Getting started with blockchain | What is a 51% power attack?
Concerned about the bitcoin's small partners, I must have heard 51% of the power to attack the word, what does it mean, what kind of "bad things" can be done after launching this kind of attack? Today, I will briefly introduce the 51% of the power attack related matters.
In the Bitcoin white paper, there has been such a statement that the sum of the honest node control power is greater than the sum of the attacker's computing power of the cooperative relationship, and the system is safe.
In other words, when the computing power controlled by the malicious node in the system exceeds the computing power controlled by the honest node, the system is at risk of being attacked. This attack, initiated by a malicious node that controls more than 50% of the power, is called a 51% attack (51% Attack).
Is it possible that all cryptocurrency systems are at risk of a 51% power attack? In fact, it is not. Only the cryptocurrency based on the PoW (workload proof) consensus mechanism has 51% computational attacks, such as bitcoin, bit cash, and current Ethereum; instead of the cryptocurrency of the PoW consensus algorithm. There is no 51% power attack, such as EOS, TRON, etc. based on the DPoS (trusted equity) consensus mechanism.
- Money Anhe: To subvert yourself, instead of waiting for others to subvert | Chain node AMA highlights
- Huawei enters the blockchain, the three giants are fighting
- Unless Aoben Cong can sleep for a year, he is not Nakamoto.
After learning about the 51% power attack, you must be curious about what bad things can be done with this attack.
1. Double Spending . Double flower means that a "money" has been spent twice or even many times.
How does the 51% power attack strike a double flower? Suppose Xiaohe has 666BTC. He also pays the coins and sends them to his other wallet address. In other words, a small black money is transferred to two people at the same time. In the end, the deal sent to Dabai was first confirmed and packaged in a block with a block height of N.
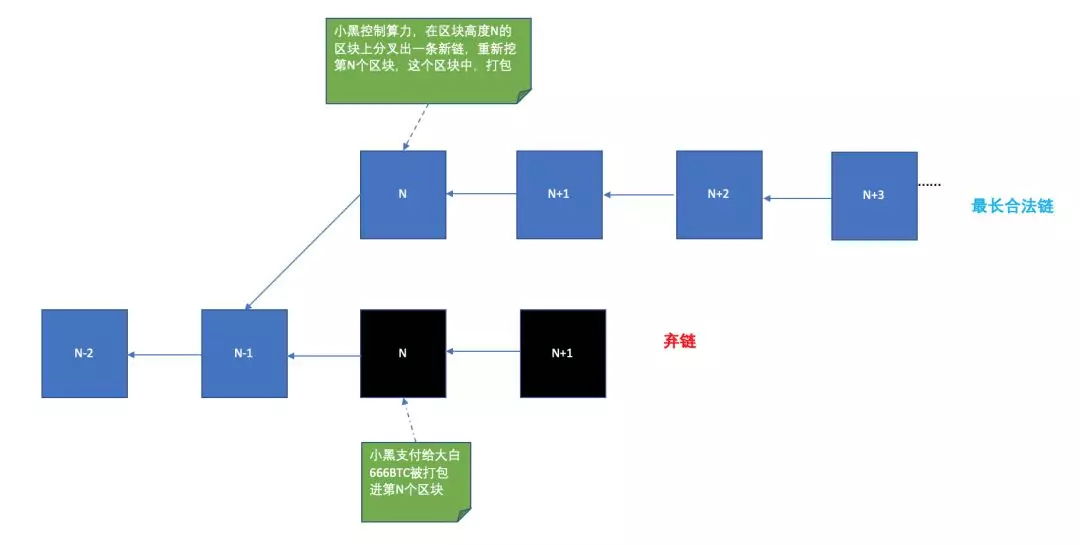
At this time, it controlled the black of more than 50% of the power, and launched a 51% power attack. By reassembling the Nth block, he packaged the deal into his block and continued to extend the block on the chain. Due to the power of computing power, this quantity will become the longest legal chain . This small black 666BTC double flower success, the 666BTC in the big white wallet "missed".

2. Suppress certain addresses to send/receive bitcoin
In addition, what can 51% of the power attack do? It can also suppress the transmission/reception of bitcoin at an address.
Xiao Hei and Da Bai quarreled, and Xiao Hei relied on 51% of his computing power. He knew that the big white bitcoin address could make the transaction related to Dabai unrecognizable. For example, in order to express his respect to Nakamoto, Dabai wants to send a bitcoin to the "Creation Address". The black that controls more than half of the computing power will not pack the deal, not only that, but also the other miners will not pack the deal. How did Xiaohe do it?
If the new block dug by other miners packs the deal, Xiaohe will choose not to continue mining after this block. He will choose to rebuild the new block after the last block and reject the deal. Relying on your own computing power, this chain of small blacks will become the longest legal chain.
Under this circumstance, other miners will not have to package the transactions related to Dabai, otherwise the excavated blocks will be isolated by Xiaohei, and the rewards will also be invalidated.

If you have more than 50% of your computing power, you can do whatever you want. What can you do with bad things? Actually not. Even if you control more than 50% of the calculation power, you can't transfer other people's coins (stolen coins), because this operation requires a private key to sign. If you want to forge a signature to "steal the currency," this behavior is an honest miner can't. Tolerance, this will subvert the system consensus. In this case, other miners will not continue to expand the blockchain after the blocks he has dug, and will actively fork out the legal blockchain, and the blocks excavated by the “stolen coins” miners will be isolated.

In addition, the system's block rewards are modified. For example, the block reward is changed from the current 12.5BTC to 50BTC. This behavior is also a subversion of the system consensus. Honest miners will refuse to branch out a new chain in such illegal blocks. .
——End——
Produced|Baihua blockchain (ID: hellobtc)
『Declaration : This series of content is only for the introduction of blockchain science, and does not constitute any investment advice or advice. If there are any errors or omissions, please leave a message. 』
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- In the era of blockchain traceability, where should the "target" of counterfeiting be pointed?
- Twitter featured: Mancoin network suspected of being stolen 100 million US dollars, the official claims to maintain
- Science | Take you to explore the mystery of the decentralized exchange structure (on)
- People with communist labor vouchers issue "coins"
- BaaS vendor competition: different tracks and different postures
- Interview with Zhu Jiaming: The era of blockchain and currency diversification is coming
- OK first disclosed OKUSD issue: Based on OKChain, anchoring USD, compliance is the primary purpose






