How to choose cryptography technology? Final exploration of the security model of quantum computing communication
Author: Yan strong
Source: Wezhong Bank Blockchain
The application life of classic cryptography technology is coming? Why does quantum computing crack existing privacy protection schemes? What are the implications of quantum communication for the design of privacy protection schemes? How to effectively deal with the challenge of quantum computing communication technology to privacy protection?
Here, we will enter the final chapter of the security model analysis trilogy, jump out of the limitations of computing and communication capabilities, focus on the enlightenment of future technological developments on the selection of privacy protection technologies, and analyze quantum computing and quantum communication technology for classic cryptography technology And the response to business technology selection.
- The money circle of the currency circle is eyeing a short video: dozens of "fire bull" platforms have been born, claiming to be "500 per month lying"
- Ali & JD.com ’s blockchain war, Jack Ma: 100 billion is not enough, I will invest 200 billion
- U.S. Congressional Oversight Agency Says Very Interested in Blockchain Technology
Quantum computing and quantum communication are both emerging technologies based on quantum mechanics. Unlike classical physics theory, quantum mechanics studies the physical theory of the movement of microscopic particles in the physical world, which can be used to explain microscopic systems that cannot be explained by classical physics theory. Together with the theory of relativity, this theory is called the two basic pillars of modern physics.
In quantum mechanics, the most classic story is Schrodinger's cat. If a similar story is interpreted by the protagonist Xiaohua and the beauty of a friend, it will be like this:

When Xiaohua first saw beauty, she had a good impression. After the "contact" of the first three stories, Xiaohua had a soft spot for beauty. On a romantic afternoon, Xiaohua summoned the courage to confess her beauty. Xiaohua has long admired Xiaohua in her heart, but the reserved she deliberately gave Xiaohua a small challenge to verify Xiaohua's sincerity-"What is the date of our first date?"
This can stump Xiaohua! The beautiful little theater has carried out three phases before. Xiaohua thinks that all three dates may be the correct answer. Fortunately, quantum computing helped Xiaohua solve this problem.
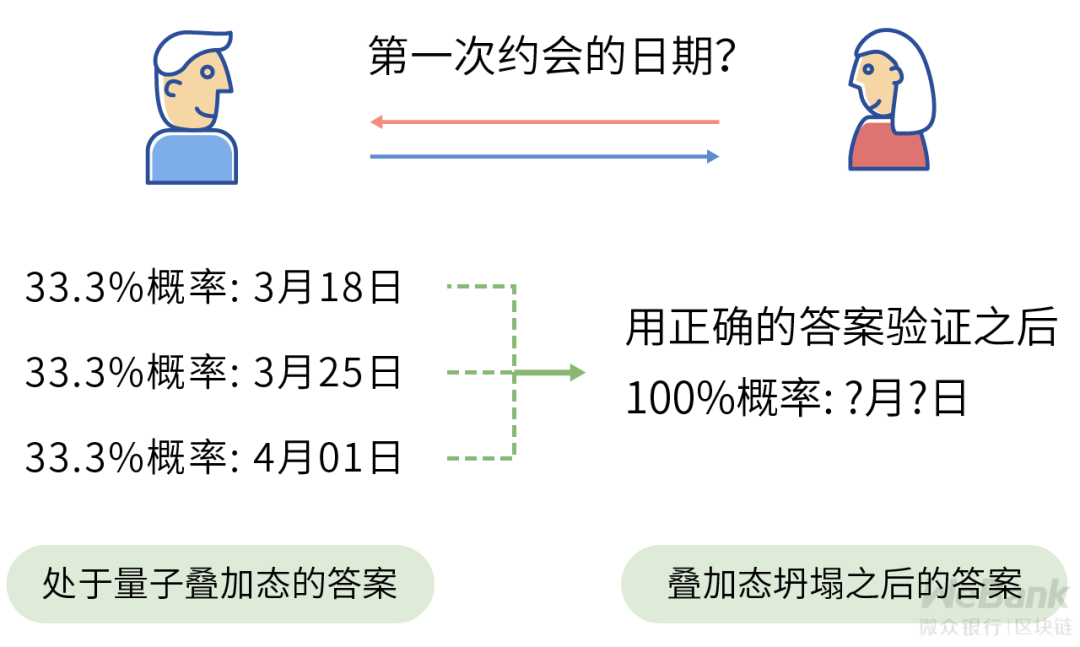
In the traditional calculation model, Xiaohua can only send the results of one date to Meili. If the answer is wrong, Meili will make mistakes after verifying with the correct results, then Xiaohua's confession process is a bit embarrassing. In the quantum computing process, Xiaohua's answer will contain all the results of these three dates at the same time. When Meili is verified with the correct answer, it can be successfully verified.
In quantum mechanics, this state containing all possible answers is called a quantum superposition state . Once the result is received by Beauty, that is, after observation, the corresponding quantum superposition state will collapse probabilistically, and the answer will be uniquely determined as a specific value, and Beauty can get the answer that matches your heart.
This probabilistic state expression and the probabilistic correlation between observed events are the core theoretical points of quantum mechanics. The quantum computing and quantum communication constructed in this way use the probability characteristics of quantum to break through the capability bottleneck of the existing technology.
The following will introduce the differences between classic computer technology and quantum computer technology by way of comparison, and analyze the impact and inspiration of these differences on cryptography-based privacy protection technology solutions.

In 1945, physicist and mathematician John von Neumann proposed a theoretical calculation model-von Neumann architecture, which laid a theoretical foundation for the design of modern computer systems.
The von Neumann architecture expresses the calculation process as a data storage process and a program control process. The data and instructions are stored in the storage medium in binary form, and the controller represented by the CPU reads the instruction stream to control the Read and write different data to execute the program serially.
Although multi-core multi-threaded CPUs have long been popular, the core execution flow is still serial execution under the von Neumann architecture, and the corresponding software implementation and algorithm design are all carried out under the premise of serial execution of programs.
In contrast, quantum computers are inherently parallel in nature due to the probability uncertainty caused by quantum superposition states.
According to the wave-particle duality in quantum mechanics, each quantum can be expressed as a wave with a certain probability distribution. Corresponding to the binary format in computer system design, a single quantum can express the values of 0 and 1 at the same time, and can interact with another quantum with the values of 0 and 1 to complete the parallel calculation.

Such a quantum is usually called qubit. Due to the inherent instability of quantum states, expressing a readable logical qubit usually requires maintaining multiple physical qubits to achieve system fault tolerance. Controlling these qubits needs to be performed in a superconducting environment close to absolute zero (minus 273.15 degrees Celsius), which is very challenging, and the corresponding engineering implementation is still early.
Google disclosed in the 2019 paper that it can already control 53 quantum qubit quantum computers to a certain extent, and complete the proof of whether a random number sequence is generated by a random number generator in 3 minutes and 20 seconds. The same proof It takes about 10,000 years to execute on the existing von Neumann architecture supercomputer.
As early as 2017, Google's partner company D-Wave released D-Wave 2000Q, a quantum computer that allegedly implemented 2,000 logical qubits. In theory, it may already have the technical ability to crack all the current classic cryptographic technical solutions.
Quantum computers provide an exponential level of computational speed, which can break the computational asymmetry we mentioned in Chapter 3 . For von Neumann computers, the classic NP problem is a computationally difficult problem, while for quantum computers, in theory, P = NP can be easily achieved, and an attacker can crack the corresponding classic cryptographic algorithm and extract the corresponding secret Private data in keys and ciphertext.
According to the National Institute of Standards and Technology NIST analysis, quantum computers have the greatest impact on asymmetric cryptography systems . Classical computational difficulty problems used to construct public key cryptographic algorithms, such as large number decomposition difficulty problems, discrete logarithm difficulty problems, discrete logarithm difficulty problems on elliptic curves, all have effective cracking algorithms on quantum computers-Shor Algorithms and their variants. These attacks will specifically affect the security of current public key encryption, digital signatures, digital certificates, key exchanges, etc.
Compared with asymmetric cryptography, the impact of quantum computer symmetric cryptography is relatively small . As long as the length of the key is increased moderately, the most effective Grover algorithm attack can be limited, but it cannot be ruled out that more efficient quantum cracking algorithms will be available in the future. These attacks will specifically affect symmetric encryption, hashing, and hash-based derivation algorithms.
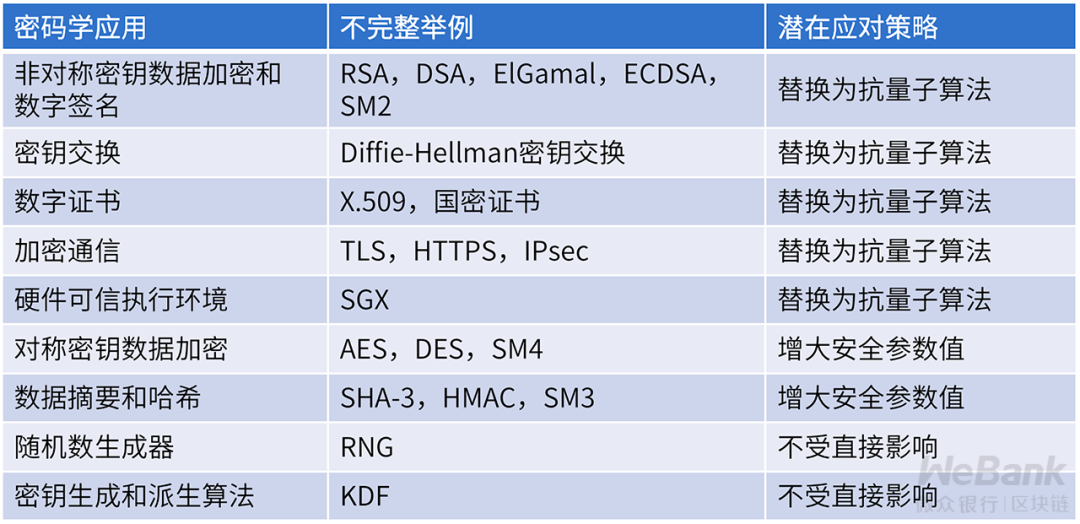
The influence of quantum computers on classic cryptographic algorithms not only affects the software level, but also has a great impact on the hardware level.
At present, the cryptographic algorithms implemented in the hardware trusted execution environment represented by Intel SGX are not resistant to quantum computing. Some modules with high performance requirements, such as SGX's memory encryption module (currently AES-128), are implemented in hardware that cannot be upgraded. Once the quantum computer is effectively applied, physical replacement of trusted hardware may bring a greater cost than remote replacement algorithm software.
In order to deal with the threat of quantum computing to classical cryptographic algorithms, we need to construct new computational difficulty problems. Considering the quantum computing security model, that is, the security assumption that allows attackers to use quantum computers, the construction of secure cryptographic algorithms is full of uncertainties, and there is currently no relevant international or national standard.
NIST has begun the second round of public evaluation of the quantum-resistant algorithm standard in 2019. It is expected that there will be some staged results in 2021, and then a third round of public evaluation process will be carried out. Jing Jiwu, then deputy director of the Institute of Information Engineering of the Chinese Academy of Sciences, said in a 2018 news report that China may carry out standardization of anti-quantum algorithms around 2022, and it is expected to be commercialized around 2025.
Before the completion of the engineering standards, the existing anti-quantum algorithms must be used with caution, even the solutions derived from top academic journals may have errors. On the other hand, as mentioned in the previous comment , even if it is theoretically safe, omissions in the engineering implementation will lead to the leakage of private data.
Therefore, the use of anti-quantum algorithm engineering standards that have been tested for a certain period of time is a necessary condition to ensure the effectiveness of the final privacy protection scheme.

Quantum Communication VS Classic Communication
The information transmission in classic communication is carried out by the sender through the transmission medium to send the various signal carriers to the receiver. The transmission speed is limited by the conductivity of the transmission medium and the energy attenuation rate of the signal carrier. According to the theory of relativity, its highest The transmission speed does not exceed the speed of light.
In contrast, quantum communication is based on the principle of quantum entanglement. In theory, after the device is initialized, there is no need to send any signal carrier to the receiver from the sender, and there is the possibility of realizing super-light speed instant communication.
Regarding the explanation of quantum entanglement theory, we continue to present it with Xiaohua and beautiful stories:

Following the above story, Xiaohua passed the test of beauty on the basis of quantum computing, successfully holding hands with beauty, and determining the relationship with her.
On a sunny day, the two met for a warm afternoon in the playground. When parting, the beautiful hunch will have surprises. As soon as she turned around, Xiaohua was holding her favorite doll slowly, and in a trance, the beauty was like the heroine of an idol drama, and her face was filled with happiness.
The two people's electrical induction is similar to the entangled state between quantum. Observing one quantum in a quantum pair in an entangled state will cause the state of the other quantum in the quantum pair to change accordingly. This change is 100% related to previous observations. Xiaohua's loving heart makes changes, and correspondingly, the beautiful heart will feel.
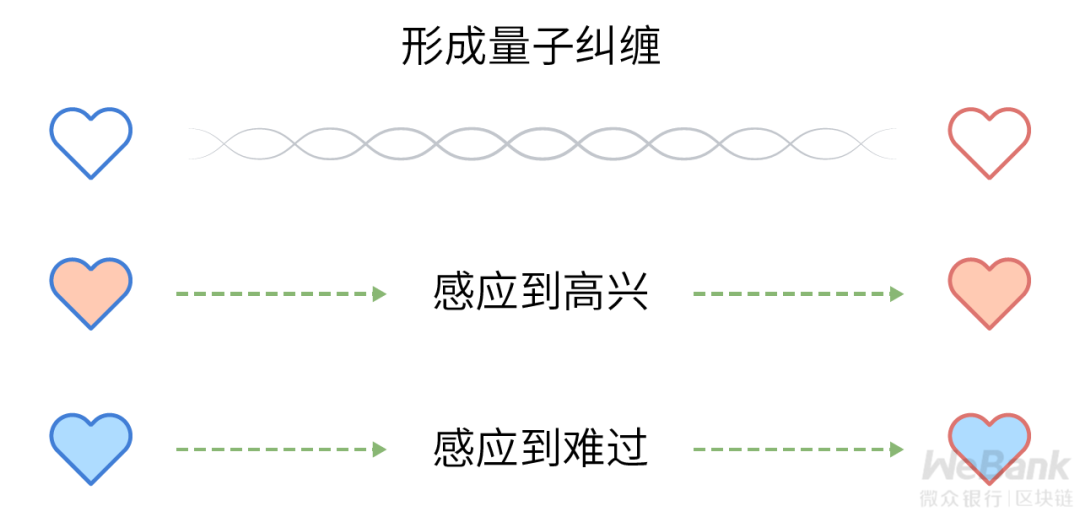
Although the characteristics of quantum entanglement can disregard the physical distance for information transmission, due to the current quantum cryptographic communication protocol design, such as the classic BB84 protocol and Ekert91 protocol, it still needs to cooperate with the classic communication channel to realize the encrypted transmission of information. It is still not possible to transmit information beyond the speed of light.

Regarding the security of quantum cryptographic communication, a common point of view is that it is information-theoretic security, that is, no matter how many computing resources an attacker has, such as a quantum computer, it cannot be cracked. The corresponding explanation is that its safety is not guaranteed by the calculation difficulty theory, but by the uncertainty principle in the laws of physics.
The uncertainty principle was formally proposed by the physicist Heisenberg in 1927. As one of the basic principles of quantum mechanics, this principle stipulates that for a quantum, it is impossible to know its position and velocity at the same time, and every observation of the quantum will change the state of the quantum. From this, the principle of non-cloning can be further derived, that is, an attacker cannot perfectly replicate all states of a quantum.
For quantum communication, even if an attacker has the ability to intercept a quantum in an entangled state, it cannot perfectly replicate it.
The attacker cannot forward the copied quantum to the recipient without the recipient's knowledge, so as to eavesdrop on sensitive data. Once eavesdropping occurs, it will inevitably change the quantum state of both parties to the eavesdropping, thereby exposing the existence of the attacker.
It should be noted here that although the quantum cryptographic communication protocol can effectively detect the existence of an attacker who directly eavesdrops, it may still be affected by attacks at other protocol levels.
For example, in the classic man-in-the-middle attack, the attacker acts as a man-in-the-middle to forward messages between the two communicating parties, using a pair of entangled states for the sender and another pair of entangled states for the receiver. If there is no other trusted The channel connects the two communicating parties, and they will not be able to perceive the existence of the attacker.
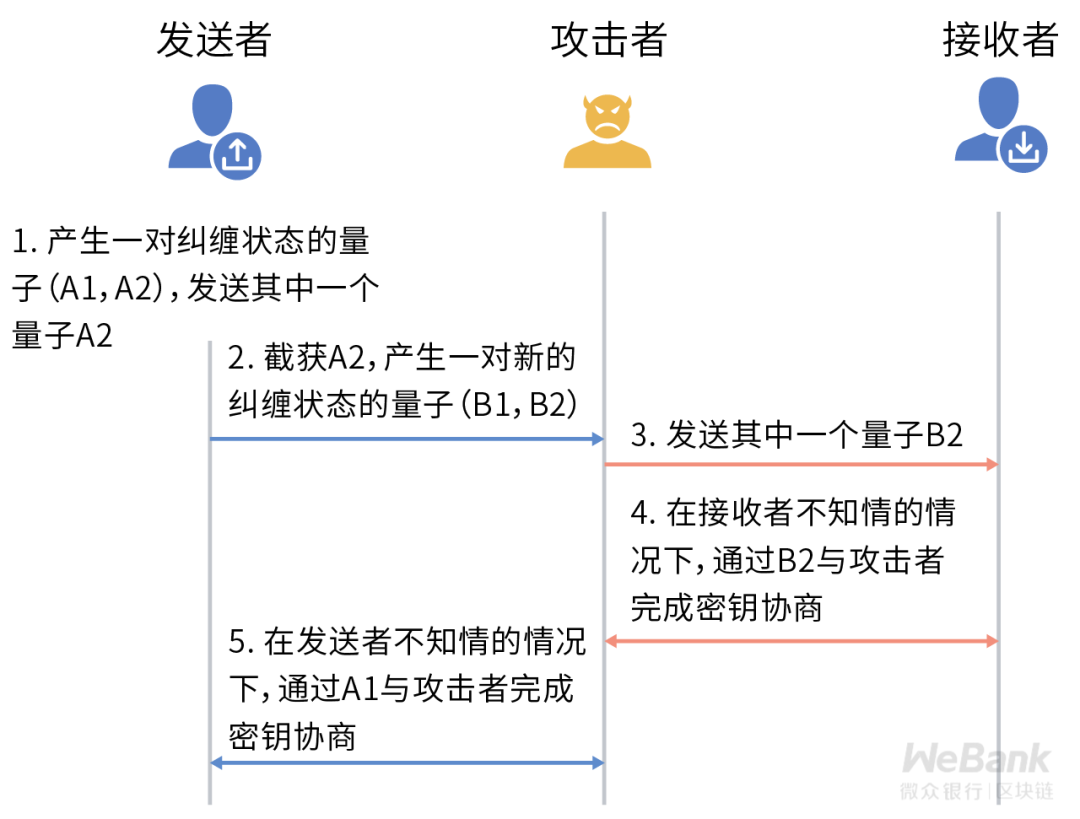
In terms of project realization, China is currently at the international advanced level. In 2016, the Mozi quantum scientific experimental satellite was the first to realize the distribution of two-way quantum entangled keys in the thousands of kilometers of stars and earth, with an effective bandwidth of about kilobits per second.
But quantum communication is still quite far away from civilian use, mainly limited by the instability of quantum channels. In strong interference environments, such as daylight environments and dense urban areas, long-distance transmission of entangled light quanta is still a huge challenge.
The modern world of quantum communication has undoubtedly added a weapon to the construction of cryptographic protocols and upper-level privacy protection schemes. As a trusted channel, quantum communication can effectively simplify the design of cryptographic protocols, improve the effectiveness of privacy protection schemes, and resist the threat of quantum computers to a certain extent.
At the same time, for the design of privacy protection schemes based on the physical limitations of transmission time, the emergence of quantum communication will affect its effectiveness.
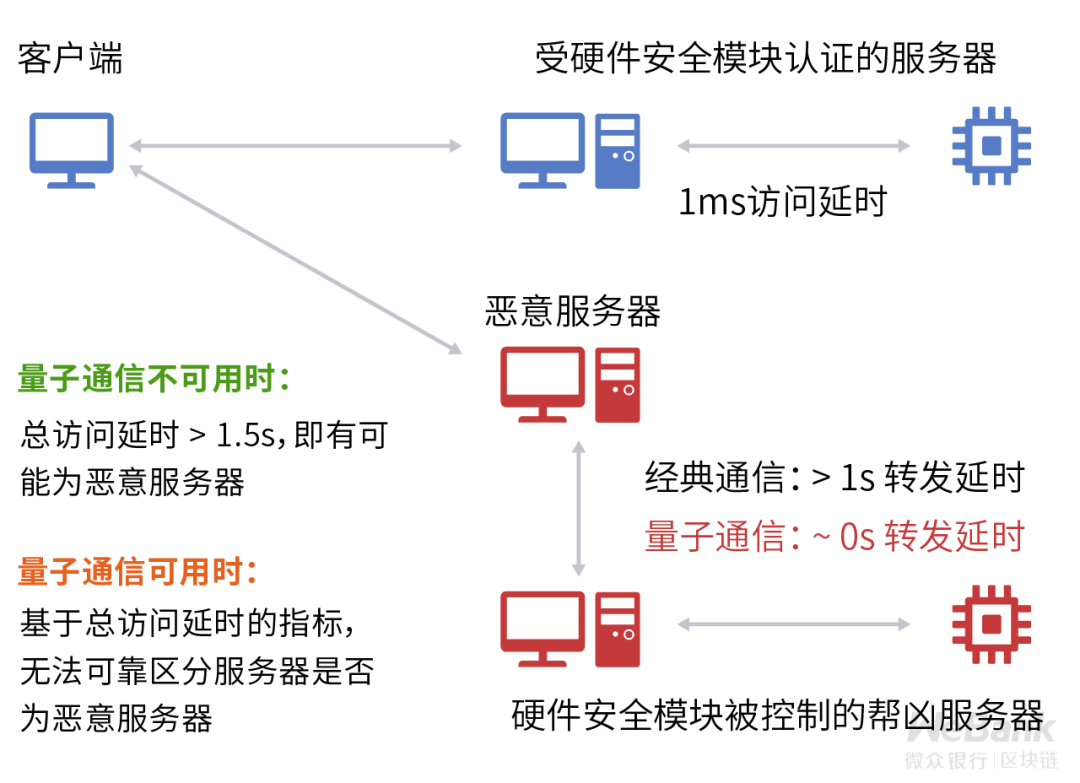
A typical example is a remote code verification protocol that combines hardware security modules and physical distance detection. In the verification process of the protocol, the honest verifier will directly call the local hardware security module to complete the server authentication. Only one interaction is required, and the effective delay can be controlled within a short time (such as 1ms). If an attacker attempts to attack the protocol, the data must be forwarded through a proxy server. On the premise of only considering classic communication, the additional forwarding delay requires a longer time (such as more than 1s).
Therefore, even if the attacker controls another hardware security module and forwards the remote code verification request to the controlled hardware security module to let it calculate for him, the total time actually consumed by the attacker will be more local than when there is no forwarding. The use of unconquered hardware security modules takes a significant amount of time to calculate, and thus the presence of an attacker can be detected.
The above information transmission requires a certain time security assumption, and it no longer holds in the face of quantum communication's distance-independent instantaneous communication capability. The time that the attacker originally used the proxy server to forward may be sharply reduced from 1s to close to 0s. This change significantly reduces the effectiveness of this type of remote code verification protocol that relies on information transmission time constraints and exposes it to the risk of overall failure.
In general, the emergence of quantum communication will bring new basic characteristics to the information transmission process. The privacy protection scheme designed based on the classic communication characteristics needs to be re-evaluated in due course to verify its effectiveness under the quantum communication security model.
Exactly: the classic password is invincible, and the quantum rookie will be sharp!
Quantum computing and quantum communication are an important milestone breakthrough in the development of information technology, which will inevitably have an impact on the existing technical system and affect the effectiveness of existing privacy protection technical solutions. However, these new theories and tools will also Promote the innovation of related technologies, and promote the emergence of more efficient and safer privacy protection technology solutions.
At present, the engineering realization of the two is still not far away from commercial use, and engineering standardization is still being gradually promoted. Enterprises should fully consider the risks they bring when selecting technologies. For the use of classic cryptographic algorithms and hardware security The system of the module provides a pluggable design, which provides necessary alternatives to privacy data of different confidentiality levels, in order to control the impact of the sudden practical application of specific quantum computing communication technology.
The key theoretical sciences related to the selection of cryptography technology have come to an end here. At the beginning of the next discussion, we will specifically launch a technical analysis of the core components of the cryptography algorithm.
We will continue to update Blocking; if you have any questions or suggestions, please contact us!
Was this article helpful?
93 out of 132 found this helpful
Related articles
- Babbitt column | stocks inward, tokens outward
- Viewpoint | Blockchain can improve data governance transparency and efficiency, privacy protection still faces challenges
- What is the impact of halving BCH, BSV, and BTC?
- There is no skyrocketing currency price, no miner death spiral, is BCH halved?
- Popular Science | Moloch Upgrade: Getting Started Version 2.0
- The Chicago DeFi Alliance (CDA) was officially launched, and TD Ameritrade, Compound, etc. joined
- What to do after halving Bitcoin? All these transactions say






