervision needs to be researched: Most of the existing research on public chain only addresses the anonymity of the blockchain, and there is still insufficient research in such fields as content supervision. Although the alliance chain is easier to supervise than the public chain, the alliance chain also has the characteristics of being non-tamperable. Once there is sensitive information on the chain, the data on the chain cannot be rolled back.
In terms of privacy protection, the importance of privacy protection continues to increase. The main research is:
(1) On-demand network layer security protection mechanism: For alliance chains and private chains, adopt appropriate access control policies to prevent malicious nodes from accessing and listening to the network, and fundamentally enhance the protection ability of the network layer. In addition, the alliance chain or private chain has many similarities with the traditional centralized architecture, and mature security measures in the traditional centralized architecture can be adopted. Aiming at the public chain network, the research focuses on the method of detecting abnormal nodes, and early detection and shielding of malicious nodes. In addition, research on better anonymous communication mechanisms in terms of efficiency, performance, and ease of use is required to replace existing anonymous communication schemes such as Tor.
(2) Transaction layer privacy protection mechanism based on cryptographic algorithms: With the development of data analysis technology, the effectiveness of traditional coin mixing mechanisms to protect privacy will gradually decrease. It is necessary to study the use of cryptographic algorithms to ensure the security of mixed coins. For example, zero-knowledge proof mechanism, homomorphic encryption mechanism. The encryption-based protection scheme should fully consider the shortcomings of the blockchain server in computing performance and storage performance, and design a more versatile encryption method.
(3) Security key technology: In the application layer, in addition to improving user security awareness and enhancing the security capabilities of blockchain service providers, the key is to study the key protection technology of the wallet and develop a convenient, secure and reliable wallet program. Wallet keys are directly related to account security. You can study keyless cryptographic algorithms and code obfuscation techniques to prevent malicious users from extracting key information through disassembly and other methods. You can study multi-factor authentication mechanisms based on passwords, hardware, and biological characteristics. Enhance the security of private keys.
4.6 Application of Blockchain Technology
In terms of blockchain applications, in addition to the financial industry, supply chain management, Internet of Things, copyright protection, medical industry, etc., the application fields are constantly expanding and the application level is deepening.
Efficiency is an important factor restricting the application of blockchain technology, which has largely restricted the application of blockchain in high-frequency transactions in the financial system. Improving blockchain efficiency is the goal and development trend of future blockchain technology in the financial industry and various related industries. Moreover, how to regulate the blockchain is also a problem that needs to be solved in the future. In addition, when blockchain technology is applied to the financial industry, its security needs to be tested using authoritative standards [ 70-72 ] .
With the continuous improvement of the level of blockchain technology, blockchain will be widely used in education, charity, traceability of agricultural products, etc. The widespread application of blockchain technology will bring greater changes to social life.
5. Concluding remarks
Compared with traditional distributed databases, the main technical advantages of blockchain include: First, the evolution from centralized storage ledger to distributed shared ledger. The blockchain has broken the original centralized bookkeeping and turned into a "shared throughout the network" distributed ledger. The parties involved in bookkeeping use a synchronization and coordination mechanism to ensure data consistency and improve payment settlement efficiency. . The second is to solve the problem of traditional centralized trust mechanism. There is no central node in the network, all nodes are equal, and an overall consensus is reached through a point-to-point transmission protocol. Third, data is secure and difficult to tamper with. The data of each block will be encrypted by an asymmetric cryptographic algorithm and distributed to all nodes to ensure that the stop of any node will not affect the overall operation of the system. Fourth, business applications are driven by smart contracts. The system's smart contract consisting of code runs automatically without human intervention.
At present, global blockchain technology innovation is becoming increasingly active. Countries around the world attach great importance to and advance the layout. International organizations, technology giants, and start-ups are actively exploring the integration and innovation of blockchain and vertical fields. The landing scene has gradually extended from the financial field to the real economy. Although the industry ecology has initially taken shape, due to the industry's emphasis on application innovation, the underlying platform lacks independent research and development capabilities, and corresponding laws and regulations have yet to be improved. At this stage, it is necessary to actively carry out pilot applications and demonstrations in key areas, gather multiple forces to break through technical bottlenecks, strengthen policy formulation and regulatory compliance research, and provide a healthy development space for the blockchain industry.
About the Author
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- U.S. mutual funds enter the blockchain in a big way
- Blockstream CEO: Bitcoin is paramount, stablecoin and central bank digital currencies cannot match it
- Behind the difficulty of recruiting on the blockchain: the number of job seekers reaches 7 times the recruitment demand
- Blockchain emerges like a tiger? Thoughts on the Fourth Wealth Mania
- U.S. digital asset supervision still follows the lawful and orderly principle. In 2019, the "toll station" model will be opened to embrace innovation
- Popular science | Zou Chuanwei: Global stablecoins and central bank digital currencies
- Trend analysis: The transaction volume of the Bitcoin chain exceeds the on-chain, and the main application scenarios tend to be centralized






